get rid of passwords
Say goodbye to passwords
single device authentication
no push notifications
no one-time codes
.avif)
4 Critical Points of Failure
Existing solutions fall back on passwords
One-time codes, push notifications, and magic links don’t remove the password. Go passwordless, across all your devices and for anyone that accesses your systems.
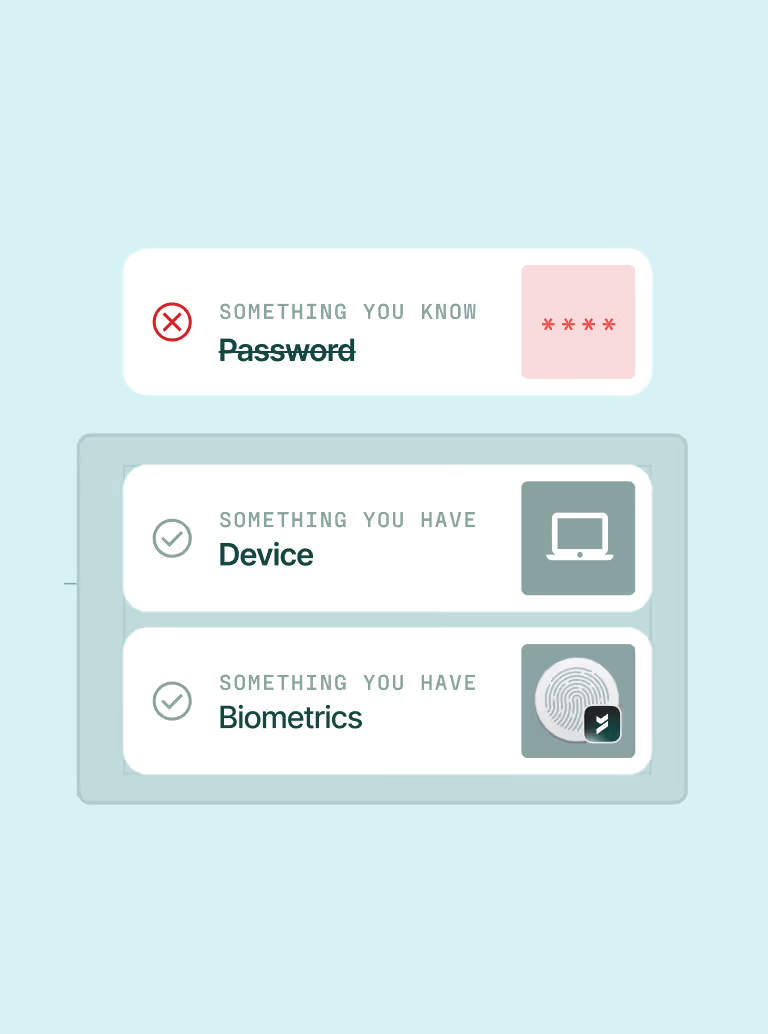
Requires a second device
Adds complexity for users and opportunity for attackers. Methods like SMS or TOTP are easily phished or replayed.
Password remains as the first factor
Credentials are stealable, phishable, and reusable.
Limited OS support
130% spike in cyberattacks targeting Linux users. (Linux Security, May 2024)
Not continuous
Lack of continuous posture leaves you blind to emerging threats.
Phishing accounted for
of unauthorized access into web applications. (Verizon DBIR, 2024)
Passwordless Without Compromise
Accelerate user productivity with a delightful passwordless experience on every device.
.png)
Universal OS support
Seamless UX on any device, operating system, or browser. Covers endpoints and SSO logins.
Always passwordless
Passwords are easily stolen and reused across sites, making them a prime target for attackers.
.png)
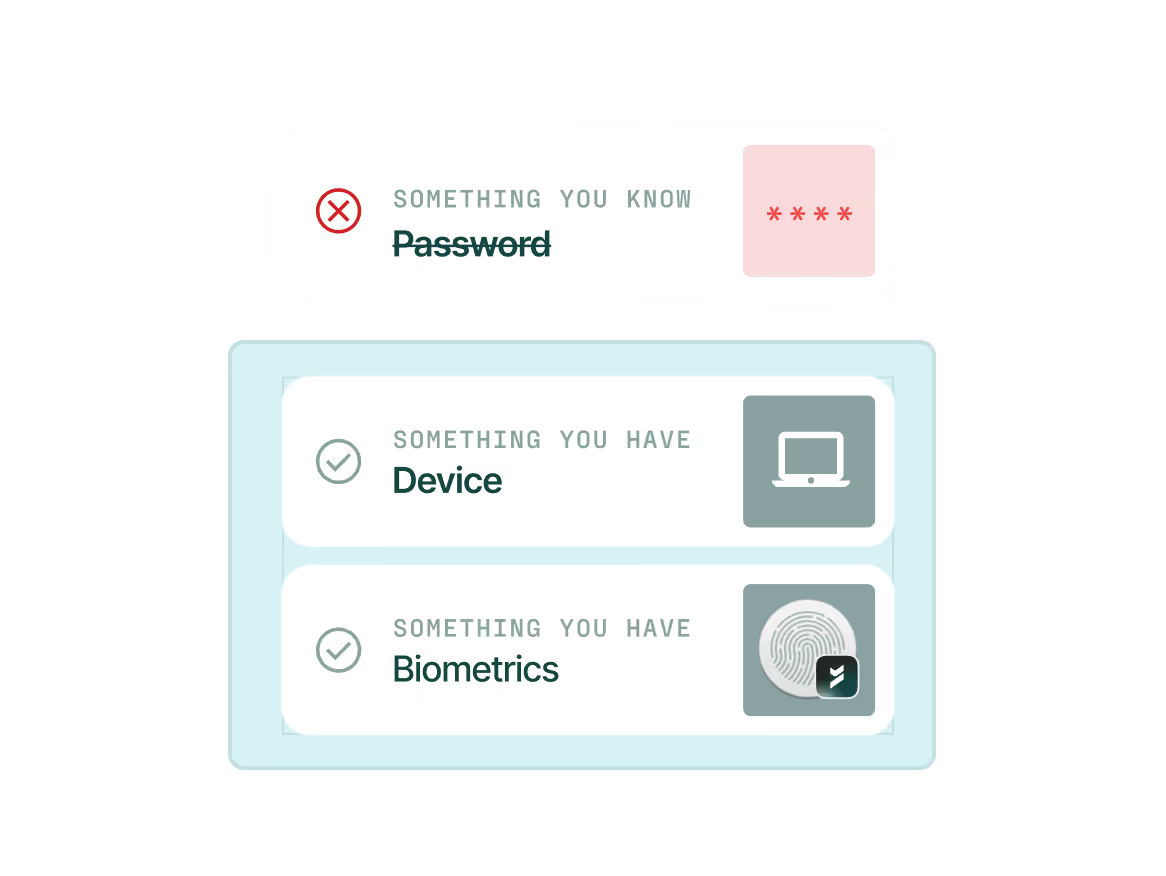
Device-bound passkeys
Device-bound passkeys stay locked to the device, while traditional credentials are stealable, phishable, and reusable.
Maximum security.
Unmatched UX.
Secure access using device-bound passkeys removes the need for a second device, push notifications, or OTPs.



.avif)

.avif)
.avif)
.avif)


.avif)

.avif)



.avif)

.avif)


