Zscaler And Beyond Identity Introduce Integrations that Lower the Risk of Password-Based Breaches and Secure Application Access
If I proposed one could minimize breaches, shrink the attack surface, AND secure application access, would you believe it or tell me Santa’s elves are not real.
Well, the new Zscaler and Beyond Identity integration can help you achieve just that and push your zero trust program forward. Let’s review the details and you decide.
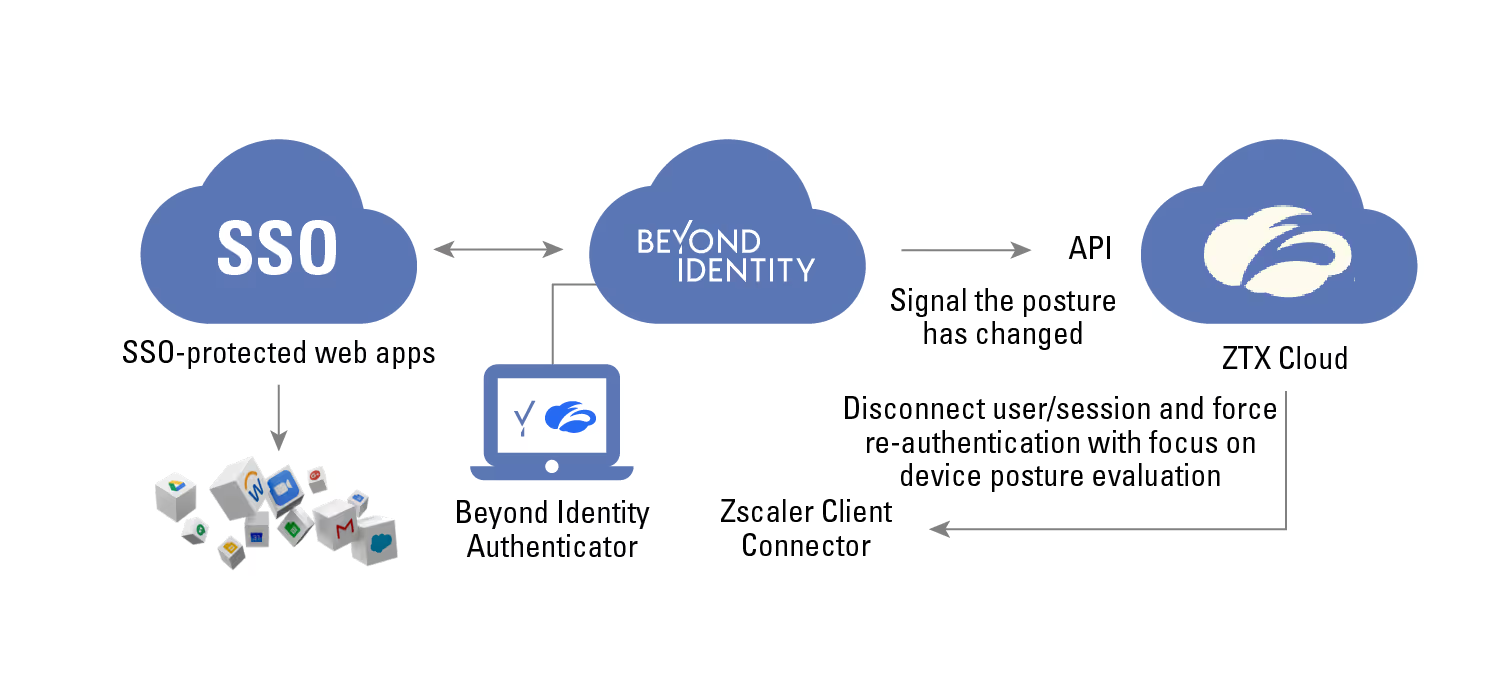
The integration combines Beyond Identity’s phishing-resistant multi-factor authentication and Zscaler’s industry leading zero trust network access (ZTNA) to secure application access, regardless of the app's location. These goals are achieved by integrating Secure Workforce with Zscaler products:
- Zscaler Internet Access (ZIA) protects cloud based services
- Zscaler Private Access (ZPA) secures access to on-premises applications
Zscaler administration access is locked down too.
Eliminating passwords
Secure Workforce eliminates passwords and other weak authentication factors thus minimizes password-related and MFA bypass breaches. Our passwordless authentication works across platforms, and provides a more seamless user experience. It turns out users love passwordless MFA, it’s like a holiday gift that gives back all year.
Shrinking the attack surface
The Secure Workforce device trust functionality shrinks the attack surface, checking and validating that the connecting endpoint security settings align with your organization's security policies. For example, an organization may require specific protections are installed and running like a corporate sanctioned EDR, local firewall, and disk encryption before connecting to computing resources. Secure Workforce confirms these policies are met before authentication and access via ZPA, ZIA, or Zscaler admin is granted. Further, Secure Workforce provides continuous authentication to regularly check and validate that these security controls remain live during active sessions.
Securing your applications
And here’s where it gets interesting, if one of these controls becomes disabled, Secure Workforce informs Zscaler via an API call to disconnect the user's session. No questions asked, just disconnect the offending device, protecting the application and securing the valuable business data. The user is forced to re-authenticate to continue. Upon re-authentication, the security controls are again validated. Access is only granted when the policy is met (EDR is reactivated, for example).
With the integration you:
- Minimize the risk of breaches by eliminating the password and weak authentication factors
- Shrink the attack surface by validating device security controls
- Secure your applications through Zscaler’s ZTNA solution
This integration truly is the gift that keeps giving.
Want to learn more?
Here is a solution brief providing more details.
This integration guide will walk you through the simple process of setting up the integration.
Ready to see Secure Workforce in action? Request a demo.
If I proposed one could minimize breaches, shrink the attack surface, AND secure application access, would you believe it or tell me Santa’s elves are not real.
Well, the new Zscaler and Beyond Identity integration can help you achieve just that and push your zero trust program forward. Let’s review the details and you decide.
The integration combines Beyond Identity’s phishing-resistant multi-factor authentication and Zscaler’s industry leading zero trust network access (ZTNA) to secure application access, regardless of the app's location. These goals are achieved by integrating Secure Workforce with Zscaler products:
- Zscaler Internet Access (ZIA) protects cloud based services
- Zscaler Private Access (ZPA) secures access to on-premises applications
Zscaler administration access is locked down too.
Eliminating passwords
Secure Workforce eliminates passwords and other weak authentication factors thus minimizes password-related and MFA bypass breaches. Our passwordless authentication works across platforms, and provides a more seamless user experience. It turns out users love passwordless MFA, it’s like a holiday gift that gives back all year.
Shrinking the attack surface
The Secure Workforce device trust functionality shrinks the attack surface, checking and validating that the connecting endpoint security settings align with your organization's security policies. For example, an organization may require specific protections are installed and running like a corporate sanctioned EDR, local firewall, and disk encryption before connecting to computing resources. Secure Workforce confirms these policies are met before authentication and access via ZPA, ZIA, or Zscaler admin is granted. Further, Secure Workforce provides continuous authentication to regularly check and validate that these security controls remain live during active sessions.
Securing your applications
And here’s where it gets interesting, if one of these controls becomes disabled, Secure Workforce informs Zscaler via an API call to disconnect the user's session. No questions asked, just disconnect the offending device, protecting the application and securing the valuable business data. The user is forced to re-authenticate to continue. Upon re-authentication, the security controls are again validated. Access is only granted when the policy is met (EDR is reactivated, for example).

With the integration you:
- Minimize the risk of breaches by eliminating the password and weak authentication factors
- Shrink the attack surface by validating device security controls
- Secure your applications through Zscaler’s ZTNA solution
This integration truly is the gift that keeps giving.
Want to learn more?
Here is a solution brief providing more details.
This integration guide will walk you through the simple process of setting up the integration.
Ready to see Secure Workforce in action? Request a demo.
If I proposed one could minimize breaches, shrink the attack surface, AND secure application access, would you believe it or tell me Santa’s elves are not real.
Well, the new Zscaler and Beyond Identity integration can help you achieve just that and push your zero trust program forward. Let’s review the details and you decide.
The integration combines Beyond Identity’s phishing-resistant multi-factor authentication and Zscaler’s industry leading zero trust network access (ZTNA) to secure application access, regardless of the app's location. These goals are achieved by integrating Secure Workforce with Zscaler products:
- Zscaler Internet Access (ZIA) protects cloud based services
- Zscaler Private Access (ZPA) secures access to on-premises applications
Zscaler administration access is locked down too.
Eliminating passwords
Secure Workforce eliminates passwords and other weak authentication factors thus minimizes password-related and MFA bypass breaches. Our passwordless authentication works across platforms, and provides a more seamless user experience. It turns out users love passwordless MFA, it’s like a holiday gift that gives back all year.
Shrinking the attack surface
The Secure Workforce device trust functionality shrinks the attack surface, checking and validating that the connecting endpoint security settings align with your organization's security policies. For example, an organization may require specific protections are installed and running like a corporate sanctioned EDR, local firewall, and disk encryption before connecting to computing resources. Secure Workforce confirms these policies are met before authentication and access via ZPA, ZIA, or Zscaler admin is granted. Further, Secure Workforce provides continuous authentication to regularly check and validate that these security controls remain live during active sessions.
Securing your applications
And here’s where it gets interesting, if one of these controls becomes disabled, Secure Workforce informs Zscaler via an API call to disconnect the user's session. No questions asked, just disconnect the offending device, protecting the application and securing the valuable business data. The user is forced to re-authenticate to continue. Upon re-authentication, the security controls are again validated. Access is only granted when the policy is met (EDR is reactivated, for example).

With the integration you:
- Minimize the risk of breaches by eliminating the password and weak authentication factors
- Shrink the attack surface by validating device security controls
- Secure your applications through Zscaler’s ZTNA solution
This integration truly is the gift that keeps giving.
Want to learn more?
Here is a solution brief providing more details.
This integration guide will walk you through the simple process of setting up the integration.
Ready to see Secure Workforce in action? Request a demo.







.png)






.avif)



.avif)






.avif)

