ELIMINATE IDENTITY-BASED ATTACKS
Eliminate your biggest source of security risk
Eliminate phishing
eliminate mfa bypass
eliminate credential theft
.avif)
4 Critical Points of Failure
Phishable factors
Credentials are stealable, phishable, and reusable.
Fallback to weak factors
Methods like SMS or TOTP are easily phished or replayed.
No device security control
Granting access to devices that fall out of compliance poses a direct risk to your organization.
Not continuous
The #1 identified gap in Zero Trust strategy is the ability to authenticate users and devices on an ongoing basis. - (Fortinet, 2022)
Phishing accounted for
of unauthorized access into web applications. (Verizon DBIR, 2024)
Make identity-based attacks impossible
Go beyond phishable factors, weak credentials, and shared secrets. Beyond Identity provides phishing-resistant MFA, without falling back to legacy technology, on every device. Your defense is only as strong as your weakest link.
.png)
Integrate risk signals from your security stack
Leverage a wide array of risk signals from your security tools to make access decisions.
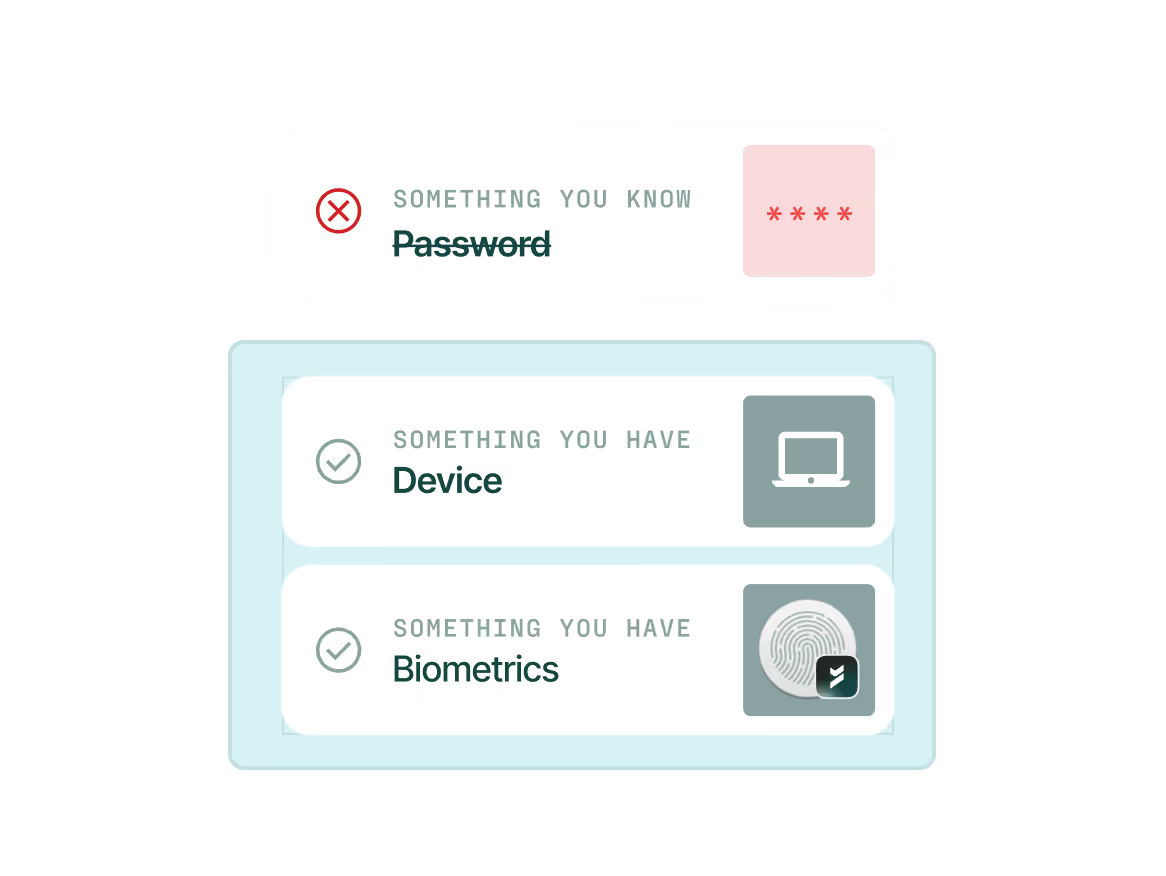
Prevent phishing
Secure access using passwordless, phishing-resistant MFA that never falls back to phishable factors.
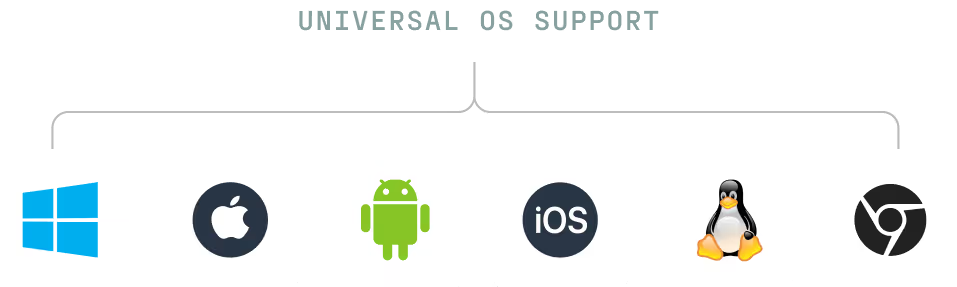
Secure all devices, any OS
Protect your entire fleet, including BYOD, contractor, and unmanaged devices.

Authenticate continuously
Continuously check real-time user and device posture to identify and stop threats as they emerge.
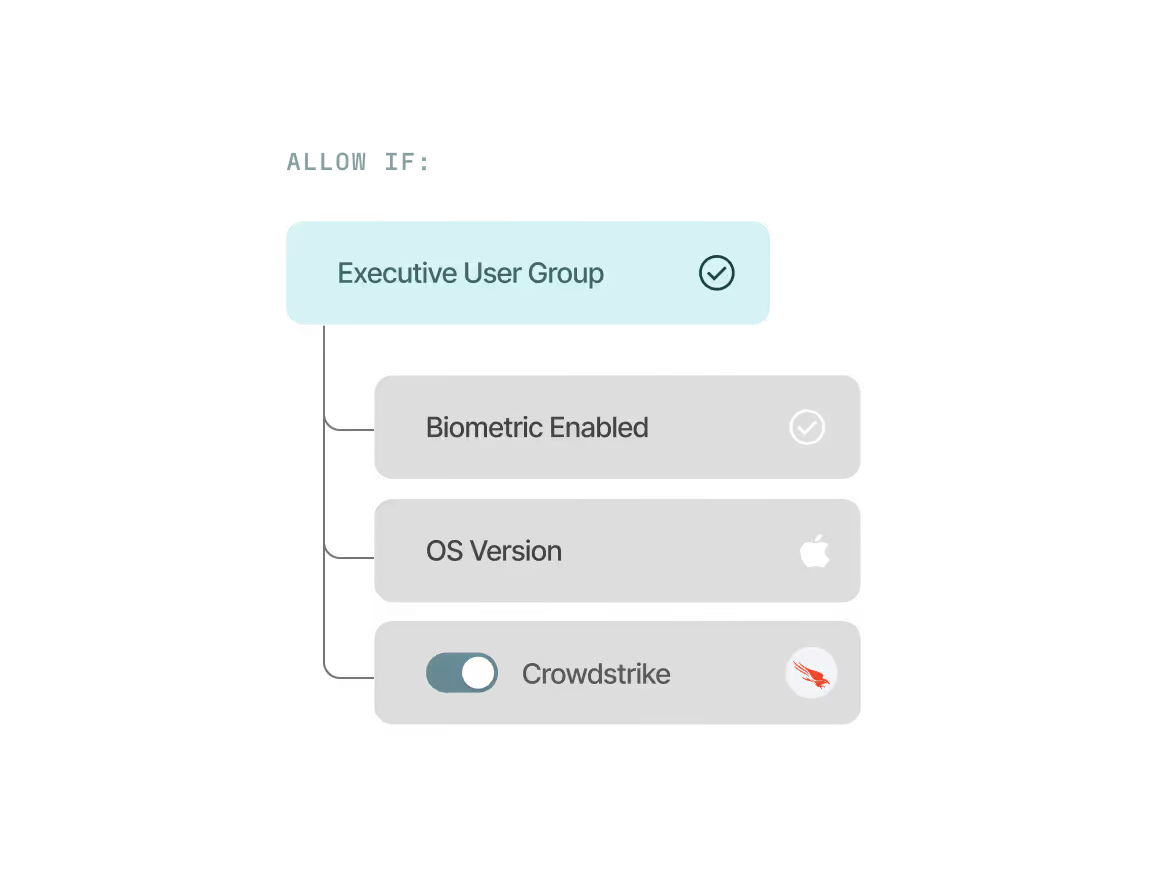
Enforce precise access controls
Easily configure granular, adaptive access policies with per app, OS, and user group controls.



.avif)

.avif)
.avif)
.avif)


.avif)

.avif)



.avif)

.avif)


