Unlock High-Fidelity Security with the New Beyond Identity App for Splunk
Security teams today live and die by the quality of their data. For many of our customers, Splunk serves as the central nervous system of the SOC, ingesting millions of events to find the needle in the haystack. But a SIEM is only as powerful as the signals fed into it. That is why we are excited to announce the launch of the new Beyond Identity App for Splunk, now available on Splunkbase.
This release represents the next major milestone in our evolving partnership with Splunk. We have been working steadily to deepen our integration, starting with raw event exports and moving toward a seamless, ecosystem-native experience.
Previously, getting our rich authentication data into a usable format within Splunk required manual effort, parsing JSON and building custom field mappings. We listened to customer feedback, and with this new app, we are removing that friction. We have built a solution that allows teams to instantly operationalize Beyond Identity’s device-bound, hardware-backed data within Splunk for accelerated anomaly detection, incident investigation, and automated response via SOAR playbooks.
What’s New?
The new Beyond Identity app streamlines our integration in two critical ways:
Pre-Built Dashboards for Immediate Visibility
Time-to-value is critical. Security engineers shouldn't have to hand-craft visulizations when what you need is instant visibility. Our new app comes with a comprehensive, pre-built dashboard out of the box, shifting effort from chart building to higher order work like correlation, risk-based alerting (RBA), and response. As soon as you install the app, you gain immediate insight into:
- Authentication trends: See exactly who is logging in and from where with cryptographic confidence.
- Device security posture: Visualize the health of all devices accessing your network, including unmanaged and contractor devices.
- Threat detection: Spot denied authentications and policy blocks instantly.
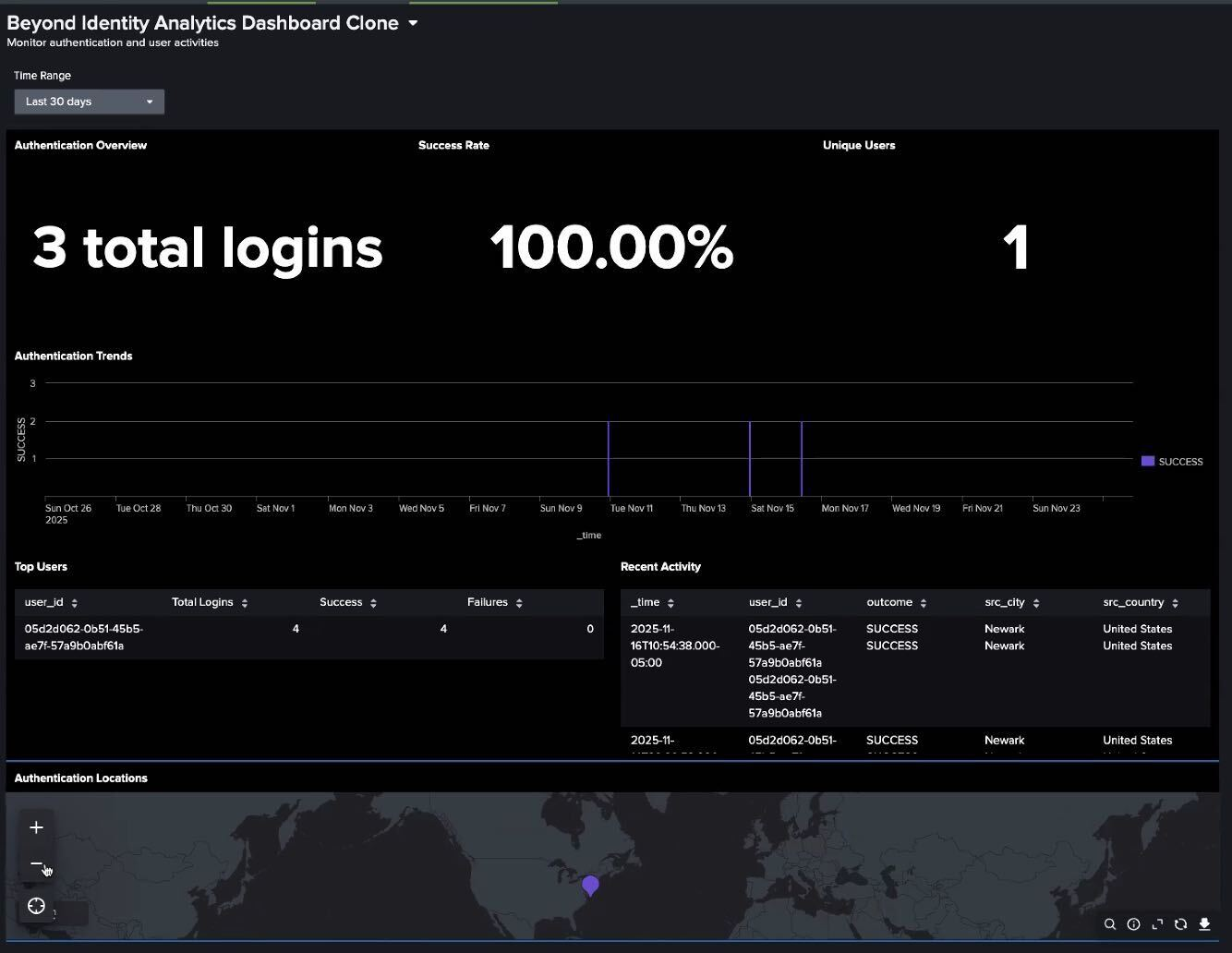
The new Beyond Identity dashboard provides a real-time view of user authentication and device trust signals.
CIM-Compliant Event Mapping
For Splunk power users, this is the game-changer. In the past, our events arrived as raw JSON. Now, the app automatically maps Beyond Identity events to Splunk’s Common Information Model (CIM). Your authentication and device trust signals arrive normalized and ready for action, not raw JSON that needs custom parsing.
- Seamless Integration: Our data now "speaks the same language" as the rest of the security stack which reduces field wrangling and schema drift headaches.
- Splunk Enterprise Security (ES) Ready: Because the data is CIM-compliant, it automatically feeds into Splunk ES correlation searches, risk-based alerting (RBA), and notable events without any custom parsing.
- Higher Fidelity Correlation: nalysts can immediately link a Beyond Identity login with endpoint and network artifacts to reconstruct the attack chain and accelerate triage.
Why Splunk + Beyond Identity?
If your organization uses Splunk to monitor your environment, you know that "garbage in means garbage out." Traditional authentication methods (passwords, push notifications, OTPs) generate noisy, low-fidelity logs. They tell you that a user logged in, but they rarely tell you if the device was secure or if the user was actually who they claimed to be.
This is where Beyond Identity transforms the Splunk experience. By upgrading to Beyond Identity’s phishing-resistant, device-bound, posture-aware authentication, you aren't just securing the front door,you are upgrading the intelligence of the entire SOC.
- Zero Noise: We cryptographically bind identity to the device, eliminating the noise of credential stuffing and brute force attacks.
- Rich Context: We ingest dozens of risk signals from the device (OS version, firewall status, biometrics) during every authentication.
- High Fidelity: When Splunk receives a "risk" signal from Beyond Identity, it’s not a guess. It’s a precise, immutable fact that analysts can trust.
Get Started Today
The new Beyond Identity app is free to download for existing customers on Splunkbase.
Not a Beyond Identity customer yet? Don’t let weak authentication data blind your SIEM. See how high-fidelity authentication logs can transform your threat detection.
Security teams today live and die by the quality of their data. For many of our customers, Splunk serves as the central nervous system of the SOC, ingesting millions of events to find the needle in the haystack. But a SIEM is only as powerful as the signals fed into it. That is why we are excited to announce the launch of the new Beyond Identity App for Splunk, now available on Splunkbase.
This release represents the next major milestone in our evolving partnership with Splunk. We have been working steadily to deepen our integration, starting with raw event exports and moving toward a seamless, ecosystem-native experience.
Previously, getting our rich authentication data into a usable format within Splunk required manual effort, parsing JSON and building custom field mappings. We listened to customer feedback, and with this new app, we are removing that friction. We have built a solution that allows teams to instantly operationalize Beyond Identity’s device-bound, hardware-backed data within Splunk for accelerated anomaly detection, incident investigation, and automated response via SOAR playbooks.
What’s New?
The new Beyond Identity app streamlines our integration in two critical ways:
Pre-Built Dashboards for Immediate Visibility
Time-to-value is critical. Security engineers shouldn't have to hand-craft visulizations when what you need is instant visibility. Our new app comes with a comprehensive, pre-built dashboard out of the box, shifting effort from chart building to higher order work like correlation, risk-based alerting (RBA), and response. As soon as you install the app, you gain immediate insight into:
- Authentication trends: See exactly who is logging in and from where with cryptographic confidence.
- Device security posture: Visualize the health of all devices accessing your network, including unmanaged and contractor devices.
- Threat detection: Spot denied authentications and policy blocks instantly.

The new Beyond Identity dashboard provides a real-time view of user authentication and device trust signals.
CIM-Compliant Event Mapping
For Splunk power users, this is the game-changer. In the past, our events arrived as raw JSON. Now, the app automatically maps Beyond Identity events to Splunk’s Common Information Model (CIM). Your authentication and device trust signals arrive normalized and ready for action, not raw JSON that needs custom parsing.
- Seamless Integration: Our data now "speaks the same language" as the rest of the security stack which reduces field wrangling and schema drift headaches.
- Splunk Enterprise Security (ES) Ready: Because the data is CIM-compliant, it automatically feeds into Splunk ES correlation searches, risk-based alerting (RBA), and notable events without any custom parsing.
- Higher Fidelity Correlation: nalysts can immediately link a Beyond Identity login with endpoint and network artifacts to reconstruct the attack chain and accelerate triage.
Why Splunk + Beyond Identity?
If your organization uses Splunk to monitor your environment, you know that "garbage in means garbage out." Traditional authentication methods (passwords, push notifications, OTPs) generate noisy, low-fidelity logs. They tell you that a user logged in, but they rarely tell you if the device was secure or if the user was actually who they claimed to be.
This is where Beyond Identity transforms the Splunk experience. By upgrading to Beyond Identity’s phishing-resistant, device-bound, posture-aware authentication, you aren't just securing the front door,you are upgrading the intelligence of the entire SOC.
- Zero Noise: We cryptographically bind identity to the device, eliminating the noise of credential stuffing and brute force attacks.
- Rich Context: We ingest dozens of risk signals from the device (OS version, firewall status, biometrics) during every authentication.
- High Fidelity: When Splunk receives a "risk" signal from Beyond Identity, it’s not a guess. It’s a precise, immutable fact that analysts can trust.
Get Started Today
The new Beyond Identity app is free to download for existing customers on Splunkbase.
Not a Beyond Identity customer yet? Don’t let weak authentication data blind your SIEM. See how high-fidelity authentication logs can transform your threat detection.
Security teams today live and die by the quality of their data. For many of our customers, Splunk serves as the central nervous system of the SOC, ingesting millions of events to find the needle in the haystack. But a SIEM is only as powerful as the signals fed into it. That is why we are excited to announce the launch of the new Beyond Identity App for Splunk, now available on Splunkbase.
This release represents the next major milestone in our evolving partnership with Splunk. We have been working steadily to deepen our integration, starting with raw event exports and moving toward a seamless, ecosystem-native experience.
Previously, getting our rich authentication data into a usable format within Splunk required manual effort, parsing JSON and building custom field mappings. We listened to customer feedback, and with this new app, we are removing that friction. We have built a solution that allows teams to instantly operationalize Beyond Identity’s device-bound, hardware-backed data within Splunk for accelerated anomaly detection, incident investigation, and automated response via SOAR playbooks.
What’s New?
The new Beyond Identity app streamlines our integration in two critical ways:
Pre-Built Dashboards for Immediate Visibility
Time-to-value is critical. Security engineers shouldn't have to hand-craft visulizations when what you need is instant visibility. Our new app comes with a comprehensive, pre-built dashboard out of the box, shifting effort from chart building to higher order work like correlation, risk-based alerting (RBA), and response. As soon as you install the app, you gain immediate insight into:
- Authentication trends: See exactly who is logging in and from where with cryptographic confidence.
- Device security posture: Visualize the health of all devices accessing your network, including unmanaged and contractor devices.
- Threat detection: Spot denied authentications and policy blocks instantly.

The new Beyond Identity dashboard provides a real-time view of user authentication and device trust signals.
CIM-Compliant Event Mapping
For Splunk power users, this is the game-changer. In the past, our events arrived as raw JSON. Now, the app automatically maps Beyond Identity events to Splunk’s Common Information Model (CIM). Your authentication and device trust signals arrive normalized and ready for action, not raw JSON that needs custom parsing.
- Seamless Integration: Our data now "speaks the same language" as the rest of the security stack which reduces field wrangling and schema drift headaches.
- Splunk Enterprise Security (ES) Ready: Because the data is CIM-compliant, it automatically feeds into Splunk ES correlation searches, risk-based alerting (RBA), and notable events without any custom parsing.
- Higher Fidelity Correlation: nalysts can immediately link a Beyond Identity login with endpoint and network artifacts to reconstruct the attack chain and accelerate triage.
Why Splunk + Beyond Identity?
If your organization uses Splunk to monitor your environment, you know that "garbage in means garbage out." Traditional authentication methods (passwords, push notifications, OTPs) generate noisy, low-fidelity logs. They tell you that a user logged in, but they rarely tell you if the device was secure or if the user was actually who they claimed to be.
This is where Beyond Identity transforms the Splunk experience. By upgrading to Beyond Identity’s phishing-resistant, device-bound, posture-aware authentication, you aren't just securing the front door,you are upgrading the intelligence of the entire SOC.
- Zero Noise: We cryptographically bind identity to the device, eliminating the noise of credential stuffing and brute force attacks.
- Rich Context: We ingest dozens of risk signals from the device (OS version, firewall status, biometrics) during every authentication.
- High Fidelity: When Splunk receives a "risk" signal from Beyond Identity, it’s not a guess. It’s a precise, immutable fact that analysts can trust.
Get Started Today
The new Beyond Identity app is free to download for existing customers on Splunkbase.
Not a Beyond Identity customer yet? Don’t let weak authentication data blind your SIEM. See how high-fidelity authentication logs can transform your threat detection.







.png)





.avif)
.avif)



.avif)






.avif)

