Delight, convert, and protect customers
Deliver a frictionless, phishing-resistant authentication experience across every browser, device, and application

Accelerate conversions
Onboard new users faster and keep them engaged with a frictionless experience for registration, login, and recovery.
Maintain brand trust
Protect every user against account takeover fraud with passwordless, phishing-resistant MFA and risk-based policies.
Increase retention
Make returning logins effortless with universal, biometric authentication that works on any device, browser, or app.
Speed up time-to-market
Deploy quickly with robust developer tools, easy-to-use SDKs, and flexible APIs that give you control without complexity.

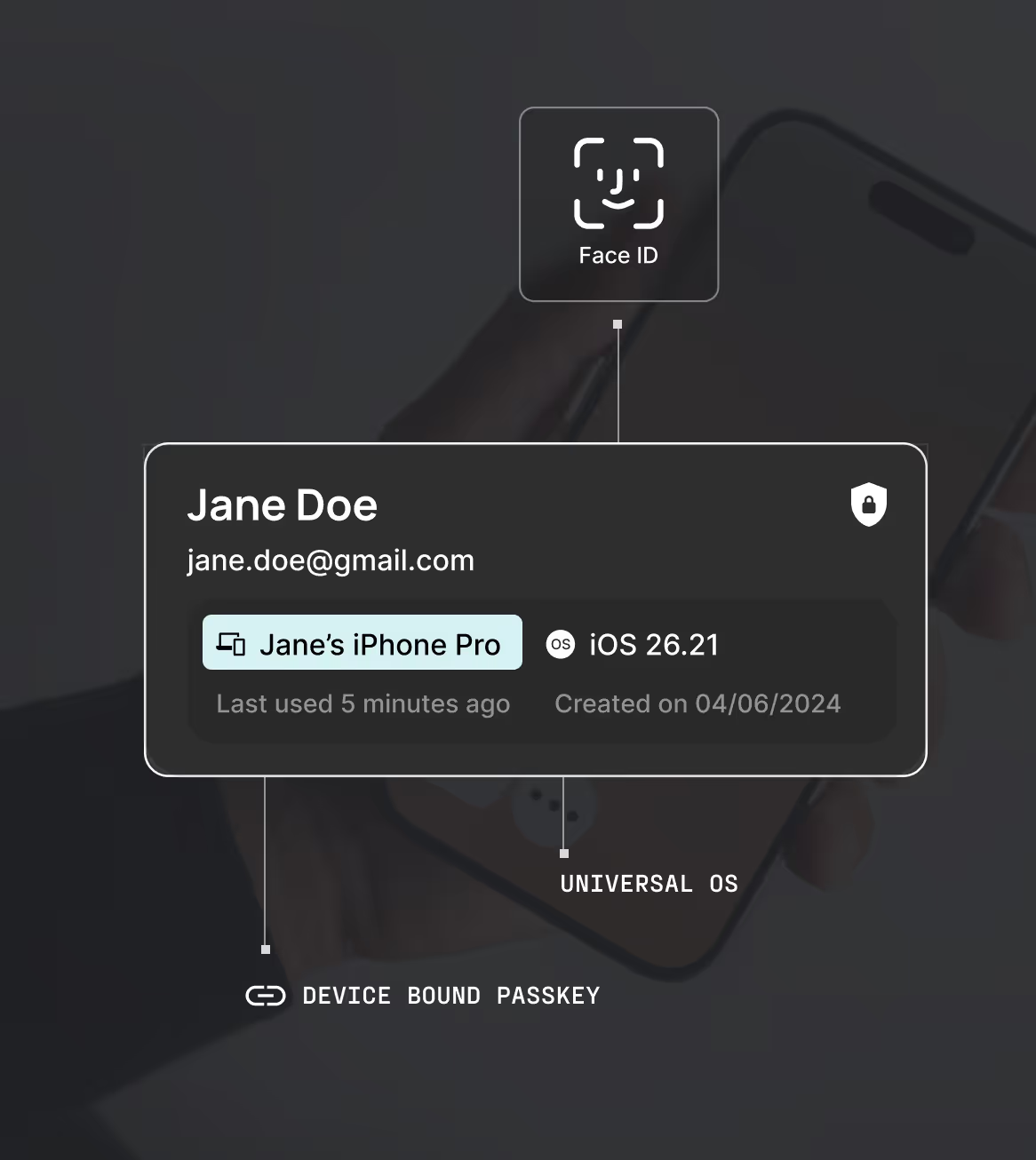
Universal passkeys
Deliver a single, consistent login experience across web and native apps. Our passkeys work on any device or browser, even those that don’t support FIDO2 WebAuthn, ensuring no customer is left behind.
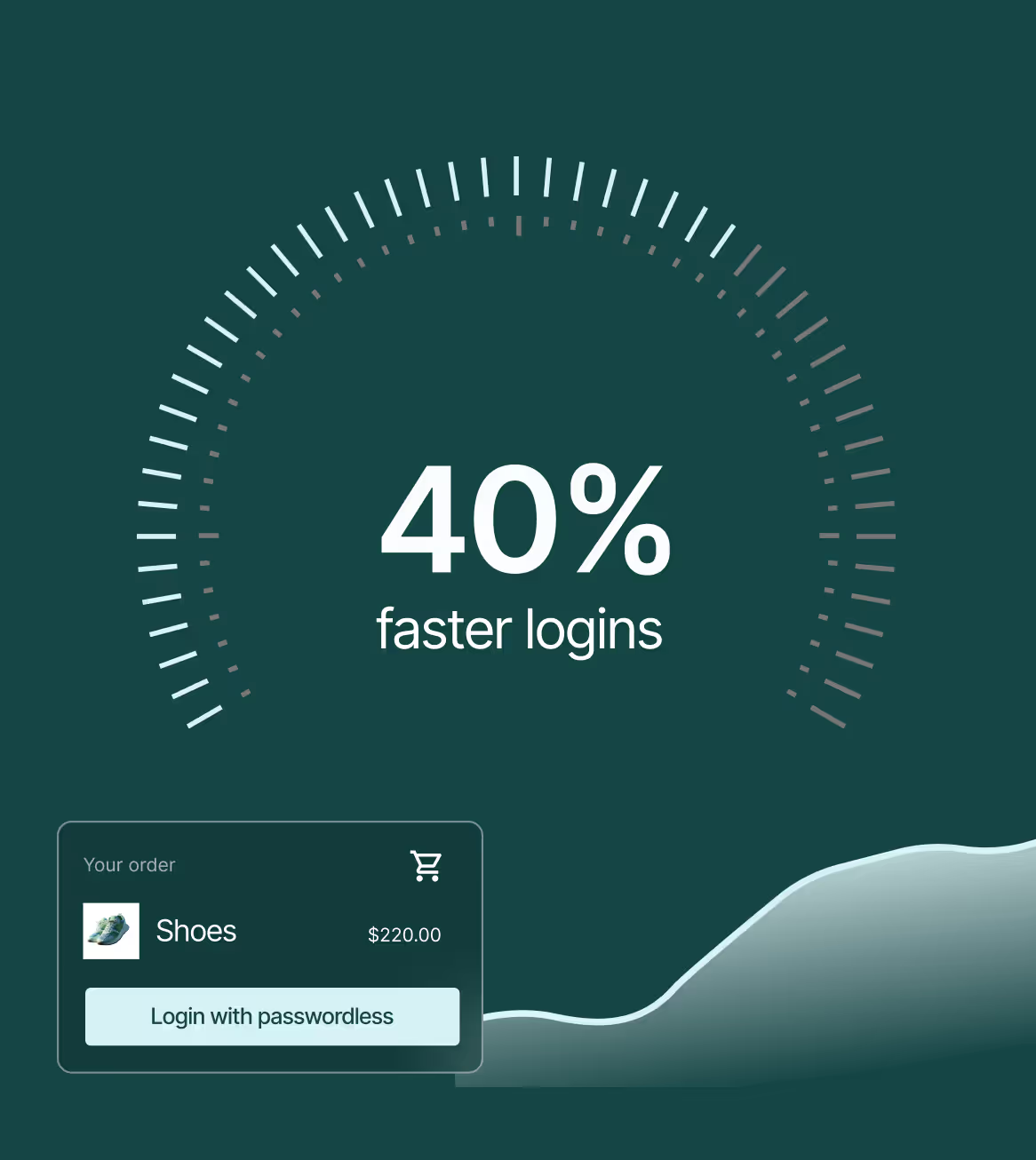
Frictionless user experience
Accelerate conversions and reduce drop off by removing passwords, one time codes, and push notifications from registration, login, and recovery.
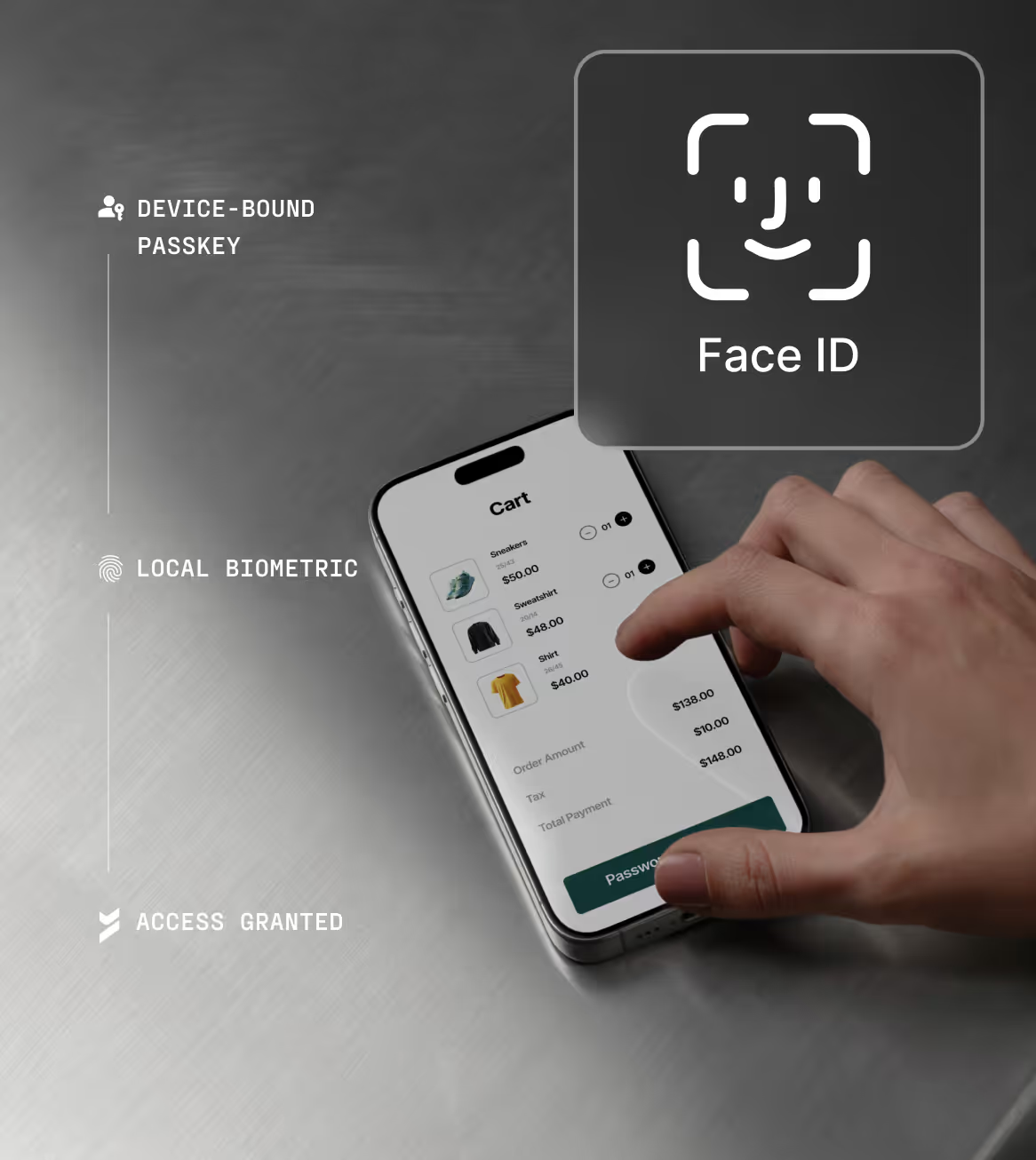
Invisible phishing-resistant MFA
Eliminate account takeover fraud with authentication that is immune to phishing and credential attacks. Every login is protected by two unphishable factors (biometric and private key) without user burden.
Low engineering lift
Deploy in days, not months. Our cloud-native, API-first platform is simple to build on, manage, and scale, with out-of-the-box integrations for major CIAM platforms, easy-to-use SDKs, and hosted options.

Built for the full customer lifecycle
From acquisition to retention, our platform provides the security and user experience needed to grow your business and protect your brand
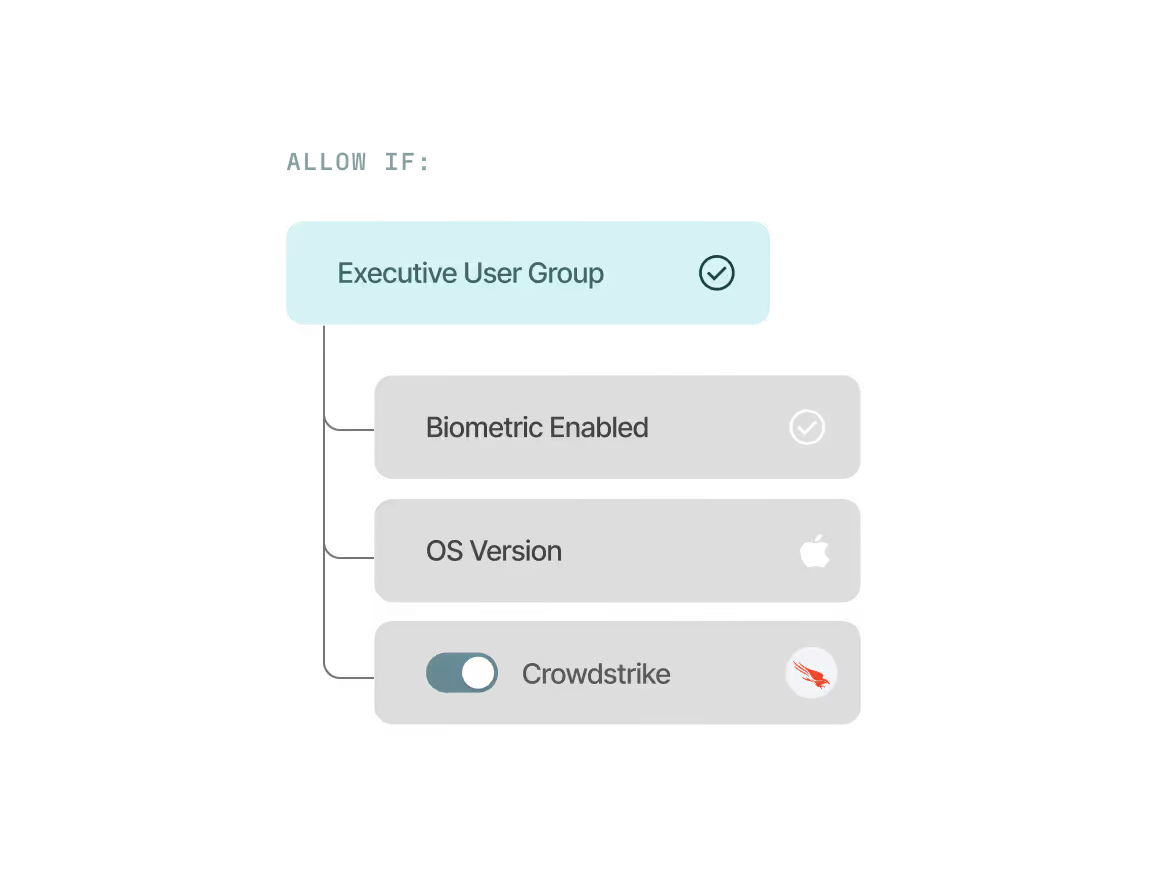
Eliminate account takeover fraud
Protect your customers and your brand from the financial and reputational damage of account takeover. Our unphishable MFA prevents credential-based attacks.
Drive top-line revenue growth
A frictionless user experience is critical to your bottom line. By removing authentication hurdles, you directly increase conversion rates, customer engagement, and lifetime value.

Reduce operational costs
Free up your support teams by completely eliminating password resets, which are a major source of user frustration and wasted operational overhead.
Stop compromising between
security and UX
Legacy customer authentication forces a trade-off. You can have a good user experience or strong security, but not both. Beyond Identity gives you both, without compromise.
Validating both users and devices continuously, as separate
but equally important requirements for risk-based authentication.
Single-point in time authorization of users only, oftentimes using phishable factors that can leave organizations open to risk.
Frictionless
Frictionless, single-step biometric login on the user's own device. No passwords, codes, or second devices.
Frustrating
High friction with passwords, OTPs, push notifications, and secondary devices that cause drop-off.
100% Phish-resistant
Uses device-bound, universal passkeys that cannot be stolen, shared, or replayed.
Vulnerable
Passwords, SMS codes, and push approvals can all be phished or socially engineered.
operation
100% Passwordless
Fully passwordless on any device and browser. No password in the user experience or stored in your database.
Relies on passwords
Password-dependent. Passwords remain a core attack vector and source of support burden.
Universal
Works on any browser, device, or app, even those that don't support FIDO2 WebAuthn.
Limited
Inconsistent experiences across platforms; some users left behind.
Low lift
Cloud-native, API-first platform with out-of-the-box CIAM integrations, easy-to-use SDKs, and hosted options.
High maintenance
Complex to build, manage, and scale across multiple authentication methods.
WebAuthn Capabilities and Limitations

Are Passkeys 2FA?


