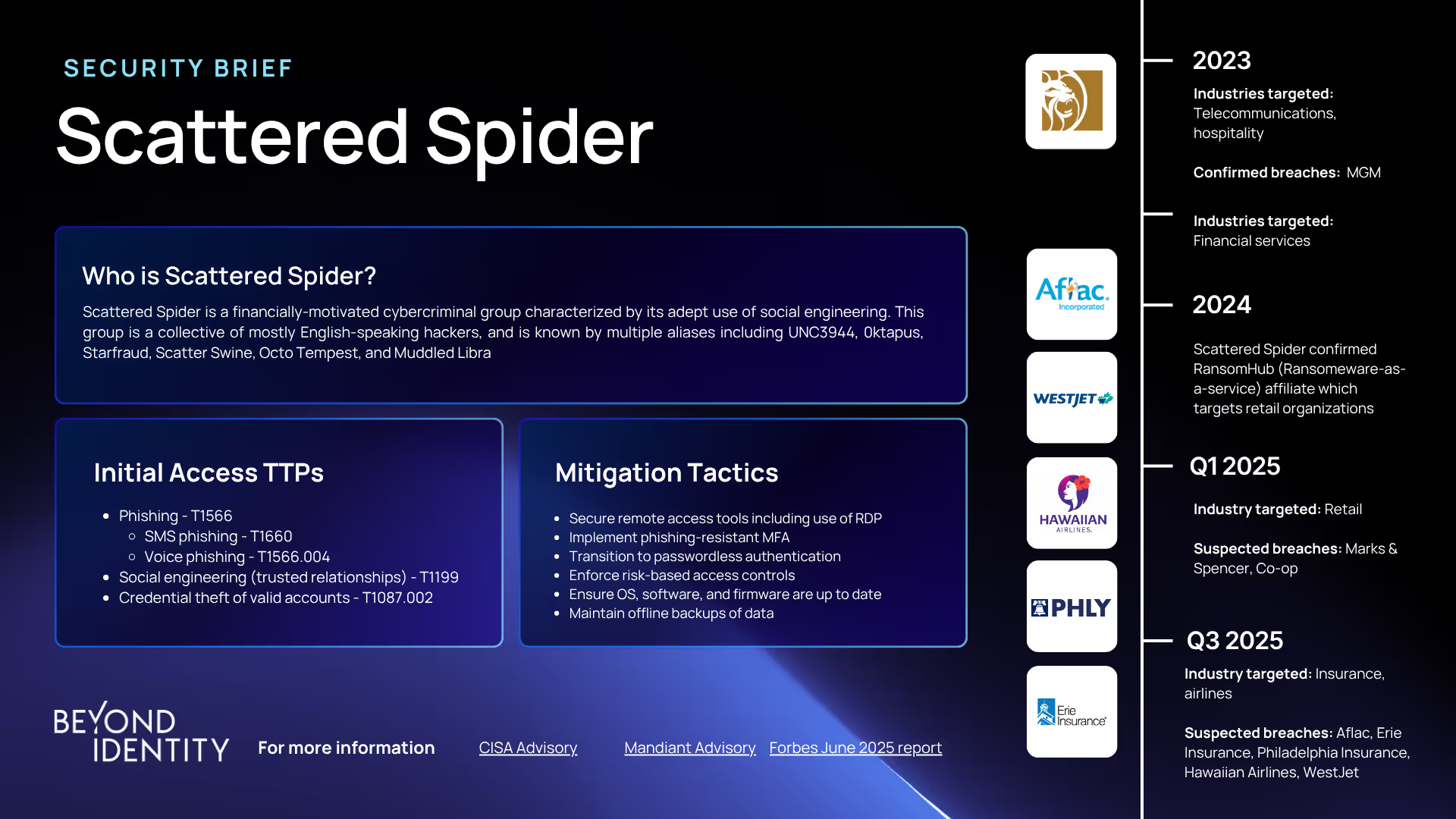
Scattered Spider: How to Effectively Defend Against This Aggressive Threat
According to a new report from Forbes, the FBI has issued a new cybersecurity warning about Scattered Spider, a financially motivated threat group now expanding its attacks beyond retail into the aviation and insurance sectors. The group uses social engineering tactics, often impersonating employees, to bypass multi-factor authentication by tricking IT help desks into enrolling unauthorized devices.
According to cybersecurity researchers, the group is likely to adopt AI-powered impersonation tactics next, making attacks even harder to detect. The FBI urges all organizations, not just those in aviation, to review their help desk procedures, watch for unusual MFA enrollment requests, and stay vigilant, especially given Scattered Spider’s reliance on exploiting human trust.
Scattered Spider’s MFA bypass technique in action
Forbes cites experts saying,
“leveraging phishing frameworks like Evilginx, and social engineering methods including video calls, initial access into targets such as the technology, finance, and retail trade sectors, has made Scattered Spider a threat to be taken very seriously indeed.”
It makes sense that Scattered Spider would rely on tools like Evilginx. Evilginx works by impersonating legitimate login portals and hijacking credentials and session tokens in real time. That means attackers don’t need to steal your password—they just need to trick the user once and Scattered Spider is well-known for their effective social engineering techniques.
If you want to see the MFA bypass flow with Evilginx in action, here's a demo:
Characteristics of secure access
The good news is that defenders can protect their environment from attackers such as Scattered Spider. Adding to CISA and Mandiant's recommendations, here are the technical characteristics of effective defense that stops the TTPs associated with Scattered Spider.
Phishing-resistant MFA
- Elimination of shared secrets: Remove shared secrets like passwords, PINs, and recovery questions across the authentication process.
- No weak fallbacks: Avoid fallback mechanisms that rely on weaker authentication factors, as these can reintroduce vulnerabilities.
- Device-bound credentials that can’t move: Bind credentials cryptographically to authenticated devices, ensuring they cannot be stolen, synced, or reused elsewhere.
- Cryptographic verifier validation: Use cryptographic methods to confirm the identity of the verifier and remove the threat of adversary-in-the-middle attacks
Risk-based access policy
- Real-time device posture: It’s not just users that login, it’s also their device. Gain visibility into device security posture over all authenticating devices including managed and unmanaged devices prior to allowing access.
- Integrated risk telemetry: Leverage risk telemetry from all available security tools including EDRs, XDRs, MDM, ZTNA, and more to make informed access decisions.
- Unified policy engine: Combine first party and third-party risk signals in a single decision plane to enforce risk-based access at point of authentication and continuously.
Continuous authentication
Authenticating the user and validating device compliance at the point of access is an important first step, but what happens if a user changes their device configurations? Even legitimate users can unknowingly create risks by disabling the firewall, downloading malicious files, or installing software with known vulnerabilities. Continuous evaluation of both device and user risks is essential to ensure that no exploitable device becomes a gateway for bad actors.
Secure access can be a reality
See how it works in your environment. Get a demo
According to a new report from Forbes, the FBI has issued a new cybersecurity warning about Scattered Spider, a financially motivated threat group now expanding its attacks beyond retail into the aviation and insurance sectors. The group uses social engineering tactics, often impersonating employees, to bypass multi-factor authentication by tricking IT help desks into enrolling unauthorized devices.
According to cybersecurity researchers, the group is likely to adopt AI-powered impersonation tactics next, making attacks even harder to detect. The FBI urges all organizations, not just those in aviation, to review their help desk procedures, watch for unusual MFA enrollment requests, and stay vigilant, especially given Scattered Spider’s reliance on exploiting human trust.

Scattered Spider’s MFA bypass technique in action
Forbes cites experts saying,
“leveraging phishing frameworks like Evilginx, and social engineering methods including video calls, initial access into targets such as the technology, finance, and retail trade sectors, has made Scattered Spider a threat to be taken very seriously indeed.”
It makes sense that Scattered Spider would rely on tools like Evilginx. Evilginx works by impersonating legitimate login portals and hijacking credentials and session tokens in real time. That means attackers don’t need to steal your password—they just need to trick the user once and Scattered Spider is well-known for their effective social engineering techniques.
If you want to see the MFA bypass flow with Evilginx in action, here's a demo:
Characteristics of secure access
The good news is that defenders can protect their environment from attackers such as Scattered Spider. Adding to CISA and Mandiant's recommendations, here are the technical characteristics of effective defense that stops the TTPs associated with Scattered Spider.
Phishing-resistant MFA
- Elimination of shared secrets: Remove shared secrets like passwords, PINs, and recovery questions across the authentication process.
- No weak fallbacks: Avoid fallback mechanisms that rely on weaker authentication factors, as these can reintroduce vulnerabilities.
- Device-bound credentials that can’t move: Bind credentials cryptographically to authenticated devices, ensuring they cannot be stolen, synced, or reused elsewhere.
- Cryptographic verifier validation: Use cryptographic methods to confirm the identity of the verifier and remove the threat of adversary-in-the-middle attacks
Risk-based access policy
- Real-time device posture: It’s not just users that login, it’s also their device. Gain visibility into device security posture over all authenticating devices including managed and unmanaged devices prior to allowing access.
- Integrated risk telemetry: Leverage risk telemetry from all available security tools including EDRs, XDRs, MDM, ZTNA, and more to make informed access decisions.
- Unified policy engine: Combine first party and third-party risk signals in a single decision plane to enforce risk-based access at point of authentication and continuously.
Continuous authentication
Authenticating the user and validating device compliance at the point of access is an important first step, but what happens if a user changes their device configurations? Even legitimate users can unknowingly create risks by disabling the firewall, downloading malicious files, or installing software with known vulnerabilities. Continuous evaluation of both device and user risks is essential to ensure that no exploitable device becomes a gateway for bad actors.
Secure access can be a reality
See how it works in your environment. Get a demo
According to a new report from Forbes, the FBI has issued a new cybersecurity warning about Scattered Spider, a financially motivated threat group now expanding its attacks beyond retail into the aviation and insurance sectors. The group uses social engineering tactics, often impersonating employees, to bypass multi-factor authentication by tricking IT help desks into enrolling unauthorized devices.
According to cybersecurity researchers, the group is likely to adopt AI-powered impersonation tactics next, making attacks even harder to detect. The FBI urges all organizations, not just those in aviation, to review their help desk procedures, watch for unusual MFA enrollment requests, and stay vigilant, especially given Scattered Spider’s reliance on exploiting human trust.

Scattered Spider’s MFA bypass technique in action
Forbes cites experts saying,
“leveraging phishing frameworks like Evilginx, and social engineering methods including video calls, initial access into targets such as the technology, finance, and retail trade sectors, has made Scattered Spider a threat to be taken very seriously indeed.”
It makes sense that Scattered Spider would rely on tools like Evilginx. Evilginx works by impersonating legitimate login portals and hijacking credentials and session tokens in real time. That means attackers don’t need to steal your password—they just need to trick the user once and Scattered Spider is well-known for their effective social engineering techniques.
If you want to see the MFA bypass flow with Evilginx in action, here's a demo:
Characteristics of secure access
The good news is that defenders can protect their environment from attackers such as Scattered Spider. Adding to CISA and Mandiant's recommendations, here are the technical characteristics of effective defense that stops the TTPs associated with Scattered Spider.
Phishing-resistant MFA
- Elimination of shared secrets: Remove shared secrets like passwords, PINs, and recovery questions across the authentication process.
- No weak fallbacks: Avoid fallback mechanisms that rely on weaker authentication factors, as these can reintroduce vulnerabilities.
- Device-bound credentials that can’t move: Bind credentials cryptographically to authenticated devices, ensuring they cannot be stolen, synced, or reused elsewhere.
- Cryptographic verifier validation: Use cryptographic methods to confirm the identity of the verifier and remove the threat of adversary-in-the-middle attacks
Risk-based access policy
- Real-time device posture: It’s not just users that login, it’s also their device. Gain visibility into device security posture over all authenticating devices including managed and unmanaged devices prior to allowing access.
- Integrated risk telemetry: Leverage risk telemetry from all available security tools including EDRs, XDRs, MDM, ZTNA, and more to make informed access decisions.
- Unified policy engine: Combine first party and third-party risk signals in a single decision plane to enforce risk-based access at point of authentication and continuously.
Continuous authentication
Authenticating the user and validating device compliance at the point of access is an important first step, but what happens if a user changes their device configurations? Even legitimate users can unknowingly create risks by disabling the firewall, downloading malicious files, or installing software with known vulnerabilities. Continuous evaluation of both device and user risks is essential to ensure that no exploitable device becomes a gateway for bad actors.
Secure access can be a reality
See how it works in your environment. Get a demo

.avif)





.png)






.avif)



.avif)






.avif)

