How is Continuous Authentication Different from Two-Factor Authentication?
Traditional multi-factor and two-factor authentication methods are falling short due to their easily phishable factors and their static, one-time verification. Continuous authentication fills these gaps and makes security dynamic and robust against evolving cyber threats.
But what is it, and how does it succeed where other methods have failed?
Authentication is constantly evolving
When the need for authentication—verifying a user is who they say they are—first became standard, passwords were considered a best practice. A simple string of text that makes sense to users, passwords quickly became the standard.
As bad actors learned to bypass or crack simple passwords, the best practice evolved from choosing and storing plaintext passwords to storing password hashes and then to adding salt.
The weaknesses remained, however, and no matter how complex passwords became bad actors found ways to bypass them. So security teams added two-factor authentication to the mix. But attackers soon found weaknesses there as well. Phishing-resistant authentication is the newest requirement, the new best thing, but it won’t be the last.
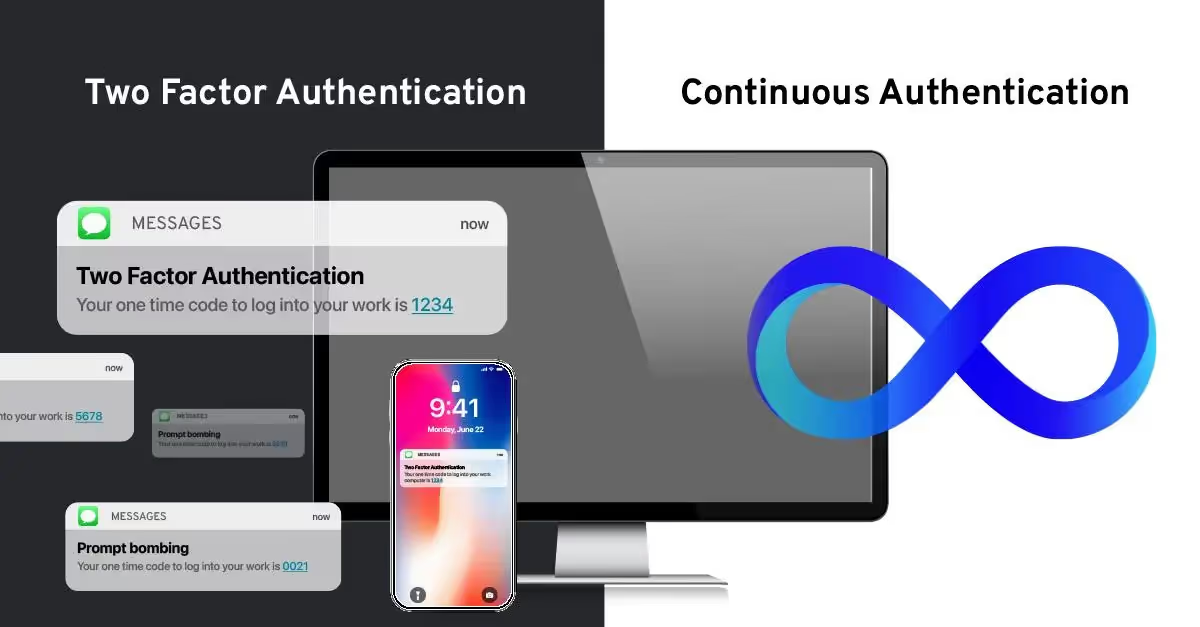
What’s two-factor authentication?
Enter multi-factor authentication (MFA), which was introduced to bolster the security of password-based authentication. By requiring two or more factors for authentication, such as the combination of a password and a one-time password (OTP) from an authenticator app, MFA makes it more difficult for an attacker to take advantage of a compromised password.
Using 2FA and MFA is best practice, but they are only as secure as the authentication factors they use, and some factors are very easily phished. Unless 2FA or MFA uses strong authentication factors, such as biometrics or cryptographic security keys, it boils down to hoping two weak authentication factors will provide the same level of security as a single, strong factor.
What’s continuous authentication?
Even if MFA is implemented with two strong factors, it only verifies identity at a single point in time—when your user first authenticates. If another person picks up an authenticated device, or the device moves from a low-risk to high-risk environment, this could place your organization at risk.
Continuous authentication is the next stage in the evolution of user authentication. Instead of providing authentication at a single point in time, continuous authentication performs ongoing risk monitoring and security policy enforcement to protect the organization throughout a user’s entire session.
Continuous authentication enables ongoing monitoring of risk conditions, a necessary element in any zero trust architecture.
For example, after a user successfully authenticates, a continuous authentication system may periodically check if antivirus software is active or if security features such as a firewall are enabled on the system.
If an authenticated user disables these security features or otherwise violates corporate security policy, then the device can be quarantined, preventing it from accessing corporate resources or posing a threat to corporate systems.
When looking at 2FA and continuous authentication, you're not making an either/or decision. This is a both/and decision. You need both to protect your resources and data.
If you are implementing a zero trust architecture, or setting up Zero Trust Authentication, your security builds on passwordless, phishing-resistant MFA using multiple factors. After the user successfully authenticates, continuous authentication provides ongoing protection and risk management by monitoring for activities that indicate a potential threat or put the organization at risk.
Continuous authentication with Beyond Identity
Continuous authentication is a simple choice, and Beyond Identity makes it easy to deploy.
Beyond Identity:
- Uses passwordless, phishing-resistant MFA to establish that the identity of your end user is verified cryptographically.
- Allows you to ensure device trust—only approved devices that meet your security requirements can gain access to your resources. Beyond Identity’s policy engine checks dozens of device security posture settings.
- Continuously polls the device (every 10 mins) to see if there are any changes in user behavior factors (like location) or device security posture settings (someone turned off the firewall after logging in).
2FA and continuous authentication are complementary solutions. 2FA bolsters the strength of the initial user authentication, while continuous authentication provides ongoing risk monitoring and security policy enforcement.
All Beyond Identity solutions, including Secure Workforce, Secure Customers, and Secure DevOps offer secure, passwordless, and phishing-resistant MFA with continuous authentication.
With passwordless MFA and continuous authentication, you can validate employee and customer identities in a secure, user-friendly way. Learn more about enhancing the security of your authentication system and implementing Zero Trust Authentication by signing up for a free demo.
Traditional multi-factor and two-factor authentication methods are falling short due to their easily phishable factors and their static, one-time verification. Continuous authentication fills these gaps and makes security dynamic and robust against evolving cyber threats.
But what is it, and how does it succeed where other methods have failed?
Authentication is constantly evolving
When the need for authentication—verifying a user is who they say they are—first became standard, passwords were considered a best practice. A simple string of text that makes sense to users, passwords quickly became the standard.
As bad actors learned to bypass or crack simple passwords, the best practice evolved from choosing and storing plaintext passwords to storing password hashes and then to adding salt.
The weaknesses remained, however, and no matter how complex passwords became bad actors found ways to bypass them. So security teams added two-factor authentication to the mix. But attackers soon found weaknesses there as well. Phishing-resistant authentication is the newest requirement, the new best thing, but it won’t be the last.
What’s two-factor authentication?
Enter multi-factor authentication (MFA), which was introduced to bolster the security of password-based authentication. By requiring two or more factors for authentication, such as the combination of a password and a one-time password (OTP) from an authenticator app, MFA makes it more difficult for an attacker to take advantage of a compromised password.
Using 2FA and MFA is best practice, but they are only as secure as the authentication factors they use, and some factors are very easily phished. Unless 2FA or MFA uses strong authentication factors, such as biometrics or cryptographic security keys, it boils down to hoping two weak authentication factors will provide the same level of security as a single, strong factor.
What’s continuous authentication?
Even if MFA is implemented with two strong factors, it only verifies identity at a single point in time—when your user first authenticates. If another person picks up an authenticated device, or the device moves from a low-risk to high-risk environment, this could place your organization at risk.
Continuous authentication is the next stage in the evolution of user authentication. Instead of providing authentication at a single point in time, continuous authentication performs ongoing risk monitoring and security policy enforcement to protect the organization throughout a user’s entire session.
Continuous authentication enables ongoing monitoring of risk conditions, a necessary element in any zero trust architecture.
For example, after a user successfully authenticates, a continuous authentication system may periodically check if antivirus software is active or if security features such as a firewall are enabled on the system.
If an authenticated user disables these security features or otherwise violates corporate security policy, then the device can be quarantined, preventing it from accessing corporate resources or posing a threat to corporate systems.
When looking at 2FA and continuous authentication, you're not making an either/or decision. This is a both/and decision. You need both to protect your resources and data.
If you are implementing a zero trust architecture, or setting up Zero Trust Authentication, your security builds on passwordless, phishing-resistant MFA using multiple factors. After the user successfully authenticates, continuous authentication provides ongoing protection and risk management by monitoring for activities that indicate a potential threat or put the organization at risk.
Continuous authentication with Beyond Identity
Continuous authentication is a simple choice, and Beyond Identity makes it easy to deploy.
Beyond Identity:
- Uses passwordless, phishing-resistant MFA to establish that the identity of your end user is verified cryptographically.
- Allows you to ensure device trust—only approved devices that meet your security requirements can gain access to your resources. Beyond Identity’s policy engine checks dozens of device security posture settings.
- Continuously polls the device (every 10 mins) to see if there are any changes in user behavior factors (like location) or device security posture settings (someone turned off the firewall after logging in).
2FA and continuous authentication are complementary solutions. 2FA bolsters the strength of the initial user authentication, while continuous authentication provides ongoing risk monitoring and security policy enforcement.
All Beyond Identity solutions, including Secure Workforce, Secure Customers, and Secure DevOps offer secure, passwordless, and phishing-resistant MFA with continuous authentication.
With passwordless MFA and continuous authentication, you can validate employee and customer identities in a secure, user-friendly way. Learn more about enhancing the security of your authentication system and implementing Zero Trust Authentication by signing up for a free demo.
Traditional multi-factor and two-factor authentication methods are falling short due to their easily phishable factors and their static, one-time verification. Continuous authentication fills these gaps and makes security dynamic and robust against evolving cyber threats.
But what is it, and how does it succeed where other methods have failed?
Authentication is constantly evolving
When the need for authentication—verifying a user is who they say they are—first became standard, passwords were considered a best practice. A simple string of text that makes sense to users, passwords quickly became the standard.
As bad actors learned to bypass or crack simple passwords, the best practice evolved from choosing and storing plaintext passwords to storing password hashes and then to adding salt.
The weaknesses remained, however, and no matter how complex passwords became bad actors found ways to bypass them. So security teams added two-factor authentication to the mix. But attackers soon found weaknesses there as well. Phishing-resistant authentication is the newest requirement, the new best thing, but it won’t be the last.
What’s two-factor authentication?
Enter multi-factor authentication (MFA), which was introduced to bolster the security of password-based authentication. By requiring two or more factors for authentication, such as the combination of a password and a one-time password (OTP) from an authenticator app, MFA makes it more difficult for an attacker to take advantage of a compromised password.
Using 2FA and MFA is best practice, but they are only as secure as the authentication factors they use, and some factors are very easily phished. Unless 2FA or MFA uses strong authentication factors, such as biometrics or cryptographic security keys, it boils down to hoping two weak authentication factors will provide the same level of security as a single, strong factor.
What’s continuous authentication?
Even if MFA is implemented with two strong factors, it only verifies identity at a single point in time—when your user first authenticates. If another person picks up an authenticated device, or the device moves from a low-risk to high-risk environment, this could place your organization at risk.
Continuous authentication is the next stage in the evolution of user authentication. Instead of providing authentication at a single point in time, continuous authentication performs ongoing risk monitoring and security policy enforcement to protect the organization throughout a user’s entire session.
Continuous authentication enables ongoing monitoring of risk conditions, a necessary element in any zero trust architecture.
For example, after a user successfully authenticates, a continuous authentication system may periodically check if antivirus software is active or if security features such as a firewall are enabled on the system.
If an authenticated user disables these security features or otherwise violates corporate security policy, then the device can be quarantined, preventing it from accessing corporate resources or posing a threat to corporate systems.
When looking at 2FA and continuous authentication, you're not making an either/or decision. This is a both/and decision. You need both to protect your resources and data.
If you are implementing a zero trust architecture, or setting up Zero Trust Authentication, your security builds on passwordless, phishing-resistant MFA using multiple factors. After the user successfully authenticates, continuous authentication provides ongoing protection and risk management by monitoring for activities that indicate a potential threat or put the organization at risk.
Continuous authentication with Beyond Identity
Continuous authentication is a simple choice, and Beyond Identity makes it easy to deploy.
Beyond Identity:
- Uses passwordless, phishing-resistant MFA to establish that the identity of your end user is verified cryptographically.
- Allows you to ensure device trust—only approved devices that meet your security requirements can gain access to your resources. Beyond Identity’s policy engine checks dozens of device security posture settings.
- Continuously polls the device (every 10 mins) to see if there are any changes in user behavior factors (like location) or device security posture settings (someone turned off the firewall after logging in).
2FA and continuous authentication are complementary solutions. 2FA bolsters the strength of the initial user authentication, while continuous authentication provides ongoing risk monitoring and security policy enforcement.
All Beyond Identity solutions, including Secure Workforce, Secure Customers, and Secure DevOps offer secure, passwordless, and phishing-resistant MFA with continuous authentication.
With passwordless MFA and continuous authentication, you can validate employee and customer identities in a secure, user-friendly way. Learn more about enhancing the security of your authentication system and implementing Zero Trust Authentication by signing up for a free demo.












.avif)
.avif)



.avif)






.avif)

