The only SSO built to eliminate identity risk
Most SSO's are built for productivity, not security. Introducing an SSO that prevents identity and device-based attacks with phishing-resistant, device-bound technology.
.avif)
Eliminate your biggest attack vector
Remove phishable credentials and block access from non-compliant devices.
Least privilege for your most critical apps
Define precise, app-by-app access controls based on roles and device health across every platform and OS.
Compliant by default, preventive by design
Meet Zero Trust and phishing-resistant mandates from NIST, CISA, and others without extra complexity.
Zero productivity tradeoffs
Users authenticate with a single gesture. No codes. No fallback flows. No second devices.

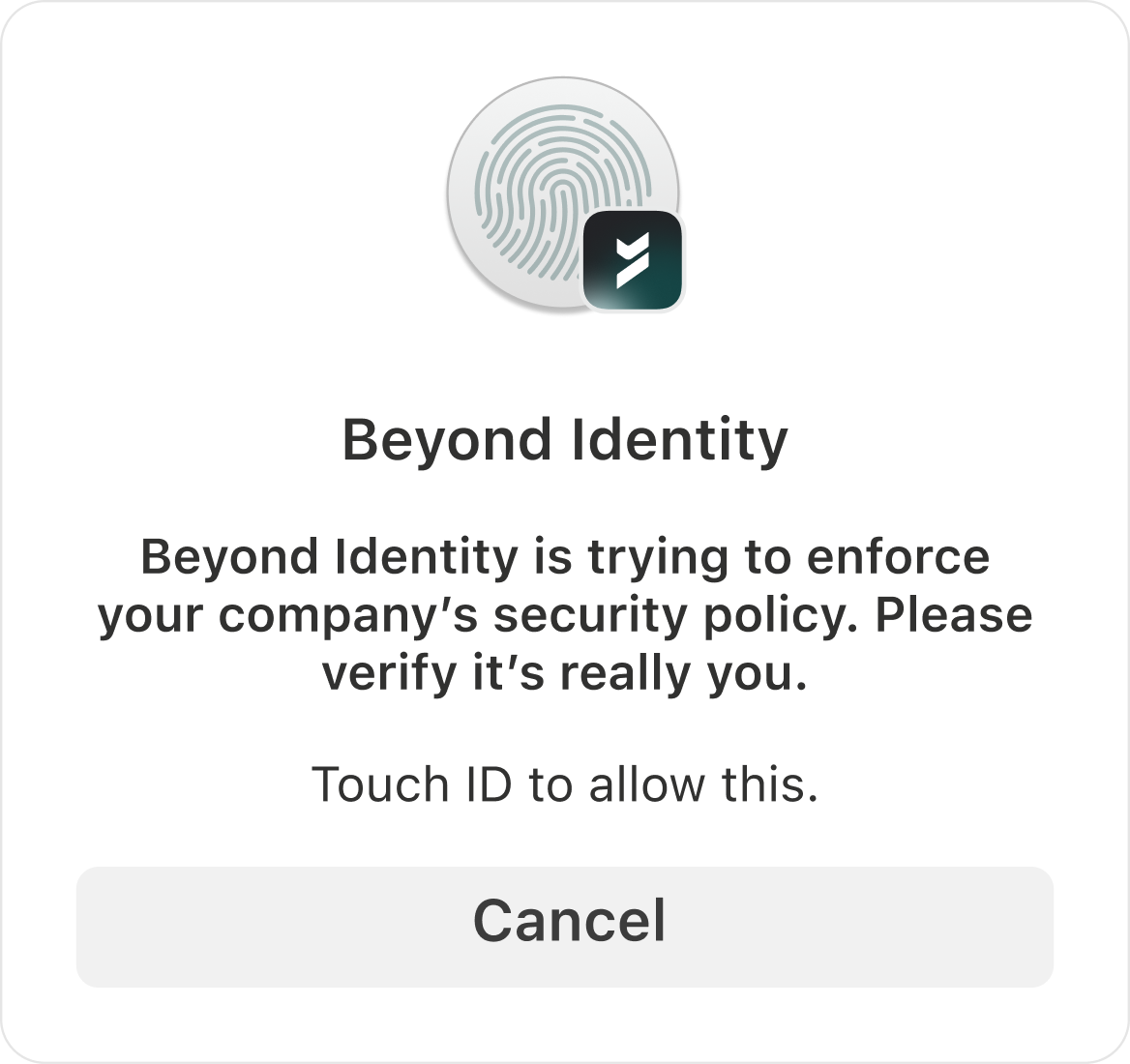
Single-device, passwordless authentication
Authenticate users with phishing-resistant, device-bound credentials. No passwords, push notifications, or OTPs to intercept.
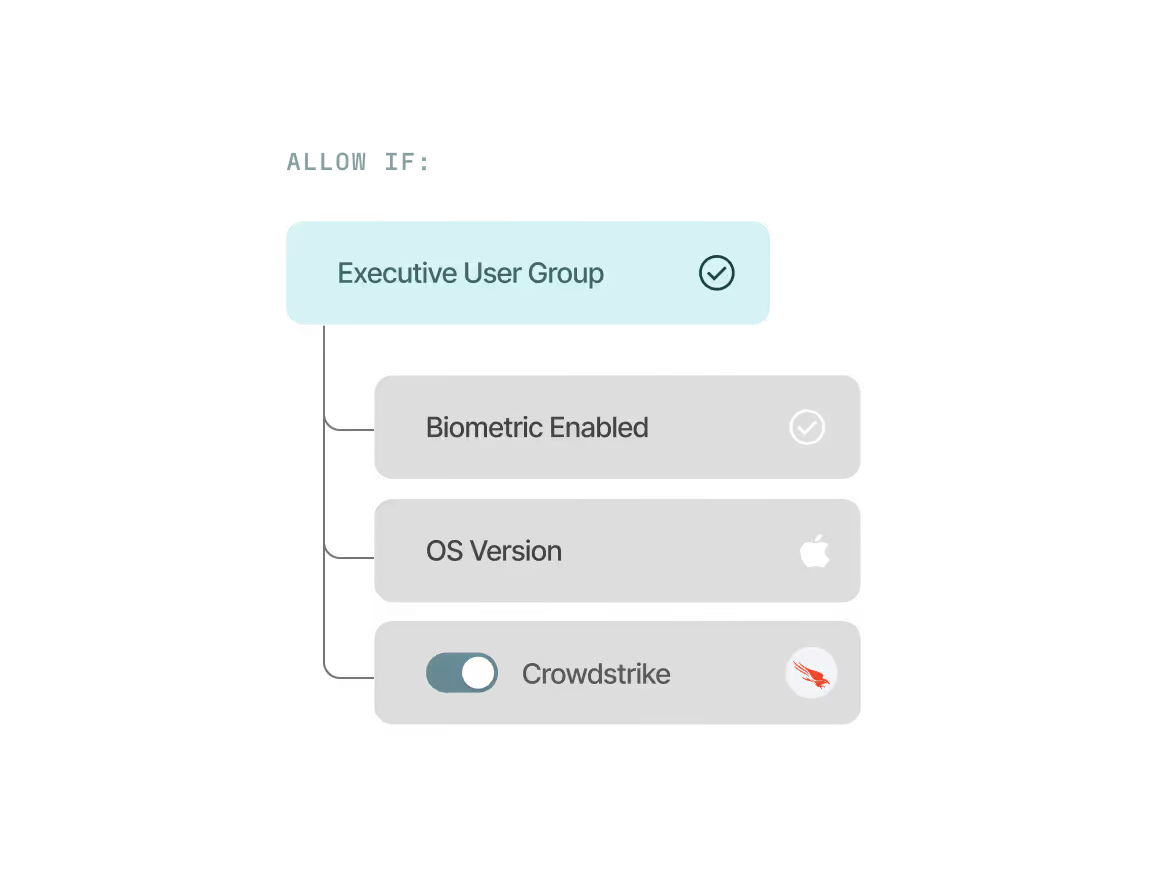
Fine-grained per-app policy enforcement
Set stricter access policies for critical apps like codebases, IP documents, and financial apps so only the right user on the right device can gain and maintain access.
.avif)
Built-in device trust
Block access from untrusted devices based on security posture: disk encryption, EDR, firewall, OS version, and more. No device left behind, secure your entire fleet including unmanaged devices.

Always-on risk enforcement
Authentication doesn't stop at login. Continuously evaluate device and user risk and automatically revoke access when security posture changes.

Secure integration with your stack
Block access instantly when your EDR, MDM, or ZTNA flag a risk on the device.
Why Beyond Identity?
Traditional SSO providers leave organizations exposed to modern threats. Beyond Identity’s Secure SSO solution blocks those threats at the source: authentication.
A secure-by-design, easy-to-use SSO that makes identity-based attacks impossible. Delivers continuous authentication for users and devices, fine-grained risk-based policies, seamless integration with your security stack—and is fully passwordless and phishing-resistant.
Legacy IT solutions designed to provide access to data and systems. Often based on single-point-in-time authorization that primarily focuses on users only (not devices), using methods that can be susceptible to phishing, such as passwords and tokens.
Seamless
Passwordless and single-device — no OTPs, no push, no password prompts.
Frustrating
Requires passwords, MFA prompts, and often a second device.
Secure-by-design
Can operate as a standalone secure access layer or augment SSO/IAM for hardened authentication.
Vulnerable
Weak default security posture; often requires additional protection layers.
scope
Users and devices
Authenticates both users and devices continuously.
Users only
Validates user identity only. Devices are unverified.
100% Phishing-resistant
Only ever uses phishing resistant factors to authenticate, including biometric checks and hardware-protected keys.
Exposed
Commonly relies on phishable factors (SMS, OTP, Push).
validation
Continuous
Continuously evaluates device health and configuration in real time.
Sporadic
Performs one-time or no device checks.
privileges
Just-in-time access
Enforces just-in-time access — permissions are granted only when needed, then revoked.
Persistent privileges
Grants persistent access that increases lateral movement risk.
Active
Uses native signals (e.g., OS status, firewall) and third-party risk inputs to revoke access mid-session.
Passive
Revocation is delayed or dependent on periodic polling.
enrichment
Collaborative
Bi-directional data sharing with your EDR, MDM, and ZTNA; blocks risky logins based on real-time integrated risk signals.
Siloed
Poor visualization, shallow integrations, limited signal reuse.
defense
Connections and in-display
Prevents unauthorized devices from joining comms platforms and visually certifies user identity.
Connections only
Cannot verify live participant identity; accepts any authenticated connection.
management
Security-first
Secure-by-design and auto-syncs with your directories for seamless JML operations.
Simple
Bolt-on provisioning tools create workflow gaps and security blind spots.
Dynamic
Continuously scans managed and unmanaged devices for misconfigurations and anomalies.
Immature
Limited detection, especially on unmanaged devices.
Secure Desktop Access with Beyond Identity and YubiKeys
Combat AI Impersonation Fraud with RealityCheck
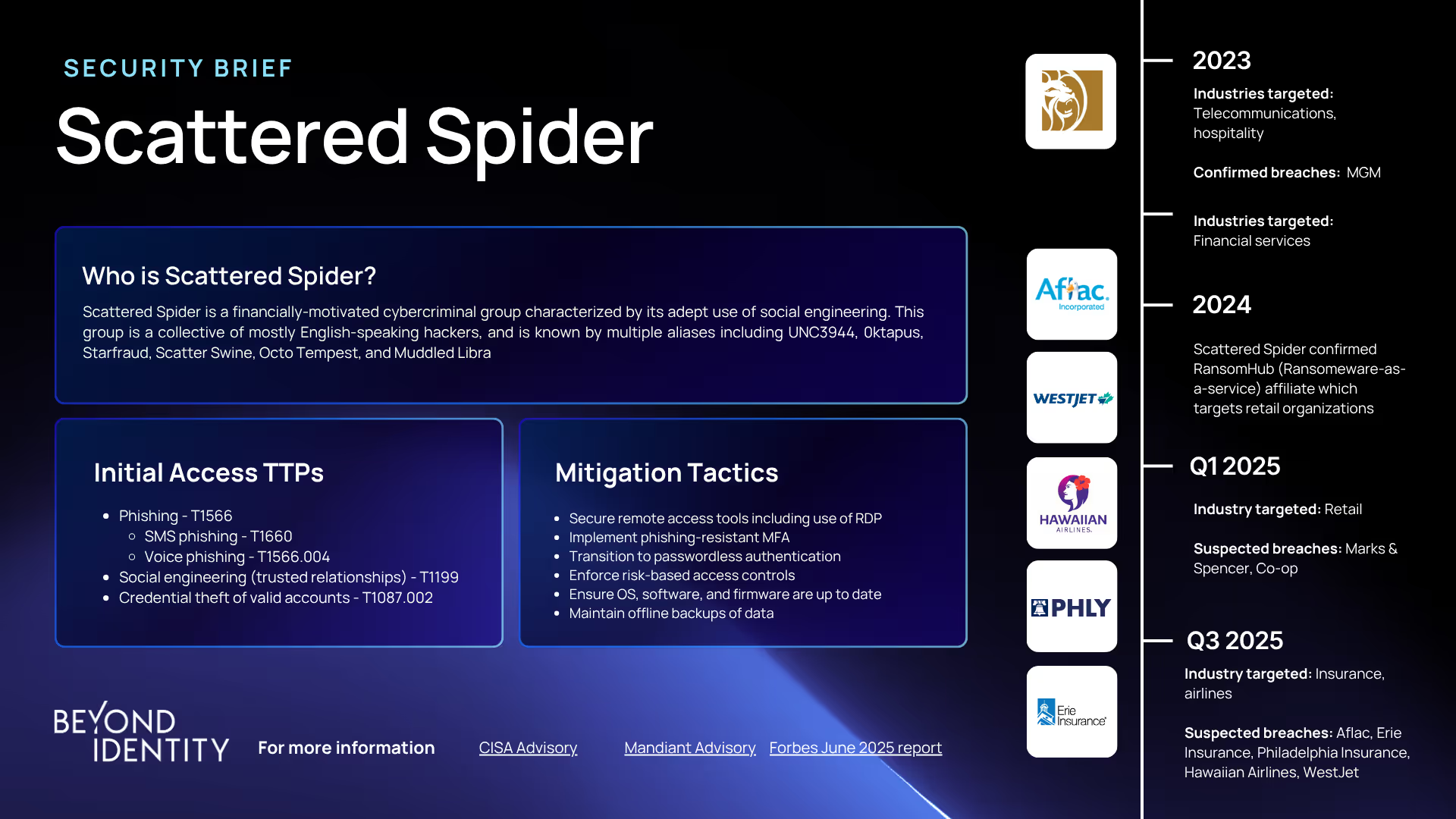
Scattered Spider: How to Effectively Defend Against This Aggressive Threat