Beyond Identity's Zero Trust Authentication Under the Hood
One of the most common questions we got as we prepared for today’s launch was what implementing effective Zero Trust Authentication “looks like” when done properly.
As we’ve discussed in various forums, there are seven key tenets of Zero Trust Authentication. All of them are critical to fulfilling the promise, so we’ll review them one-by-one and show you exactly what it looks like.
1. Passwordless
“No use of passwords or other shared secrets, because shared secrets can easily be obtained from users, captured on networks, or hacked from databases.”
Beyond Identity uses a combination of two factors for secure verification of user identity:
- A certificate, which is permanently and inextricably stored in the security hardware, such as a TPM (Trusted Platform Module, also known as ISO/IEC 11889), of every user device is used to prove possession. This certificate constitutes an individual, durable link to each authorized device belonging to a user, authorizing that device as one possible source of a secure login from that user.
- That certificate is unlocked using either biometrics, to prove inherence, or a PIN, to prove knowledge. Much like cameras, the best biometrics are the ones you have with you, so we leverage existing technology like Hello on Windows or TouchID and FaceID on Mac and iOS to safeguard users’ passkeys.
Just like the Chip+PIN security used to safeguard most bank accounts from unauthorized access at the ATM, these two factors only work when taken together. A single factor is worthless, much like someone in another country knowing your bank PIN without having your chip card.
2. Phishing resistant
“No opportunity to obtain codes, magic links, or other authentication factors through phishing, adversary-in-the-middle, or other attacks”
While the passwordless nature of Zero Trust Authentication is visible front and center and instantly apparent to every user, phishing resistance must be instilled into the underlying core technology itself.
The White House put it quite succinctly in the Federal Zero Trust Strategy:
“…agency systems must discontinue support for authentication methods that fail to resist phishing, such as protocols that register phone numbers for SMS or voice calls, supply one-time codes, or receive push notifications.”
Removing SMS, one time codes, calls and push notifications gets rid of most of the factors that are being exploited by threat actors today. Beyond Identity uses more modern PKI and FIDO2-based technology to provide a fully phishing-resistant system. This is in line with guidance from CISA, the United States Cybersecurity and Infrastructure Security Agency, that oversees critical infrastructure security and resilience, which confirm in their Fact Sheet “Implementing Phishing-Resistant MFA” Fact Sheet, that “The only widely available phishing-resistant authentication is FIDO/WebAuthn authentication.”
Beyond Identity provides both a platform authenticator as well as a roaming authenticator to solve for all the use cases of a modern, distributed enterprise.
3. User device validation
“Ensures that requesting devices are bound to a user and authorized to access information assets and applications”
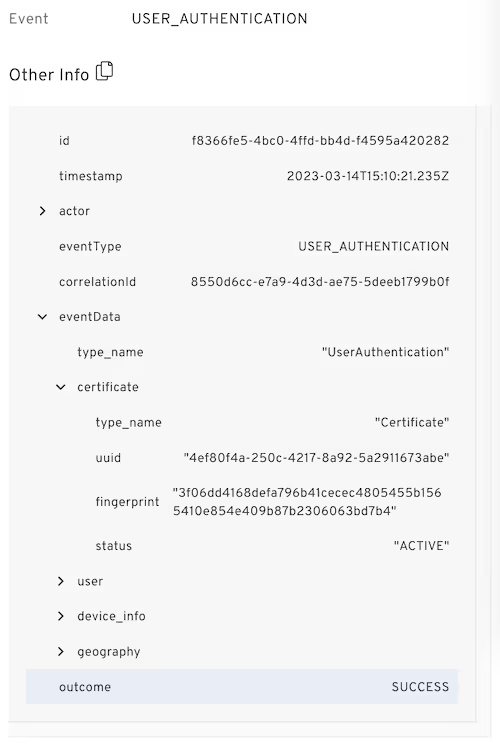
Unlike enterprises, which have slowly been exploring BYOD schemes, threat actors have always had to bring their own devices. They immediately realized that all they had to do to bypass first-generation MFA was either socially engineer/phish the code (whether via SMS, hardware token, or phone app) from the user, or cause the user to press “Yes” on a mobile device to authorize access for the attacker’s computer, which effectively removes the user’s own device from the picture.
These attacks are effective because they abuse one of the typical factors in authentication: possession. Knowing a code that can be phished doesn’t actually prove possession of anything.
Beyond Identity uses the cryptographic hardware present in modern computers to validate device trust relationships. It is purpose-built to generate and maintain keys that cannot physically be extracted, moved, or stolen, and can easily be verified using standard software. Beyond Identity uses this hardware in a novel manner, backed by managed PKI within the framework of the industry-standard FIDO protocol suite, to ensure reliably that only authorized devices are granted access to data.
Our system re-establishes the trust in possession as an authentication factor that otherwise was lost as attackers learned to bypass systems based on tokens, codes, and pushes, and makes reliable authentication across multiple factors—typically possession (of the device) and inherence (via biometrics)—simple and easy for enterprises.
4. Device security posture assessment
“Determines whether devices comply with security policies by checking that appropriate security settings are enabled and security software is actively running”
Just because there is an authorized user operating from a legitimate device doesn’t ensure that the device itself is in a safe state to process protected data or connect to sensitive apps. There can be a lot of complexity in establishing whether a device is “safe” and this definition can be different for every enterprise and even for individual groups of users within the enterprise, such as executives, regular full-time employees, contractors, suppliers and partners.
For example, one-size-fits-all rules often fail to accommodate both employees with corporate devices in addition to contractors with their own devices, not to mention the challenges of supporting selective BYOD, outsourced business processes and divisions, extranets, and all of the other groups that are stakeholders in a modern business.
At a minimum, a robust policy engine is required to even begin to solve the problem. Beyond Identity provides users the ability to define a complete ruleset - just like in a firewall - to assess the posture of all the different devices that commonly and legitimately access data in a modern enterprise for all stakeholders in a robust manner.
The different capabilities of each operating system are abstracted into a modern interface, where the administrator sets requirements for the local configuration on a per-operating system basis:
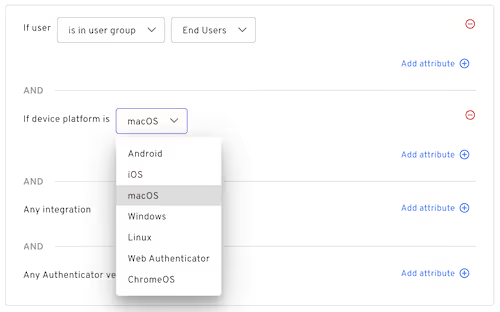
Users can enable different sets of requirements for each user community on each operating system. For example, it’s common to require some basic local hygiene for contractors accessing corporate systems:
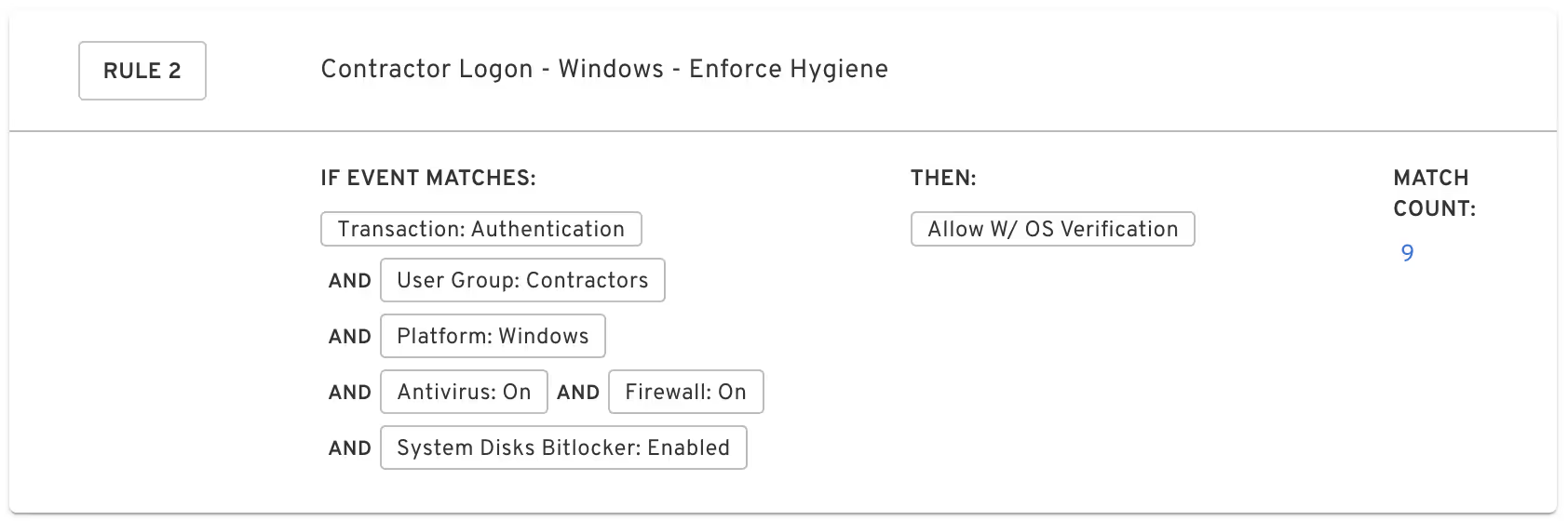
Here we see that users in the contractor group are required to have some antivirus software active, their firewall must not be disabled, and their disks must be encrypted in order to gain access to internal systems.
Other common use cases are to validate critical security settings, such as ensuring that Remote Desktop remains deactivated, that operating system versions are within expected constraints, or that local logon scripts are running correctly.
5. Multi-dimensional risk signal incorporation
“Ingests and analyzes data from endpoints and security and IT management tools, with a policy engine to assess risks based on factors such as user behavior, the security posture of devices, and the status of detection and response tools”
While the local security posture of a device is an important piece of the puzzle, it is insufficient to make risk decisions without signals from other security tools in today’s interconnected world.
Beyond Identity integrates with other security tools such as MDM and EDR to build a bridge between granting access to data or applications and enterprise endpoint management. That gap was hard to span before, as older types of authentication and MFA allowed any endpoint on the planet to be authorized just by knowing a code or accepting a push. Incorporating strong device trust and multi-dimensional risk signals allows organizations to gain new control over the devices accessing their data in cloud services.
To illustrate that, here is an example of a simple rule for internal employees. In this case, we’ll simply verify that the system is correctly enrolled in MDM and EDR before allowing access to data or applications:
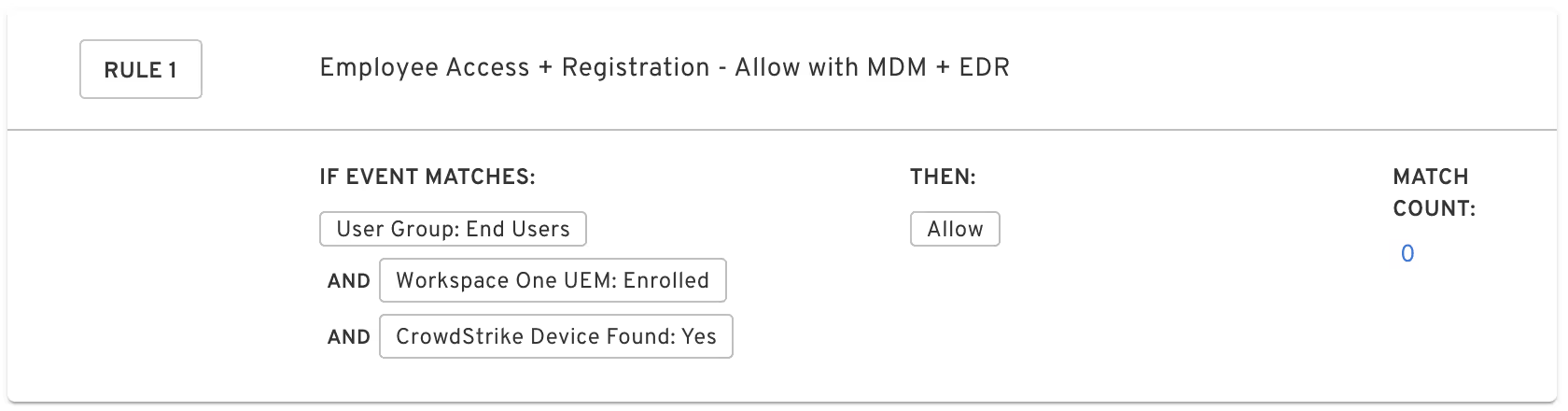
As you can see, this rule requires end user devices to be enrolled in both VMware MDM and CrowdStrike EDR before allowing access.
Though deceptively simple, it’s a powerful rule. These checks for MDM and EDR are performed via cloud-to-cloud via direct API calls, allowing Beyond Identity to verify directly with those third-party providers that the device is correctly registered and in good standing with their external systems.
Attackers have been faking processes since they were knee high to their local grasshoppers, but spoofing is not an option anymore when we’re talking to the real CrowdStrike cloud and gathering risk signals there.
Specifically for our joint customers with CrowdStrike, we also incorporate CrowdStrike’s security baseline, called the Zero Trust Assessment Score. The above rule can easily be expanded to include that context. For example, in an environment where the average baseline score is 75, and no endpoints are seen below 60, the administrator might configure it like this:
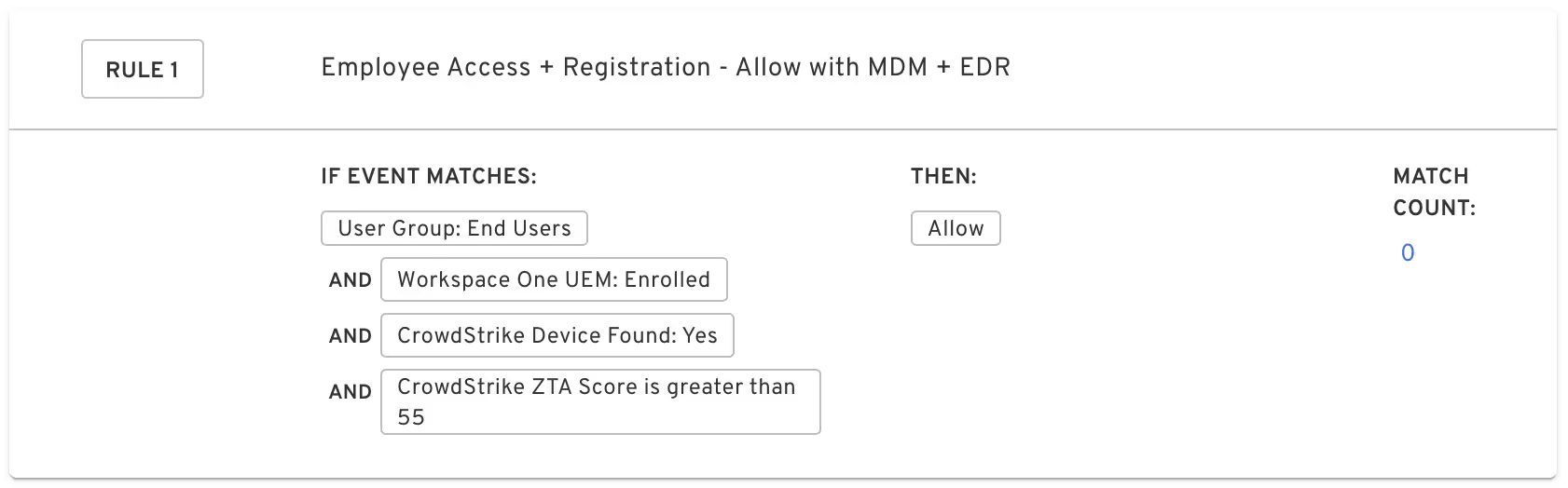
Of course, the administrator might also include a monitoring rule to alert on endpoints that are dipping under 60 so their SOC or help desk can review whether any actions need to be taken to remediate.
6. Continuous risk assessment
“Risk is evaluated throughout a session, rather than relying on one-time authentication to trust a full user session”
Defending against modern threat actors is a game of speed, in which waiting is a losing strategy. Beyond Identity continuously re-validates the full posture of every device.
In the event that a security posture violation is detected, Beyond Identity’s Zero Trust Policy Engine takes action, for example by isolating the endpoint on the network and kicking it out of the VPN.
No extra configuration or other work is needed on the part of the customer or administrator. There is no load or slowdown on user devices - until of course, a violation is detected and action is taken.
7. Integrated with the security infrastructure
“Context is integrated from a variety of tools in the security infrastructure to improve risk detection, accelerate responses to suspicious behaviors, while data is provided to others to improve audit and compliance reporting”
Knowledge without action is, of course, futile - not a lot of dogfights would be won without the last step in the OODA loop - but action without knowledge is useless. Beyond Identity security infrastructure integrations are designed to support every phase of the customer’s SOC process. Integrations can take the form of actions, such as taking action to neutralize the threat of a rogue endpoint, or sending information to other parts of the customer’s infrastructure.
In this example, there are multiple EDR solutions present in different areas of the fleet, as well as Zscaler for remote access, and action will be taken using whichever means are available against endpoints that maliciously fall out of compliance:
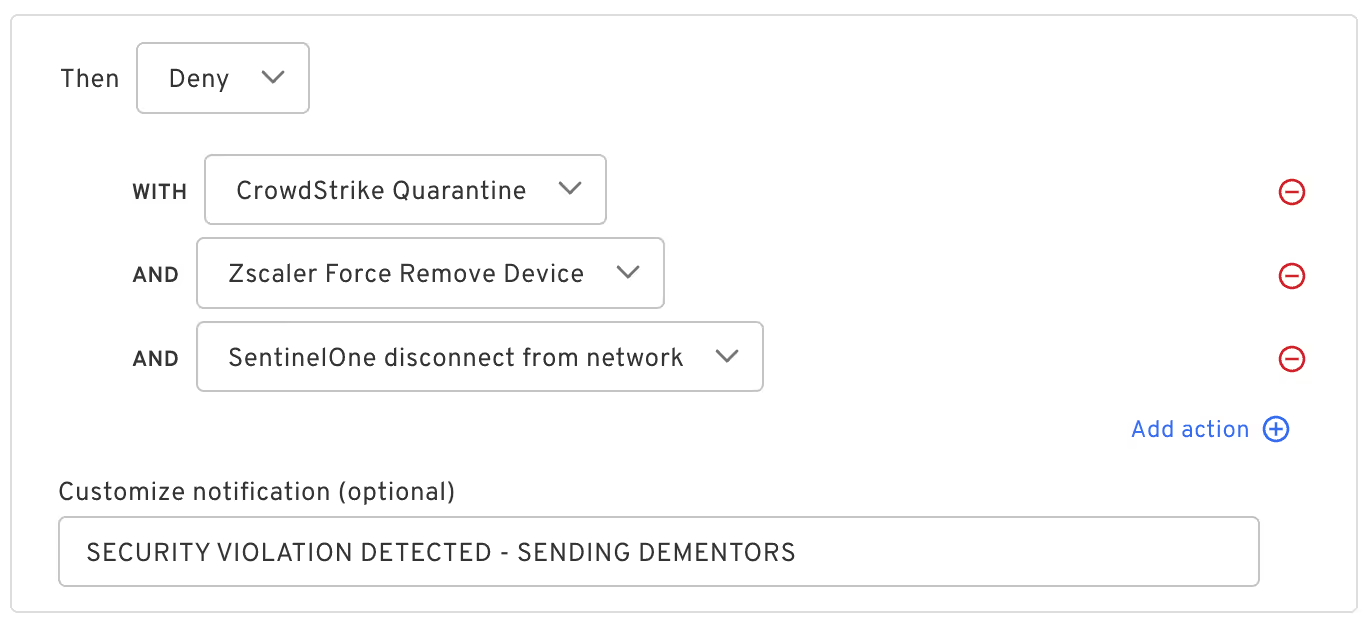
This organization has chosen to not only isolate the host and remote it from the extranet, they have also decided to implement a custom message to inform the user that dementors are on their way, probably to scare them straight.
Additionally, context is being sent to Splunk, where further analysis, alerting, and data processing can be performed:

The organization could have chosen from a handful of pre-integrated SIEM and GRC systems, or written their own integration using a generic webhook connector, to integrate with whatever particular flavors of infrastructure they have selected and implemented in their environment.
Conclusion
After studying the standards, speaking with security industry experts and collaborating with our most security-conscious customers, these seven key requirements emerged. They must all be operating in sync in order to realize the benefits of Zero Trust Authentication.
When brought into harmony, however, systems of this nature have the potential to achieving the rare trifecta:
- They can make life better and simpler for the user,
- Make systems more secure and resilient for the security team, and
- Make an organization easier to do business with for partners and customers.
We hope you enjoy the benefits of Zero Trust Authentication - reach out directly if we can help!
One of the most common questions we got as we prepared for today’s launch was what implementing effective Zero Trust Authentication “looks like” when done properly.
As we’ve discussed in various forums, there are seven key tenets of Zero Trust Authentication. All of them are critical to fulfilling the promise, so we’ll review them one-by-one and show you exactly what it looks like.
1. Passwordless
“No use of passwords or other shared secrets, because shared secrets can easily be obtained from users, captured on networks, or hacked from databases.”
Beyond Identity uses a combination of two factors for secure verification of user identity:
- A certificate, which is permanently and inextricably stored in the security hardware, such as a TPM (Trusted Platform Module, also known as ISO/IEC 11889), of every user device is used to prove possession. This certificate constitutes an individual, durable link to each authorized device belonging to a user, authorizing that device as one possible source of a secure login from that user.
- That certificate is unlocked using either biometrics, to prove inherence, or a PIN, to prove knowledge. Much like cameras, the best biometrics are the ones you have with you, so we leverage existing technology like Hello on Windows or TouchID and FaceID on Mac and iOS to safeguard users’ passkeys.
Just like the Chip+PIN security used to safeguard most bank accounts from unauthorized access at the ATM, these two factors only work when taken together. A single factor is worthless, much like someone in another country knowing your bank PIN without having your chip card.

2. Phishing resistant
“No opportunity to obtain codes, magic links, or other authentication factors through phishing, adversary-in-the-middle, or other attacks”
While the passwordless nature of Zero Trust Authentication is visible front and center and instantly apparent to every user, phishing resistance must be instilled into the underlying core technology itself.
The White House put it quite succinctly in the Federal Zero Trust Strategy:
“…agency systems must discontinue support for authentication methods that fail to resist phishing, such as protocols that register phone numbers for SMS or voice calls, supply one-time codes, or receive push notifications.”
Removing SMS, one time codes, calls and push notifications gets rid of most of the factors that are being exploited by threat actors today. Beyond Identity uses more modern PKI and FIDO2-based technology to provide a fully phishing-resistant system. This is in line with guidance from CISA, the United States Cybersecurity and Infrastructure Security Agency, that oversees critical infrastructure security and resilience, which confirm in their Fact Sheet “Implementing Phishing-Resistant MFA” Fact Sheet, that “The only widely available phishing-resistant authentication is FIDO/WebAuthn authentication.”
Beyond Identity provides both a platform authenticator as well as a roaming authenticator to solve for all the use cases of a modern, distributed enterprise.
3. User device validation
“Ensures that requesting devices are bound to a user and authorized to access information assets and applications”

Unlike enterprises, which have slowly been exploring BYOD schemes, threat actors have always had to bring their own devices. They immediately realized that all they had to do to bypass first-generation MFA was either socially engineer/phish the code (whether via SMS, hardware token, or phone app) from the user, or cause the user to press “Yes” on a mobile device to authorize access for the attacker’s computer, which effectively removes the user’s own device from the picture.
These attacks are effective because they abuse one of the typical factors in authentication: possession. Knowing a code that can be phished doesn’t actually prove possession of anything.
Beyond Identity uses the cryptographic hardware present in modern computers to validate device trust relationships. It is purpose-built to generate and maintain keys that cannot physically be extracted, moved, or stolen, and can easily be verified using standard software. Beyond Identity uses this hardware in a novel manner, backed by managed PKI within the framework of the industry-standard FIDO protocol suite, to ensure reliably that only authorized devices are granted access to data.
Our system re-establishes the trust in possession as an authentication factor that otherwise was lost as attackers learned to bypass systems based on tokens, codes, and pushes, and makes reliable authentication across multiple factors—typically possession (of the device) and inherence (via biometrics)—simple and easy for enterprises.
4. Device security posture assessment
“Determines whether devices comply with security policies by checking that appropriate security settings are enabled and security software is actively running”
Just because there is an authorized user operating from a legitimate device doesn’t ensure that the device itself is in a safe state to process protected data or connect to sensitive apps. There can be a lot of complexity in establishing whether a device is “safe” and this definition can be different for every enterprise and even for individual groups of users within the enterprise, such as executives, regular full-time employees, contractors, suppliers and partners.
For example, one-size-fits-all rules often fail to accommodate both employees with corporate devices in addition to contractors with their own devices, not to mention the challenges of supporting selective BYOD, outsourced business processes and divisions, extranets, and all of the other groups that are stakeholders in a modern business.
At a minimum, a robust policy engine is required to even begin to solve the problem. Beyond Identity provides users the ability to define a complete ruleset - just like in a firewall - to assess the posture of all the different devices that commonly and legitimately access data in a modern enterprise for all stakeholders in a robust manner.
The different capabilities of each operating system are abstracted into a modern interface, where the administrator sets requirements for the local configuration on a per-operating system basis:

Users can enable different sets of requirements for each user community on each operating system. For example, it’s common to require some basic local hygiene for contractors accessing corporate systems:

Here we see that users in the contractor group are required to have some antivirus software active, their firewall must not be disabled, and their disks must be encrypted in order to gain access to internal systems.
Other common use cases are to validate critical security settings, such as ensuring that Remote Desktop remains deactivated, that operating system versions are within expected constraints, or that local logon scripts are running correctly.
5. Multi-dimensional risk signal incorporation
“Ingests and analyzes data from endpoints and security and IT management tools, with a policy engine to assess risks based on factors such as user behavior, the security posture of devices, and the status of detection and response tools”
While the local security posture of a device is an important piece of the puzzle, it is insufficient to make risk decisions without signals from other security tools in today’s interconnected world.
Beyond Identity integrates with other security tools such as MDM and EDR to build a bridge between granting access to data or applications and enterprise endpoint management. That gap was hard to span before, as older types of authentication and MFA allowed any endpoint on the planet to be authorized just by knowing a code or accepting a push. Incorporating strong device trust and multi-dimensional risk signals allows organizations to gain new control over the devices accessing their data in cloud services.
To illustrate that, here is an example of a simple rule for internal employees. In this case, we’ll simply verify that the system is correctly enrolled in MDM and EDR before allowing access to data or applications:

As you can see, this rule requires end user devices to be enrolled in both VMware MDM and CrowdStrike EDR before allowing access.
Though deceptively simple, it’s a powerful rule. These checks for MDM and EDR are performed via cloud-to-cloud via direct API calls, allowing Beyond Identity to verify directly with those third-party providers that the device is correctly registered and in good standing with their external systems.
Attackers have been faking processes since they were knee high to their local grasshoppers, but spoofing is not an option anymore when we’re talking to the real CrowdStrike cloud and gathering risk signals there.
Specifically for our joint customers with CrowdStrike, we also incorporate CrowdStrike’s security baseline, called the Zero Trust Assessment Score. The above rule can easily be expanded to include that context. For example, in an environment where the average baseline score is 75, and no endpoints are seen below 60, the administrator might configure it like this:

Of course, the administrator might also include a monitoring rule to alert on endpoints that are dipping under 60 so their SOC or help desk can review whether any actions need to be taken to remediate.
6. Continuous risk assessment
“Risk is evaluated throughout a session, rather than relying on one-time authentication to trust a full user session”

Defending against modern threat actors is a game of speed, in which waiting is a losing strategy. Beyond Identity continuously re-validates the full posture of every device.
In the event that a security posture violation is detected, Beyond Identity’s Zero Trust Policy Engine takes action, for example by isolating the endpoint on the network and kicking it out of the VPN.
No extra configuration or other work is needed on the part of the customer or administrator. There is no load or slowdown on user devices - until of course, a violation is detected and action is taken.
7. Integrated with the security infrastructure
“Context is integrated from a variety of tools in the security infrastructure to improve risk detection, accelerate responses to suspicious behaviors, while data is provided to others to improve audit and compliance reporting”
Knowledge without action is, of course, futile - not a lot of dogfights would be won without the last step in the OODA loop - but action without knowledge is useless. Beyond Identity security infrastructure integrations are designed to support every phase of the customer’s SOC process. Integrations can take the form of actions, such as taking action to neutralize the threat of a rogue endpoint, or sending information to other parts of the customer’s infrastructure.
In this example, there are multiple EDR solutions present in different areas of the fleet, as well as Zscaler for remote access, and action will be taken using whichever means are available against endpoints that maliciously fall out of compliance:

This organization has chosen to not only isolate the host and remote it from the extranet, they have also decided to implement a custom message to inform the user that dementors are on their way, probably to scare them straight.
Additionally, context is being sent to Splunk, where further analysis, alerting, and data processing can be performed:

The organization could have chosen from a handful of pre-integrated SIEM and GRC systems, or written their own integration using a generic webhook connector, to integrate with whatever particular flavors of infrastructure they have selected and implemented in their environment.
Conclusion
After studying the standards, speaking with security industry experts and collaborating with our most security-conscious customers, these seven key requirements emerged. They must all be operating in sync in order to realize the benefits of Zero Trust Authentication.
When brought into harmony, however, systems of this nature have the potential to achieving the rare trifecta:
- They can make life better and simpler for the user,
- Make systems more secure and resilient for the security team, and
- Make an organization easier to do business with for partners and customers.
We hope you enjoy the benefits of Zero Trust Authentication - reach out directly if we can help!
One of the most common questions we got as we prepared for today’s launch was what implementing effective Zero Trust Authentication “looks like” when done properly.
As we’ve discussed in various forums, there are seven key tenets of Zero Trust Authentication. All of them are critical to fulfilling the promise, so we’ll review them one-by-one and show you exactly what it looks like.
1. Passwordless
“No use of passwords or other shared secrets, because shared secrets can easily be obtained from users, captured on networks, or hacked from databases.”
Beyond Identity uses a combination of two factors for secure verification of user identity:
- A certificate, which is permanently and inextricably stored in the security hardware, such as a TPM (Trusted Platform Module, also known as ISO/IEC 11889), of every user device is used to prove possession. This certificate constitutes an individual, durable link to each authorized device belonging to a user, authorizing that device as one possible source of a secure login from that user.
- That certificate is unlocked using either biometrics, to prove inherence, or a PIN, to prove knowledge. Much like cameras, the best biometrics are the ones you have with you, so we leverage existing technology like Hello on Windows or TouchID and FaceID on Mac and iOS to safeguard users’ passkeys.
Just like the Chip+PIN security used to safeguard most bank accounts from unauthorized access at the ATM, these two factors only work when taken together. A single factor is worthless, much like someone in another country knowing your bank PIN without having your chip card.

2. Phishing resistant
“No opportunity to obtain codes, magic links, or other authentication factors through phishing, adversary-in-the-middle, or other attacks”
While the passwordless nature of Zero Trust Authentication is visible front and center and instantly apparent to every user, phishing resistance must be instilled into the underlying core technology itself.
The White House put it quite succinctly in the Federal Zero Trust Strategy:
“…agency systems must discontinue support for authentication methods that fail to resist phishing, such as protocols that register phone numbers for SMS or voice calls, supply one-time codes, or receive push notifications.”
Removing SMS, one time codes, calls and push notifications gets rid of most of the factors that are being exploited by threat actors today. Beyond Identity uses more modern PKI and FIDO2-based technology to provide a fully phishing-resistant system. This is in line with guidance from CISA, the United States Cybersecurity and Infrastructure Security Agency, that oversees critical infrastructure security and resilience, which confirm in their Fact Sheet “Implementing Phishing-Resistant MFA” Fact Sheet, that “The only widely available phishing-resistant authentication is FIDO/WebAuthn authentication.”
Beyond Identity provides both a platform authenticator as well as a roaming authenticator to solve for all the use cases of a modern, distributed enterprise.
3. User device validation
“Ensures that requesting devices are bound to a user and authorized to access information assets and applications”

Unlike enterprises, which have slowly been exploring BYOD schemes, threat actors have always had to bring their own devices. They immediately realized that all they had to do to bypass first-generation MFA was either socially engineer/phish the code (whether via SMS, hardware token, or phone app) from the user, or cause the user to press “Yes” on a mobile device to authorize access for the attacker’s computer, which effectively removes the user’s own device from the picture.
These attacks are effective because they abuse one of the typical factors in authentication: possession. Knowing a code that can be phished doesn’t actually prove possession of anything.
Beyond Identity uses the cryptographic hardware present in modern computers to validate device trust relationships. It is purpose-built to generate and maintain keys that cannot physically be extracted, moved, or stolen, and can easily be verified using standard software. Beyond Identity uses this hardware in a novel manner, backed by managed PKI within the framework of the industry-standard FIDO protocol suite, to ensure reliably that only authorized devices are granted access to data.
Our system re-establishes the trust in possession as an authentication factor that otherwise was lost as attackers learned to bypass systems based on tokens, codes, and pushes, and makes reliable authentication across multiple factors—typically possession (of the device) and inherence (via biometrics)—simple and easy for enterprises.
4. Device security posture assessment
“Determines whether devices comply with security policies by checking that appropriate security settings are enabled and security software is actively running”
Just because there is an authorized user operating from a legitimate device doesn’t ensure that the device itself is in a safe state to process protected data or connect to sensitive apps. There can be a lot of complexity in establishing whether a device is “safe” and this definition can be different for every enterprise and even for individual groups of users within the enterprise, such as executives, regular full-time employees, contractors, suppliers and partners.
For example, one-size-fits-all rules often fail to accommodate both employees with corporate devices in addition to contractors with their own devices, not to mention the challenges of supporting selective BYOD, outsourced business processes and divisions, extranets, and all of the other groups that are stakeholders in a modern business.
At a minimum, a robust policy engine is required to even begin to solve the problem. Beyond Identity provides users the ability to define a complete ruleset - just like in a firewall - to assess the posture of all the different devices that commonly and legitimately access data in a modern enterprise for all stakeholders in a robust manner.
The different capabilities of each operating system are abstracted into a modern interface, where the administrator sets requirements for the local configuration on a per-operating system basis:

Users can enable different sets of requirements for each user community on each operating system. For example, it’s common to require some basic local hygiene for contractors accessing corporate systems:

Here we see that users in the contractor group are required to have some antivirus software active, their firewall must not be disabled, and their disks must be encrypted in order to gain access to internal systems.
Other common use cases are to validate critical security settings, such as ensuring that Remote Desktop remains deactivated, that operating system versions are within expected constraints, or that local logon scripts are running correctly.
5. Multi-dimensional risk signal incorporation
“Ingests and analyzes data from endpoints and security and IT management tools, with a policy engine to assess risks based on factors such as user behavior, the security posture of devices, and the status of detection and response tools”
While the local security posture of a device is an important piece of the puzzle, it is insufficient to make risk decisions without signals from other security tools in today’s interconnected world.
Beyond Identity integrates with other security tools such as MDM and EDR to build a bridge between granting access to data or applications and enterprise endpoint management. That gap was hard to span before, as older types of authentication and MFA allowed any endpoint on the planet to be authorized just by knowing a code or accepting a push. Incorporating strong device trust and multi-dimensional risk signals allows organizations to gain new control over the devices accessing their data in cloud services.
To illustrate that, here is an example of a simple rule for internal employees. In this case, we’ll simply verify that the system is correctly enrolled in MDM and EDR before allowing access to data or applications:

As you can see, this rule requires end user devices to be enrolled in both VMware MDM and CrowdStrike EDR before allowing access.
Though deceptively simple, it’s a powerful rule. These checks for MDM and EDR are performed via cloud-to-cloud via direct API calls, allowing Beyond Identity to verify directly with those third-party providers that the device is correctly registered and in good standing with their external systems.
Attackers have been faking processes since they were knee high to their local grasshoppers, but spoofing is not an option anymore when we’re talking to the real CrowdStrike cloud and gathering risk signals there.
Specifically for our joint customers with CrowdStrike, we also incorporate CrowdStrike’s security baseline, called the Zero Trust Assessment Score. The above rule can easily be expanded to include that context. For example, in an environment where the average baseline score is 75, and no endpoints are seen below 60, the administrator might configure it like this:

Of course, the administrator might also include a monitoring rule to alert on endpoints that are dipping under 60 so their SOC or help desk can review whether any actions need to be taken to remediate.
6. Continuous risk assessment
“Risk is evaluated throughout a session, rather than relying on one-time authentication to trust a full user session”

Defending against modern threat actors is a game of speed, in which waiting is a losing strategy. Beyond Identity continuously re-validates the full posture of every device.
In the event that a security posture violation is detected, Beyond Identity’s Zero Trust Policy Engine takes action, for example by isolating the endpoint on the network and kicking it out of the VPN.
No extra configuration or other work is needed on the part of the customer or administrator. There is no load or slowdown on user devices - until of course, a violation is detected and action is taken.
7. Integrated with the security infrastructure
“Context is integrated from a variety of tools in the security infrastructure to improve risk detection, accelerate responses to suspicious behaviors, while data is provided to others to improve audit and compliance reporting”
Knowledge without action is, of course, futile - not a lot of dogfights would be won without the last step in the OODA loop - but action without knowledge is useless. Beyond Identity security infrastructure integrations are designed to support every phase of the customer’s SOC process. Integrations can take the form of actions, such as taking action to neutralize the threat of a rogue endpoint, or sending information to other parts of the customer’s infrastructure.
In this example, there are multiple EDR solutions present in different areas of the fleet, as well as Zscaler for remote access, and action will be taken using whichever means are available against endpoints that maliciously fall out of compliance:

This organization has chosen to not only isolate the host and remote it from the extranet, they have also decided to implement a custom message to inform the user that dementors are on their way, probably to scare them straight.
Additionally, context is being sent to Splunk, where further analysis, alerting, and data processing can be performed:

The organization could have chosen from a handful of pre-integrated SIEM and GRC systems, or written their own integration using a generic webhook connector, to integrate with whatever particular flavors of infrastructure they have selected and implemented in their environment.
Conclusion
After studying the standards, speaking with security industry experts and collaborating with our most security-conscious customers, these seven key requirements emerged. They must all be operating in sync in order to realize the benefits of Zero Trust Authentication.
When brought into harmony, however, systems of this nature have the potential to achieving the rare trifecta:
- They can make life better and simpler for the user,
- Make systems more secure and resilient for the security team, and
- Make an organization easier to do business with for partners and customers.
We hope you enjoy the benefits of Zero Trust Authentication - reach out directly if we can help!







.png)






.avif)



.avif)






.avif)

