The Beyond Blog
17 Feb 2026
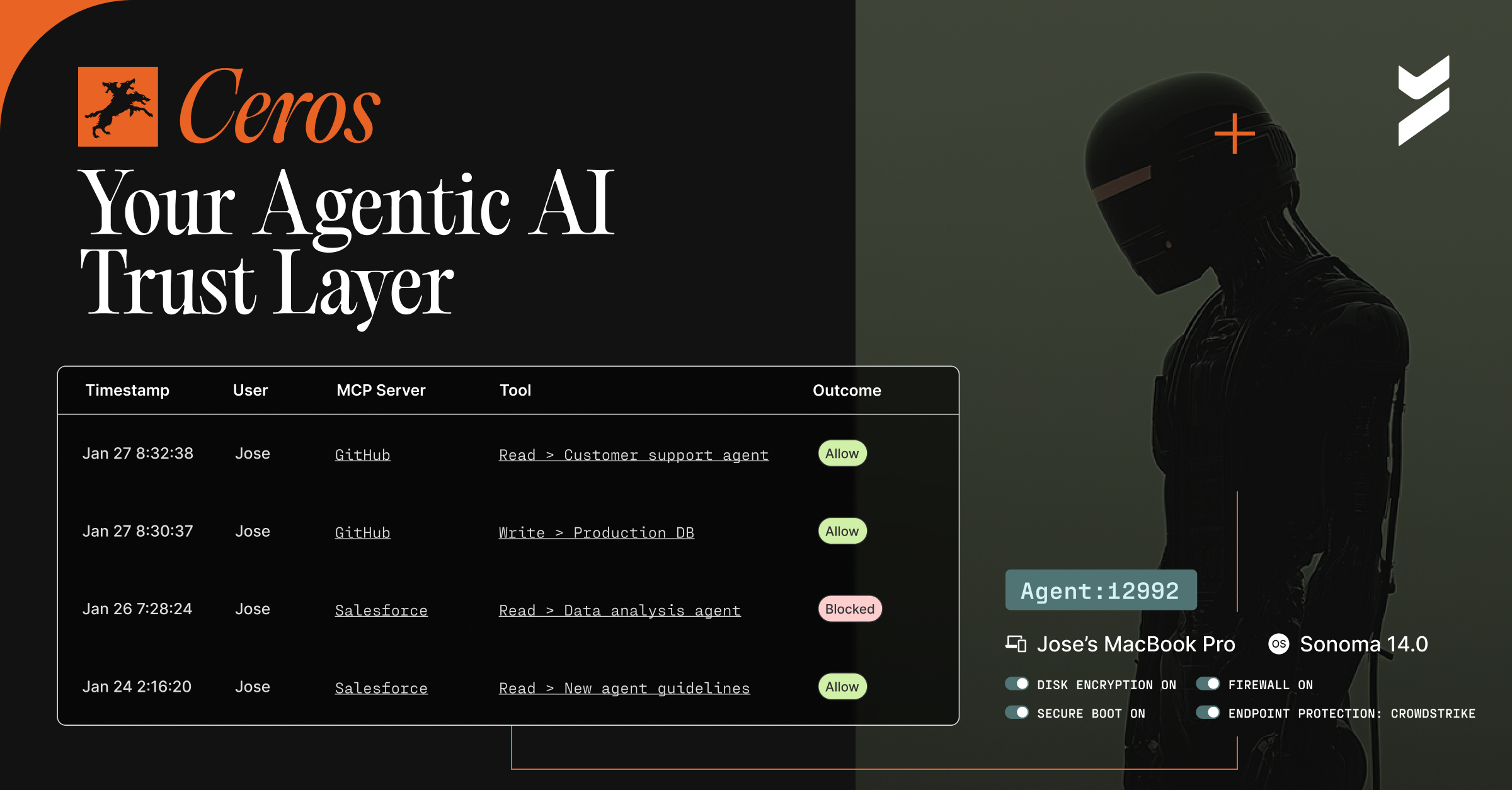
Introducing Ceros: The Agentic AI Trust Layer, Now Open for Public Preview
Secure your AI agents with Ceros, the trust layer that prevents credential theft, enforces policy in real time, and delivers full session visibility. Open for public preview now.
.png)
24 Feb 2026
February 24, 2026
Your First 5 Minutes with Ceros: See What You've Been Missing
With Ceros, go from zero AI agent visibility to full forensic audit trails in under 5 minutes. No pipeline changes required.

02 Feb 2026
February 2, 2026
The Attacker Gave Claude Their API Key: Why AI Agents Need Hardware-Bound Identity
A Claude prompt injection attack exfiltrated files via attacker API keys. Learn what it reveals about AI security and why AI agents need real identity.

22 Jan 2026
January 22, 2026
Beyond Identity Opens Early Access for the AI Security Suite
Gain visibility and control over autonomous AI agents with Beyond Identity's AI Security Suite. Enforce identity, device context, and data governance with cryptographic proof. Early access is now open!

16 Jan 2026
January 16, 2026
Unlock High-Fidelity Security with the New Beyond Identity App for Splunk
The new Beyond Identity App for Splunk delivers pre-built dashboards and CIM-compliant authentication data for instant visibility. Eliminate manual parsing and accelerate threat detection with device-bound, hardware-backed security signals.

05 Jan 2026
January 5, 2026
Beyond Identity Joins NVIDIA Inception Program to Advance Hardware-Enforced Security for the AI Era
Learn how to integrate device-bound credentials with NVIDIA DPUs to secure critical AI workloads and the entire AI supply chain.

19 Dec 2025
December 19, 2025
Chips and SLSA: Why TPMs Matter for Code Commits
Learn how TPM chips enable cryptographic commit signing for SLSA compliance. Hardware-backed identity makes code provenance auditable and tamper-proof.

17 Dec 2025
December 17, 2025
Why Is Code Provenance Non-Negotiable in the Age of AI?
As AI generates nearly half of all new code, knowing who—or what—is behind every commit has become the most critical question in software security. This article outlines why identity-based code provenance is the new cornerstone of the software supply chain.
.avif)
19 Nov 2025
November 19, 2025
How Beyond Identity & Nametag Stop Identity Fraud at Onboarding & Recovery
Beyond Identity and Nametag have expanded our strategic partnership to include a commercial integration, enabling single-contract procurement
.avif)
13 Nov 2025
November 13, 2025
New: Self Remediation Features to Reduce Help Desk Tickets and Improve UX
Beyond Identity continues to simplify secure access and our latest updates, Self-Remediation and a New Loading Screen, take another step toward making passwordless authentication effortless for everyone.

