Beyond Identity + Okta Integration
Provide your workforce with a passwordless login and risk-based authorization for secure access to applications and data.
How to get started
To get started, simply add Beyond Identity as a delegated identity provider in Okta’s single sign-on. It only takes a few minutes to point Okta to our cloud-hosted identity provider.
Admins can leverage simple routing rules in the Okta Admin Console to enroll all users to Beyond Identity or selectively enroll individual users to specific apps.
Once enrolled, users can download the Beyond Identity Authenticator app and self-register their devices, enabling passwordless login for your Okta single sign-on and applications. Your users can easily add and remove additional devices to reduce lockouts and help desk tickets. You and other admins get full visibility into user login transactions and each devices’ security posture in Beyond Identity’s admin portal. There’s no need for mobile device management. Security posture data is provided by the Beyond Identity Authenticator app.
Logging in on different devices
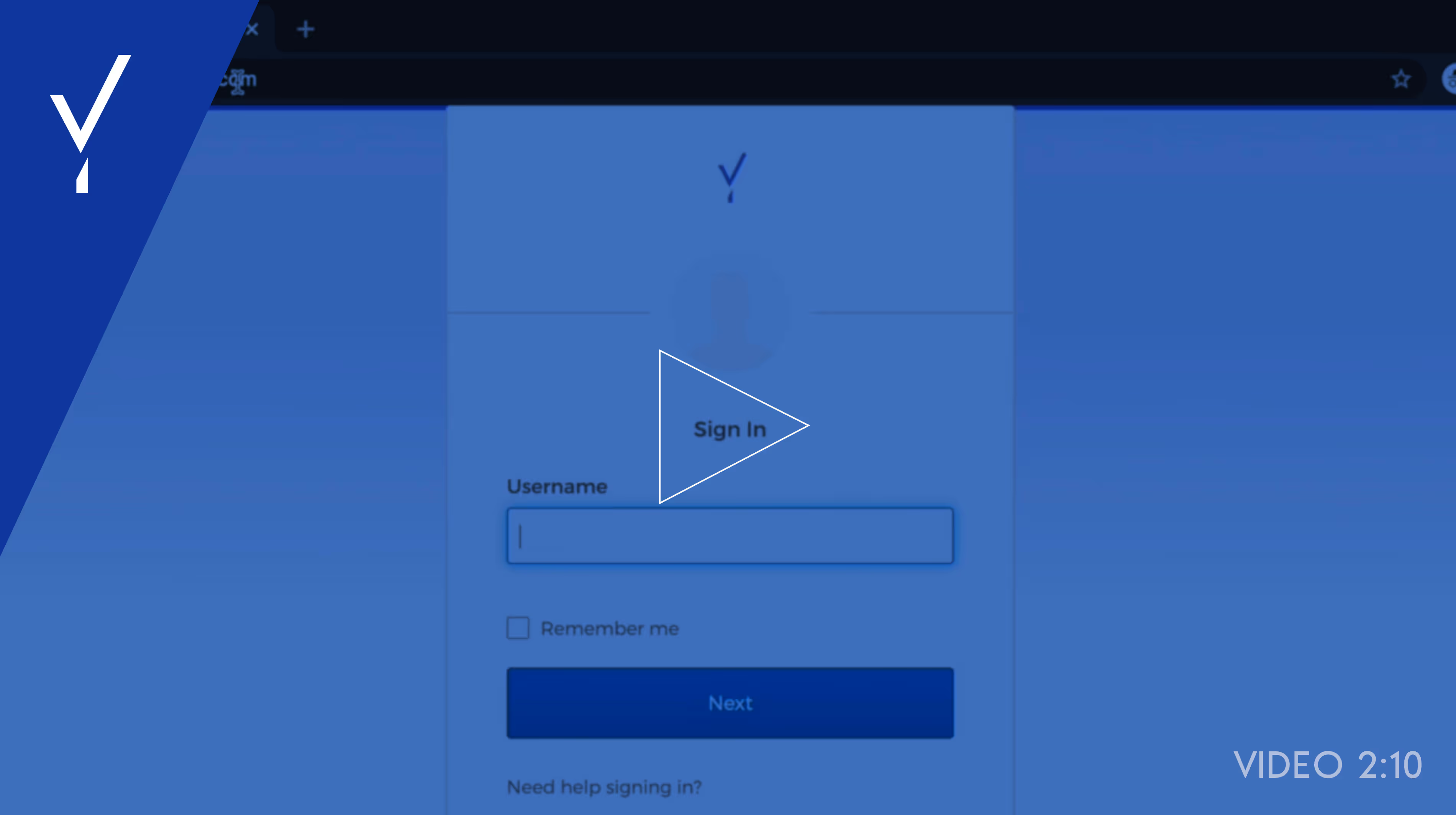
Now let’s log into my Okta End User Dashboard on a computer. As you can see, there is no password. I’ve put in my username and clicked next. And now I have access to my Okta End User Dashboard. I logged in securely without a password and without having to pick up a phone. Now it’s off to work.
Now let’s login to a desktop app. I’ve added my username, clicked next, and now we’re in. Once again, no password, no need for an external device.
Let’s login to a native app on my phone. I’ve put in my username, and again, no password. The Slack app automatically opens up the Beyond Identity Authenticator app, and now we’re logged into Slack. And just like that, you're done.
No passwords, no help desk calls, and no hassle.
Provide your workforce with a passwordless login and risk-based authorization for secure access to applications and data.
How to get started
To get started, simply add Beyond Identity as a delegated identity provider in Okta’s single sign-on. It only takes a few minutes to point Okta to our cloud-hosted identity provider.
Admins can leverage simple routing rules in the Okta Admin Console to enroll all users to Beyond Identity or selectively enroll individual users to specific apps.
Once enrolled, users can download the Beyond Identity Authenticator app and self-register their devices, enabling passwordless login for your Okta single sign-on and applications. Your users can easily add and remove additional devices to reduce lockouts and help desk tickets. You and other admins get full visibility into user login transactions and each devices’ security posture in Beyond Identity’s admin portal. There’s no need for mobile device management. Security posture data is provided by the Beyond Identity Authenticator app.
Logging in on different devices
Now let’s log into my Okta End User Dashboard on a computer. As you can see, there is no password. I’ve put in my username and clicked next. And now I have access to my Okta End User Dashboard. I logged in securely without a password and without having to pick up a phone. Now it’s off to work.
Now let’s login to a desktop app. I’ve added my username, clicked next, and now we’re in. Once again, no password, no need for an external device.
Let’s login to a native app on my phone. I’ve put in my username, and again, no password. The Slack app automatically opens up the Beyond Identity Authenticator app, and now we’re logged into Slack. And just like that, you're done.
No passwords, no help desk calls, and no hassle.
Provide your workforce with a passwordless login and risk-based authorization for secure access to applications and data.
How to get started
To get started, simply add Beyond Identity as a delegated identity provider in Okta’s single sign-on. It only takes a few minutes to point Okta to our cloud-hosted identity provider.
Admins can leverage simple routing rules in the Okta Admin Console to enroll all users to Beyond Identity or selectively enroll individual users to specific apps.
Once enrolled, users can download the Beyond Identity Authenticator app and self-register their devices, enabling passwordless login for your Okta single sign-on and applications. Your users can easily add and remove additional devices to reduce lockouts and help desk tickets. You and other admins get full visibility into user login transactions and each devices’ security posture in Beyond Identity’s admin portal. There’s no need for mobile device management. Security posture data is provided by the Beyond Identity Authenticator app.
Logging in on different devices
Now let’s log into my Okta End User Dashboard on a computer. As you can see, there is no password. I’ve put in my username and clicked next. And now I have access to my Okta End User Dashboard. I logged in securely without a password and without having to pick up a phone. Now it’s off to work.
Now let’s login to a desktop app. I’ve added my username, clicked next, and now we’re in. Once again, no password, no need for an external device.
Let’s login to a native app on my phone. I’ve put in my username, and again, no password. The Slack app automatically opens up the Beyond Identity Authenticator app, and now we’re logged into Slack. And just like that, you're done.
No passwords, no help desk calls, and no hassle.






.png)






.avif)



.avif)






.avif)

