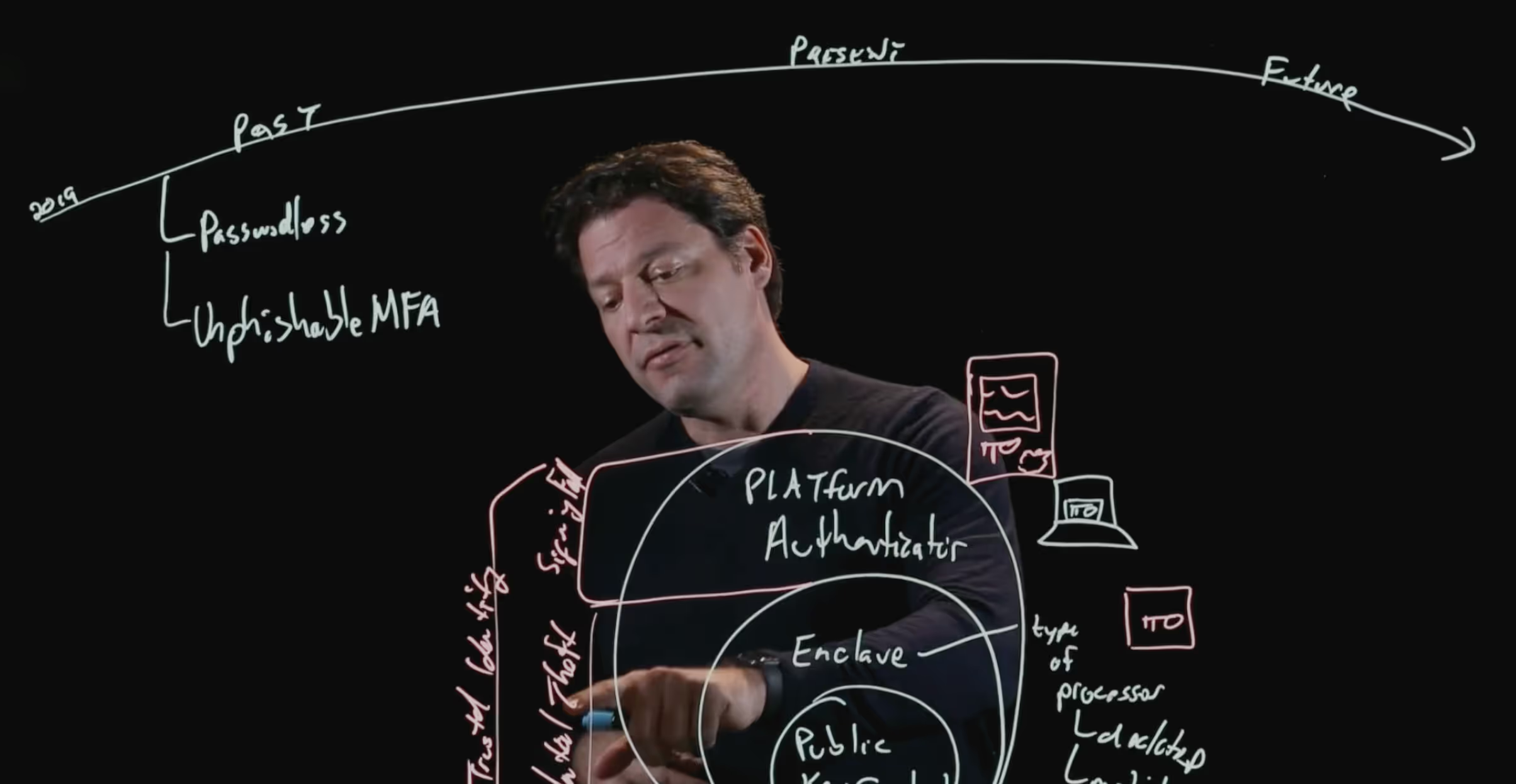
Zero trust maturity
Achieve Zero Trust with user & device verification
Secure all devices
universal os
Authenticate continuously
.avif)

4 Critical Points of Failure
No visibility into device posture
Traditional IAM tools rely on phishable credentials that can be stolen by insecure devices, leading to unauthorized access to your systems.
Only authenticates at login
Users and devices change over time and must be continuously authenticated based on risk, even during open sessions. Legacy providers don’t continuously monitor risk signals.
Relies on phishable factors
Legacy MFA providers rely on weak, phishable factors like passwords and OTPs that are easily stolen or bypassed. Additionally, their fallback methods use insecure credentials.
Lacks integrations
Traditional identity providers weren’t built for zero trust — they operate in isolation and don’t share risk data across your security stack.
of organizations worldwide have fully or partially implemented a zero-trust strategy. (Gartner)


.avif)

.avif)
.avif)
.avif)


.avif)

.avif)



.avif)

.avif)


