Our mission is to protect the livelihood of our customers
Join Beyond Identity's partner ecosystem to deliver the only access management platform eliminating identity-based threats, enabling true zero trust security with phishing-resistant MFA and risk-based device trust.
Collaborative partnerships
We win with people and develop collaborative opportunities built on trust and transparency.
Shared growth
We invest in our partners to grow our joint businesses and drive relationships forward.
High-value program
Our three-tier program delivers high rewards and empowers partners to provide exceptional value as we enable organizations to eliminate risk and enable business growth.
Who we work with
.svg)
Solution Providers/VARs
Expand your security portfolio and meet customers compliance requirements with a cutting-edge IAM solution that is both secure and delightful for end-users.
.svg)
Managed Service Providers
Offer advanced identity and device security services to your customers. Extend visibility and control to unmanaged BYOD devices with a solution that ensures security controls are in place and active.
.svg)
Distribution Partners
Capitalize on zero trust security solution with aggressive rebates, market development funds, and deal protection that ensures partner profitability.
.svg)
Global Systems Integrators
Gain top tier support and value from a security solution that users love, admins appreciate, and security teams cry for.
Partner first channel program
Spend smarter, lower your bills, get cashback on everything you buy, and unlock credit to grow your business.
Discounts and Incentives
Technical Excellence
Marketing Success
Sales Support and Training

Our advantage
Eliminate your client's biggest attack vector while accelerating productivity with our Security-first Access Management Platform.
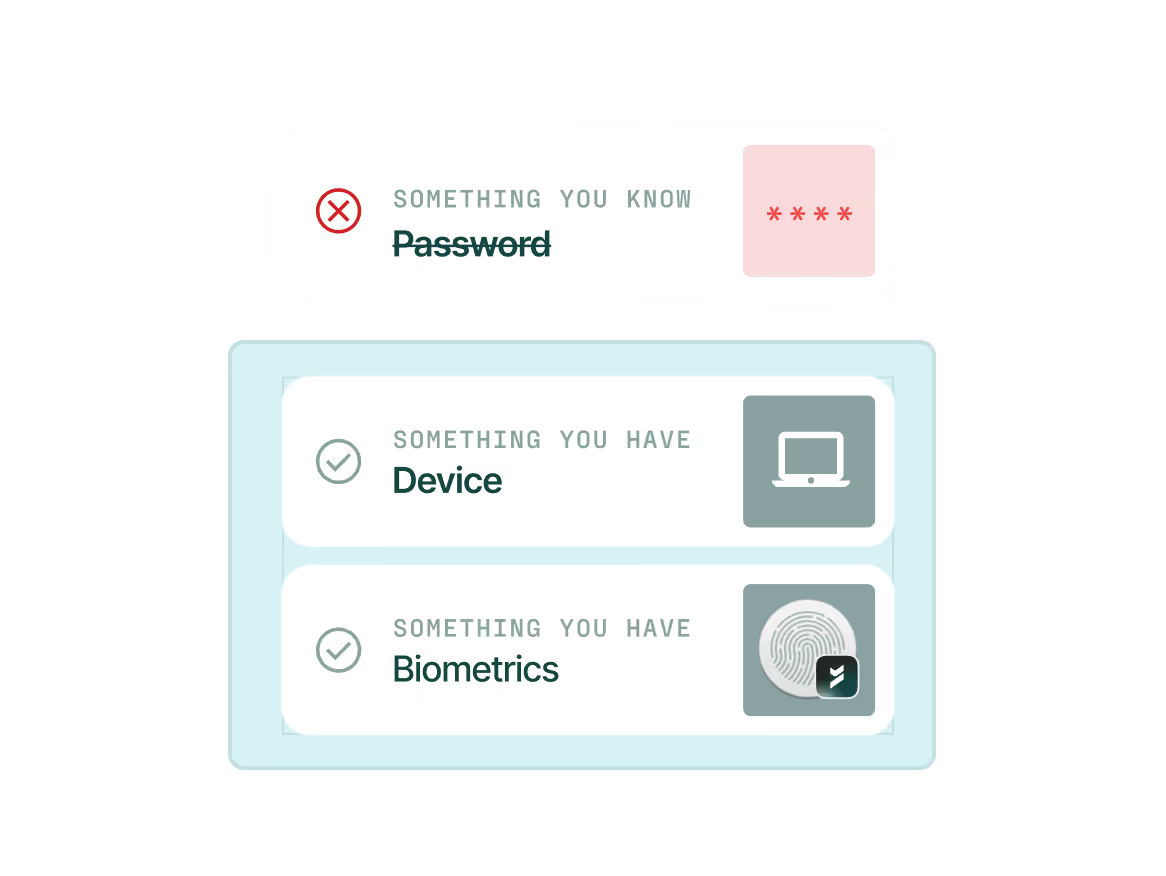
Passwordless and always phishing-resistant
The only AM platform engineered to categorically prevent identity-based threats. We never fall back to phishable factors and provide a single-device delightful, passwordless user experience.
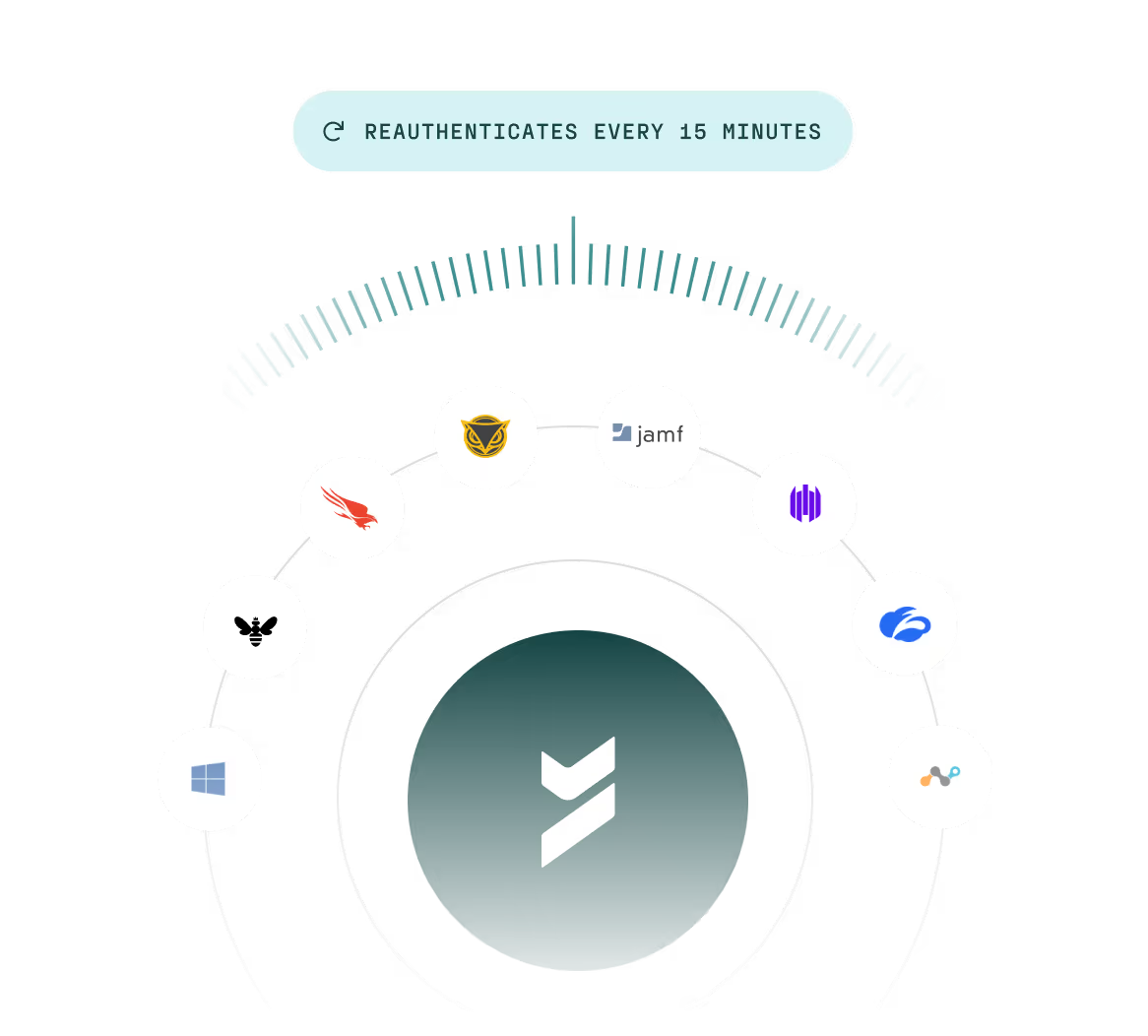
Continuous risk-based authentication
Turn every risk signal into a real-time access decision that is continuously evaluated at the point of access and during active sessions.

Device security & precise policy enforcement
Ensure access is only granted to trusted and secure devices, managed or unmanaged. Easily configure customizable risk-based policies precisely tailored to your customers' business and compliance requirements.




.svg)


















.avif)
.avif)



.avif)






.avif)

