What Is The TPM (Trusted Platform Module) And Why Is It Important?
If you’re working from a modern computer, chances are there’s a TPM inside, soldered onto the motherboard of your device. TPMs are unique to Windows and Linux PCs. Apple devices and Androids have something similar, which operates on many of the same principles discussed in the article. With Apple, it’s called the Secure Enclave and with Android, it’s called the Android Knox. But our focus here will be describing the TPM specifically.
If you’re not familiar with the TPM (Trusted Platform Module), it is in some ways similar to the SmartCard chip embedded in your credit card.
The smartchip's purpose is to securely authenticate the card during transactions, using asymmetric key cryptography.
Think of the TPM as a SmartCard or Credit Card chip that is permanently attached to the computer. Just like SmartCard chips secure credit cards, TPMs secure computer hardware with cryptographic keys.
What Is A TPM?
A TPM or Trusted Platform Module is a hardware-based, tamper-resistant chip in most PCs, networking equipment, and industrial controllers.
From its beginnings more than 20 years ago, the TPM was designed to protect and manage private encryption keys. Some things you can do with a TPM include:
- Manage encryption keys
- Full-disk encryption
- Augment smart cards, fingerprint readers, and fobs for multi-factor authentication
- Encrypt files and folders to control access
- Establish state information to enable endpoint integrity
- Hash state information prior to hard drive shutdown for endpoint integrity
- Enable more secure VPN, remote, and wireless access
- Use in conjunction with Full Disk Encryption to restrict access to sensitive data
This blog, however, will focus on how the TPM enables secret and unclonable authentication of digital identities to service providers, using asymmetric key cryptography and other industry protocols. The hardware-based TPM securely stores the private encryption key, which is used to authenticate a digital identity with service providers in possession of the public encryption key.
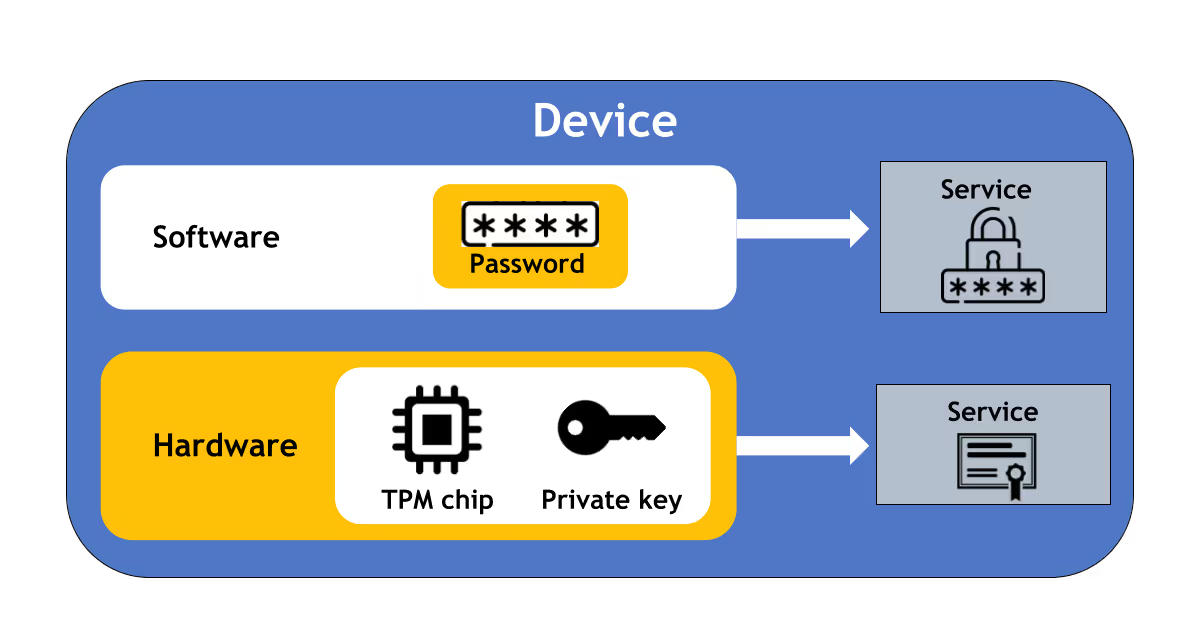
A comparison of two methods to prove a user’s digital identity: software and a password (top) versus the hardware-based TPM and asymmetric cryptography (bottom).
The benefit is that the private key is never exposed to attacks. On the other hand, passwords are exposed at rest or in transit across the network. This secret is used only within the TPM’s protections — away from software and only to provide the response to the service’s challenge to authenticate.
Why Is the TPM Important?
The TPM is a secure, tamper-resistant location for storing encryption keys and performing highly trusted cryptographic operations. Unlike a password, the private key remains protected inside the TPM, even in the event of:
- Stolen data and files (the private key can only be used by that TPM)
- A compromise of the Operating System
- A stolen computer
The TPM also provides strong supply chain assurance, helping to validate that the device's hardware and software components have not been tampered with or otherwise modified.
A TPM-enabled device can provide cryptographic proof of its hardware identity. Institutions can verify (and provide an audit trail) of the specific device used to execute transactions. Using Attestation, the TPM can also provide the identity of the firmware, the OS, and even applications.
Institutions can therefore have assurance that transactions have strong, key-based user authentication but they are also being executed on an authorized (and updated) device that has not been tampered with.
How Secure Is the TPM?
The TPM’s security is based on the long-standing concept of protecting critical data (such as secrets) by isolating them from hostile components — including the Operating System itself. This isolated area is called a Trusted Execution Environment (TEE).
While there are many types and products that make use of a TEE, most are proprietary.
- The TPM is an International Industry Standard with more than 20+ years of deployments and public evaluation. It is an International Organization for Standardization (ISO) standard (ISO/IEC 11889) accepted worldwide.
- Most TPMs have Federal Information Processing Standards (FIPS) 140 certification and have been evaluated by Common Criteria laboratories.
- TPM is mentioned as an example authentication token in NIST SP 800-63-3 and can be used as a Multi Factor Authentication device.
- It is even recommended for use in critical infrastructure applications by ISO/IEC 62443.
How Beyond Identity Uses the TPM
Beyond Identity uses the TPM (and similar hardware modules on Macs and Android devices) to replace insecure passwords with a secure and cryptographically provable digital identity. And unlike passwords, the private key in the TPM is never exposed to the application or even the Operating System itself.
The tamper-resistant TPM stores encryption keys in such a way where they can not be read or removed from the device, making it a secure way to protect and bind a user’s digital identity to a device. This enables strong authentication of users and the ability to control access to only authorized devices.
Conclusion
Here’s a summary of the benefit of using the TPM for a person’s authentication:
- The TPM is a proven International standard with 20+ years of deployment.
- The TPM’s specifications are public with the reference source code publicly available.
- Most TPM’s are evaluated using national and international standards.
- The TPM protects the asymmetric key’s secrets from software adversaries even if the attacker has control of the operating system.
Beyond Identity uses the private key stored in the TPM to provide unforgeable, strong authentication. Click here to learn more on a demo with one of our engineers.
If you’re working from a modern computer, chances are there’s a TPM inside, soldered onto the motherboard of your device. TPMs are unique to Windows and Linux PCs. Apple devices and Androids have something similar, which operates on many of the same principles discussed in the article. With Apple, it’s called the Secure Enclave and with Android, it’s called the Android Knox. But our focus here will be describing the TPM specifically.
If you’re not familiar with the TPM (Trusted Platform Module), it is in some ways similar to the SmartCard chip embedded in your credit card.
The smartchip's purpose is to securely authenticate the card during transactions, using asymmetric key cryptography.
Think of the TPM as a SmartCard or Credit Card chip that is permanently attached to the computer. Just like SmartCard chips secure credit cards, TPMs secure computer hardware with cryptographic keys.
What Is A TPM?
A TPM or Trusted Platform Module is a hardware-based, tamper-resistant chip in most PCs, networking equipment, and industrial controllers.
From its beginnings more than 20 years ago, the TPM was designed to protect and manage private encryption keys. Some things you can do with a TPM include:
- Manage encryption keys
- Full-disk encryption
- Augment smart cards, fingerprint readers, and fobs for multi-factor authentication
- Encrypt files and folders to control access
- Establish state information to enable endpoint integrity
- Hash state information prior to hard drive shutdown for endpoint integrity
- Enable more secure VPN, remote, and wireless access
- Use in conjunction with Full Disk Encryption to restrict access to sensitive data
This blog, however, will focus on how the TPM enables secret and unclonable authentication of digital identities to service providers, using asymmetric key cryptography and other industry protocols. The hardware-based TPM securely stores the private encryption key, which is used to authenticate a digital identity with service providers in possession of the public encryption key.

A comparison of two methods to prove a user’s digital identity: software and a password (top) versus the hardware-based TPM and asymmetric cryptography (bottom).
The benefit is that the private key is never exposed to attacks. On the other hand, passwords are exposed at rest or in transit across the network. This secret is used only within the TPM’s protections — away from software and only to provide the response to the service’s challenge to authenticate.
Why Is the TPM Important?
The TPM is a secure, tamper-resistant location for storing encryption keys and performing highly trusted cryptographic operations. Unlike a password, the private key remains protected inside the TPM, even in the event of:
- Stolen data and files (the private key can only be used by that TPM)
- A compromise of the Operating System
- A stolen computer
The TPM also provides strong supply chain assurance, helping to validate that the device's hardware and software components have not been tampered with or otherwise modified.
A TPM-enabled device can provide cryptographic proof of its hardware identity. Institutions can verify (and provide an audit trail) of the specific device used to execute transactions. Using Attestation, the TPM can also provide the identity of the firmware, the OS, and even applications.
Institutions can therefore have assurance that transactions have strong, key-based user authentication but they are also being executed on an authorized (and updated) device that has not been tampered with.
How Secure Is the TPM?
The TPM’s security is based on the long-standing concept of protecting critical data (such as secrets) by isolating them from hostile components — including the Operating System itself. This isolated area is called a Trusted Execution Environment (TEE).
While there are many types and products that make use of a TEE, most are proprietary.
- The TPM is an International Industry Standard with more than 20+ years of deployments and public evaluation. It is an International Organization for Standardization (ISO) standard (ISO/IEC 11889) accepted worldwide.
- Most TPMs have Federal Information Processing Standards (FIPS) 140 certification and have been evaluated by Common Criteria laboratories.
- TPM is mentioned as an example authentication token in NIST SP 800-63-3 and can be used as a Multi Factor Authentication device.
- It is even recommended for use in critical infrastructure applications by ISO/IEC 62443.
How Beyond Identity Uses the TPM
Beyond Identity uses the TPM (and similar hardware modules on Macs and Android devices) to replace insecure passwords with a secure and cryptographically provable digital identity. And unlike passwords, the private key in the TPM is never exposed to the application or even the Operating System itself.
The tamper-resistant TPM stores encryption keys in such a way where they can not be read or removed from the device, making it a secure way to protect and bind a user’s digital identity to a device. This enables strong authentication of users and the ability to control access to only authorized devices.
Conclusion
Here’s a summary of the benefit of using the TPM for a person’s authentication:
- The TPM is a proven International standard with 20+ years of deployment.
- The TPM’s specifications are public with the reference source code publicly available.
- Most TPM’s are evaluated using national and international standards.
- The TPM protects the asymmetric key’s secrets from software adversaries even if the attacker has control of the operating system.
Beyond Identity uses the private key stored in the TPM to provide unforgeable, strong authentication. Click here to learn more on a demo with one of our engineers.
If you’re working from a modern computer, chances are there’s a TPM inside, soldered onto the motherboard of your device. TPMs are unique to Windows and Linux PCs. Apple devices and Androids have something similar, which operates on many of the same principles discussed in the article. With Apple, it’s called the Secure Enclave and with Android, it’s called the Android Knox. But our focus here will be describing the TPM specifically.
If you’re not familiar with the TPM (Trusted Platform Module), it is in some ways similar to the SmartCard chip embedded in your credit card.
The smartchip's purpose is to securely authenticate the card during transactions, using asymmetric key cryptography.
Think of the TPM as a SmartCard or Credit Card chip that is permanently attached to the computer. Just like SmartCard chips secure credit cards, TPMs secure computer hardware with cryptographic keys.
What Is A TPM?
A TPM or Trusted Platform Module is a hardware-based, tamper-resistant chip in most PCs, networking equipment, and industrial controllers.
From its beginnings more than 20 years ago, the TPM was designed to protect and manage private encryption keys. Some things you can do with a TPM include:
- Manage encryption keys
- Full-disk encryption
- Augment smart cards, fingerprint readers, and fobs for multi-factor authentication
- Encrypt files and folders to control access
- Establish state information to enable endpoint integrity
- Hash state information prior to hard drive shutdown for endpoint integrity
- Enable more secure VPN, remote, and wireless access
- Use in conjunction with Full Disk Encryption to restrict access to sensitive data
This blog, however, will focus on how the TPM enables secret and unclonable authentication of digital identities to service providers, using asymmetric key cryptography and other industry protocols. The hardware-based TPM securely stores the private encryption key, which is used to authenticate a digital identity with service providers in possession of the public encryption key.

A comparison of two methods to prove a user’s digital identity: software and a password (top) versus the hardware-based TPM and asymmetric cryptography (bottom).
The benefit is that the private key is never exposed to attacks. On the other hand, passwords are exposed at rest or in transit across the network. This secret is used only within the TPM’s protections — away from software and only to provide the response to the service’s challenge to authenticate.
Why Is the TPM Important?
The TPM is a secure, tamper-resistant location for storing encryption keys and performing highly trusted cryptographic operations. Unlike a password, the private key remains protected inside the TPM, even in the event of:
- Stolen data and files (the private key can only be used by that TPM)
- A compromise of the Operating System
- A stolen computer
The TPM also provides strong supply chain assurance, helping to validate that the device's hardware and software components have not been tampered with or otherwise modified.
A TPM-enabled device can provide cryptographic proof of its hardware identity. Institutions can verify (and provide an audit trail) of the specific device used to execute transactions. Using Attestation, the TPM can also provide the identity of the firmware, the OS, and even applications.
Institutions can therefore have assurance that transactions have strong, key-based user authentication but they are also being executed on an authorized (and updated) device that has not been tampered with.
How Secure Is the TPM?
The TPM’s security is based on the long-standing concept of protecting critical data (such as secrets) by isolating them from hostile components — including the Operating System itself. This isolated area is called a Trusted Execution Environment (TEE).
While there are many types and products that make use of a TEE, most are proprietary.
- The TPM is an International Industry Standard with more than 20+ years of deployments and public evaluation. It is an International Organization for Standardization (ISO) standard (ISO/IEC 11889) accepted worldwide.
- Most TPMs have Federal Information Processing Standards (FIPS) 140 certification and have been evaluated by Common Criteria laboratories.
- TPM is mentioned as an example authentication token in NIST SP 800-63-3 and can be used as a Multi Factor Authentication device.
- It is even recommended for use in critical infrastructure applications by ISO/IEC 62443.
How Beyond Identity Uses the TPM
Beyond Identity uses the TPM (and similar hardware modules on Macs and Android devices) to replace insecure passwords with a secure and cryptographically provable digital identity. And unlike passwords, the private key in the TPM is never exposed to the application or even the Operating System itself.
The tamper-resistant TPM stores encryption keys in such a way where they can not be read or removed from the device, making it a secure way to protect and bind a user’s digital identity to a device. This enables strong authentication of users and the ability to control access to only authorized devices.
Conclusion
Here’s a summary of the benefit of using the TPM for a person’s authentication:
- The TPM is a proven International standard with 20+ years of deployment.
- The TPM’s specifications are public with the reference source code publicly available.
- Most TPM’s are evaluated using national and international standards.
- The TPM protects the asymmetric key’s secrets from software adversaries even if the attacker has control of the operating system.
Beyond Identity uses the private key stored in the TPM to provide unforgeable, strong authentication. Click here to learn more on a demo with one of our engineers.






.png)






.avif)



.avif)






.avif)

