Introducing New Device Context and MDM Integrations
We’re excited to introduce new device context for risk-based authentication! There’s now 25+ new attributes to use in risk policies, plus new integrations with the most popular MDMs: Jamf, Microsoft Intune, and VMware Workspace ONE UEM.
We built this to help security teams stop risky users and devices from accessing company resources. This new feature helps close the gap and gives you greater access controls, especially to SaaS cloud apps, while giving authorized users the flexibility to access work from secure, approved devices.
Go passwordless to stop attackers from logging in from any device
It’s especially difficult to manage access to SaaS cloud applications. With SaaS, anyone can log in from any web browser, on any device if they can get a user’s password. We all know that passwords can be easily stolen and purchased on the dark web, and password-based attacks are the number one source of data breaches. Passwords can be stolen using a whole category of credential attacks, putting your company data at risk.
Eliminating passwords is the first step to stopping unauthorized users from logging in from any device.
The most secure way to go passwordless is to use Beyond Identity, which ensures that only registered users and their registered devices can request access to your company resources. Beyond Identity’s passwordless approach utilizes proven cryptography to tie users’ credentials to their registered devices. These credentials, in the form of private keys and certificates, are created on each device and can't be moved from the hardware of the device. This ensures that only identity-bound devices that are registered with Beyond Identity can request access to company resources.
Check every device for its security posture, even BYOD
Eliminating passwords is a great first step, however, this doesn’t ensure that the device requesting access is secure and can be trusted.
With Beyond Identity, each user and device also needs to pass behavioral and security checks to get in.
“Device trust” historically has been used to describe if a device is managed. However, just because a device has a MDM running on it doesn’t mean that important security software is running properly at the time of login (see our Triad of Risk blog post). Sometimes, the devices requesting access aren’t managed at all, and users are sometimes using BYOD.
It’s time to get visibility into these devices at the time of authentication.
25+ risk signals out-of-the-box for policies
Take advantage of 25+ attributes from users, devices, and applications – including granular device context from all desktop computers, tablets, and phones.
Risk signals are collected from every device with the Beyond Identity Authenticator, during every authentication, which includes unmanaged and BYOD, without requiring a third-party MDM:

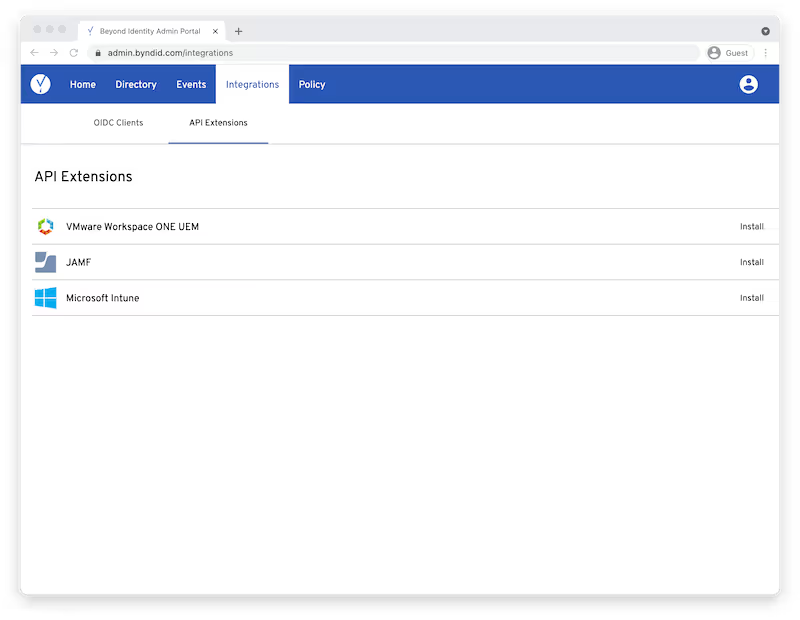
Additionally, if you already have a MDM on some devices, Beyond Identity has integrations with MDMs to enhance this data set for risk policies. It’s quick to configure these integrations:
Risk-based authentication is a practical step toward zero trust
Now security teams can get risk signals from both unmanaged and managed devices. This helps teams take a practical step toward achieving a zero trust security model – helping them check every user, every device, at every authentication. These risk policies can be configured with precision, using an expansive and extensible set of 25+ attributes out-of-the-box. Teams can customize policies to meet their risk tolerance in every situation and analyze them if they’re working as expected, or if they need to be fine-tuned.
We’re excited to introduce new device context for risk-based authentication! There’s now 25+ new attributes to use in risk policies, plus new integrations with the most popular MDMs: Jamf, Microsoft Intune, and VMware Workspace ONE UEM.
We built this to help security teams stop risky users and devices from accessing company resources. This new feature helps close the gap and gives you greater access controls, especially to SaaS cloud apps, while giving authorized users the flexibility to access work from secure, approved devices.
Go passwordless to stop attackers from logging in from any device
It’s especially difficult to manage access to SaaS cloud applications. With SaaS, anyone can log in from any web browser, on any device if they can get a user’s password. We all know that passwords can be easily stolen and purchased on the dark web, and password-based attacks are the number one source of data breaches. Passwords can be stolen using a whole category of credential attacks, putting your company data at risk.
Eliminating passwords is the first step to stopping unauthorized users from logging in from any device.
The most secure way to go passwordless is to use Beyond Identity, which ensures that only registered users and their registered devices can request access to your company resources. Beyond Identity’s passwordless approach utilizes proven cryptography to tie users’ credentials to their registered devices. These credentials, in the form of private keys and certificates, are created on each device and can't be moved from the hardware of the device. This ensures that only identity-bound devices that are registered with Beyond Identity can request access to company resources.
Check every device for its security posture, even BYOD
Eliminating passwords is a great first step, however, this doesn’t ensure that the device requesting access is secure and can be trusted.
With Beyond Identity, each user and device also needs to pass behavioral and security checks to get in.
“Device trust” historically has been used to describe if a device is managed. However, just because a device has a MDM running on it doesn’t mean that important security software is running properly at the time of login (see our Triad of Risk blog post). Sometimes, the devices requesting access aren’t managed at all, and users are sometimes using BYOD.
It’s time to get visibility into these devices at the time of authentication.
25+ risk signals out-of-the-box for policies
Take advantage of 25+ attributes from users, devices, and applications – including granular device context from all desktop computers, tablets, and phones.
Risk signals are collected from every device with the Beyond Identity Authenticator, during every authentication, which includes unmanaged and BYOD, without requiring a third-party MDM:

Additionally, if you already have a MDM on some devices, Beyond Identity has integrations with MDMs to enhance this data set for risk policies. It’s quick to configure these integrations:

Risk-based authentication is a practical step toward zero trust
Now security teams can get risk signals from both unmanaged and managed devices. This helps teams take a practical step toward achieving a zero trust security model – helping them check every user, every device, at every authentication. These risk policies can be configured with precision, using an expansive and extensible set of 25+ attributes out-of-the-box. Teams can customize policies to meet their risk tolerance in every situation and analyze them if they’re working as expected, or if they need to be fine-tuned.
We’re excited to introduce new device context for risk-based authentication! There’s now 25+ new attributes to use in risk policies, plus new integrations with the most popular MDMs: Jamf, Microsoft Intune, and VMware Workspace ONE UEM.
We built this to help security teams stop risky users and devices from accessing company resources. This new feature helps close the gap and gives you greater access controls, especially to SaaS cloud apps, while giving authorized users the flexibility to access work from secure, approved devices.
Go passwordless to stop attackers from logging in from any device
It’s especially difficult to manage access to SaaS cloud applications. With SaaS, anyone can log in from any web browser, on any device if they can get a user’s password. We all know that passwords can be easily stolen and purchased on the dark web, and password-based attacks are the number one source of data breaches. Passwords can be stolen using a whole category of credential attacks, putting your company data at risk.
Eliminating passwords is the first step to stopping unauthorized users from logging in from any device.
The most secure way to go passwordless is to use Beyond Identity, which ensures that only registered users and their registered devices can request access to your company resources. Beyond Identity’s passwordless approach utilizes proven cryptography to tie users’ credentials to their registered devices. These credentials, in the form of private keys and certificates, are created on each device and can't be moved from the hardware of the device. This ensures that only identity-bound devices that are registered with Beyond Identity can request access to company resources.
Check every device for its security posture, even BYOD
Eliminating passwords is a great first step, however, this doesn’t ensure that the device requesting access is secure and can be trusted.
With Beyond Identity, each user and device also needs to pass behavioral and security checks to get in.
“Device trust” historically has been used to describe if a device is managed. However, just because a device has a MDM running on it doesn’t mean that important security software is running properly at the time of login (see our Triad of Risk blog post). Sometimes, the devices requesting access aren’t managed at all, and users are sometimes using BYOD.
It’s time to get visibility into these devices at the time of authentication.
25+ risk signals out-of-the-box for policies
Take advantage of 25+ attributes from users, devices, and applications – including granular device context from all desktop computers, tablets, and phones.
Risk signals are collected from every device with the Beyond Identity Authenticator, during every authentication, which includes unmanaged and BYOD, without requiring a third-party MDM:

Additionally, if you already have a MDM on some devices, Beyond Identity has integrations with MDMs to enhance this data set for risk policies. It’s quick to configure these integrations:

Risk-based authentication is a practical step toward zero trust
Now security teams can get risk signals from both unmanaged and managed devices. This helps teams take a practical step toward achieving a zero trust security model – helping them check every user, every device, at every authentication. These risk policies can be configured with precision, using an expansive and extensible set of 25+ attributes out-of-the-box. Teams can customize policies to meet their risk tolerance in every situation and analyze them if they’re working as expected, or if they need to be fine-tuned.







.png)






.avif)



.avif)






.avif)

