Cybersecurity Habits of Hyper-Growth Companies [Survey]
Key Takeaways
- Sixty-two percent of hyper-growth companies took a proactive approach to cybersecurity.
- Only 55% of hyper-growth companies restricted network administration rights.
- Hyper-growth companies were more likely than standard growth companies to report a higher incidence of cyberattacks.
- Cyberattacks were approximated to have the potential to cost up to $119,000 in damages for standard-growth companies which was roughly $95,000 more costly than it was for hyper-growth companies.
Security, especially cybersecurity, is paramount in today’s business environment. And while hackers still focus on stealing passwords from unsuspecting individuals, an even greater danger has emerged as worldwide rings of advanced cyber criminals continue to hold major corporations hostage by inserting ransomware and compromising critical data.
From the maintenance staff to the CEO’s office, nearly every employee finds themselves entrusted with multiple passwords that could wreak havoc if stolen. And when industries experience incredible periods of growth, they become an easier target for hackers looking for vulnerable data.
Information Technology (IT) and cybersecurity professionals understand how situations turn on a dime when hackers invade a company’s databases. Nonetheless, some employees often don’t exercise enough caution to protect company information.
To uncover the issues associated with cybercrimes, we asked over 1,100 employees, from entry- and mid-level to business leaders within their respective organizations to chime in about cybersecurity issues. Let’s see what concerns our survey respondents shared and how following strict cybersecurity guidelines can save companies thousands, if not millions, of dollars.
Growth and Cybersecurity
With parts of the worldwide economy exploding, some companies are experiencing what business experts call a compound annual growth rate (CAGR), which means a growth of above 40% annually—otherwise known as hyper growth.
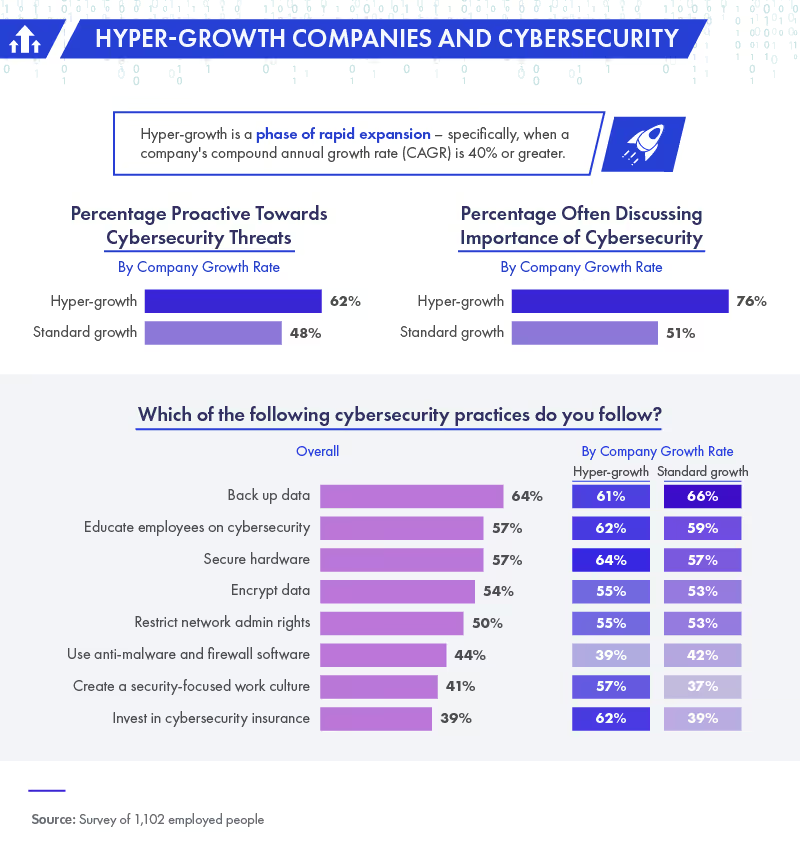
Unfortunately, such tremendous growth often means vital security issues go unattended, leaving the company open to hackers. Just under half of respondents who work for normal growth companies reported that their business takes a proactive approach to cybersecurity. Hyper-growth companies responded more aggressively, with 62% claiming assertive status. While the majority of these types of companies are buckling down and actively protecting their most vulnerable data, the remaining minority may find they have a few holes in their cyber armor.
Academic cybersecurity professionals constantly warn businesses about new dangers and ways to safeguard critical cyber infrastructure. Phishing attacks, which are phony electronic messages designed to trick recipients into turning over sensitive personal and company information, increase each year. Ransomware attacks are already costing companies billions of dollars, making criminals more brazen.
Company IT and cybersecurity employees find themselves with the task of protecting all sorts of data. Besides critical company secrets, think about each employee’s personal information on job applications and company information databases. With rapid expansion comes more employee data to protect, which is perhaps why 76% of hyper-growth respondents reported often discussing cybersecurity issues, compared to only 51% of standard growth company workers.
Beyond simply discussing cybersecurity measures, other steps can be taken to protect vital company data. Of these, the most popular among our respondents was backing up data (64%), although hyper-growth companies were a few percentage points behind standard growth companies in this respect. However, hyper-growth companies were several percentage points ahead in other areas, including educating employees on cybersecurity measures and protecting hardware.
Two areas where hyper-growth companies had a 20-plus point lead were in creating a security-focused culture and investing in cybersecurity insurance. One alarming statistic is that, overall, only 50% of respondents reported that their companies restrict network administration rights.
Hyper-growth companies also wrestle with other issues that may distract focus from cybersecurity concerns. Over 80% of hyper-growth respondents said that increasing revenue, financial stability, security, and marketing outreach were also critical issues for their business.
Areas of Vulnerability
Whether they know it or not, employees often expose confidential data to outside sources by using their personal email address for company business and not taking adequate precautions to protect passwords.
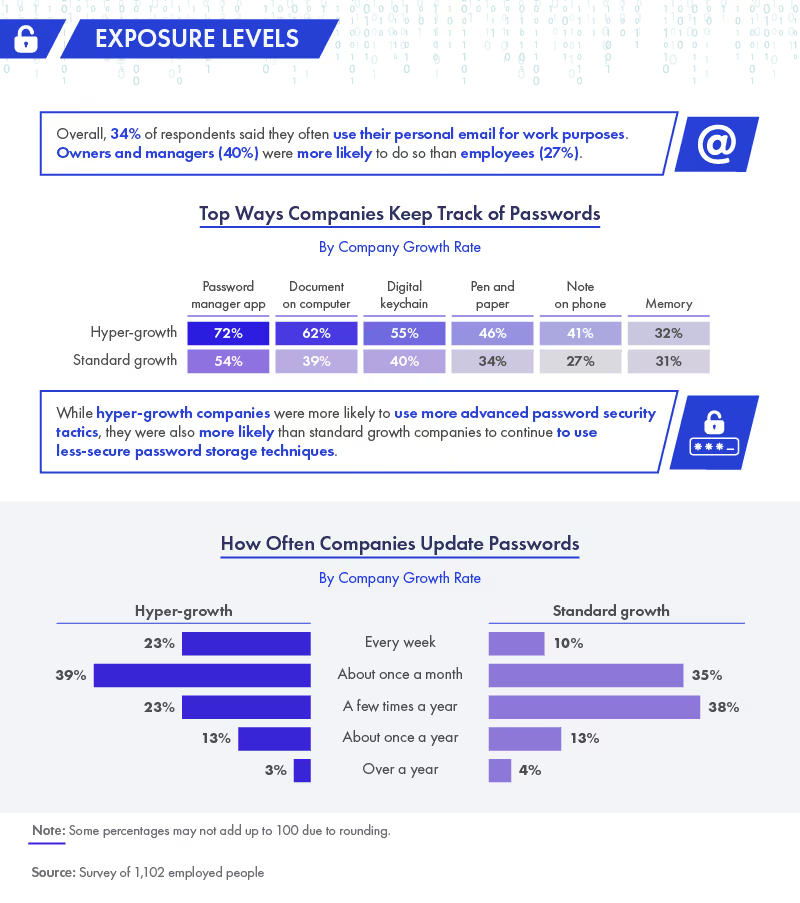
Employees may think that using personal emails to conduct company business is safe. However, cyberintruders often find intercepting personal emails easier by using phishing scams built to trick unsuspecting employees. What’s surprising is that owners and managers make this mistake more often than lower level employees (40% versus 27%, respectively).
Respondents used many different methods to keep track of their passwords. Seven out of 10 respondents from hyper-growth companies used a password manager app, followed by 62% who documented passwords on computers. Another 55% implemented digital keychains, and 46% used the now-archaic method of writing passwords on paper.
How often passwords are changed also impacts a company’s cybersecurity. The majority of hyper-growth respondents (39%) reported changing their passwords monthly. Once a week and a few times a year tied in second place with 23% of the vote, respectively. Companies with less growth were even more lax—only 35% reported changing their passwords monthly, and 38% only did so a few times per year. While continuously updating your password has become a standard practice for many to avoid hackers and boost cyber security, experts in the security space generally believe that passwords are becoming a thing of the past.
Practically every place consumers frequent these days offers Wi-Fi connectivity. Cybersecurity experts warn individuals not to disclose important information on public networks. Protecting Wi-Fi networks within a company is even more essential.
Wired Equivalent Privacy (WEP) was introduced in 1997 by the Wi-Fi Alliance to protect wireless networks. Think of the user being on one end and the network on the other. Passwords work to stop unauthorized intruders from intercepting data transmitted through radio networks. WEP worked for a while until savvy hackers figured out how to circumvent its security protocols.
Wi-Fi Protected Access (WPA) followed WEP with improvements in handling user authorization and security keys. Hackers eventually bypassed WPA keys, leading to WPA-2 in 2004. Slightly over half of respondents from high-growth companies said their company uses WPA, with 30% selecting WPA-2, followed by WEP at 20%. Today’s most advanced security features don’t even require passwords, thus substantially increasing cyber safety and eliminating the need for tedious updates.
Frequency of Heisted Data
It’s scary to think that 62% of companies surveyed have experienced at least one data breach. Globally, ransomware attacks impact thousands of businesses annually and cost billions of dollars. Hackers find network vulnerabilities and insert malicious software to prevent companies from accessing files, networks, and entire systems. Unsuspecting employees often open email attachments, click on ads, follow links, or even visit websites embedded with malware. Health care, financial, and educational institutions are popular targets for attackers.

Cybersecurity experts say following the basics, such as securing networks and keeping all personal electronic software current, will minimize ransomware attacks.
Employees from hyper-growth companies reported more cyberattacks than standard growth companies. Over a third of respondents said their company had experienced three to five previous attacks. Slightly more than a quarter reported undergoing one to two previous attacks.
2020 was an unusual year in many respects. As the world dealt with a health pandemic, cyber criminals took advantage of an expanded remote workforce. One of the most common attacks involved phishing emails centered around COVID-19 issues. With employees working remotely, many were without corporate IT assistance, especially when using personal computers, tablets, and mobile phones for business purposes.
Hyper-growth companies, many of which operate in the health and technology sectors, were particularly hard hit. For example, Magellan Health, a Fortune 500 insurer, experienced a cyber attack in March of 2020 that exposed 1.7 million internal and external customer accounts. Blackbaud, a global technology company, received a ransomware notice that bank account information and user passwords were compromised. Standard growth companies experienced fewer attacks, with 30% saying one to two attacks had occurred and 26% reporting that they’d seen three to five breaches.
Criminals targeted the company’s most sensitive data, with 68% of hyper-growth respondents saying financial and employee information were the top targets, followed by customer information. Respondents from standard growth companies also listed financial information as the most frequent target. Of course, there is a hard cost to cybersecurity attacks. However, hyper-growth companies estimated the average cost of an attack at $20K–$25K, compared with other companies who estimated losses between $34K and $119K.
The most expensive costs for hyper-growth companies averaged just over $25K and involved operations information. Therefore, although financial and employee information breaches were most common, they actually cost hyper-growth companies the least. The opposite was true for smaller growth companies because when financial data breaches occurred, the associated costs soared to over $118K.
Boosting Cybersecurity Efforts
While hackers continue their attempts to infiltrate companies and government networks, taking the necessary steps to educate employees and secure networks should be top priority.
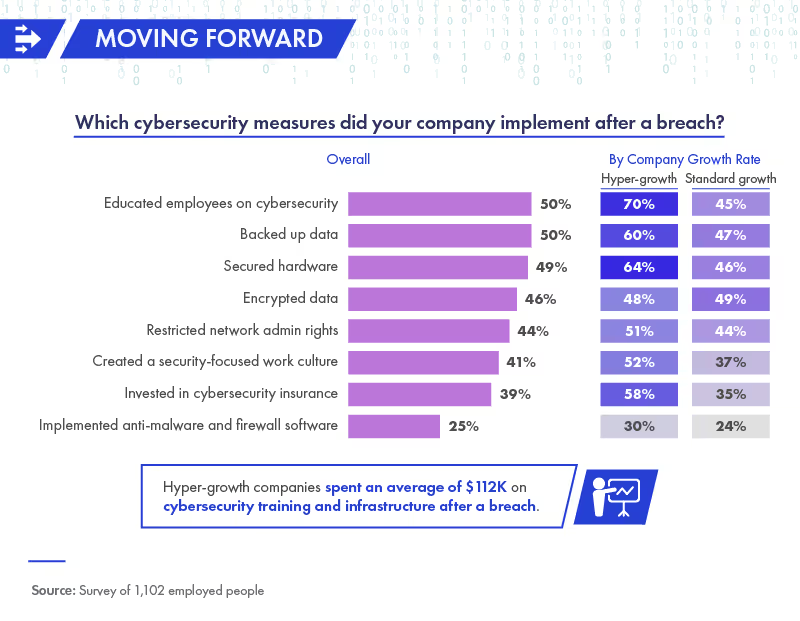
Companies should not wait until a breach occurs to implement safety protocols; however, this is often the reality. On average, hyper-growth companies spent $112K on cybersecurity training and systems improvement after experiencing a breach.
Of all the companies that had an attack, 50% devoted resources to educating employees on cybersecurity strategies and the importance of backing up data. Securing hardware was another priority, followed by encrypting data and restricting network administration access.
Hyper-growth companies were also far more likely than standard growth companies to invest in a cybersecurity insurance policy following a breach.
Receiving notice of a ransomware attack can be an IT and cybersecurity professional’s worst nightmare. Experts warn impacted companies against initially paying the ransom. Two of the first recommended steps are capturing an image of the ransomware notice and disconnecting affected computers from the network.
Retaining a cybersecurity firm and updating network protocols is imperative for companies of any size hoping to avoid such an attack.
Protect Your Company’s Valuable Data
Cybersecurity remains a top priority for businesses of all sizes. Eight in 10 cybersecurity attacks begin with password breaches. With more employees working remotely, protecting valuable company data is even more essential. Beyond Identity’s Secure Work product protects company resources through passwordless authentication, and restricts access to only verified corporate identities.
Regardless of where or how employees access company data, Beyond Identity can enforce adherence to company security policies 24/7 and provide continuous authentication with phishing-resistant MFA. This allows organizations to focus on core objectives without wondering if unauthorized users are lurking in the shadows, and help achieve zero trust security. Don’t waste another moment and try our complimentary product demo today.
Methodology and Limitations
We surveyed 1,102 employees from entry- and mid-level employees to business leaders to explore how their companies expose themselves to cybercrimes and whether they practice cybersecurity. 652 respondents were business leaders, and 450 were entry- to mid-level employees. Among them, 61% were men, and 39% were women.
For short, open-ended questions, outliers were removed.
To help ensure that all respondents took our survey seriously, they were required to identify and correctly answer an attention-check question.
Survey data have certain limitations related to self-reporting. These limitations include telescoping, exaggeration, and selective memory. We didn’t weight our data or statistically test our hypothesis. The margin of error was +/- 3% with a 95% confidence interval.
Fair Use Statement
Cyberattacks are costly to all businesses. The good news is that conveying this information to your readers for noncommercial purposes is free. All we ask is that you link back to the original article and provide appropriate credit.
Key Takeaways
- Sixty-two percent of hyper-growth companies took a proactive approach to cybersecurity.
- Only 55% of hyper-growth companies restricted network administration rights.
- Hyper-growth companies were more likely than standard growth companies to report a higher incidence of cyberattacks.
- Cyberattacks were approximated to have the potential to cost up to $119,000 in damages for standard-growth companies which was roughly $95,000 more costly than it was for hyper-growth companies.
Security, especially cybersecurity, is paramount in today’s business environment. And while hackers still focus on stealing passwords from unsuspecting individuals, an even greater danger has emerged as worldwide rings of advanced cyber criminals continue to hold major corporations hostage by inserting ransomware and compromising critical data.
From the maintenance staff to the CEO’s office, nearly every employee finds themselves entrusted with multiple passwords that could wreak havoc if stolen. And when industries experience incredible periods of growth, they become an easier target for hackers looking for vulnerable data.
Information Technology (IT) and cybersecurity professionals understand how situations turn on a dime when hackers invade a company’s databases. Nonetheless, some employees often don’t exercise enough caution to protect company information.
To uncover the issues associated with cybercrimes, we asked over 1,100 employees, from entry- and mid-level to business leaders within their respective organizations to chime in about cybersecurity issues. Let’s see what concerns our survey respondents shared and how following strict cybersecurity guidelines can save companies thousands, if not millions, of dollars.
Growth and Cybersecurity
With parts of the worldwide economy exploding, some companies are experiencing what business experts call a compound annual growth rate (CAGR), which means a growth of above 40% annually—otherwise known as hyper growth.

Unfortunately, such tremendous growth often means vital security issues go unattended, leaving the company open to hackers. Just under half of respondents who work for normal growth companies reported that their business takes a proactive approach to cybersecurity. Hyper-growth companies responded more aggressively, with 62% claiming assertive status. While the majority of these types of companies are buckling down and actively protecting their most vulnerable data, the remaining minority may find they have a few holes in their cyber armor.
Academic cybersecurity professionals constantly warn businesses about new dangers and ways to safeguard critical cyber infrastructure. Phishing attacks, which are phony electronic messages designed to trick recipients into turning over sensitive personal and company information, increase each year. Ransomware attacks are already costing companies billions of dollars, making criminals more brazen.
Company IT and cybersecurity employees find themselves with the task of protecting all sorts of data. Besides critical company secrets, think about each employee’s personal information on job applications and company information databases. With rapid expansion comes more employee data to protect, which is perhaps why 76% of hyper-growth respondents reported often discussing cybersecurity issues, compared to only 51% of standard growth company workers.
Beyond simply discussing cybersecurity measures, other steps can be taken to protect vital company data. Of these, the most popular among our respondents was backing up data (64%), although hyper-growth companies were a few percentage points behind standard growth companies in this respect. However, hyper-growth companies were several percentage points ahead in other areas, including educating employees on cybersecurity measures and protecting hardware.
Two areas where hyper-growth companies had a 20-plus point lead were in creating a security-focused culture and investing in cybersecurity insurance. One alarming statistic is that, overall, only 50% of respondents reported that their companies restrict network administration rights.
Hyper-growth companies also wrestle with other issues that may distract focus from cybersecurity concerns. Over 80% of hyper-growth respondents said that increasing revenue, financial stability, security, and marketing outreach were also critical issues for their business.
Areas of Vulnerability
Whether they know it or not, employees often expose confidential data to outside sources by using their personal email address for company business and not taking adequate precautions to protect passwords.

Employees may think that using personal emails to conduct company business is safe. However, cyberintruders often find intercepting personal emails easier by using phishing scams built to trick unsuspecting employees. What’s surprising is that owners and managers make this mistake more often than lower level employees (40% versus 27%, respectively).
Respondents used many different methods to keep track of their passwords. Seven out of 10 respondents from hyper-growth companies used a password manager app, followed by 62% who documented passwords on computers. Another 55% implemented digital keychains, and 46% used the now-archaic method of writing passwords on paper.
How often passwords are changed also impacts a company’s cybersecurity. The majority of hyper-growth respondents (39%) reported changing their passwords monthly. Once a week and a few times a year tied in second place with 23% of the vote, respectively. Companies with less growth were even more lax—only 35% reported changing their passwords monthly, and 38% only did so a few times per year. While continuously updating your password has become a standard practice for many to avoid hackers and boost cyber security, experts in the security space generally believe that passwords are becoming a thing of the past.
Practically every place consumers frequent these days offers Wi-Fi connectivity. Cybersecurity experts warn individuals not to disclose important information on public networks. Protecting Wi-Fi networks within a company is even more essential.
Wired Equivalent Privacy (WEP) was introduced in 1997 by the Wi-Fi Alliance to protect wireless networks. Think of the user being on one end and the network on the other. Passwords work to stop unauthorized intruders from intercepting data transmitted through radio networks. WEP worked for a while until savvy hackers figured out how to circumvent its security protocols.
Wi-Fi Protected Access (WPA) followed WEP with improvements in handling user authorization and security keys. Hackers eventually bypassed WPA keys, leading to WPA-2 in 2004. Slightly over half of respondents from high-growth companies said their company uses WPA, with 30% selecting WPA-2, followed by WEP at 20%. Today’s most advanced security features don’t even require passwords, thus substantially increasing cyber safety and eliminating the need for tedious updates.
Frequency of Heisted Data
It’s scary to think that 62% of companies surveyed have experienced at least one data breach. Globally, ransomware attacks impact thousands of businesses annually and cost billions of dollars. Hackers find network vulnerabilities and insert malicious software to prevent companies from accessing files, networks, and entire systems. Unsuspecting employees often open email attachments, click on ads, follow links, or even visit websites embedded with malware. Health care, financial, and educational institutions are popular targets for attackers.

Cybersecurity experts say following the basics, such as securing networks and keeping all personal electronic software current, will minimize ransomware attacks.
Employees from hyper-growth companies reported more cyberattacks than standard growth companies. Over a third of respondents said their company had experienced three to five previous attacks. Slightly more than a quarter reported undergoing one to two previous attacks.
2020 was an unusual year in many respects. As the world dealt with a health pandemic, cyber criminals took advantage of an expanded remote workforce. One of the most common attacks involved phishing emails centered around COVID-19 issues. With employees working remotely, many were without corporate IT assistance, especially when using personal computers, tablets, and mobile phones for business purposes.
Hyper-growth companies, many of which operate in the health and technology sectors, were particularly hard hit. For example, Magellan Health, a Fortune 500 insurer, experienced a cyber attack in March of 2020 that exposed 1.7 million internal and external customer accounts. Blackbaud, a global technology company, received a ransomware notice that bank account information and user passwords were compromised. Standard growth companies experienced fewer attacks, with 30% saying one to two attacks had occurred and 26% reporting that they’d seen three to five breaches.
Criminals targeted the company’s most sensitive data, with 68% of hyper-growth respondents saying financial and employee information were the top targets, followed by customer information. Respondents from standard growth companies also listed financial information as the most frequent target. Of course, there is a hard cost to cybersecurity attacks. However, hyper-growth companies estimated the average cost of an attack at $20K–$25K, compared with other companies who estimated losses between $34K and $119K.
The most expensive costs for hyper-growth companies averaged just over $25K and involved operations information. Therefore, although financial and employee information breaches were most common, they actually cost hyper-growth companies the least. The opposite was true for smaller growth companies because when financial data breaches occurred, the associated costs soared to over $118K.
Boosting Cybersecurity Efforts
While hackers continue their attempts to infiltrate companies and government networks, taking the necessary steps to educate employees and secure networks should be top priority.

Companies should not wait until a breach occurs to implement safety protocols; however, this is often the reality. On average, hyper-growth companies spent $112K on cybersecurity training and systems improvement after experiencing a breach.
Of all the companies that had an attack, 50% devoted resources to educating employees on cybersecurity strategies and the importance of backing up data. Securing hardware was another priority, followed by encrypting data and restricting network administration access.
Hyper-growth companies were also far more likely than standard growth companies to invest in a cybersecurity insurance policy following a breach.
Receiving notice of a ransomware attack can be an IT and cybersecurity professional’s worst nightmare. Experts warn impacted companies against initially paying the ransom. Two of the first recommended steps are capturing an image of the ransomware notice and disconnecting affected computers from the network.
Retaining a cybersecurity firm and updating network protocols is imperative for companies of any size hoping to avoid such an attack.
Protect Your Company’s Valuable Data
Cybersecurity remains a top priority for businesses of all sizes. Eight in 10 cybersecurity attacks begin with password breaches. With more employees working remotely, protecting valuable company data is even more essential. Beyond Identity’s Secure Work product protects company resources through passwordless authentication, and restricts access to only verified corporate identities.
Regardless of where or how employees access company data, Beyond Identity can enforce adherence to company security policies 24/7 and provide continuous authentication with phishing-resistant MFA. This allows organizations to focus on core objectives without wondering if unauthorized users are lurking in the shadows, and help achieve zero trust security. Don’t waste another moment and try our complimentary product demo today.
Methodology and Limitations
We surveyed 1,102 employees from entry- and mid-level employees to business leaders to explore how their companies expose themselves to cybercrimes and whether they practice cybersecurity. 652 respondents were business leaders, and 450 were entry- to mid-level employees. Among them, 61% were men, and 39% were women.
For short, open-ended questions, outliers were removed.
To help ensure that all respondents took our survey seriously, they were required to identify and correctly answer an attention-check question.
Survey data have certain limitations related to self-reporting. These limitations include telescoping, exaggeration, and selective memory. We didn’t weight our data or statistically test our hypothesis. The margin of error was +/- 3% with a 95% confidence interval.
Fair Use Statement
Cyberattacks are costly to all businesses. The good news is that conveying this information to your readers for noncommercial purposes is free. All we ask is that you link back to the original article and provide appropriate credit.
Key Takeaways
- Sixty-two percent of hyper-growth companies took a proactive approach to cybersecurity.
- Only 55% of hyper-growth companies restricted network administration rights.
- Hyper-growth companies were more likely than standard growth companies to report a higher incidence of cyberattacks.
- Cyberattacks were approximated to have the potential to cost up to $119,000 in damages for standard-growth companies which was roughly $95,000 more costly than it was for hyper-growth companies.
Security, especially cybersecurity, is paramount in today’s business environment. And while hackers still focus on stealing passwords from unsuspecting individuals, an even greater danger has emerged as worldwide rings of advanced cyber criminals continue to hold major corporations hostage by inserting ransomware and compromising critical data.
From the maintenance staff to the CEO’s office, nearly every employee finds themselves entrusted with multiple passwords that could wreak havoc if stolen. And when industries experience incredible periods of growth, they become an easier target for hackers looking for vulnerable data.
Information Technology (IT) and cybersecurity professionals understand how situations turn on a dime when hackers invade a company’s databases. Nonetheless, some employees often don’t exercise enough caution to protect company information.
To uncover the issues associated with cybercrimes, we asked over 1,100 employees, from entry- and mid-level to business leaders within their respective organizations to chime in about cybersecurity issues. Let’s see what concerns our survey respondents shared and how following strict cybersecurity guidelines can save companies thousands, if not millions, of dollars.
Growth and Cybersecurity
With parts of the worldwide economy exploding, some companies are experiencing what business experts call a compound annual growth rate (CAGR), which means a growth of above 40% annually—otherwise known as hyper growth.

Unfortunately, such tremendous growth often means vital security issues go unattended, leaving the company open to hackers. Just under half of respondents who work for normal growth companies reported that their business takes a proactive approach to cybersecurity. Hyper-growth companies responded more aggressively, with 62% claiming assertive status. While the majority of these types of companies are buckling down and actively protecting their most vulnerable data, the remaining minority may find they have a few holes in their cyber armor.
Academic cybersecurity professionals constantly warn businesses about new dangers and ways to safeguard critical cyber infrastructure. Phishing attacks, which are phony electronic messages designed to trick recipients into turning over sensitive personal and company information, increase each year. Ransomware attacks are already costing companies billions of dollars, making criminals more brazen.
Company IT and cybersecurity employees find themselves with the task of protecting all sorts of data. Besides critical company secrets, think about each employee’s personal information on job applications and company information databases. With rapid expansion comes more employee data to protect, which is perhaps why 76% of hyper-growth respondents reported often discussing cybersecurity issues, compared to only 51% of standard growth company workers.
Beyond simply discussing cybersecurity measures, other steps can be taken to protect vital company data. Of these, the most popular among our respondents was backing up data (64%), although hyper-growth companies were a few percentage points behind standard growth companies in this respect. However, hyper-growth companies were several percentage points ahead in other areas, including educating employees on cybersecurity measures and protecting hardware.
Two areas where hyper-growth companies had a 20-plus point lead were in creating a security-focused culture and investing in cybersecurity insurance. One alarming statistic is that, overall, only 50% of respondents reported that their companies restrict network administration rights.
Hyper-growth companies also wrestle with other issues that may distract focus from cybersecurity concerns. Over 80% of hyper-growth respondents said that increasing revenue, financial stability, security, and marketing outreach were also critical issues for their business.
Areas of Vulnerability
Whether they know it or not, employees often expose confidential data to outside sources by using their personal email address for company business and not taking adequate precautions to protect passwords.

Employees may think that using personal emails to conduct company business is safe. However, cyberintruders often find intercepting personal emails easier by using phishing scams built to trick unsuspecting employees. What’s surprising is that owners and managers make this mistake more often than lower level employees (40% versus 27%, respectively).
Respondents used many different methods to keep track of their passwords. Seven out of 10 respondents from hyper-growth companies used a password manager app, followed by 62% who documented passwords on computers. Another 55% implemented digital keychains, and 46% used the now-archaic method of writing passwords on paper.
How often passwords are changed also impacts a company’s cybersecurity. The majority of hyper-growth respondents (39%) reported changing their passwords monthly. Once a week and a few times a year tied in second place with 23% of the vote, respectively. Companies with less growth were even more lax—only 35% reported changing their passwords monthly, and 38% only did so a few times per year. While continuously updating your password has become a standard practice for many to avoid hackers and boost cyber security, experts in the security space generally believe that passwords are becoming a thing of the past.
Practically every place consumers frequent these days offers Wi-Fi connectivity. Cybersecurity experts warn individuals not to disclose important information on public networks. Protecting Wi-Fi networks within a company is even more essential.
Wired Equivalent Privacy (WEP) was introduced in 1997 by the Wi-Fi Alliance to protect wireless networks. Think of the user being on one end and the network on the other. Passwords work to stop unauthorized intruders from intercepting data transmitted through radio networks. WEP worked for a while until savvy hackers figured out how to circumvent its security protocols.
Wi-Fi Protected Access (WPA) followed WEP with improvements in handling user authorization and security keys. Hackers eventually bypassed WPA keys, leading to WPA-2 in 2004. Slightly over half of respondents from high-growth companies said their company uses WPA, with 30% selecting WPA-2, followed by WEP at 20%. Today’s most advanced security features don’t even require passwords, thus substantially increasing cyber safety and eliminating the need for tedious updates.
Frequency of Heisted Data
It’s scary to think that 62% of companies surveyed have experienced at least one data breach. Globally, ransomware attacks impact thousands of businesses annually and cost billions of dollars. Hackers find network vulnerabilities and insert malicious software to prevent companies from accessing files, networks, and entire systems. Unsuspecting employees often open email attachments, click on ads, follow links, or even visit websites embedded with malware. Health care, financial, and educational institutions are popular targets for attackers.

Cybersecurity experts say following the basics, such as securing networks and keeping all personal electronic software current, will minimize ransomware attacks.
Employees from hyper-growth companies reported more cyberattacks than standard growth companies. Over a third of respondents said their company had experienced three to five previous attacks. Slightly more than a quarter reported undergoing one to two previous attacks.
2020 was an unusual year in many respects. As the world dealt with a health pandemic, cyber criminals took advantage of an expanded remote workforce. One of the most common attacks involved phishing emails centered around COVID-19 issues. With employees working remotely, many were without corporate IT assistance, especially when using personal computers, tablets, and mobile phones for business purposes.
Hyper-growth companies, many of which operate in the health and technology sectors, were particularly hard hit. For example, Magellan Health, a Fortune 500 insurer, experienced a cyber attack in March of 2020 that exposed 1.7 million internal and external customer accounts. Blackbaud, a global technology company, received a ransomware notice that bank account information and user passwords were compromised. Standard growth companies experienced fewer attacks, with 30% saying one to two attacks had occurred and 26% reporting that they’d seen three to five breaches.
Criminals targeted the company’s most sensitive data, with 68% of hyper-growth respondents saying financial and employee information were the top targets, followed by customer information. Respondents from standard growth companies also listed financial information as the most frequent target. Of course, there is a hard cost to cybersecurity attacks. However, hyper-growth companies estimated the average cost of an attack at $20K–$25K, compared with other companies who estimated losses between $34K and $119K.
The most expensive costs for hyper-growth companies averaged just over $25K and involved operations information. Therefore, although financial and employee information breaches were most common, they actually cost hyper-growth companies the least. The opposite was true for smaller growth companies because when financial data breaches occurred, the associated costs soared to over $118K.
Boosting Cybersecurity Efforts
While hackers continue their attempts to infiltrate companies and government networks, taking the necessary steps to educate employees and secure networks should be top priority.

Companies should not wait until a breach occurs to implement safety protocols; however, this is often the reality. On average, hyper-growth companies spent $112K on cybersecurity training and systems improvement after experiencing a breach.
Of all the companies that had an attack, 50% devoted resources to educating employees on cybersecurity strategies and the importance of backing up data. Securing hardware was another priority, followed by encrypting data and restricting network administration access.
Hyper-growth companies were also far more likely than standard growth companies to invest in a cybersecurity insurance policy following a breach.
Receiving notice of a ransomware attack can be an IT and cybersecurity professional’s worst nightmare. Experts warn impacted companies against initially paying the ransom. Two of the first recommended steps are capturing an image of the ransomware notice and disconnecting affected computers from the network.
Retaining a cybersecurity firm and updating network protocols is imperative for companies of any size hoping to avoid such an attack.
Protect Your Company’s Valuable Data
Cybersecurity remains a top priority for businesses of all sizes. Eight in 10 cybersecurity attacks begin with password breaches. With more employees working remotely, protecting valuable company data is even more essential. Beyond Identity’s Secure Work product protects company resources through passwordless authentication, and restricts access to only verified corporate identities.
Regardless of where or how employees access company data, Beyond Identity can enforce adherence to company security policies 24/7 and provide continuous authentication with phishing-resistant MFA. This allows organizations to focus on core objectives without wondering if unauthorized users are lurking in the shadows, and help achieve zero trust security. Don’t waste another moment and try our complimentary product demo today.
Methodology and Limitations
We surveyed 1,102 employees from entry- and mid-level employees to business leaders to explore how their companies expose themselves to cybercrimes and whether they practice cybersecurity. 652 respondents were business leaders, and 450 were entry- to mid-level employees. Among them, 61% were men, and 39% were women.
For short, open-ended questions, outliers were removed.
To help ensure that all respondents took our survey seriously, they were required to identify and correctly answer an attention-check question.
Survey data have certain limitations related to self-reporting. These limitations include telescoping, exaggeration, and selective memory. We didn’t weight our data or statistically test our hypothesis. The margin of error was +/- 3% with a 95% confidence interval.
Fair Use Statement
Cyberattacks are costly to all businesses. The good news is that conveying this information to your readers for noncommercial purposes is free. All we ask is that you link back to the original article and provide appropriate credit.

![Cybersecurity Habits of Hyper-Growth Companies [Survey]](https://cdn.prod.website-files.com/6835da5ccf38540935c3c9c1/6890d55485a3b7f93f72e63e_65e764325780a2a9143b2d2f_header2.avif)





.png)






.avif)



.avif)






.avif)

