The Beyond Blog

22 Jan 2026
Beyond Identity Opens Early Access for the AI Security Suite
Gain visibility and control over autonomous AI agents with Beyond Identity's AI Security Suite. Enforce identity, device context, and data governance with cryptographic proof. Early access is now open!

05 Jan 2023
January 5, 2023
Getting Hacked Through a Video Game
Are certain consoles more prone to getting hacked than others? What kind of data is compromised? Read on to learn how hacks affect the gaming world.
15 Dec 2022
December 15, 2022
Hacker Tracker: December 2022
Read on for Beyond Identity's analysis of high-profile cyberattacks, and more, that took place during December 2022.

13 Dec 2022
December 13, 2022
Beyond Identity and CrowdStrike Integration: Advanced Attack Prevention and a Strong Zero Trust Foundation
Today our engineering team dropped a technical integration with CrowdStrike Falcon and this combination can help stop ransomware and account takeover attacks.

07 Dec 2022
December 7, 2022
Zscaler And Beyond Identity Introduce Integrations that Lower the Risk of Password-Based Breaches and Secure Application Access
The new Zscaler and Beyond Identity integration can help minimize breaches, shrink the attack surface, and secure application access.

07 Dec 2022
December 7, 2022
Identity: A Key Element to Zero Trust Authentication
Zero trust is built on the premise that the identity of any entity on your network should be continuously verified through MFA.
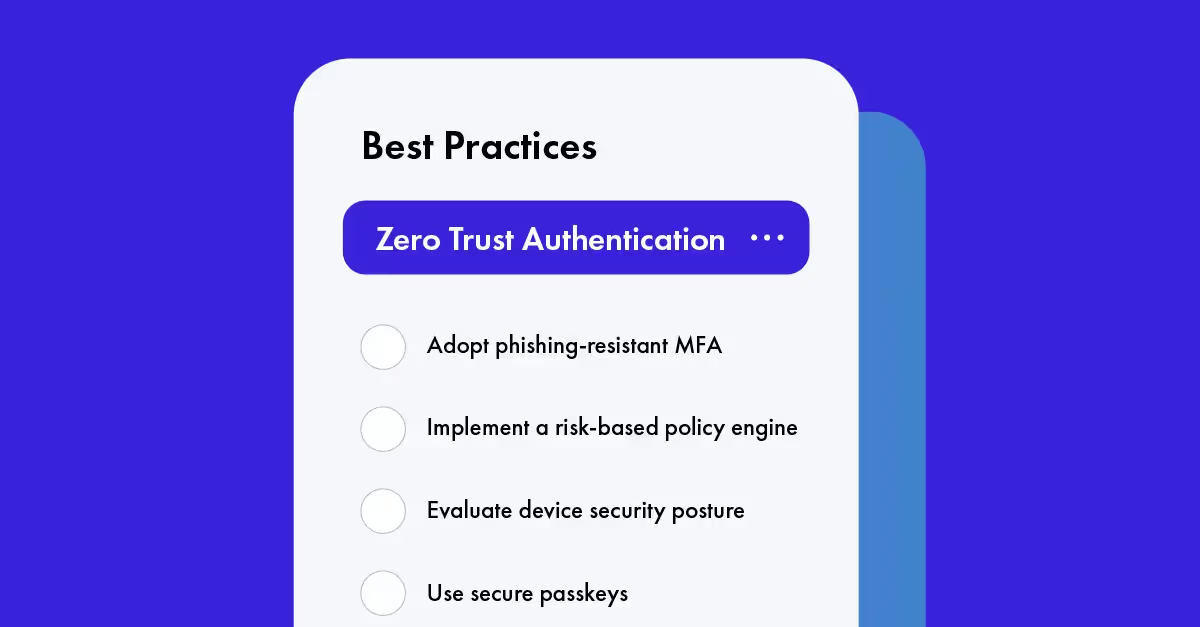
07 Dec 2022
December 7, 2022
5 Best Practices for Authentication in a Zero Trust Strategy
It sounds complicated, but zero trust authentication can be a straightforward process.

30 Nov 2022
November 30, 2022
Beyond Identity Expands Integrations Ecosystem to No-Code Passkey Plugin for Bubble
No-code developers can now easily build passkey authentication in their Bubble applications with Beyond Identity’s new plugins.
.avif)
29 Nov 2022
November 29, 2022
Introducing No-Code Passkey Plugins for Bubble Applications
No-code platforms abstract programming languages and logic and instead use a visual, drag-and-drop approach to software development.

22 Nov 2022
November 22, 2022
5 Authentication Requirements for Zero Trust Environments
Discover the five requirements you need to implement zero trust authentication.

