Introducing Zero-Friction Passwordless Authentication for Customers that Eliminates Account Takeover Fraud
Customer authentication is a critical component of almost every application that exists because it serves as a gateway into your product and services, impacting 100% of customers. While it is a standard feature, it is not easy to get right, and the consequences for getting it wrong are higher than ever.
Customers have increasingly demanding expectations for digital experiences, global security and privacy regulations are rapidly expanding, and fraud and breaches can cost companies up to $401 million not to mention the long-term deterioration of brand trust.
The security vulnerabilities and financial impact of passwords are well-documented. However, existing solutions such as social logins, password-based MFA, and other passwordless products fail to eradicate the root cause of security and friction issues—the password.
Beyond Identity was the first company to deliver an innovative and practical implementation of asymmetric cryptography and X.509 certificates that completely eliminates passwords for users and from the database across native mobile, native desktop, and web applications. Our solution provides a highly secure, zero-friction, passwordless multi-factor authentication (MFA) that does not require a second device and enables companies to implement adaptive risk-based access policies based on real-time user and device risk.
Since our founding, we’ve expanded from securing the workforce to verifying code signing for DevOps. Today, we’re making our Secure Customers product generally available.
Secure Customers provides easy-to-integrate SDKs that enables you to recreate Beyond Identity’s passwordless authentication capabilities across both native and web applications to accelerate account conversions while providing full protection from account takeover fraud.
Here are some unique features of Secure Customer that make zero-friction, secure customer authentication a reality for your applications.
Ready to see Secure Customer in action? Get a personalized demo today.
Fastest Strong Customer Authentication (SCA) on any platform
Password requirements cause visitors to drop-off during new account registration and creates hurdles for returning customers, lowering both acquisition and engagement rates. In fact, 46% of US consumers failed to complete a transaction due to forgotten passwords and issues with password resets.
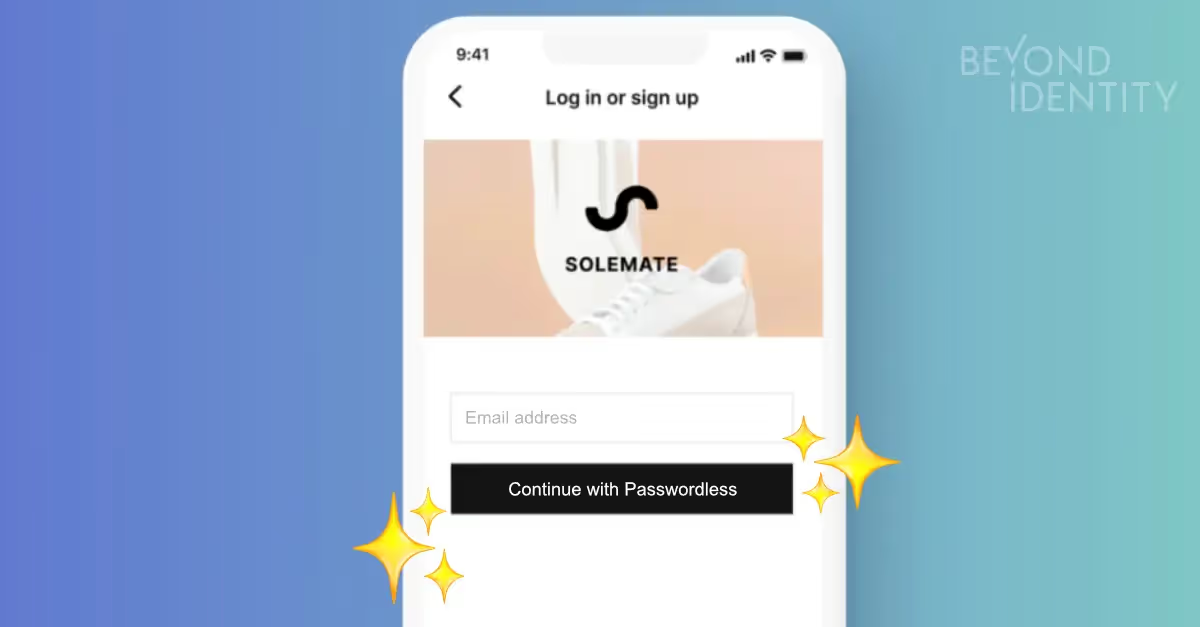
Secure Customer makes it possible for your customers to register without creating yet another password or picking up a second device for a one-time password (OTP) or push notification on native and web applications. Instead, passwordless enrollment happens once and the only thing your customers have to do is provide their email address to bind their identity to their device.
In compliance with PSD2 Strong Customer Authentication requirements, Beyond Identity authenticates customers with two strong factors by default, “something you are” from the local device biometric, and “something you own” from the private key created and stored in the device’s local secure enclave or Trusted Platform Module (TPM).
The TPM is a hardware-based, tamper-resistant location for storing encryption keys and performing highly trusted cryptographic operations. Unlike a password, the private key remains protected inside the TPM, even in the event of operating system compromise or lost device.
By replacing passwords with secure credentials, Secure Customers removes the burden of authentication from customers so they can enjoy consistent, lightning-fast passwordless logins without picking up a second device for a code, magic link, or push notification.
Eliminate account takeovers by replacing passwords with tamper-proof credentials
Account takeover fraud has been on a steep and chilling increase in the last three years. In 2018, account takeovers tripled, costing businesses $5.1 billion. 2020 saw an incredible 292% jump in account takeover fraud, and so far in 2021, account takeovers attempted increased by 80%.
At the root of account takeover fraud is the password problem. Attackers compromise customer accounts with phishing attacks, credential stuffing with purchased password credentials, or brute force attacks with bots. The fact that password reuse is common practice only exacerbates the problem.
Many companies have tried to mitigate account takeover risks with band-aid methods like password-based MFA. However, as long as the password exists, attackers still have a viable way to compromise customer accounts. Not to mention, Google research captured the general Americans’ attitude towards MFA as “thanks, but no thanks” with only 37% of Americans using MFA due to the added friction.
The solution is to completely eliminate the password from the customer experience and your database so that it is never used or stored. What doesn’t exist cannot be stolen, and when you don’t have to store passwords, you can effectively secure customer accounts and take the target off of your password database.
Beyond Identity makes passwords completely obsolete by replacing them with cryptographically verifiable, immutable, and unclonable private key credentials that your customers own and control. Given that the private key is created in and can never leave the device TPM, it is completely protected against attacks and breaches even if an adversary has control of the operating system.
Additionally, once a customer completes their one-time passwordless enrollment, our SDKs empower them to securely access and extend their credentials to other approved devices.
Real-time user and device risk signals for adaptive step-up authentication
Another unique capability of Beyond Identity’s approach to passwordless authentication is the ability to capture, digitally sign, and send user and device security posture signals in real time from the device making the authentication request.
Given that risk is never static as customers travel, change device security settings, and download files and applications, this unprecedented level of insight into user and device risk helps security teams make informed risk-based access decisions.
Coupled with a configurable policy engine, Beyond Identity makes it possible to implement adaptive step-up authentication that dynamically prompts biometric verification within your application according to your risk policies. For example, you can require step-up authentication for jailbroken or rooted devices or for when a customer is attempting to make a large purchase, transfer money, or extend their credentials to a new device.
Get a demo of Secure Customer’s step-up authentication capabilities.
Cloud-native architecture and standards-based extensibility to modernize your applications
Customer authentication is a collaborative effort across product, security, engineering, and marketing teams given its broad business impact. As such, a successful deployment must address the strategic imperatives of all teams and enable agile product development.
To shorten time-to-market and decrease maintenance costs of legacy authentication infrastructure, the Secure Customer product provides:
- SDKs in popular languages for native and web applications
- Robust developer documentation to accelerate integration
- Open standards support for built-in extensibility
- Cloud-native architecture to ensure availability and elastic scalability
- Out-of-box integrations with popular CIAM SSOs including Auth0, Keycloak, and Forgerock
Eliminate passwords for customers today
With an innovative implementation of asymmetric cryptography, Beyond Identity’s Secure Customers product helps you ship zero-friction passwordless authentication across mobile, desktop, and web applications quickly, securely, and scalably.
In addition to eliminating customer authentication friction, Beyond Identity makes account takeover fraud impossible to execute and enables adaptive step-up authentication based on real-time user and device risk.
Take the next step to elevate customer authentication in your applications today.
Customer authentication is a critical component of almost every application that exists because it serves as a gateway into your product and services, impacting 100% of customers. While it is a standard feature, it is not easy to get right, and the consequences for getting it wrong are higher than ever.
Customers have increasingly demanding expectations for digital experiences, global security and privacy regulations are rapidly expanding, and fraud and breaches can cost companies up to $401 million not to mention the long-term deterioration of brand trust.
The security vulnerabilities and financial impact of passwords are well-documented. However, existing solutions such as social logins, password-based MFA, and other passwordless products fail to eradicate the root cause of security and friction issues—the password.
Beyond Identity was the first company to deliver an innovative and practical implementation of asymmetric cryptography and X.509 certificates that completely eliminates passwords for users and from the database across native mobile, native desktop, and web applications. Our solution provides a highly secure, zero-friction, passwordless multi-factor authentication (MFA) that does not require a second device and enables companies to implement adaptive risk-based access policies based on real-time user and device risk.
Since our founding, we’ve expanded from securing the workforce to verifying code signing for DevOps. Today, we’re making our Secure Customers product generally available.
Secure Customers provides easy-to-integrate SDKs that enables you to recreate Beyond Identity’s passwordless authentication capabilities across both native and web applications to accelerate account conversions while providing full protection from account takeover fraud.
Here are some unique features of Secure Customer that make zero-friction, secure customer authentication a reality for your applications.
Ready to see Secure Customer in action? Get a personalized demo today.
Fastest Strong Customer Authentication (SCA) on any platform
Password requirements cause visitors to drop-off during new account registration and creates hurdles for returning customers, lowering both acquisition and engagement rates. In fact, 46% of US consumers failed to complete a transaction due to forgotten passwords and issues with password resets.
Secure Customer makes it possible for your customers to register without creating yet another password or picking up a second device for a one-time password (OTP) or push notification on native and web applications. Instead, passwordless enrollment happens once and the only thing your customers have to do is provide their email address to bind their identity to their device.
In compliance with PSD2 Strong Customer Authentication requirements, Beyond Identity authenticates customers with two strong factors by default, “something you are” from the local device biometric, and “something you own” from the private key created and stored in the device’s local secure enclave or Trusted Platform Module (TPM).
The TPM is a hardware-based, tamper-resistant location for storing encryption keys and performing highly trusted cryptographic operations. Unlike a password, the private key remains protected inside the TPM, even in the event of operating system compromise or lost device.
By replacing passwords with secure credentials, Secure Customers removes the burden of authentication from customers so they can enjoy consistent, lightning-fast passwordless logins without picking up a second device for a code, magic link, or push notification.
Eliminate account takeovers by replacing passwords with tamper-proof credentials
Account takeover fraud has been on a steep and chilling increase in the last three years. In 2018, account takeovers tripled, costing businesses $5.1 billion. 2020 saw an incredible 292% jump in account takeover fraud, and so far in 2021, account takeovers attempted increased by 80%.
At the root of account takeover fraud is the password problem. Attackers compromise customer accounts with phishing attacks, credential stuffing with purchased password credentials, or brute force attacks with bots. The fact that password reuse is common practice only exacerbates the problem.
Many companies have tried to mitigate account takeover risks with band-aid methods like password-based MFA. However, as long as the password exists, attackers still have a viable way to compromise customer accounts. Not to mention, Google research captured the general Americans’ attitude towards MFA as “thanks, but no thanks” with only 37% of Americans using MFA due to the added friction.
The solution is to completely eliminate the password from the customer experience and your database so that it is never used or stored. What doesn’t exist cannot be stolen, and when you don’t have to store passwords, you can effectively secure customer accounts and take the target off of your password database.
Beyond Identity makes passwords completely obsolete by replacing them with cryptographically verifiable, immutable, and unclonable private key credentials that your customers own and control. Given that the private key is created in and can never leave the device TPM, it is completely protected against attacks and breaches even if an adversary has control of the operating system.
Additionally, once a customer completes their one-time passwordless enrollment, our SDKs empower them to securely access and extend their credentials to other approved devices.
Real-time user and device risk signals for adaptive step-up authentication
Another unique capability of Beyond Identity’s approach to passwordless authentication is the ability to capture, digitally sign, and send user and device security posture signals in real time from the device making the authentication request.
Given that risk is never static as customers travel, change device security settings, and download files and applications, this unprecedented level of insight into user and device risk helps security teams make informed risk-based access decisions.
Coupled with a configurable policy engine, Beyond Identity makes it possible to implement adaptive step-up authentication that dynamically prompts biometric verification within your application according to your risk policies. For example, you can require step-up authentication for jailbroken or rooted devices or for when a customer is attempting to make a large purchase, transfer money, or extend their credentials to a new device.
Get a demo of Secure Customer’s step-up authentication capabilities.
Cloud-native architecture and standards-based extensibility to modernize your applications
Customer authentication is a collaborative effort across product, security, engineering, and marketing teams given its broad business impact. As such, a successful deployment must address the strategic imperatives of all teams and enable agile product development.
To shorten time-to-market and decrease maintenance costs of legacy authentication infrastructure, the Secure Customer product provides:
- SDKs in popular languages for native and web applications
- Robust developer documentation to accelerate integration
- Open standards support for built-in extensibility
- Cloud-native architecture to ensure availability and elastic scalability
- Out-of-box integrations with popular CIAM SSOs including Auth0, Keycloak, and Forgerock
Eliminate passwords for customers today
With an innovative implementation of asymmetric cryptography, Beyond Identity’s Secure Customers product helps you ship zero-friction passwordless authentication across mobile, desktop, and web applications quickly, securely, and scalably.
In addition to eliminating customer authentication friction, Beyond Identity makes account takeover fraud impossible to execute and enables adaptive step-up authentication based on real-time user and device risk.
Take the next step to elevate customer authentication in your applications today.
Customer authentication is a critical component of almost every application that exists because it serves as a gateway into your product and services, impacting 100% of customers. While it is a standard feature, it is not easy to get right, and the consequences for getting it wrong are higher than ever.
Customers have increasingly demanding expectations for digital experiences, global security and privacy regulations are rapidly expanding, and fraud and breaches can cost companies up to $401 million not to mention the long-term deterioration of brand trust.
The security vulnerabilities and financial impact of passwords are well-documented. However, existing solutions such as social logins, password-based MFA, and other passwordless products fail to eradicate the root cause of security and friction issues—the password.
Beyond Identity was the first company to deliver an innovative and practical implementation of asymmetric cryptography and X.509 certificates that completely eliminates passwords for users and from the database across native mobile, native desktop, and web applications. Our solution provides a highly secure, zero-friction, passwordless multi-factor authentication (MFA) that does not require a second device and enables companies to implement adaptive risk-based access policies based on real-time user and device risk.
Since our founding, we’ve expanded from securing the workforce to verifying code signing for DevOps. Today, we’re making our Secure Customers product generally available.
Secure Customers provides easy-to-integrate SDKs that enables you to recreate Beyond Identity’s passwordless authentication capabilities across both native and web applications to accelerate account conversions while providing full protection from account takeover fraud.
Here are some unique features of Secure Customer that make zero-friction, secure customer authentication a reality for your applications.
Ready to see Secure Customer in action? Get a personalized demo today.
Fastest Strong Customer Authentication (SCA) on any platform
Password requirements cause visitors to drop-off during new account registration and creates hurdles for returning customers, lowering both acquisition and engagement rates. In fact, 46% of US consumers failed to complete a transaction due to forgotten passwords and issues with password resets.
Secure Customer makes it possible for your customers to register without creating yet another password or picking up a second device for a one-time password (OTP) or push notification on native and web applications. Instead, passwordless enrollment happens once and the only thing your customers have to do is provide their email address to bind their identity to their device.
In compliance with PSD2 Strong Customer Authentication requirements, Beyond Identity authenticates customers with two strong factors by default, “something you are” from the local device biometric, and “something you own” from the private key created and stored in the device’s local secure enclave or Trusted Platform Module (TPM).
The TPM is a hardware-based, tamper-resistant location for storing encryption keys and performing highly trusted cryptographic operations. Unlike a password, the private key remains protected inside the TPM, even in the event of operating system compromise or lost device.
By replacing passwords with secure credentials, Secure Customers removes the burden of authentication from customers so they can enjoy consistent, lightning-fast passwordless logins without picking up a second device for a code, magic link, or push notification.
Eliminate account takeovers by replacing passwords with tamper-proof credentials
Account takeover fraud has been on a steep and chilling increase in the last three years. In 2018, account takeovers tripled, costing businesses $5.1 billion. 2020 saw an incredible 292% jump in account takeover fraud, and so far in 2021, account takeovers attempted increased by 80%.
At the root of account takeover fraud is the password problem. Attackers compromise customer accounts with phishing attacks, credential stuffing with purchased password credentials, or brute force attacks with bots. The fact that password reuse is common practice only exacerbates the problem.
Many companies have tried to mitigate account takeover risks with band-aid methods like password-based MFA. However, as long as the password exists, attackers still have a viable way to compromise customer accounts. Not to mention, Google research captured the general Americans’ attitude towards MFA as “thanks, but no thanks” with only 37% of Americans using MFA due to the added friction.
The solution is to completely eliminate the password from the customer experience and your database so that it is never used or stored. What doesn’t exist cannot be stolen, and when you don’t have to store passwords, you can effectively secure customer accounts and take the target off of your password database.
Beyond Identity makes passwords completely obsolete by replacing them with cryptographically verifiable, immutable, and unclonable private key credentials that your customers own and control. Given that the private key is created in and can never leave the device TPM, it is completely protected against attacks and breaches even if an adversary has control of the operating system.
Additionally, once a customer completes their one-time passwordless enrollment, our SDKs empower them to securely access and extend their credentials to other approved devices.
Real-time user and device risk signals for adaptive step-up authentication
Another unique capability of Beyond Identity’s approach to passwordless authentication is the ability to capture, digitally sign, and send user and device security posture signals in real time from the device making the authentication request.
Given that risk is never static as customers travel, change device security settings, and download files and applications, this unprecedented level of insight into user and device risk helps security teams make informed risk-based access decisions.
Coupled with a configurable policy engine, Beyond Identity makes it possible to implement adaptive step-up authentication that dynamically prompts biometric verification within your application according to your risk policies. For example, you can require step-up authentication for jailbroken or rooted devices or for when a customer is attempting to make a large purchase, transfer money, or extend their credentials to a new device.
Get a demo of Secure Customer’s step-up authentication capabilities.
Cloud-native architecture and standards-based extensibility to modernize your applications
Customer authentication is a collaborative effort across product, security, engineering, and marketing teams given its broad business impact. As such, a successful deployment must address the strategic imperatives of all teams and enable agile product development.
To shorten time-to-market and decrease maintenance costs of legacy authentication infrastructure, the Secure Customer product provides:
- SDKs in popular languages for native and web applications
- Robust developer documentation to accelerate integration
- Open standards support for built-in extensibility
- Cloud-native architecture to ensure availability and elastic scalability
- Out-of-box integrations with popular CIAM SSOs including Auth0, Keycloak, and Forgerock
Eliminate passwords for customers today
With an innovative implementation of asymmetric cryptography, Beyond Identity’s Secure Customers product helps you ship zero-friction passwordless authentication across mobile, desktop, and web applications quickly, securely, and scalably.
In addition to eliminating customer authentication friction, Beyond Identity makes account takeover fraud impossible to execute and enables adaptive step-up authentication based on real-time user and device risk.
Take the next step to elevate customer authentication in your applications today.












.avif)
.avif)



.avif)






.avif)

