Four Ways to Make Quick Gains in Zero Trust Maturity
The cybersecurity landscape is becoming more and more vulnerable to attacks that are both cost-effective and powerful. These attacks use techniques like MFA bypass and Initial Access Brokers with stolen credentials. To tackle this issue, organizations must implement a zero trust security architecture emphasizing the importance of continuous, phishing-resistant MFA.
One of the most critical aspects of this architecture is the concept of device trust. This means that security protocols should validate not only the user's credentials but also the integrity of the device from which access is being sought. In other words, a secure fortress requires vigilant gatekeepers to ensure that a breach of credentials doesn't equate to a breach of the system.
Strong authentication and device trust directly address zero trust security architecture’s Identity and Device pillars. Unfortunately, many incumbent identity and security vendors continue to misdirect the market by redefining phishing resistance, implementing weak device trust, and preserving suboptimal security defaults.
Now more than ever, CIOs and CISOs need to lead their organizations toward a pragmatic and structured approach, like the one outlined by CISA’s Zero Trust Maturity Model. This model provides a well-articulated pathway towards continuous, automated access reevaluation and efficient cross-system integrations, which aligns with NIST's robust security recommendations.
The urgency to address these issues is palpable, and the strategy is clear: a comprehensive, neutrally endorsed, proactive, and interconnected security approach that thwarts today’s adversaries and their tactics while providing a firm foundation for an AI and cloud-intensive future.
The CISA Maturity Model
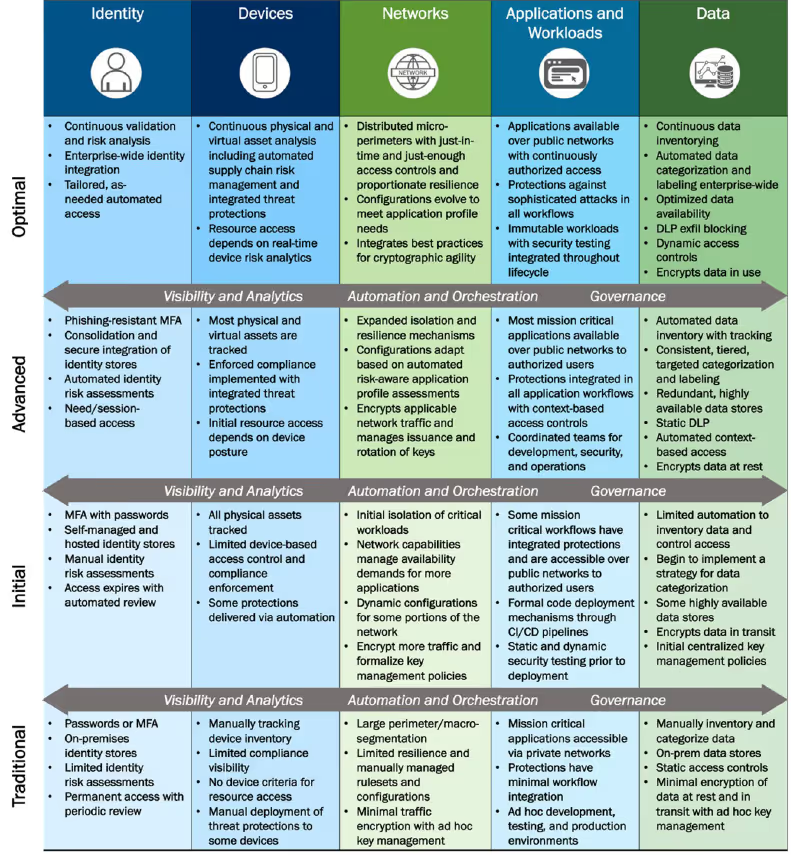
CISA created the Zero Trust Maturity Model (ZTMM) to help organizations create a roadmap for achieving Zero Trust maturity. In their report, they unpack five key areas called “pillars” that companies should focus on: identity, devices, networks, applications and workloads, and data.
The Zero Trust Maturity Model defines how to move from the lowest “Traditional” stage of maturity to “Optimal” or full maturity. Companies can elect to mature faster in one or more pillars since each is assigned its own maturity level.
The figure below provides an overview of the Zero Trust Maturity Model, with each pillar listed from left to right and the specific functions required to mature detailed from bottom to top. As you’ll see in the chart, moving to “continuous” and “automated” processes that occur in near real-time is the key to Zero Trust maturity.
Four ways to make quick gains in maturity
1. Address identity first
Identity is the attributes that describe a user or entity. Cybercriminals most frequently attack the identity pillar through phishing, stolen credentials, and social engineering.
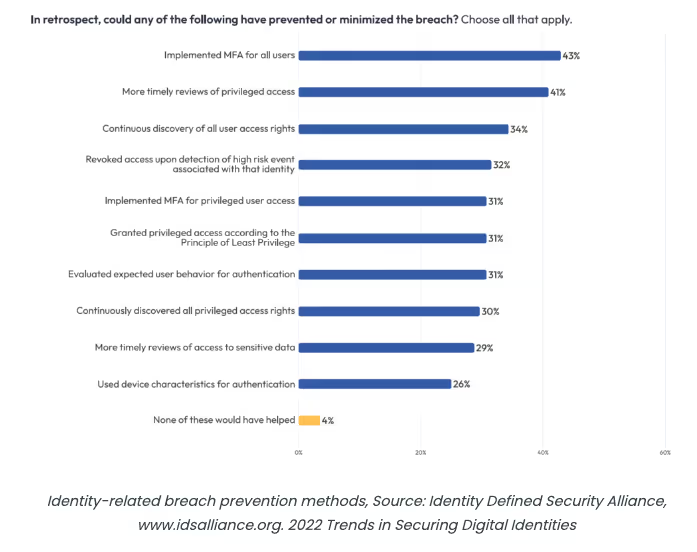
In one recent survey by Trends in Security Digital Identities, 84% of respondents said their company had an identity-related attack that year. Respondents overwhelmingly said implementing MFA and better privileged user access controls would have prevented the attacks. Both of these elements are part of the Zero Trust Maturity Model for Identity, showing just how vital it is to address the identity pillar first.
The goal of identity maturity is ensuring the right user is given access to what they need, when they need it, without giving them access to more than they require.
The table below from the Zero Trust Maturity Model shows the improvements a company needs to make from passwords and static access to continuous validation with phishing-resistant MFA.
2. Link together identity and devices
According to CISA, a device is any asset that connects to a network “including its hardware, software, firmware, etc.” The number of devices companies manage today continues to grow. The need to secure everything from printers to employee mobile phones can be challenging for IT leaders.
To mature in the device pillar, device trust must be factored into authentication and access decisions. When devices are bound to identity for authentication, companies have even more ways to verify that the right user, using only a trusted device, can access networks and resources. Data must be made shareable across the two pillars to enable this functionality.
For Optimal maturity with CISA’s ZTMM, device checks must move from one-time validation to real-time and continuous. The table below shows the steps required to move from Traditional to Optimal in the device pillar.
3. Feed your zero trust policy engine with security telemetry
The policy engine is a key component of zero trust architecture. It houses company rules around access, device security, and authentication. But the policy engine can only check rules against the data it’s given. Therefore, the more information you can feed it regarding security, the more accurate and thorough its enforcement becomes. Mature companies link device security to their policy engine and data from security and IT management tools. That’s where an XDR solution comes in.
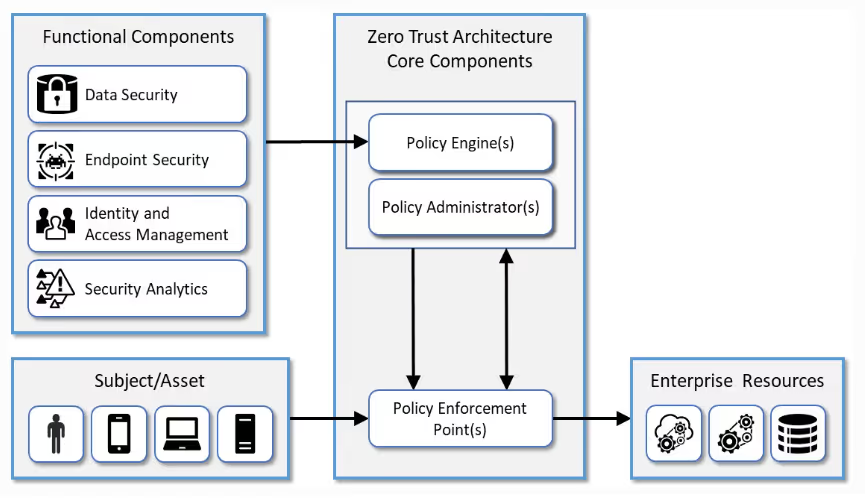
Here is a great example of a Zero Trust authentication policy in action:
- If: A device makes an access request
- And if: It does not have an active EDR agent on it
- Then: Do not authenticate
- And: Send an alert to the Security Operations Center
- And: Generate a ticket on the IT service management system and notify the user of the need to comply with device security policies
4. Prioritize “continuous” and “automated”
The most common theme across all pillars of the Zero Trust Maturity Model is that continuous and automated processes are required for Optimal maturity. Continuous checks are needed because hackers who log in with compromised credentials may wait a while before acting, or authenticated users may remove a firewall or antivirus software after authentication.
Automation is what enables continuous processes. Humans simply can’t keep pace with what’s required for zero trust maturity. Automated workflows that cross the Zero Trust Maturity Model pillars allow companies to move fast enough to stop cyberattacks before they happen.
Move to optimal Zero Trust maturity with Beyond Identity
The journey from Traditional to Optimal maturity can be daunting, but it doesn’t have to be. With Beyond Identity, your organization can immediately jump from Traditional to Optimal in the Identity and Device pillars.
Our Zero Trust Authentication is passwordless, phishing-resistant, and easy to use. We’ve already built in continuous and automated processes, decreasing your time-to-deployment.
To learn more about Zero Trust maturity, download A Practitioner’s Guide to the CISA Zero Trust Maturity Model.
The cybersecurity landscape is becoming more and more vulnerable to attacks that are both cost-effective and powerful. These attacks use techniques like MFA bypass and Initial Access Brokers with stolen credentials. To tackle this issue, organizations must implement a zero trust security architecture emphasizing the importance of continuous, phishing-resistant MFA.
One of the most critical aspects of this architecture is the concept of device trust. This means that security protocols should validate not only the user's credentials but also the integrity of the device from which access is being sought. In other words, a secure fortress requires vigilant gatekeepers to ensure that a breach of credentials doesn't equate to a breach of the system.
Strong authentication and device trust directly address zero trust security architecture’s Identity and Device pillars. Unfortunately, many incumbent identity and security vendors continue to misdirect the market by redefining phishing resistance, implementing weak device trust, and preserving suboptimal security defaults.
Now more than ever, CIOs and CISOs need to lead their organizations toward a pragmatic and structured approach, like the one outlined by CISA’s Zero Trust Maturity Model. This model provides a well-articulated pathway towards continuous, automated access reevaluation and efficient cross-system integrations, which aligns with NIST's robust security recommendations.
The urgency to address these issues is palpable, and the strategy is clear: a comprehensive, neutrally endorsed, proactive, and interconnected security approach that thwarts today’s adversaries and their tactics while providing a firm foundation for an AI and cloud-intensive future.
The CISA Maturity Model
CISA created the Zero Trust Maturity Model (ZTMM) to help organizations create a roadmap for achieving Zero Trust maturity. In their report, they unpack five key areas called “pillars” that companies should focus on: identity, devices, networks, applications and workloads, and data.
The Zero Trust Maturity Model defines how to move from the lowest “Traditional” stage of maturity to “Optimal” or full maturity. Companies can elect to mature faster in one or more pillars since each is assigned its own maturity level.
The figure below provides an overview of the Zero Trust Maturity Model, with each pillar listed from left to right and the specific functions required to mature detailed from bottom to top. As you’ll see in the chart, moving to “continuous” and “automated” processes that occur in near real-time is the key to Zero Trust maturity.

Four ways to make quick gains in maturity
1. Address identity first
Identity is the attributes that describe a user or entity. Cybercriminals most frequently attack the identity pillar through phishing, stolen credentials, and social engineering.
In one recent survey by Trends in Security Digital Identities, 84% of respondents said their company had an identity-related attack that year. Respondents overwhelmingly said implementing MFA and better privileged user access controls would have prevented the attacks. Both of these elements are part of the Zero Trust Maturity Model for Identity, showing just how vital it is to address the identity pillar first.

The goal of identity maturity is ensuring the right user is given access to what they need, when they need it, without giving them access to more than they require.
The table below from the Zero Trust Maturity Model shows the improvements a company needs to make from passwords and static access to continuous validation with phishing-resistant MFA.
2. Link together identity and devices
According to CISA, a device is any asset that connects to a network “including its hardware, software, firmware, etc.” The number of devices companies manage today continues to grow. The need to secure everything from printers to employee mobile phones can be challenging for IT leaders.
To mature in the device pillar, device trust must be factored into authentication and access decisions. When devices are bound to identity for authentication, companies have even more ways to verify that the right user, using only a trusted device, can access networks and resources. Data must be made shareable across the two pillars to enable this functionality.
For Optimal maturity with CISA’s ZTMM, device checks must move from one-time validation to real-time and continuous. The table below shows the steps required to move from Traditional to Optimal in the device pillar.
3. Feed your zero trust policy engine with security telemetry
The policy engine is a key component of zero trust architecture. It houses company rules around access, device security, and authentication. But the policy engine can only check rules against the data it’s given. Therefore, the more information you can feed it regarding security, the more accurate and thorough its enforcement becomes. Mature companies link device security to their policy engine and data from security and IT management tools. That’s where an XDR solution comes in.

Here is a great example of a Zero Trust authentication policy in action:
- If: A device makes an access request
- And if: It does not have an active EDR agent on it
- Then: Do not authenticate
- And: Send an alert to the Security Operations Center
- And: Generate a ticket on the IT service management system and notify the user of the need to comply with device security policies
4. Prioritize “continuous” and “automated”
The most common theme across all pillars of the Zero Trust Maturity Model is that continuous and automated processes are required for Optimal maturity. Continuous checks are needed because hackers who log in with compromised credentials may wait a while before acting, or authenticated users may remove a firewall or antivirus software after authentication.
Automation is what enables continuous processes. Humans simply can’t keep pace with what’s required for zero trust maturity. Automated workflows that cross the Zero Trust Maturity Model pillars allow companies to move fast enough to stop cyberattacks before they happen.
Move to optimal Zero Trust maturity with Beyond Identity
The journey from Traditional to Optimal maturity can be daunting, but it doesn’t have to be. With Beyond Identity, your organization can immediately jump from Traditional to Optimal in the Identity and Device pillars.
Our Zero Trust Authentication is passwordless, phishing-resistant, and easy to use. We’ve already built in continuous and automated processes, decreasing your time-to-deployment.
To learn more about Zero Trust maturity, download A Practitioner’s Guide to the CISA Zero Trust Maturity Model.
The cybersecurity landscape is becoming more and more vulnerable to attacks that are both cost-effective and powerful. These attacks use techniques like MFA bypass and Initial Access Brokers with stolen credentials. To tackle this issue, organizations must implement a zero trust security architecture emphasizing the importance of continuous, phishing-resistant MFA.
One of the most critical aspects of this architecture is the concept of device trust. This means that security protocols should validate not only the user's credentials but also the integrity of the device from which access is being sought. In other words, a secure fortress requires vigilant gatekeepers to ensure that a breach of credentials doesn't equate to a breach of the system.
Strong authentication and device trust directly address zero trust security architecture’s Identity and Device pillars. Unfortunately, many incumbent identity and security vendors continue to misdirect the market by redefining phishing resistance, implementing weak device trust, and preserving suboptimal security defaults.
Now more than ever, CIOs and CISOs need to lead their organizations toward a pragmatic and structured approach, like the one outlined by CISA’s Zero Trust Maturity Model. This model provides a well-articulated pathway towards continuous, automated access reevaluation and efficient cross-system integrations, which aligns with NIST's robust security recommendations.
The urgency to address these issues is palpable, and the strategy is clear: a comprehensive, neutrally endorsed, proactive, and interconnected security approach that thwarts today’s adversaries and their tactics while providing a firm foundation for an AI and cloud-intensive future.
The CISA Maturity Model
CISA created the Zero Trust Maturity Model (ZTMM) to help organizations create a roadmap for achieving Zero Trust maturity. In their report, they unpack five key areas called “pillars” that companies should focus on: identity, devices, networks, applications and workloads, and data.
The Zero Trust Maturity Model defines how to move from the lowest “Traditional” stage of maturity to “Optimal” or full maturity. Companies can elect to mature faster in one or more pillars since each is assigned its own maturity level.
The figure below provides an overview of the Zero Trust Maturity Model, with each pillar listed from left to right and the specific functions required to mature detailed from bottom to top. As you’ll see in the chart, moving to “continuous” and “automated” processes that occur in near real-time is the key to Zero Trust maturity.

Four ways to make quick gains in maturity
1. Address identity first
Identity is the attributes that describe a user or entity. Cybercriminals most frequently attack the identity pillar through phishing, stolen credentials, and social engineering.
In one recent survey by Trends in Security Digital Identities, 84% of respondents said their company had an identity-related attack that year. Respondents overwhelmingly said implementing MFA and better privileged user access controls would have prevented the attacks. Both of these elements are part of the Zero Trust Maturity Model for Identity, showing just how vital it is to address the identity pillar first.

The goal of identity maturity is ensuring the right user is given access to what they need, when they need it, without giving them access to more than they require.
The table below from the Zero Trust Maturity Model shows the improvements a company needs to make from passwords and static access to continuous validation with phishing-resistant MFA.
2. Link together identity and devices
According to CISA, a device is any asset that connects to a network “including its hardware, software, firmware, etc.” The number of devices companies manage today continues to grow. The need to secure everything from printers to employee mobile phones can be challenging for IT leaders.
To mature in the device pillar, device trust must be factored into authentication and access decisions. When devices are bound to identity for authentication, companies have even more ways to verify that the right user, using only a trusted device, can access networks and resources. Data must be made shareable across the two pillars to enable this functionality.
For Optimal maturity with CISA’s ZTMM, device checks must move from one-time validation to real-time and continuous. The table below shows the steps required to move from Traditional to Optimal in the device pillar.
3. Feed your zero trust policy engine with security telemetry
The policy engine is a key component of zero trust architecture. It houses company rules around access, device security, and authentication. But the policy engine can only check rules against the data it’s given. Therefore, the more information you can feed it regarding security, the more accurate and thorough its enforcement becomes. Mature companies link device security to their policy engine and data from security and IT management tools. That’s where an XDR solution comes in.

Here is a great example of a Zero Trust authentication policy in action:
- If: A device makes an access request
- And if: It does not have an active EDR agent on it
- Then: Do not authenticate
- And: Send an alert to the Security Operations Center
- And: Generate a ticket on the IT service management system and notify the user of the need to comply with device security policies
4. Prioritize “continuous” and “automated”
The most common theme across all pillars of the Zero Trust Maturity Model is that continuous and automated processes are required for Optimal maturity. Continuous checks are needed because hackers who log in with compromised credentials may wait a while before acting, or authenticated users may remove a firewall or antivirus software after authentication.
Automation is what enables continuous processes. Humans simply can’t keep pace with what’s required for zero trust maturity. Automated workflows that cross the Zero Trust Maturity Model pillars allow companies to move fast enough to stop cyberattacks before they happen.
Move to optimal Zero Trust maturity with Beyond Identity
The journey from Traditional to Optimal maturity can be daunting, but it doesn’t have to be. With Beyond Identity, your organization can immediately jump from Traditional to Optimal in the Identity and Device pillars.
Our Zero Trust Authentication is passwordless, phishing-resistant, and easy to use. We’ve already built in continuous and automated processes, decreasing your time-to-deployment.
To learn more about Zero Trust maturity, download A Practitioner’s Guide to the CISA Zero Trust Maturity Model.













.avif)
.avif)



.avif)






.avif)

