AI Security suite
AI security, anchored
in hardware

Eliminate the new attack surface
Block AI-powered credential theft and phishingGPT's with passwordless, device-bound authentication that cryptographically ties every login to a specific device.
See your entire AI ecosystem
Prevent compromised devices from accessing resources, committing code, or building with AI agents.
Prevent unauthorized agent actions
Identify deepfake attacks in real-time by continuously verifying both the user and their device during meetings and chats.
Audit and provenance
Secure non-human identities and AI agents with the same device-bound authentication and continuous posture verification applied to human users.
Hardware-bound
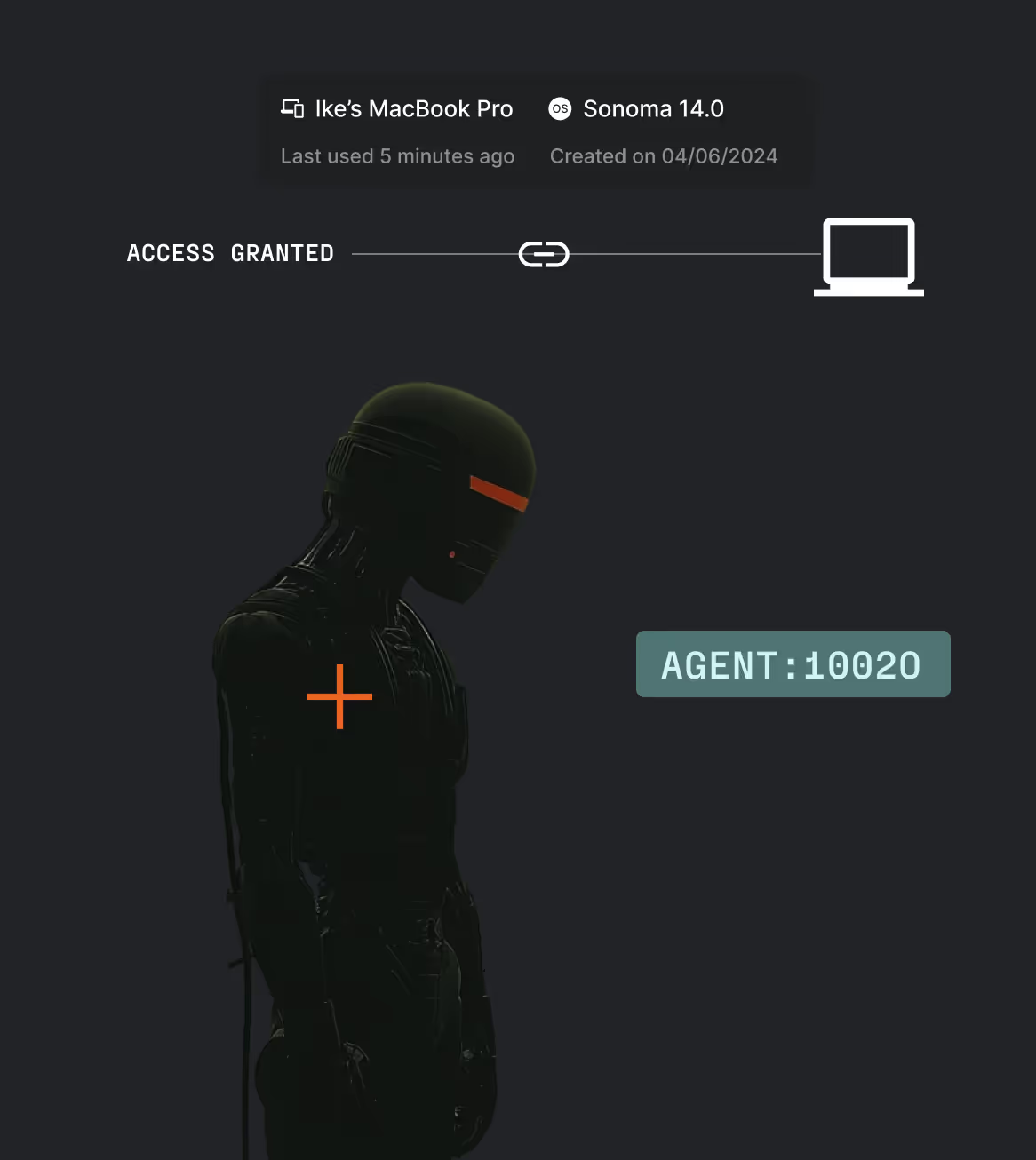
Hardware-bound agent identity
Eliminate credential and API key sprawl. Keys never leave hardware.
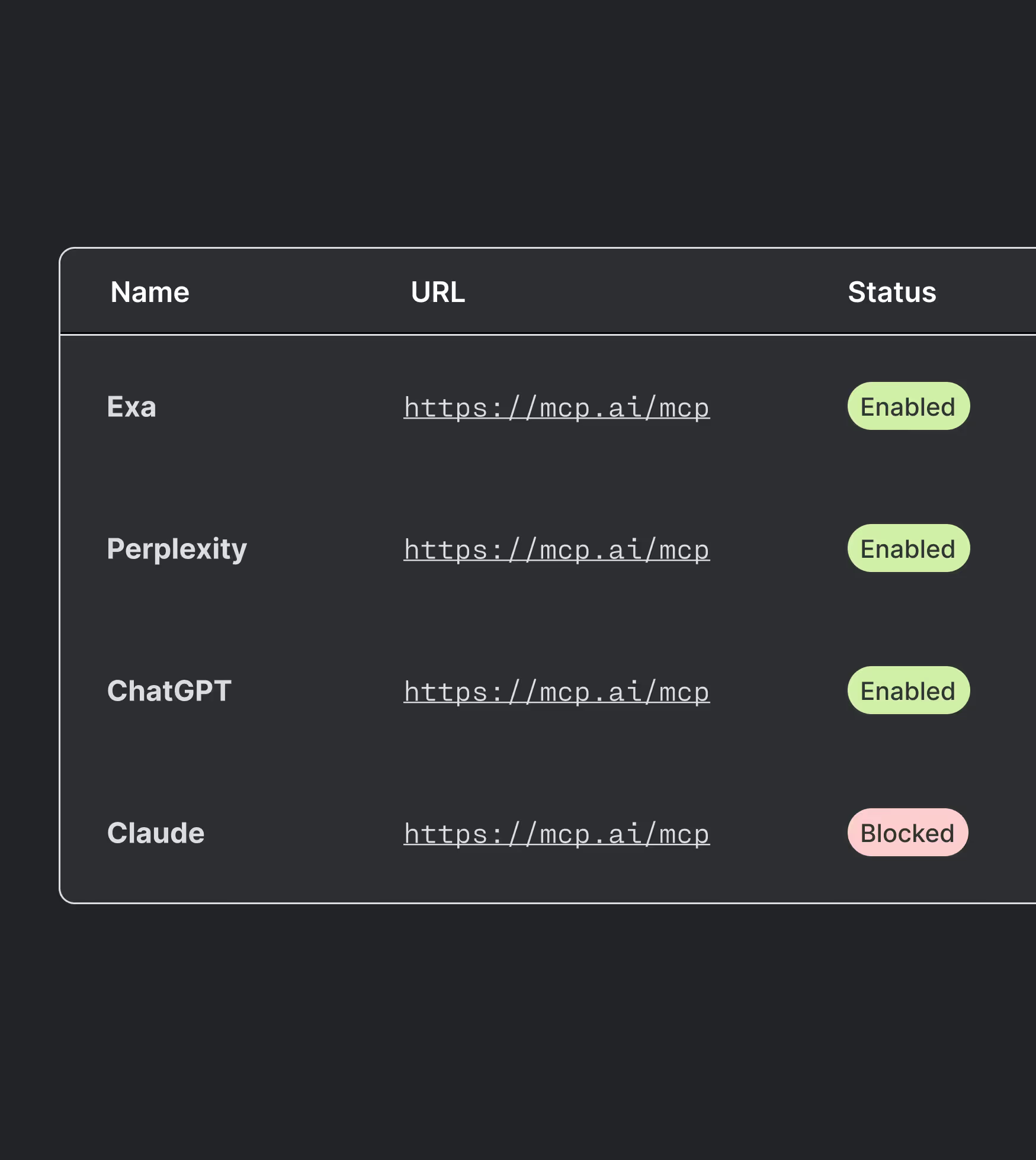
MCP Discovery
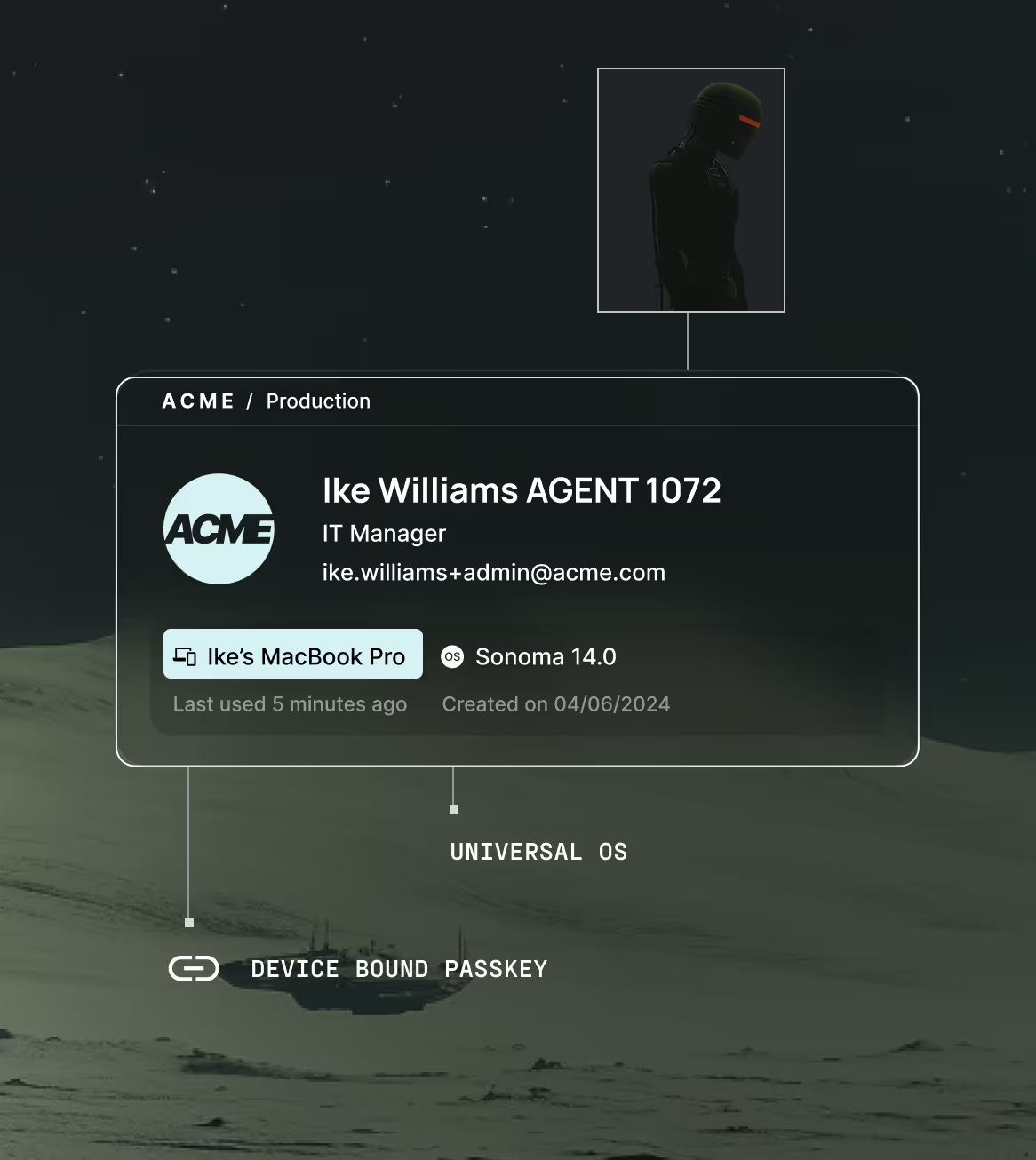
MCP server discovery
& control
Map and control every MCP server across your environment. Enforce which servers are allowed, what they can do, and who can invoke them.
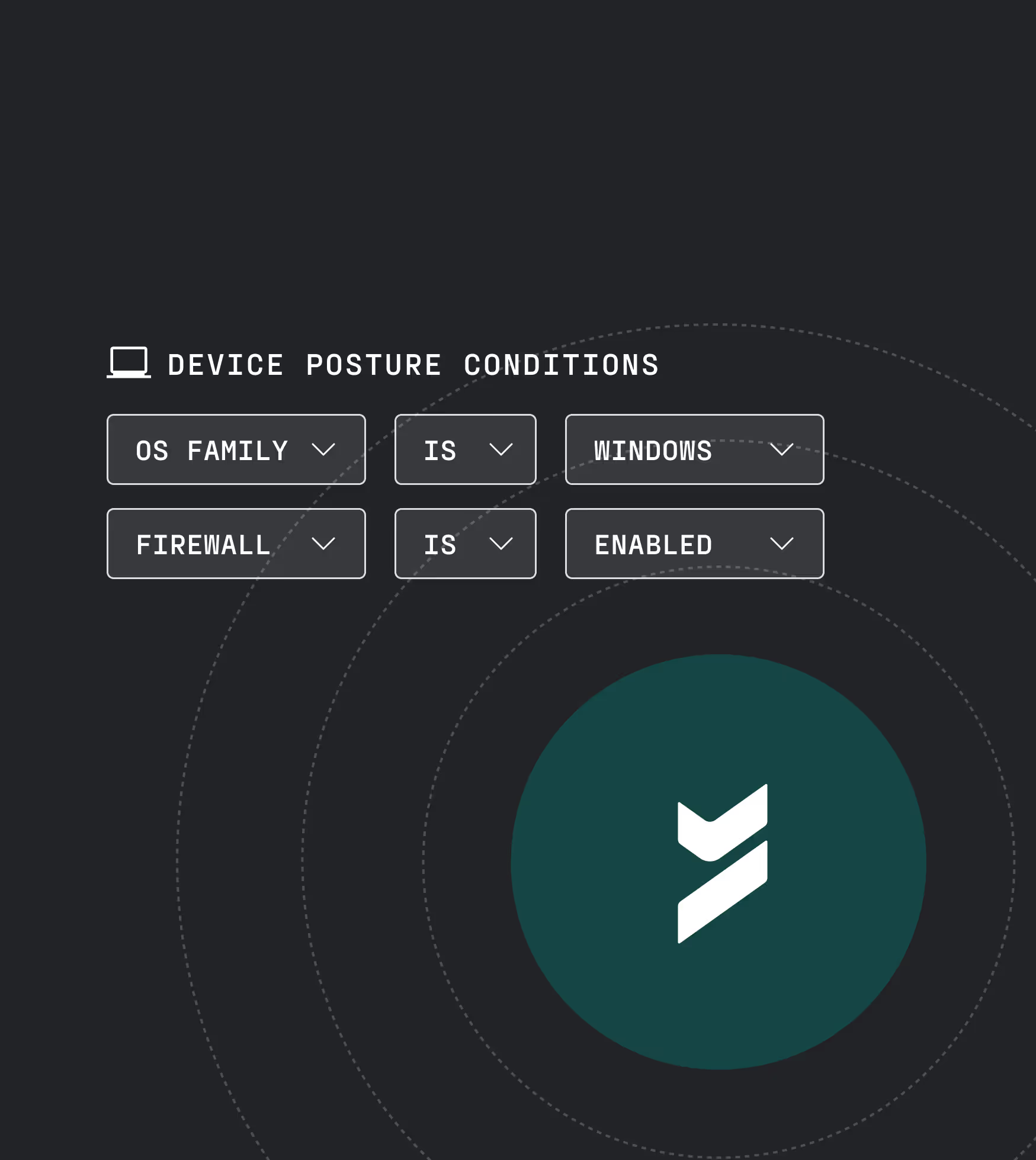
continuous enforcement
Continuous posture verification
Autonomous trust enforced continuously. Evaluate the security posture of every agent and device.
activity details
Agent activity tracing
Log the complete identity chain for every agent transaction: which agent, which device, which tool, which user.
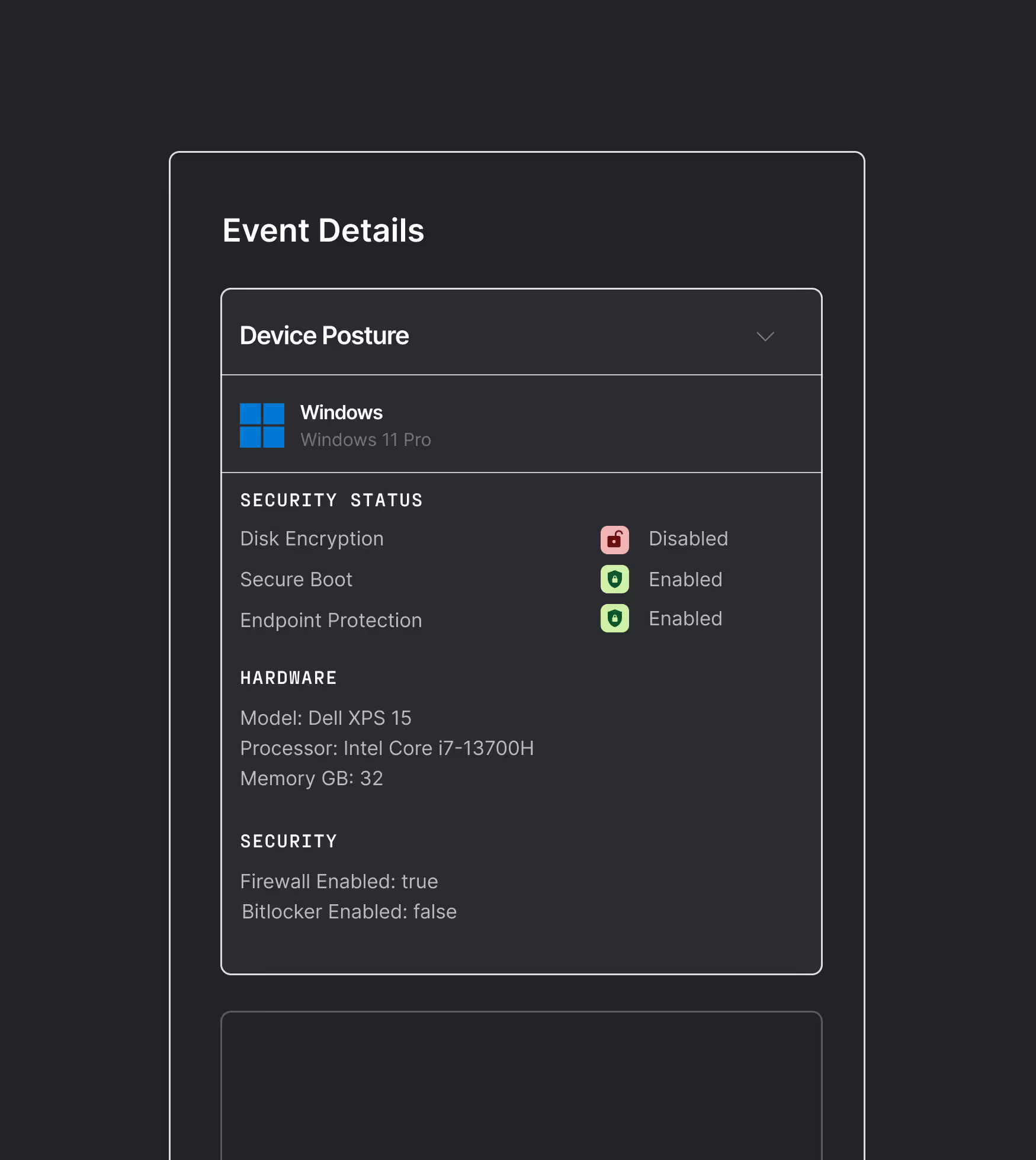
granular policies
Policy-based tool authorization
Define granular policies controlling which agents can invoke which tools and access what data based on device posture, user identity, and organizational role.
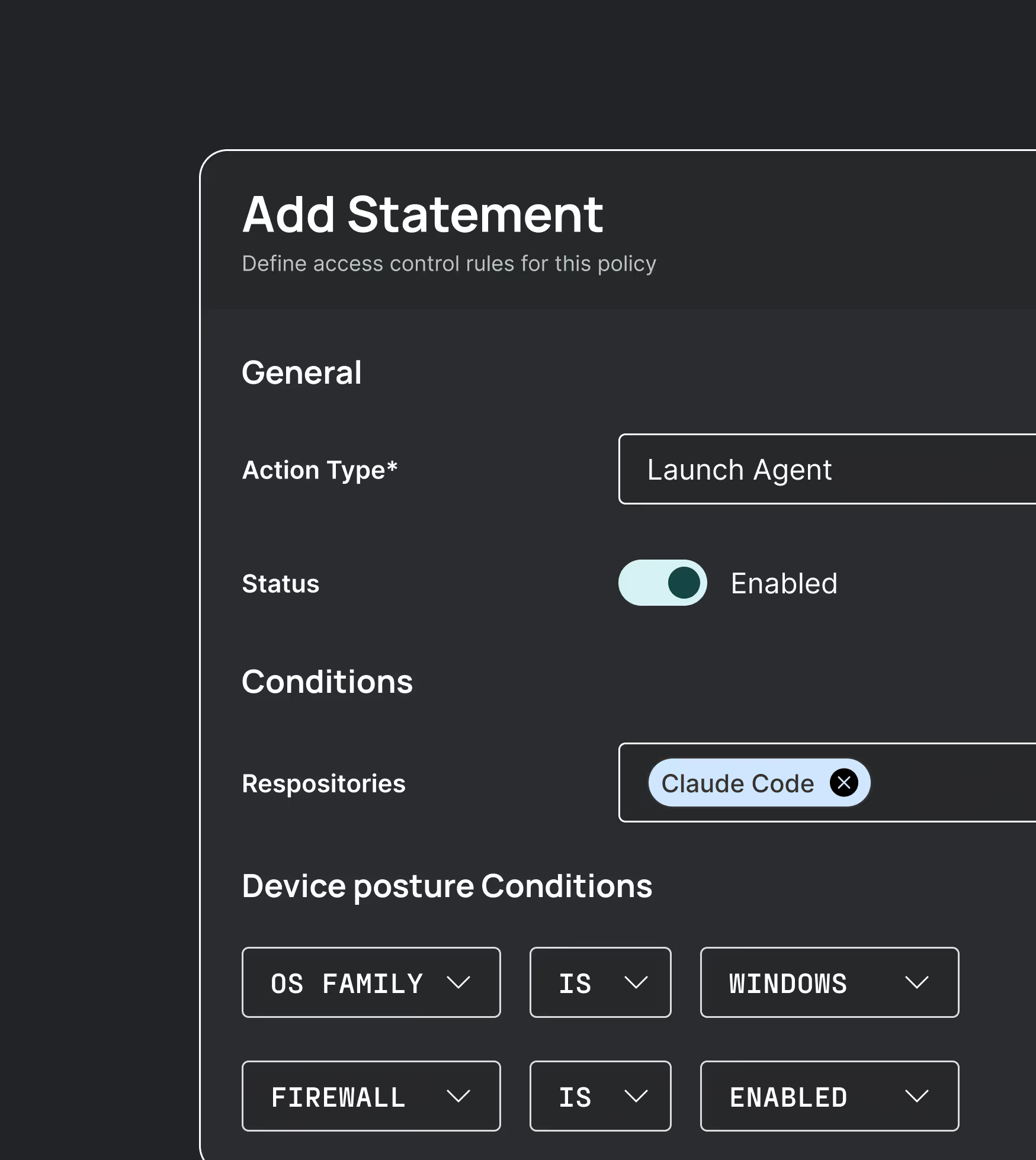
Built to protect every agent,
on every device
AI agents run everywhere. Traditional security was not designed for non-human identities that act autonomously.
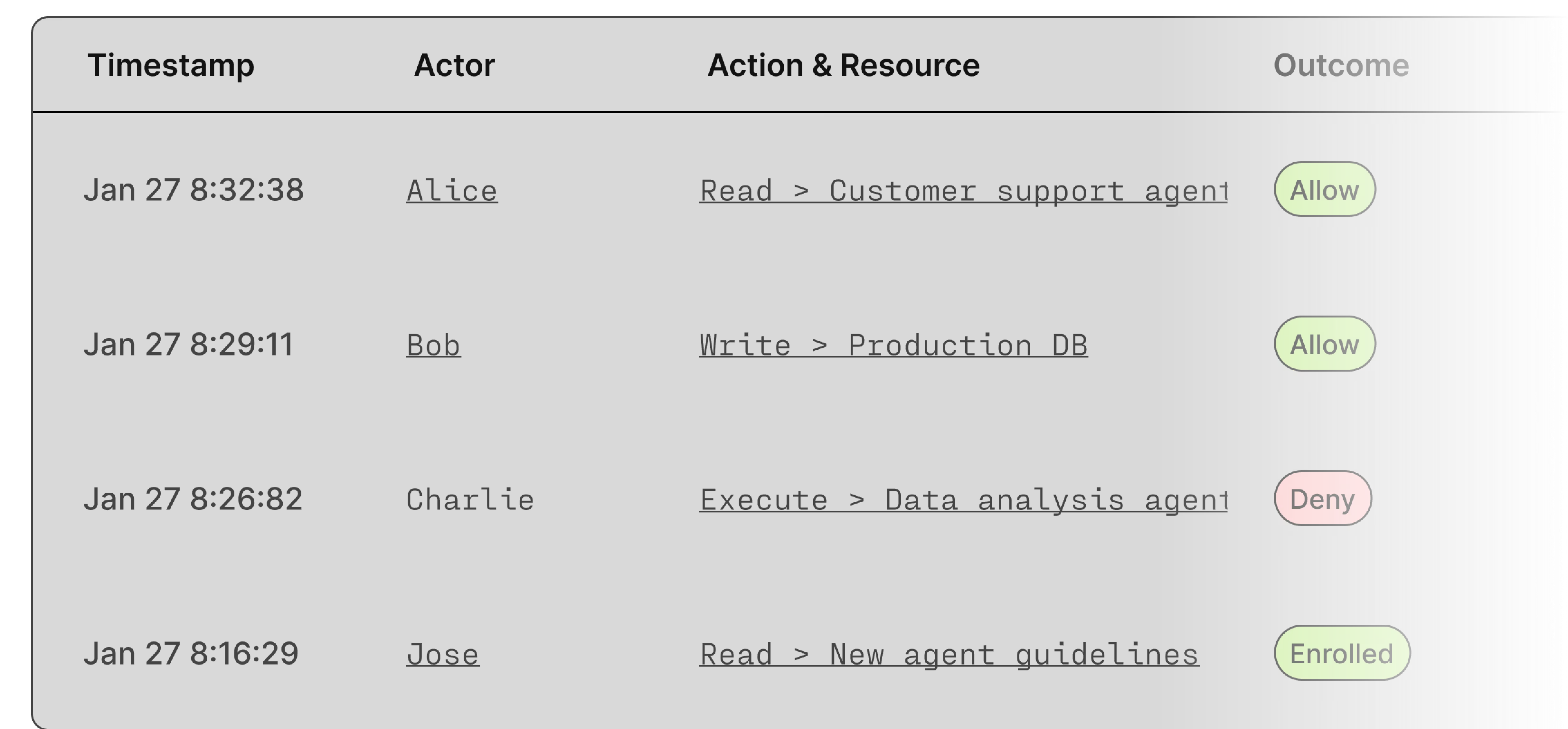
Understand your AI attack surface
Catalog every agent: what it does, where it runs, what tools it uses, who it acts for. Visualize relationships between AI agents, users, MCP servers, and data sources.
Build the foundation for what's next
AI security is evolving. Soon you will need to answer "what data influenced this decision." Hardware-anchored identity is the foundation for context-aware security.
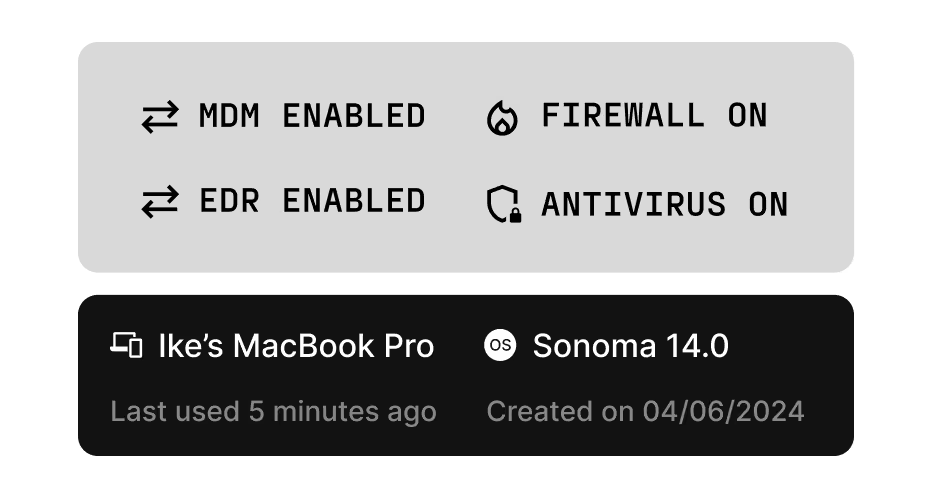
Ensure agents only run on trusted devices
Apply device trust verification to agent infrastructure. Managed or unmanaged, cloud or on-prem, every device must meet your posture requirements.
