5 Best Practices for Authentication in a Zero Trust Strategy
Cybercrime is on the rise, with the average number of cyberattacks and data breaches in 2021 up 15.1% from the previous year. Yet even as companies increasingly embrace cybersecurity, their protection measures have not evolved to keep up, leaving their systems—and customers—exposed.
Additionally, the rise in the number of remote workers and contractors using devices outside corporate perimeters adds risk, while expansive global networks introduce multiple entry points for attackers. As a result, traditional perimeter-based security is no longer sufficient to protect today’s expansive digital landscape.
That’s why federal and industry standards now promote zero trust architecture.
Conventional networks operate on a “trust but verify'' security philosophy. Zero trust is a security framework based on the model “never trust, always verify.” In other words, there are no trusted sources in a zero trust security program—every user, device, or service (inside or outside the network) must be authorized and authenticated on a continuous basis.
Authentication lays the foundation for a strong zero trust security architecture as it is the entryway into all of your resources and applications. Continuous authentication gives you high trust in the user, high trust in the device, and verifies that the device meets the standards and policies you set as part of your zero trust architecture. Authentication is a vital part of zero trust.
Use the following best practices to implement a robust Zero Trust Authentication solution to protect your organization.
Best practices for Zero Trust Authentication
1. Adopt passwordless, phishing-resistant multi-factor authentication (MFA)
Passwords are one of the most common (and easy) ways hackers gain entry to otherwise secure systems. All it takes is one compromised password and attackers gain access to the network. That’s why MFA has become such a popular security measure in recent years—requiring two or more authentication factors makes it a little more difficult for bad actors to gain access.
Authentication factors are divided into three main categories:
- Something you know (e.g., passwords, PIN codes, security questions)
- Something you have (e.g., one-time passcodes, hardware security tokens)
- Something you are (e.g., biometrics like fingerprint scans)
However, not all factors used in MFA are equally secure. Most legacy MFA utilizes phishable factors, such as one-time passwords, push notifications, and magic links, which rely on trusting that the user entering the code is who they say they are, making them more vulnerable to brute force, social engineering, and phishing attacks. That vulnerability is no longer acceptable. In January 2022, the U.S. government released a memo advising the use of phishing-resistant MFA. Other agencies, including the FTC, CISA, and the FBI are also recommending organizations implement phishing-resistant MFA.
The best practice is to implement phishing-resistant MFA that utilizes passwordless authentication like cryptographic keys and biometrics. These do not rely on trust because the key is tied to the person or device.
Key-based authentication, or cryptographic authentication, uses cryptographic passkeys that form a public-private key pair to authenticate users. Secure passkeys allow users to authenticate without the risk of shared secrets, such as passwords, one-time codes, and SMS text messages—all of which implicitly trust the user and device.
Here’s how it works:
- The end-user requests access.
- The server generates a random value that the end-user signs with their private key.
- The server verifies the signature with the public key and grants access.
A password can be shared, stolen, or guessed by anyone. But with public key-based authentication, users (including bad actors) can’t gain access to a server without the corresponding private key.
2. Validate device and evaluate device security posture
Ensuring devices are compliant and meet security standards is critical for Zero Trust Authentication. This evaluation takes place at the enforcement points you set for your systems.
Verifying that the device requesting access is in the user’s possession and is authorized to access resources removes the risk that the device has been stolen, or that it never belonged to the user at all. Validating the device also prevents the user from logging in from a personal or home computer or a device especially vulnerable to compromise.
When considering device security posture, Zero Trust Authentication makes two key assumptions:
- Just because a device is managed doesn’t mean it can be trusted
- Just because a device has antivirus software installed doesn’t mean it is free of threats
Zero Trust Authentication requires validating device compliance and checking the identity and integrity of those devices before granting access—without respect to location. Traditional MFA and perimeter-based security frameworks don’t include this critical check and trust the device is up to the standards of the organization if it falls within the corporate perimeter.
3. Risk signals
Collecting and analyzing risk signals is central to Zero Trust Authentication. In zero trust security, authentication is not just checking one or two factors and making a decision to grant or deny. Decisions should be made based on risk assessments that use several types of data and contextual information. Risk assessments and security policies can point to a range of actions.
Zero Trust Authentication leverages the entire security ecosystem by using risk signals and security tools to identify risks and take action in real-time. For example, what happens if a device falls into the wrong hands after authentication?
Suspicious behavior or location data can alert your system to lock down the device in real-time. This increases your security posture by accounting for incidents that occur in between security checks in a traditional approach.
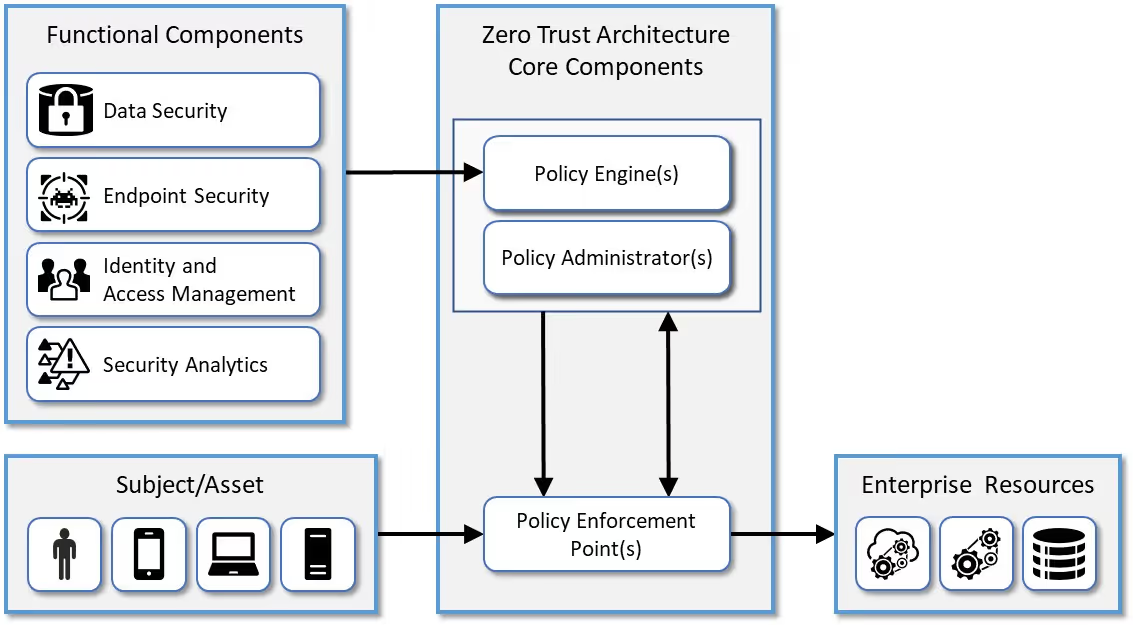
4. Integrate with other tools in the security ecosystem
Zero Trust Authentication needs to share data with other tools in your security ecosystem (EDR, XDR, and SOC/SIEM) to improve risk detection so it can continuously detect abnormal behavior and verify the device regularly.
To accomplish this, organizations must integrate their endpoint detection and response (EDR), extended detection and response, security information and event management systems (SIEMs) and security operation centers (SOCs) solutions. Many traditional security solutions still operate in silos. So integrating them will provide the comprehensive, real-time visibility necessary for end-to-end security and continuous authentication in a zero trust environment.
5. Enable continuous authentication
Risk-based access at login alone isn’t enough. To achieve Zero Trust Authentication, you must continuously verify the user's identity and authorization to access sensitive resources. You are able to limit access to different resources by setting up enforcement points for each as part of your policies.
For example, instead of a simple authentication system that trusts that user identity is enough, a risk-based policy considers the user’s entire behavior and risk profile. This allows you to block access if the system detects risky or abnormal behavior (like a disabled firewall during the session) or ask for additional authentication for high-risk situations (such as logging in from an unmanaged device).
The future of authentication is zero trust
Zero trust begins with authentication. No matter who is accessing your systems, what device they are using, or where they are connecting from, Zero Trust Authentication gives you the peace of mind that the right people are accessing the right resources at the right time.
Ensure your Zero Trust Authentication policies support a robust security posture across all endpoints with Beyond Identity. Beyond Identity is the leading provider of Zero Trust Authentication, delivering continuous risk-based multi-factor authentication. Our cloud-native solution provides a phishing-resistant and passwordless authentication experience that prevents security breaches and offers unparalleled security. Get a demo today.
Cybercrime is on the rise, with the average number of cyberattacks and data breaches in 2021 up 15.1% from the previous year. Yet even as companies increasingly embrace cybersecurity, their protection measures have not evolved to keep up, leaving their systems—and customers—exposed.
Additionally, the rise in the number of remote workers and contractors using devices outside corporate perimeters adds risk, while expansive global networks introduce multiple entry points for attackers. As a result, traditional perimeter-based security is no longer sufficient to protect today’s expansive digital landscape.
That’s why federal and industry standards now promote zero trust architecture.
Conventional networks operate on a “trust but verify'' security philosophy. Zero trust is a security framework based on the model “never trust, always verify.” In other words, there are no trusted sources in a zero trust security program—every user, device, or service (inside or outside the network) must be authorized and authenticated on a continuous basis.
Authentication lays the foundation for a strong zero trust security architecture as it is the entryway into all of your resources and applications. Continuous authentication gives you high trust in the user, high trust in the device, and verifies that the device meets the standards and policies you set as part of your zero trust architecture. Authentication is a vital part of zero trust.
Use the following best practices to implement a robust Zero Trust Authentication solution to protect your organization.
Best practices for Zero Trust Authentication
1. Adopt passwordless, phishing-resistant multi-factor authentication (MFA)
Passwords are one of the most common (and easy) ways hackers gain entry to otherwise secure systems. All it takes is one compromised password and attackers gain access to the network. That’s why MFA has become such a popular security measure in recent years—requiring two or more authentication factors makes it a little more difficult for bad actors to gain access.
Authentication factors are divided into three main categories:
- Something you know (e.g., passwords, PIN codes, security questions)
- Something you have (e.g., one-time passcodes, hardware security tokens)
- Something you are (e.g., biometrics like fingerprint scans)
However, not all factors used in MFA are equally secure. Most legacy MFA utilizes phishable factors, such as one-time passwords, push notifications, and magic links, which rely on trusting that the user entering the code is who they say they are, making them more vulnerable to brute force, social engineering, and phishing attacks. That vulnerability is no longer acceptable. In January 2022, the U.S. government released a memo advising the use of phishing-resistant MFA. Other agencies, including the FTC, CISA, and the FBI are also recommending organizations implement phishing-resistant MFA.
The best practice is to implement phishing-resistant MFA that utilizes passwordless authentication like cryptographic keys and biometrics. These do not rely on trust because the key is tied to the person or device.
Key-based authentication, or cryptographic authentication, uses cryptographic passkeys that form a public-private key pair to authenticate users. Secure passkeys allow users to authenticate without the risk of shared secrets, such as passwords, one-time codes, and SMS text messages—all of which implicitly trust the user and device.
Here’s how it works:
- The end-user requests access.
- The server generates a random value that the end-user signs with their private key.
- The server verifies the signature with the public key and grants access.
A password can be shared, stolen, or guessed by anyone. But with public key-based authentication, users (including bad actors) can’t gain access to a server without the corresponding private key.
2. Validate device and evaluate device security posture
Ensuring devices are compliant and meet security standards is critical for Zero Trust Authentication. This evaluation takes place at the enforcement points you set for your systems.
Verifying that the device requesting access is in the user’s possession and is authorized to access resources removes the risk that the device has been stolen, or that it never belonged to the user at all. Validating the device also prevents the user from logging in from a personal or home computer or a device especially vulnerable to compromise.
When considering device security posture, Zero Trust Authentication makes two key assumptions:
- Just because a device is managed doesn’t mean it can be trusted
- Just because a device has antivirus software installed doesn’t mean it is free of threats
Zero Trust Authentication requires validating device compliance and checking the identity and integrity of those devices before granting access—without respect to location. Traditional MFA and perimeter-based security frameworks don’t include this critical check and trust the device is up to the standards of the organization if it falls within the corporate perimeter.
3. Risk signals
Collecting and analyzing risk signals is central to Zero Trust Authentication. In zero trust security, authentication is not just checking one or two factors and making a decision to grant or deny. Decisions should be made based on risk assessments that use several types of data and contextual information. Risk assessments and security policies can point to a range of actions.
Zero Trust Authentication leverages the entire security ecosystem by using risk signals and security tools to identify risks and take action in real-time. For example, what happens if a device falls into the wrong hands after authentication?
Suspicious behavior or location data can alert your system to lock down the device in real-time. This increases your security posture by accounting for incidents that occur in between security checks in a traditional approach.

4. Integrate with other tools in the security ecosystem
Zero Trust Authentication needs to share data with other tools in your security ecosystem (EDR, XDR, and SOC/SIEM) to improve risk detection so it can continuously detect abnormal behavior and verify the device regularly.
To accomplish this, organizations must integrate their endpoint detection and response (EDR), extended detection and response, security information and event management systems (SIEMs) and security operation centers (SOCs) solutions. Many traditional security solutions still operate in silos. So integrating them will provide the comprehensive, real-time visibility necessary for end-to-end security and continuous authentication in a zero trust environment.
5. Enable continuous authentication
Risk-based access at login alone isn’t enough. To achieve Zero Trust Authentication, you must continuously verify the user's identity and authorization to access sensitive resources. You are able to limit access to different resources by setting up enforcement points for each as part of your policies.
For example, instead of a simple authentication system that trusts that user identity is enough, a risk-based policy considers the user’s entire behavior and risk profile. This allows you to block access if the system detects risky or abnormal behavior (like a disabled firewall during the session) or ask for additional authentication for high-risk situations (such as logging in from an unmanaged device).
The future of authentication is zero trust
Zero trust begins with authentication. No matter who is accessing your systems, what device they are using, or where they are connecting from, Zero Trust Authentication gives you the peace of mind that the right people are accessing the right resources at the right time.
Ensure your Zero Trust Authentication policies support a robust security posture across all endpoints with Beyond Identity. Beyond Identity is the leading provider of Zero Trust Authentication, delivering continuous risk-based multi-factor authentication. Our cloud-native solution provides a phishing-resistant and passwordless authentication experience that prevents security breaches and offers unparalleled security. Get a demo today.
Cybercrime is on the rise, with the average number of cyberattacks and data breaches in 2021 up 15.1% from the previous year. Yet even as companies increasingly embrace cybersecurity, their protection measures have not evolved to keep up, leaving their systems—and customers—exposed.
Additionally, the rise in the number of remote workers and contractors using devices outside corporate perimeters adds risk, while expansive global networks introduce multiple entry points for attackers. As a result, traditional perimeter-based security is no longer sufficient to protect today’s expansive digital landscape.
That’s why federal and industry standards now promote zero trust architecture.
Conventional networks operate on a “trust but verify'' security philosophy. Zero trust is a security framework based on the model “never trust, always verify.” In other words, there are no trusted sources in a zero trust security program—every user, device, or service (inside or outside the network) must be authorized and authenticated on a continuous basis.
Authentication lays the foundation for a strong zero trust security architecture as it is the entryway into all of your resources and applications. Continuous authentication gives you high trust in the user, high trust in the device, and verifies that the device meets the standards and policies you set as part of your zero trust architecture. Authentication is a vital part of zero trust.
Use the following best practices to implement a robust Zero Trust Authentication solution to protect your organization.
Best practices for Zero Trust Authentication
1. Adopt passwordless, phishing-resistant multi-factor authentication (MFA)
Passwords are one of the most common (and easy) ways hackers gain entry to otherwise secure systems. All it takes is one compromised password and attackers gain access to the network. That’s why MFA has become such a popular security measure in recent years—requiring two or more authentication factors makes it a little more difficult for bad actors to gain access.
Authentication factors are divided into three main categories:
- Something you know (e.g., passwords, PIN codes, security questions)
- Something you have (e.g., one-time passcodes, hardware security tokens)
- Something you are (e.g., biometrics like fingerprint scans)
However, not all factors used in MFA are equally secure. Most legacy MFA utilizes phishable factors, such as one-time passwords, push notifications, and magic links, which rely on trusting that the user entering the code is who they say they are, making them more vulnerable to brute force, social engineering, and phishing attacks. That vulnerability is no longer acceptable. In January 2022, the U.S. government released a memo advising the use of phishing-resistant MFA. Other agencies, including the FTC, CISA, and the FBI are also recommending organizations implement phishing-resistant MFA.
The best practice is to implement phishing-resistant MFA that utilizes passwordless authentication like cryptographic keys and biometrics. These do not rely on trust because the key is tied to the person or device.
Key-based authentication, or cryptographic authentication, uses cryptographic passkeys that form a public-private key pair to authenticate users. Secure passkeys allow users to authenticate without the risk of shared secrets, such as passwords, one-time codes, and SMS text messages—all of which implicitly trust the user and device.
Here’s how it works:
- The end-user requests access.
- The server generates a random value that the end-user signs with their private key.
- The server verifies the signature with the public key and grants access.
A password can be shared, stolen, or guessed by anyone. But with public key-based authentication, users (including bad actors) can’t gain access to a server without the corresponding private key.
2. Validate device and evaluate device security posture
Ensuring devices are compliant and meet security standards is critical for Zero Trust Authentication. This evaluation takes place at the enforcement points you set for your systems.
Verifying that the device requesting access is in the user’s possession and is authorized to access resources removes the risk that the device has been stolen, or that it never belonged to the user at all. Validating the device also prevents the user from logging in from a personal or home computer or a device especially vulnerable to compromise.
When considering device security posture, Zero Trust Authentication makes two key assumptions:
- Just because a device is managed doesn’t mean it can be trusted
- Just because a device has antivirus software installed doesn’t mean it is free of threats
Zero Trust Authentication requires validating device compliance and checking the identity and integrity of those devices before granting access—without respect to location. Traditional MFA and perimeter-based security frameworks don’t include this critical check and trust the device is up to the standards of the organization if it falls within the corporate perimeter.
3. Risk signals
Collecting and analyzing risk signals is central to Zero Trust Authentication. In zero trust security, authentication is not just checking one or two factors and making a decision to grant or deny. Decisions should be made based on risk assessments that use several types of data and contextual information. Risk assessments and security policies can point to a range of actions.
Zero Trust Authentication leverages the entire security ecosystem by using risk signals and security tools to identify risks and take action in real-time. For example, what happens if a device falls into the wrong hands after authentication?
Suspicious behavior or location data can alert your system to lock down the device in real-time. This increases your security posture by accounting for incidents that occur in between security checks in a traditional approach.

4. Integrate with other tools in the security ecosystem
Zero Trust Authentication needs to share data with other tools in your security ecosystem (EDR, XDR, and SOC/SIEM) to improve risk detection so it can continuously detect abnormal behavior and verify the device regularly.
To accomplish this, organizations must integrate their endpoint detection and response (EDR), extended detection and response, security information and event management systems (SIEMs) and security operation centers (SOCs) solutions. Many traditional security solutions still operate in silos. So integrating them will provide the comprehensive, real-time visibility necessary for end-to-end security and continuous authentication in a zero trust environment.
5. Enable continuous authentication
Risk-based access at login alone isn’t enough. To achieve Zero Trust Authentication, you must continuously verify the user's identity and authorization to access sensitive resources. You are able to limit access to different resources by setting up enforcement points for each as part of your policies.
For example, instead of a simple authentication system that trusts that user identity is enough, a risk-based policy considers the user’s entire behavior and risk profile. This allows you to block access if the system detects risky or abnormal behavior (like a disabled firewall during the session) or ask for additional authentication for high-risk situations (such as logging in from an unmanaged device).
The future of authentication is zero trust
Zero trust begins with authentication. No matter who is accessing your systems, what device they are using, or where they are connecting from, Zero Trust Authentication gives you the peace of mind that the right people are accessing the right resources at the right time.
Ensure your Zero Trust Authentication policies support a robust security posture across all endpoints with Beyond Identity. Beyond Identity is the leading provider of Zero Trust Authentication, delivering continuous risk-based multi-factor authentication. Our cloud-native solution provides a phishing-resistant and passwordless authentication experience that prevents security breaches and offers unparalleled security. Get a demo today.






.png)






.avif)



.avif)






.avif)

