Make AI impersonation fraud impossible
Ensure digital communication is with verified users, on a trusted devices with RealityCheck.

Detection is unreliable
Don’t try to detect deepfakes—make them irrelevant.
Prevent AI fraud before secrets are shared
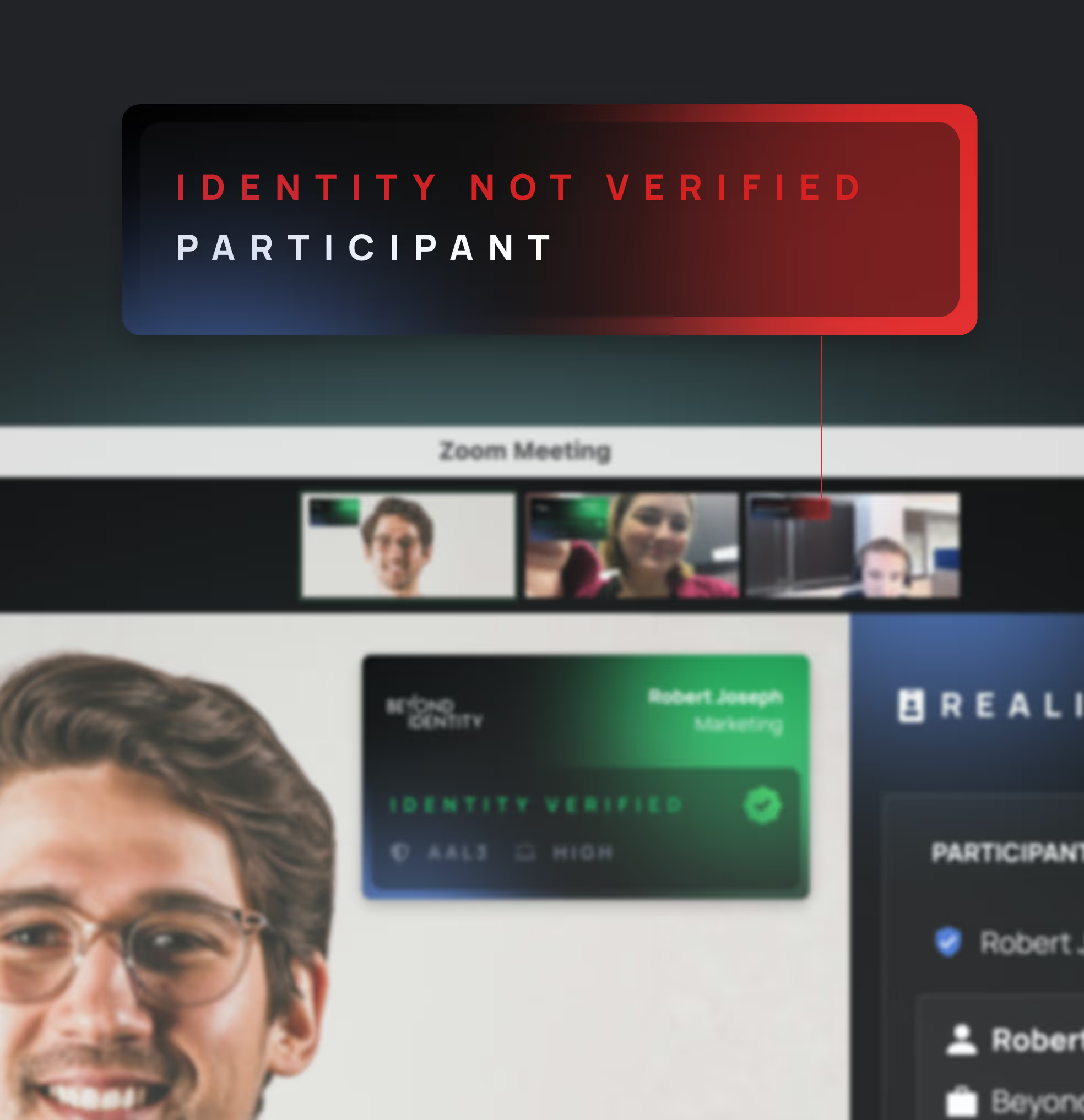
Verify both the user and the device behind the camera at login and during the meeting or chat.
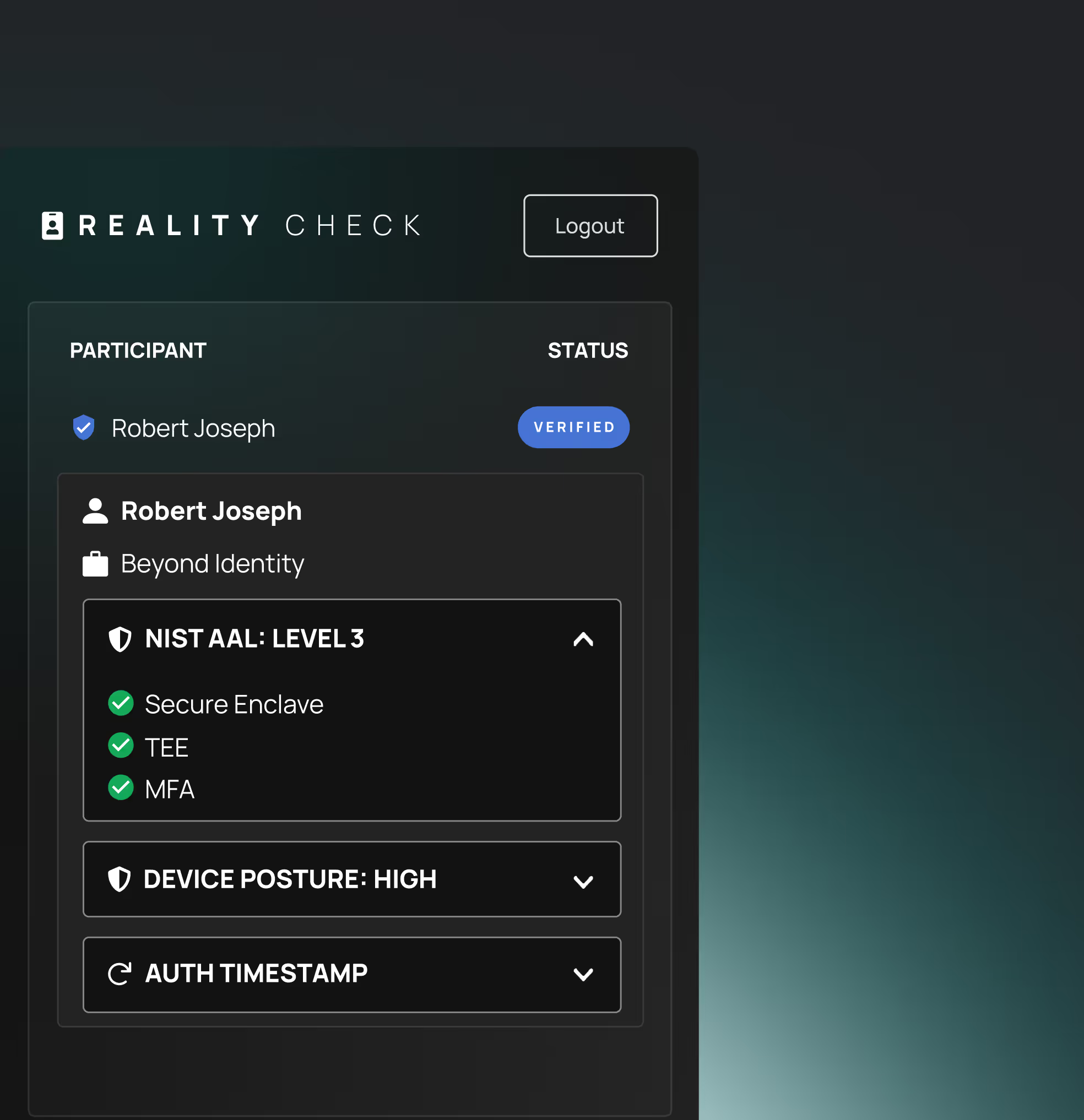
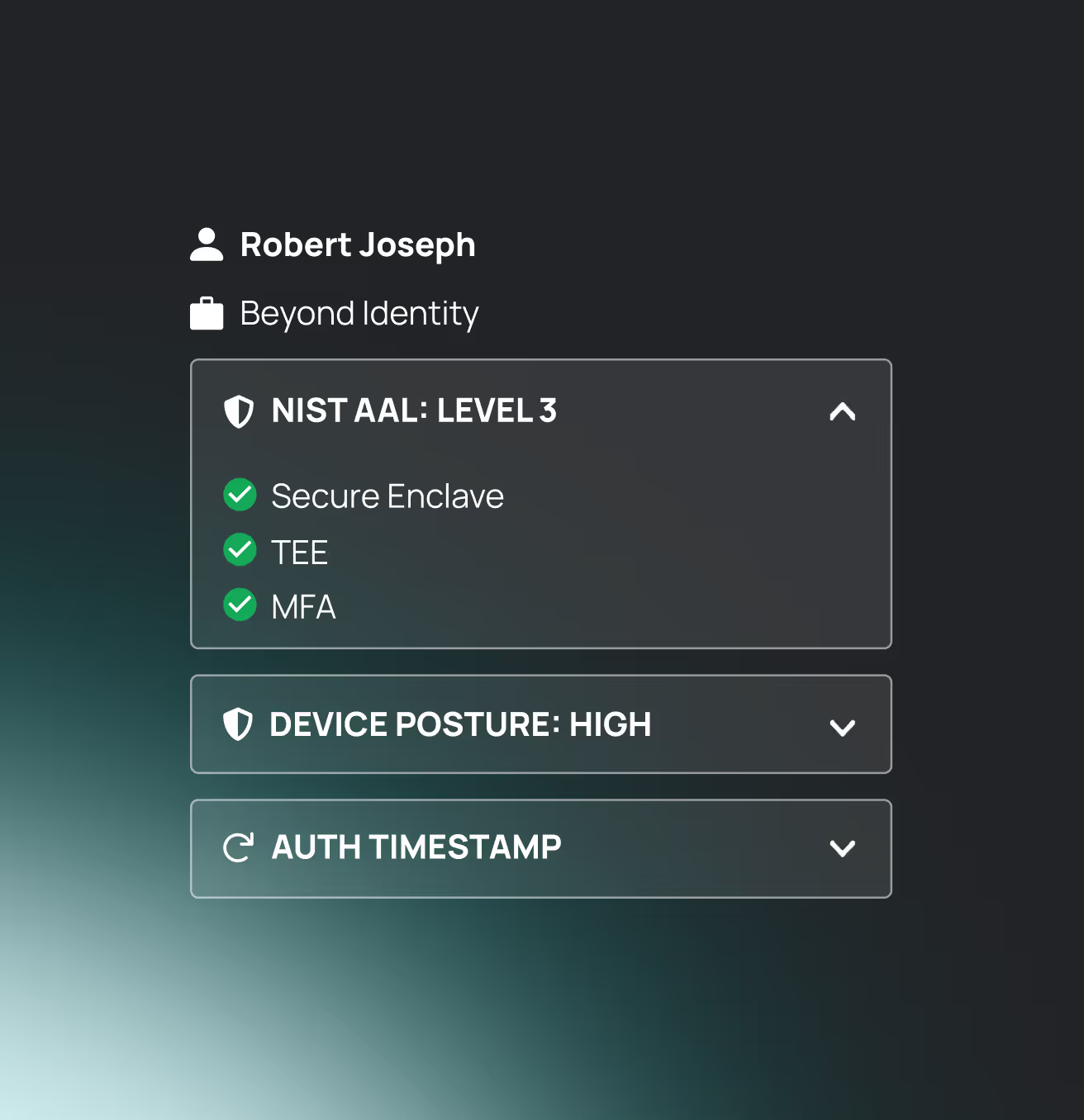
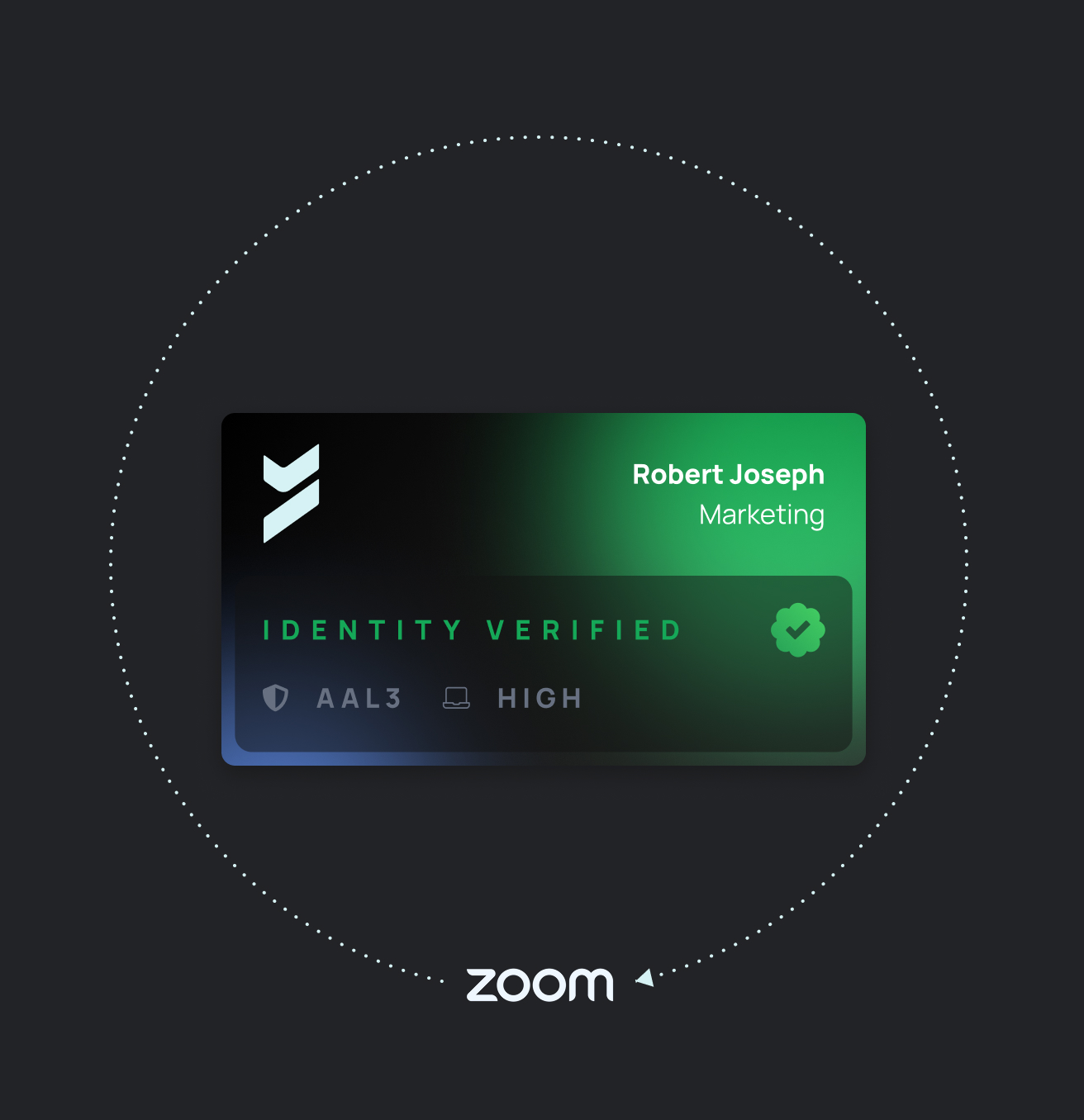
Verified identity, verified posture, verified presence
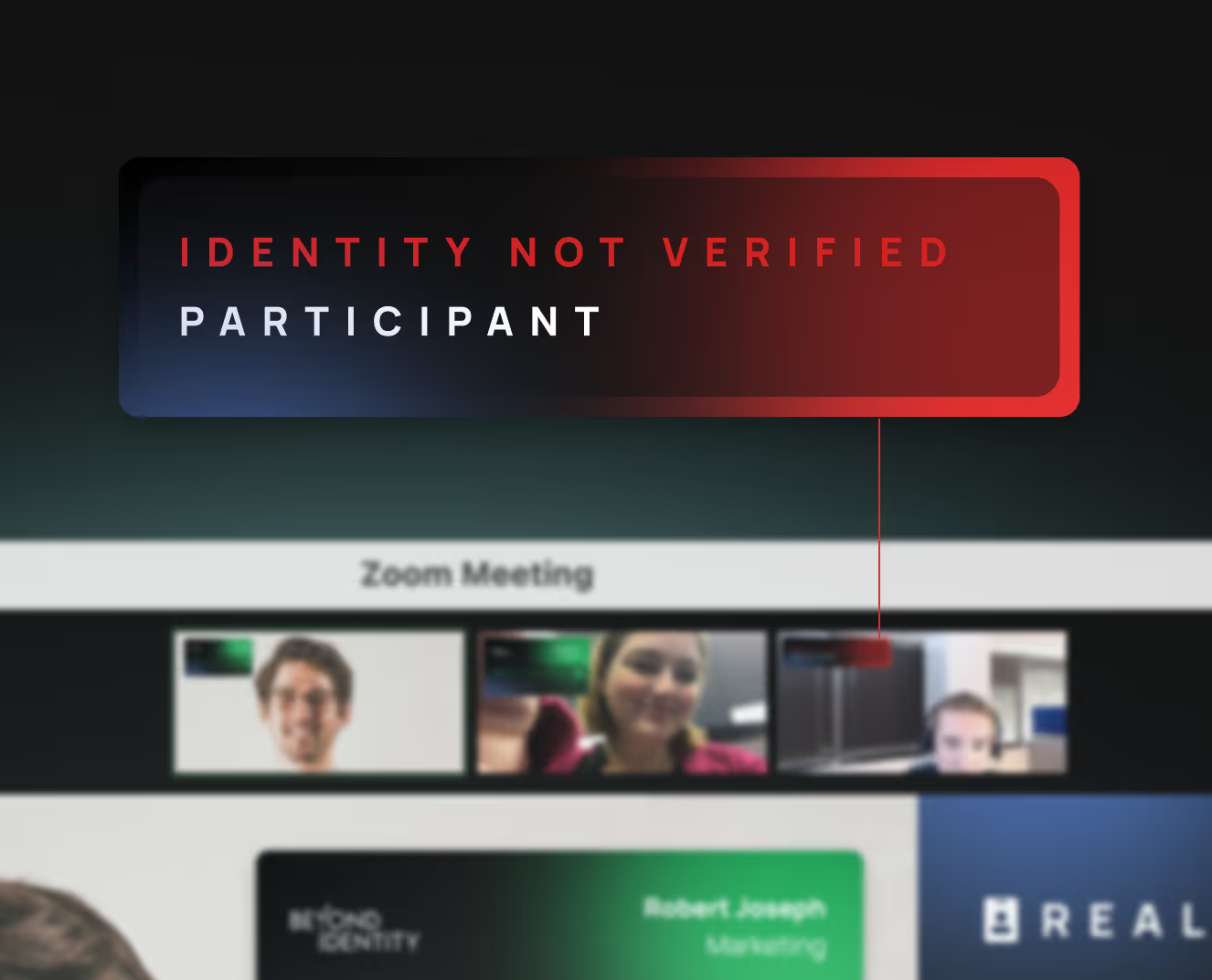
Deepfakes, impersonators, and unverified callers get flagged before they can say a word.
Remove suspicious users
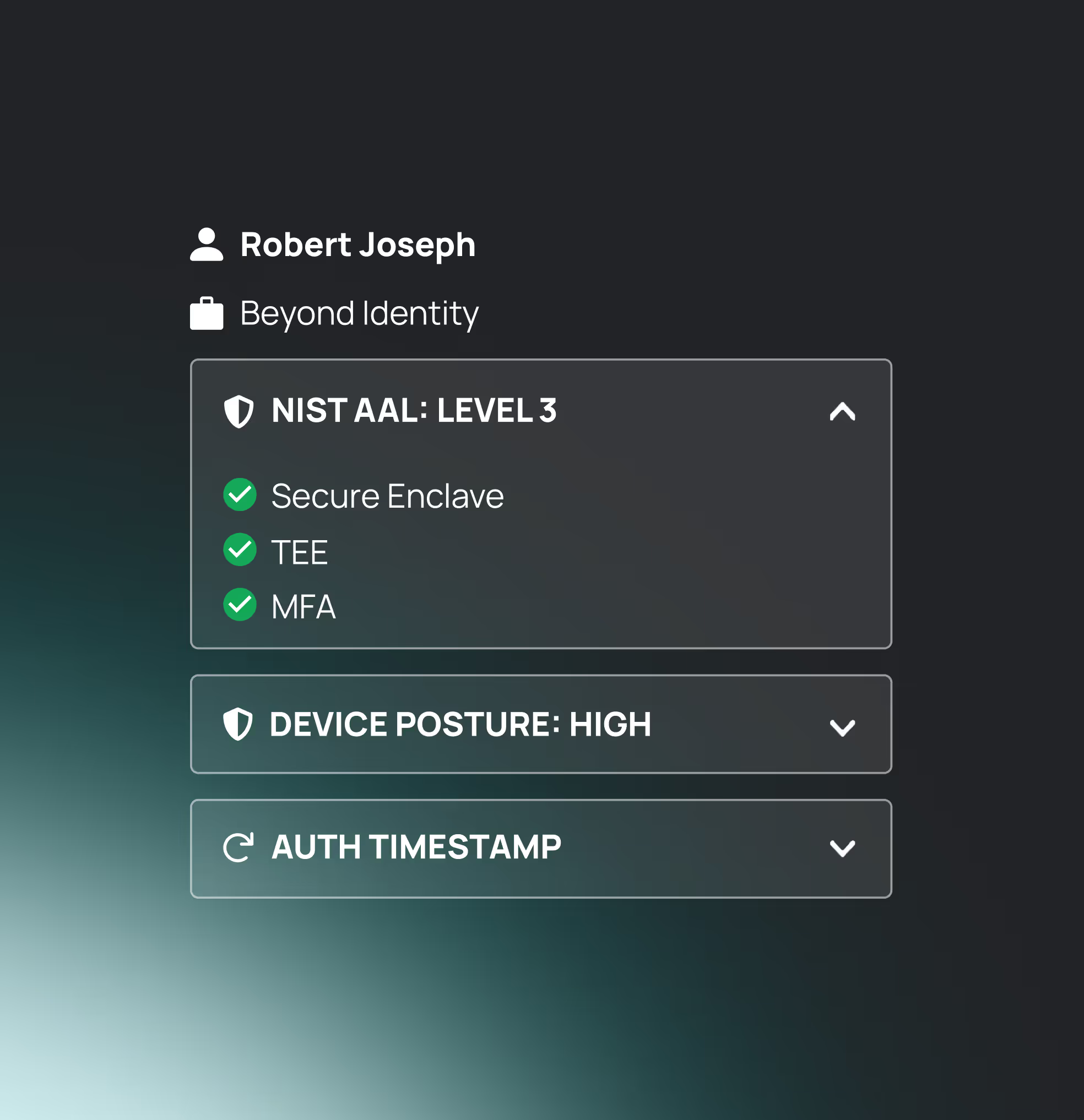
Use insights from the tamperproof risk signals panel to revoke access for unauthenticated participants, before they cause damage.

Why Beyond Identity?
Other deepfake detectors leave organizations exposed to modern threats. Beyond Identity’s RealityCheck solution blocks those threats at the source.
Validating both users and devices continuously, as separate
but equally important requirements for risk-based authentication.
Single-point in time authorization of users only, oftentimes using phishable factors that can leave organizations open to risk.
Frictionless
Frictionless, single-step biometric login on the user's own device. No passwords, codes, or second devices.
Frustrating
High friction with passwords, OTPs, push notifications, and secondary devices that cause drop-off.
100% Phish-resistant
Uses device-bound, universal passkeys that cannot be stolen, shared, or replayed.
Vulnerable
Passwords, SMS codes, and push approvals can all be phished or socially engineered.
operation
100% Passwordless
Fully passwordless on any device and browser. No password in the user experience or stored in your database.
Relies on passwords
Password-dependent. Passwords remain a core attack vector and source of support burden.
Universal
Works on any browser, device, or app, even those that don't support FIDO2 WebAuthn.
Limited
Inconsistent experiences across platforms; some users left behind.
Low lift
Cloud-native, API-first platform with out-of-the-box CIAM integrations, easy-to-use SDKs, and hosted options.
High maintenance
Complex to build, manage, and scale across multiple authentication methods.
Hiring Fraud Is Costing You More Than You Think
Inside the CrowdStrike 2025 Global Threat Report: AI as a threat “force multiplier”
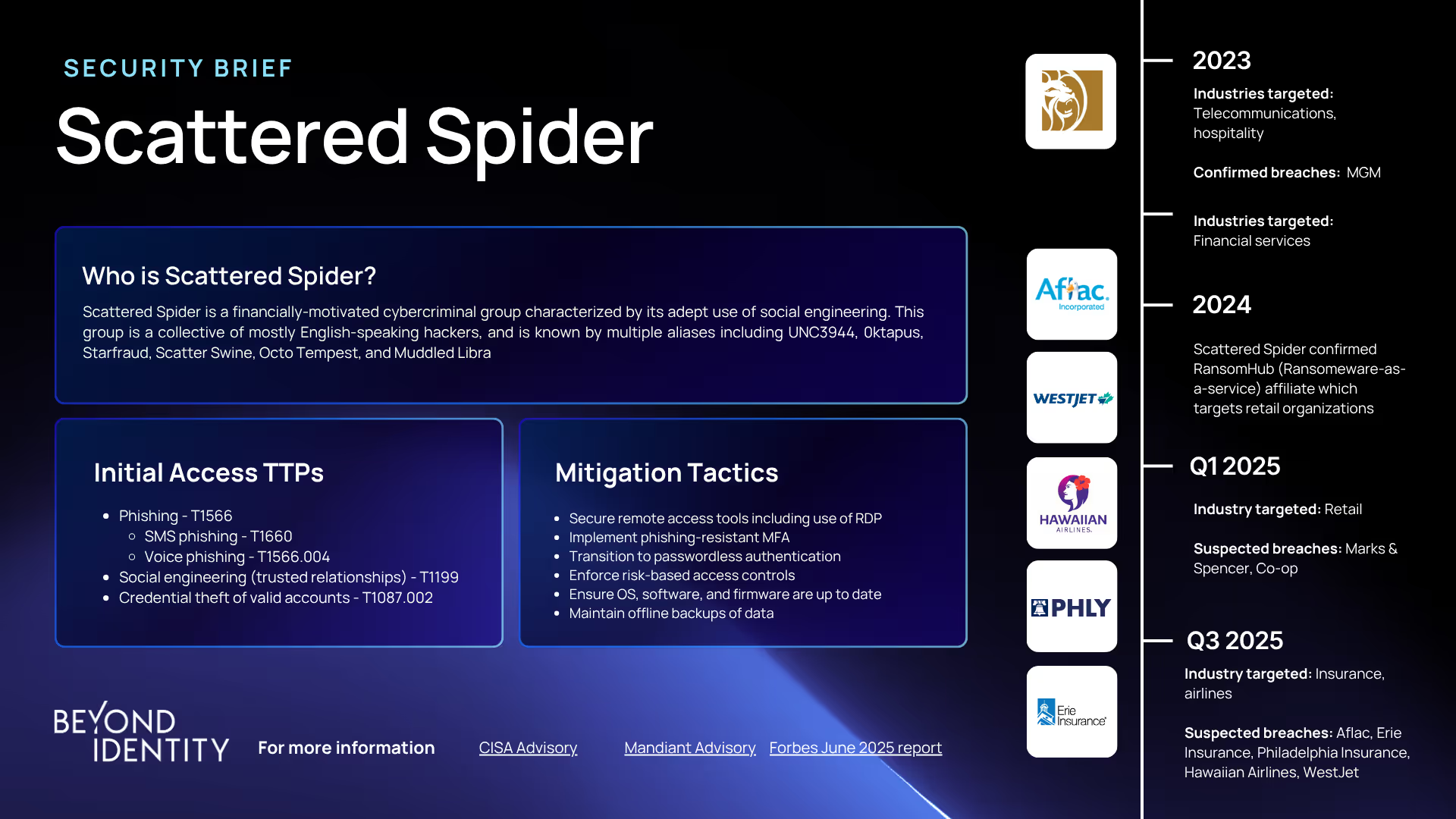
Scattered Spider: How to Effectively Defend Against This Aggressive Threat