History of Online Security, from CAPTCHA to Multi-Factor Authentication
As more people have been moving their office work to remote computers, trying to hold secure meetings over technologies like Zoom from home or coffee shops is increasingly common. While some criminal activities like skimming your credit card at gas pumps may be falling out of fashion as fewer people commute every day, other activities, such as classic hacking, can thrive as long as people are using their computers to work remotely, opening new opportunities for hackers. In the past five years, there have been more than 2.76 million complaints to the FBI regarding various cybercrimes, including identity theft, extortion, and phishing, with losses exceeding $6.9 billion, according to 2021 data from the FBI.
With security top of mind, Beyond Identity collected information from think tanks, news reports, and industry professionals to understand landmark moments in internet security over the past 50 years. The internet began as a classified government program to connect different important military and government facilities. The first outside users were from universities, where very smart people have long been inventing new ways to poke holes in the internet as a form of preventive research.
From the first antivirus program in the 1970s to the zero-trust protocols of today, security has evolved over the years as developers strive to stay one step ahead of hackers.

1970s: Antivirus software
A computer virus is a piece of software the user typically downloads when they click on an infected email attachment or another file. The first virus was a 1970s program called Creeper, which was designed to crawl the early internet known as ARPANET, according to a report from Cyber Magazine. Like modern penetration testers, researchers wanted to see how they could hypothetically invade their own system. In response, email inventor Ray Tomlinson wrote a program he named Reaper, which chased and destroyed Creeper. That makes Reaper the first-ever antivirus program, creating a genre that endures today.
Safeguard sensitive resources
Verify device trust across all endpoints and positively verify who is behind every device.

1970s: Encryption
Cryptography is the blanket term for the field of mathematics and security that involves setting codes and encoding information for safe transit. Encryption simply means applying a cryptographic algorithm to a piece of information. With computers, one of the first examples of network encryption came from IBM in the early 1970s. The first standard encryption algorithm, known as the data encryption standard, lasted for more than 20 years before computer calculations finally broke it. Today, researchers race to keep their mathematics ahead of those who are trying to use the same computing power to break the algorithms.
Modern digital security tools
Access critical data from anywhere while blocking digital threats using a secure remote access solution.
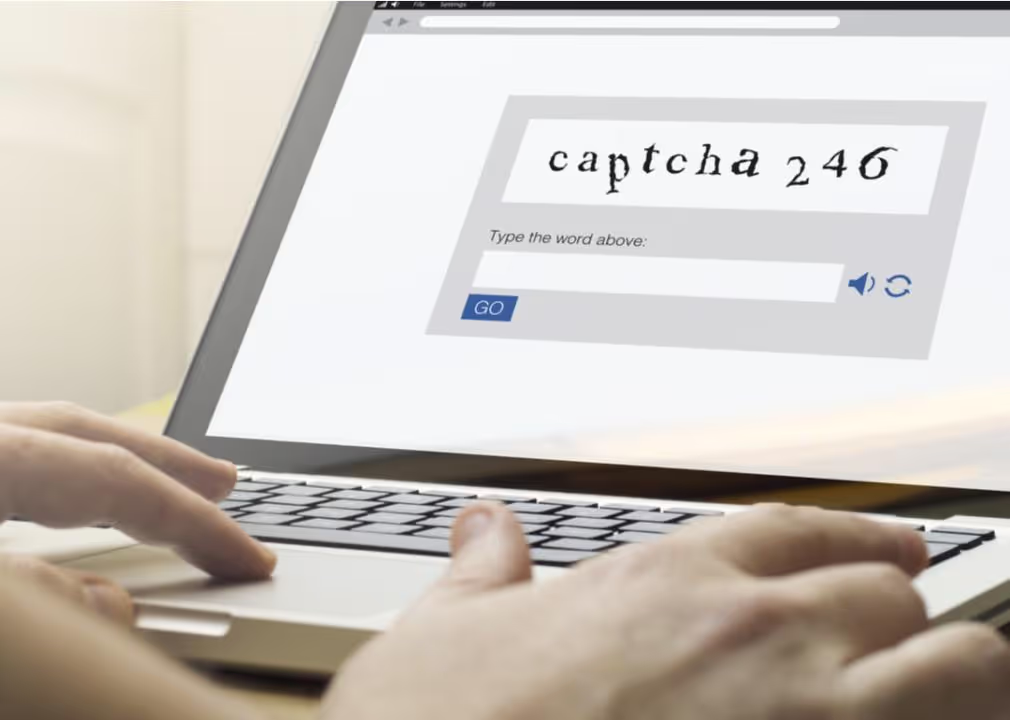
2000s: CAPTCHA
In the late 1990s, the internet was rapidly growing in popularity, with intrusive technology like cookies and viruses rapidly following. People realized they could use bots, or automated processes, to post spam comments on websites at a massive scale, for example.
Researchers at Carnegie Mellon University invented CAPTCHA in 2000 as a way to combat those bots. Computer programs struggle with many tasks humans do almost without thinking, especially tasks that involve processing visual information. CAPTCHA is now considered deprecated in most usages, but it paved the way for other forms of security like the popular “Which of these pictures shows a motorcycle?” CAPTCHAs that are still used today.

2000s: Multi-factor authentication
Multi-factor (or two-factor) authentication is a form of login technology that asks users to offer a second, corroborative piece of information along with their simple username and password. This may come as a text message or through an app like Google Authenticator. While this technology dates back to the 1980s, it was first introduced to consumers in the 2000s when it rolled out to banks. The New York Times reported on the rise of two-factor authentication in 2004, a time when many Americans didn’t even have broadband internet yet.
Streamline user experiences
Implement passwordless MFA to empower user experiences and protect against data loss.
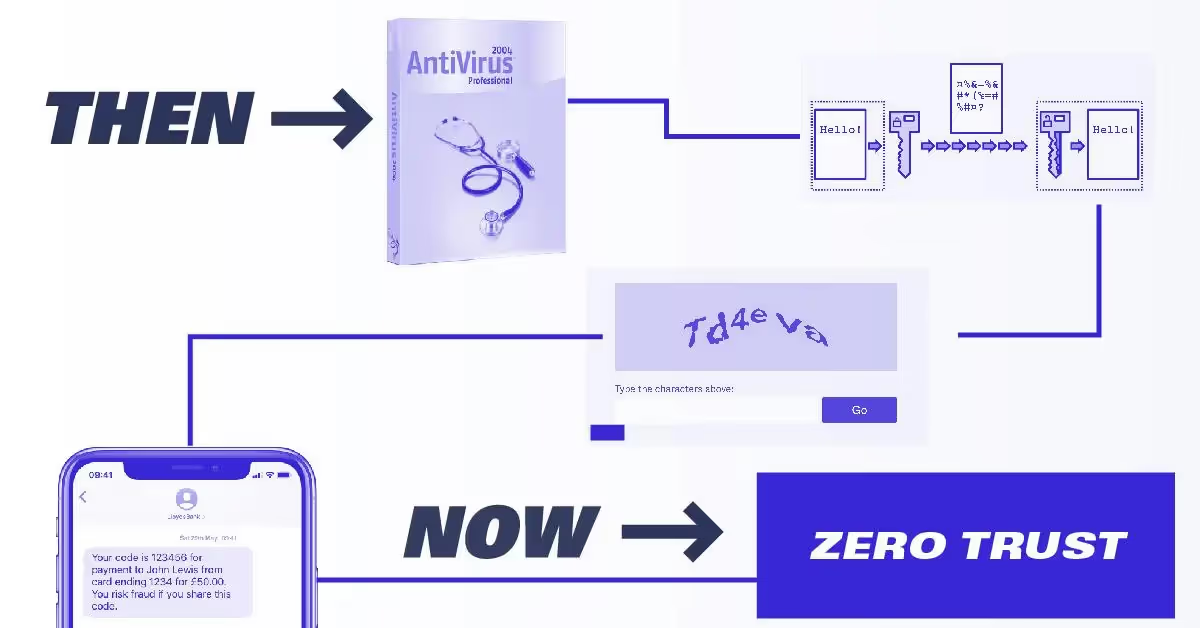
2010s: Zero trust
If you’ve read this far, you may be starting to feel like no piece of data is ever safe. You’re not alone. Computer security is deeply complex and ever-changing because of the equal pace at which criminals and other bad actors are following new forms of intrusion. One of the latest paradigms is that of zero trust, a term that means doing away with previous ideas like “trusted devices.” This means always verifying security information on each device trying to access a network. Users would also only be allowed access to data and information needed to complete a request.
As more people have been moving their office work to remote computers, trying to hold secure meetings over technologies like Zoom from home or coffee shops is increasingly common. While some criminal activities like skimming your credit card at gas pumps may be falling out of fashion as fewer people commute every day, other activities, such as classic hacking, can thrive as long as people are using their computers to work remotely, opening new opportunities for hackers. In the past five years, there have been more than 2.76 million complaints to the FBI regarding various cybercrimes, including identity theft, extortion, and phishing, with losses exceeding $6.9 billion, according to 2021 data from the FBI.
With security top of mind, Beyond Identity collected information from think tanks, news reports, and industry professionals to understand landmark moments in internet security over the past 50 years. The internet began as a classified government program to connect different important military and government facilities. The first outside users were from universities, where very smart people have long been inventing new ways to poke holes in the internet as a form of preventive research.
From the first antivirus program in the 1970s to the zero-trust protocols of today, security has evolved over the years as developers strive to stay one step ahead of hackers.

1970s: Antivirus software
A computer virus is a piece of software the user typically downloads when they click on an infected email attachment or another file. The first virus was a 1970s program called Creeper, which was designed to crawl the early internet known as ARPANET, according to a report from Cyber Magazine. Like modern penetration testers, researchers wanted to see how they could hypothetically invade their own system. In response, email inventor Ray Tomlinson wrote a program he named Reaper, which chased and destroyed Creeper. That makes Reaper the first-ever antivirus program, creating a genre that endures today.
Safeguard sensitive resources
Verify device trust across all endpoints and positively verify who is behind every device.

1970s: Encryption
Cryptography is the blanket term for the field of mathematics and security that involves setting codes and encoding information for safe transit. Encryption simply means applying a cryptographic algorithm to a piece of information. With computers, one of the first examples of network encryption came from IBM in the early 1970s. The first standard encryption algorithm, known as the data encryption standard, lasted for more than 20 years before computer calculations finally broke it. Today, researchers race to keep their mathematics ahead of those who are trying to use the same computing power to break the algorithms.
Modern digital security tools
Access critical data from anywhere while blocking digital threats using a secure remote access solution.

2000s: CAPTCHA
In the late 1990s, the internet was rapidly growing in popularity, with intrusive technology like cookies and viruses rapidly following. People realized they could use bots, or automated processes, to post spam comments on websites at a massive scale, for example.
Researchers at Carnegie Mellon University invented CAPTCHA in 2000 as a way to combat those bots. Computer programs struggle with many tasks humans do almost without thinking, especially tasks that involve processing visual information. CAPTCHA is now considered deprecated in most usages, but it paved the way for other forms of security like the popular “Which of these pictures shows a motorcycle?” CAPTCHAs that are still used today.

2000s: Multi-factor authentication
Multi-factor (or two-factor) authentication is a form of login technology that asks users to offer a second, corroborative piece of information along with their simple username and password. This may come as a text message or through an app like Google Authenticator. While this technology dates back to the 1980s, it was first introduced to consumers in the 2000s when it rolled out to banks. The New York Times reported on the rise of two-factor authentication in 2004, a time when many Americans didn’t even have broadband internet yet.
Streamline user experiences
Implement passwordless MFA to empower user experiences and protect against data loss.

2010s: Zero trust
If you’ve read this far, you may be starting to feel like no piece of data is ever safe. You’re not alone. Computer security is deeply complex and ever-changing because of the equal pace at which criminals and other bad actors are following new forms of intrusion. One of the latest paradigms is that of zero trust, a term that means doing away with previous ideas like “trusted devices.” This means always verifying security information on each device trying to access a network. Users would also only be allowed access to data and information needed to complete a request.
As more people have been moving their office work to remote computers, trying to hold secure meetings over technologies like Zoom from home or coffee shops is increasingly common. While some criminal activities like skimming your credit card at gas pumps may be falling out of fashion as fewer people commute every day, other activities, such as classic hacking, can thrive as long as people are using their computers to work remotely, opening new opportunities for hackers. In the past five years, there have been more than 2.76 million complaints to the FBI regarding various cybercrimes, including identity theft, extortion, and phishing, with losses exceeding $6.9 billion, according to 2021 data from the FBI.
With security top of mind, Beyond Identity collected information from think tanks, news reports, and industry professionals to understand landmark moments in internet security over the past 50 years. The internet began as a classified government program to connect different important military and government facilities. The first outside users were from universities, where very smart people have long been inventing new ways to poke holes in the internet as a form of preventive research.
From the first antivirus program in the 1970s to the zero-trust protocols of today, security has evolved over the years as developers strive to stay one step ahead of hackers.

1970s: Antivirus software
A computer virus is a piece of software the user typically downloads when they click on an infected email attachment or another file. The first virus was a 1970s program called Creeper, which was designed to crawl the early internet known as ARPANET, according to a report from Cyber Magazine. Like modern penetration testers, researchers wanted to see how they could hypothetically invade their own system. In response, email inventor Ray Tomlinson wrote a program he named Reaper, which chased and destroyed Creeper. That makes Reaper the first-ever antivirus program, creating a genre that endures today.
Safeguard sensitive resources
Verify device trust across all endpoints and positively verify who is behind every device.

1970s: Encryption
Cryptography is the blanket term for the field of mathematics and security that involves setting codes and encoding information for safe transit. Encryption simply means applying a cryptographic algorithm to a piece of information. With computers, one of the first examples of network encryption came from IBM in the early 1970s. The first standard encryption algorithm, known as the data encryption standard, lasted for more than 20 years before computer calculations finally broke it. Today, researchers race to keep their mathematics ahead of those who are trying to use the same computing power to break the algorithms.
Modern digital security tools
Access critical data from anywhere while blocking digital threats using a secure remote access solution.

2000s: CAPTCHA
In the late 1990s, the internet was rapidly growing in popularity, with intrusive technology like cookies and viruses rapidly following. People realized they could use bots, or automated processes, to post spam comments on websites at a massive scale, for example.
Researchers at Carnegie Mellon University invented CAPTCHA in 2000 as a way to combat those bots. Computer programs struggle with many tasks humans do almost without thinking, especially tasks that involve processing visual information. CAPTCHA is now considered deprecated in most usages, but it paved the way for other forms of security like the popular “Which of these pictures shows a motorcycle?” CAPTCHAs that are still used today.

2000s: Multi-factor authentication
Multi-factor (or two-factor) authentication is a form of login technology that asks users to offer a second, corroborative piece of information along with their simple username and password. This may come as a text message or through an app like Google Authenticator. While this technology dates back to the 1980s, it was first introduced to consumers in the 2000s when it rolled out to banks. The New York Times reported on the rise of two-factor authentication in 2004, a time when many Americans didn’t even have broadband internet yet.
Streamline user experiences
Implement passwordless MFA to empower user experiences and protect against data loss.

2010s: Zero trust
If you’ve read this far, you may be starting to feel like no piece of data is ever safe. You’re not alone. Computer security is deeply complex and ever-changing because of the equal pace at which criminals and other bad actors are following new forms of intrusion. One of the latest paradigms is that of zero trust, a term that means doing away with previous ideas like “trusted devices.” This means always verifying security information on each device trying to access a network. Users would also only be allowed access to data and information needed to complete a request.






.png)






.avif)



.avif)






.avif)

