How to Ensure Security Settings Are Configured Properly on Your Employees' Devices
Having device context is critical to enforcing security policies at your organization, especially with the accelerated adoption of remote work.
Now there’s a way to gather security context from managed and unmanaged devices in a single solution so you can make secure access decisions.
You can write authentication policies in Beyond Identity based on the managed status of a device. You can also create policy checks for almost any software or configuration on Windows and macOS devices.
How to Make Sure Your Employees’ Devices Are Secure
The Beyond Identity passwordless authentication platform not only eliminates the use of passwords at your company but also looks at device security context to enforce authentication.
It looks at two aspects of device security: the settings on the device itself and the status of the third-party security apps running on the device.
Check the Security Settings for Unmanaged and Managed Devices
You can write policies in the Beyond Identity console that inspect device security settings before authenticating a user to an application. Some attributes include:
- Is the device iOS, MacOS, Android, or Windows?
- Is the device managed or unmanaged?
- Are biometrics enabled?
- Is encryption on?
- Is the firewall activated?
- Is the device jailbroken or rooted?
- Is the machine running the most up-to-date operating system?
You can also create policies that check if certain files, applications, packages, services, and processes are running on the device.
Here’s a look inside the console that you’d use to create these policies.
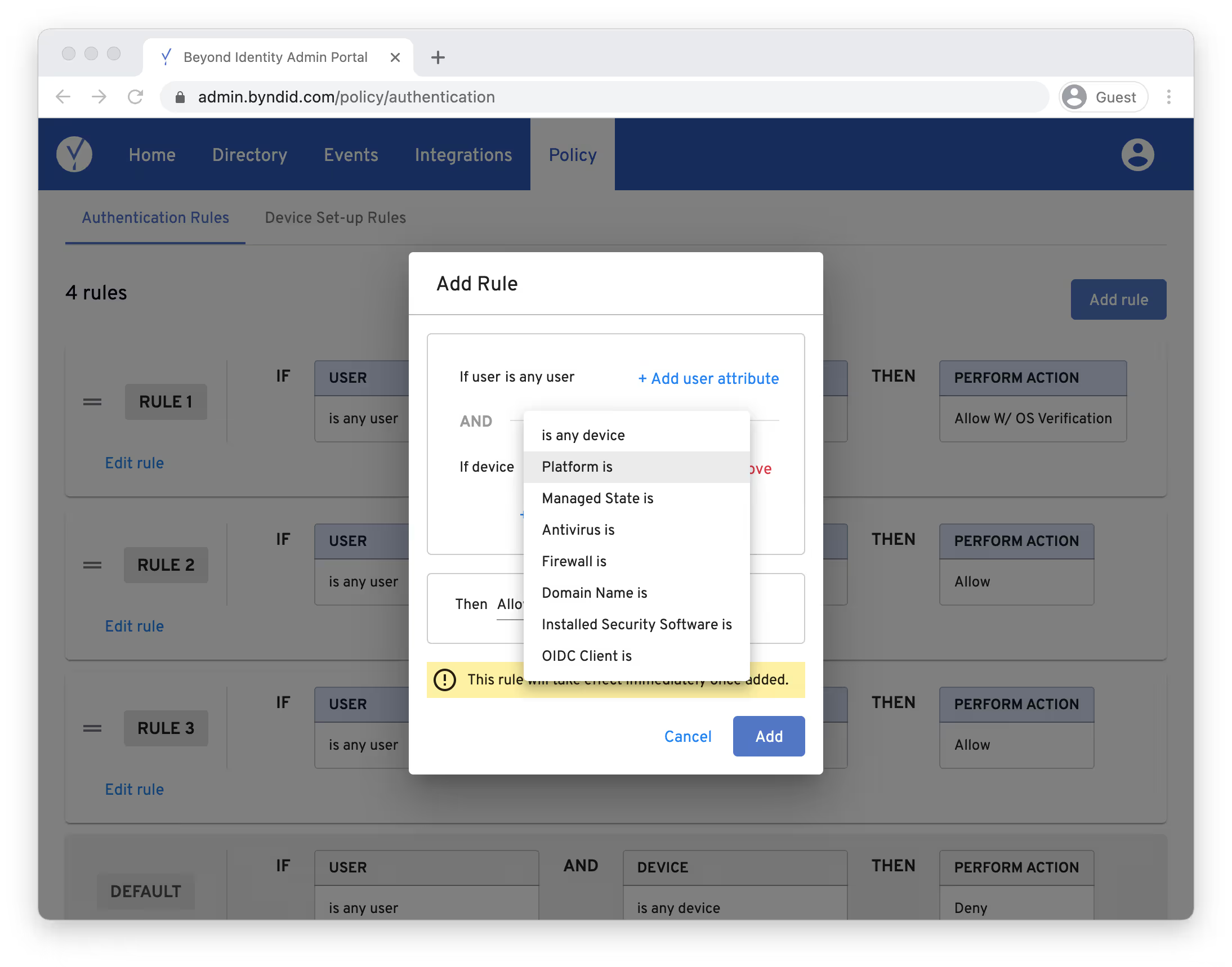
For companies that don’t have UEM, these risk-based policies are a powerful alternative.
Now you can trust that these “untrusted” devices are no longer accessing company resources at will.
Check How Your Security Software Is Communicating With Managed Devices
Beyond Identity also sees the software installed and running on devices. This includes integrations with your endpoint management, asset management, and security tools.
With this information, you can create dynamic policies that add more detail to the checks for security settings mentioned in the previous section.
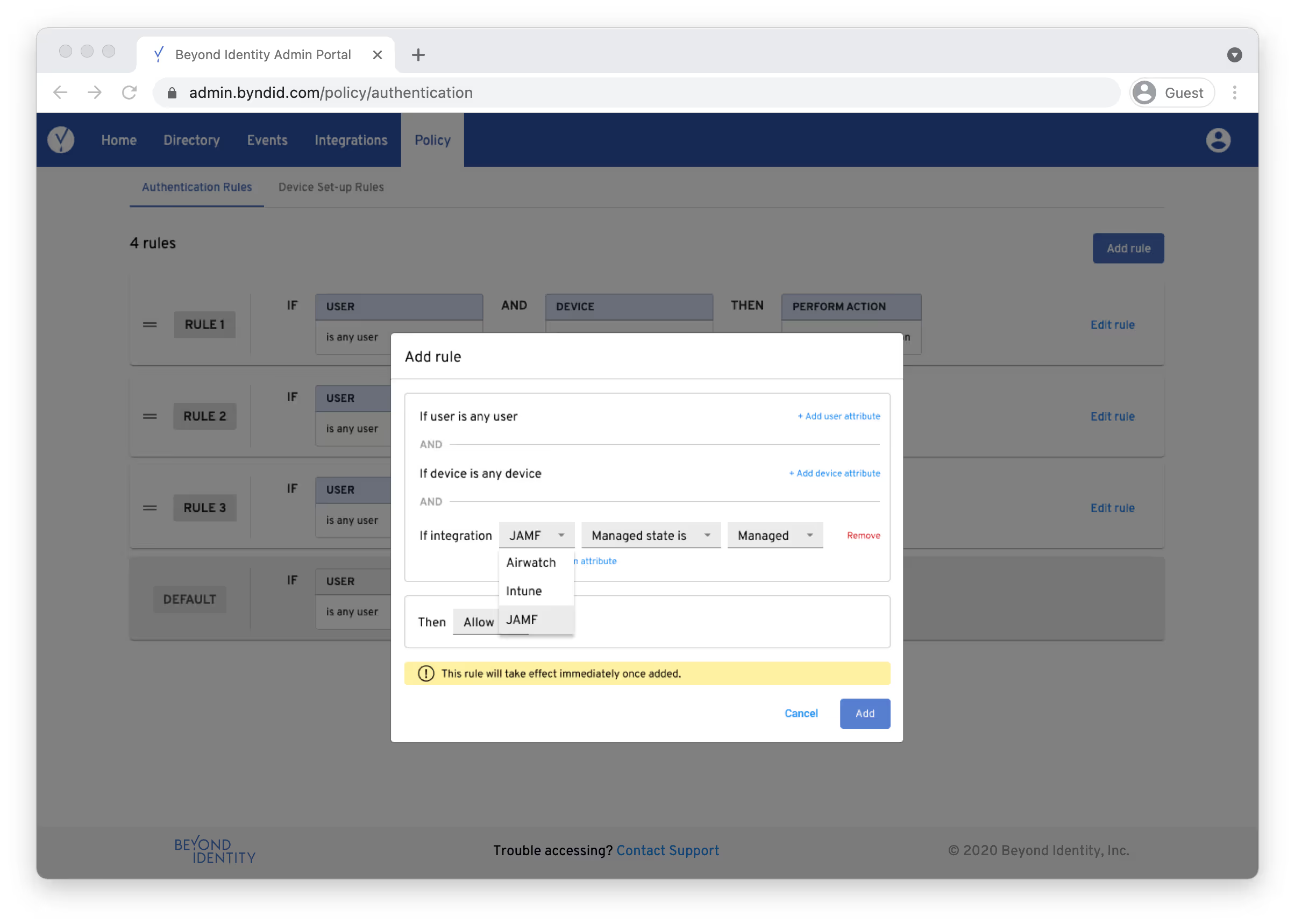
Does your organization use VMware Workspace ONE UEM, Microsoft Intune, or Jamf? Beyond Identity checks if every device in your environment is managed or enrolled. If a device is not, you can deny that user access.
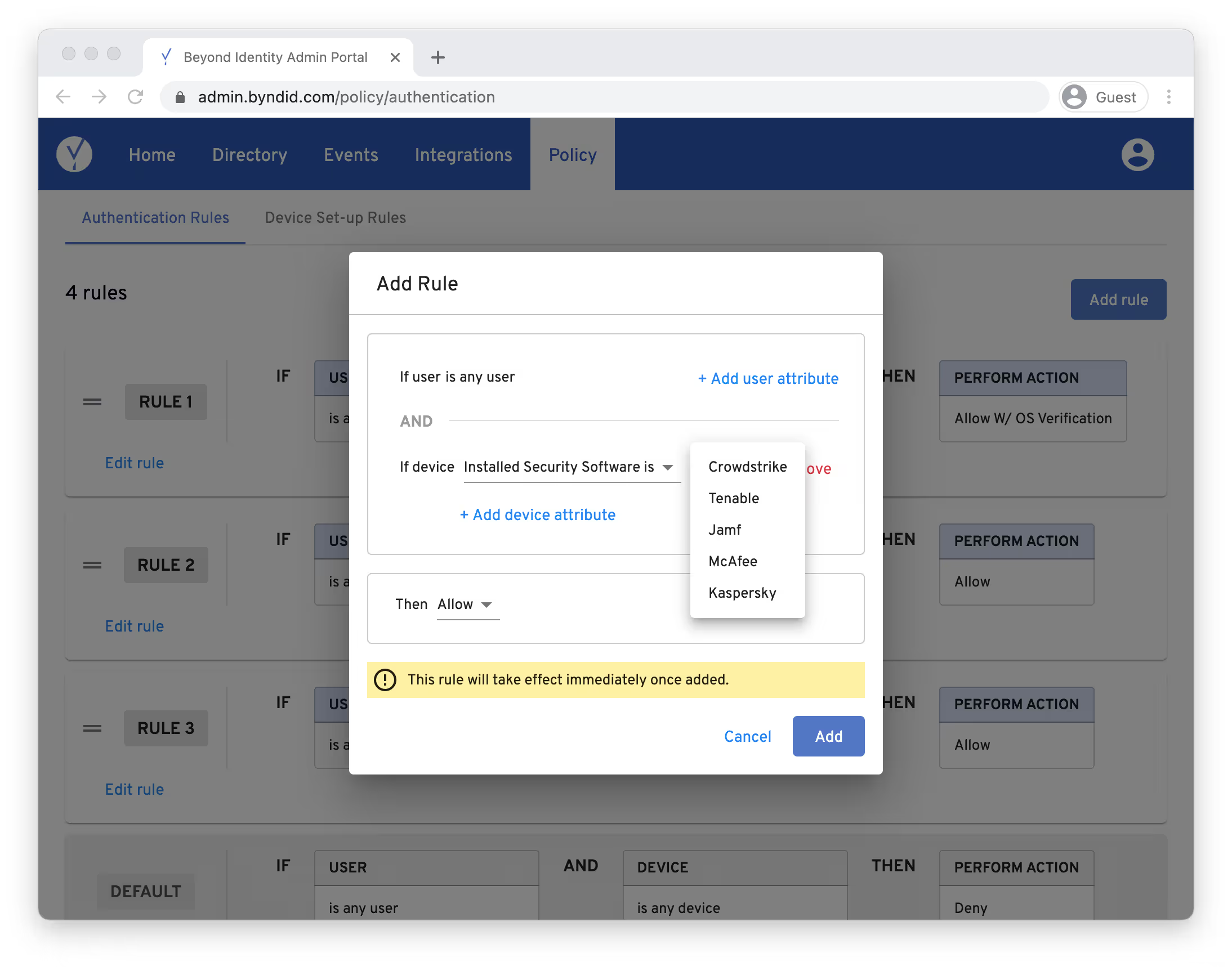
Does your organization use CrowdStrike, Tenable, McAfee, Kaspersky, or Jamf? Beyond Identity checks that employee devices are reporting into the cloud and getting configurations.
For example, you can see:
- Is the correct version of CrowdStrike running on your employees’ machines?
- Is the machine talking to the CrowdStrike cloud?
- When was the last time the machine checked into the CrowdStrike server
Enforcing Risk-Based Authentication Starts With Secure Devices
The device checks from Beyond Identity let you ask detailed questions in your security policies, giving you peace of mind that your security setup is totally functional.
Check out how it works in the video below.
Having device context is critical to enforcing security policies at your organization, especially with the accelerated adoption of remote work.
Now there’s a way to gather security context from managed and unmanaged devices in a single solution so you can make secure access decisions.
You can write authentication policies in Beyond Identity based on the managed status of a device. You can also create policy checks for almost any software or configuration on Windows and macOS devices.
How to Make Sure Your Employees’ Devices Are Secure
The Beyond Identity passwordless authentication platform not only eliminates the use of passwords at your company but also looks at device security context to enforce authentication.
It looks at two aspects of device security: the settings on the device itself and the status of the third-party security apps running on the device.
Check the Security Settings for Unmanaged and Managed Devices
You can write policies in the Beyond Identity console that inspect device security settings before authenticating a user to an application. Some attributes include:
- Is the device iOS, MacOS, Android, or Windows?
- Is the device managed or unmanaged?
- Are biometrics enabled?
- Is encryption on?
- Is the firewall activated?
- Is the device jailbroken or rooted?
- Is the machine running the most up-to-date operating system?
You can also create policies that check if certain files, applications, packages, services, and processes are running on the device.
Here’s a look inside the console that you’d use to create these policies.

For companies that don’t have UEM, these risk-based policies are a powerful alternative.
Now you can trust that these “untrusted” devices are no longer accessing company resources at will.
Check How Your Security Software Is Communicating With Managed Devices
Beyond Identity also sees the software installed and running on devices. This includes integrations with your endpoint management, asset management, and security tools.
With this information, you can create dynamic policies that add more detail to the checks for security settings mentioned in the previous section.
Does your organization use VMware Workspace ONE UEM, Microsoft Intune, or Jamf? Beyond Identity checks if every device in your environment is managed or enrolled. If a device is not, you can deny that user access.

Does your organization use CrowdStrike, Tenable, McAfee, Kaspersky, or Jamf? Beyond Identity checks that employee devices are reporting into the cloud and getting configurations.
For example, you can see:
- Is the correct version of CrowdStrike running on your employees’ machines?
- Is the machine talking to the CrowdStrike cloud?
- When was the last time the machine checked into the CrowdStrike server

Enforcing Risk-Based Authentication Starts With Secure Devices
The device checks from Beyond Identity let you ask detailed questions in your security policies, giving you peace of mind that your security setup is totally functional.
Check out how it works in the video below.
Having device context is critical to enforcing security policies at your organization, especially with the accelerated adoption of remote work.
Now there’s a way to gather security context from managed and unmanaged devices in a single solution so you can make secure access decisions.
You can write authentication policies in Beyond Identity based on the managed status of a device. You can also create policy checks for almost any software or configuration on Windows and macOS devices.
How to Make Sure Your Employees’ Devices Are Secure
The Beyond Identity passwordless authentication platform not only eliminates the use of passwords at your company but also looks at device security context to enforce authentication.
It looks at two aspects of device security: the settings on the device itself and the status of the third-party security apps running on the device.
Check the Security Settings for Unmanaged and Managed Devices
You can write policies in the Beyond Identity console that inspect device security settings before authenticating a user to an application. Some attributes include:
- Is the device iOS, MacOS, Android, or Windows?
- Is the device managed or unmanaged?
- Are biometrics enabled?
- Is encryption on?
- Is the firewall activated?
- Is the device jailbroken or rooted?
- Is the machine running the most up-to-date operating system?
You can also create policies that check if certain files, applications, packages, services, and processes are running on the device.
Here’s a look inside the console that you’d use to create these policies.

For companies that don’t have UEM, these risk-based policies are a powerful alternative.
Now you can trust that these “untrusted” devices are no longer accessing company resources at will.
Check How Your Security Software Is Communicating With Managed Devices
Beyond Identity also sees the software installed and running on devices. This includes integrations with your endpoint management, asset management, and security tools.
With this information, you can create dynamic policies that add more detail to the checks for security settings mentioned in the previous section.
Does your organization use VMware Workspace ONE UEM, Microsoft Intune, or Jamf? Beyond Identity checks if every device in your environment is managed or enrolled. If a device is not, you can deny that user access.

Does your organization use CrowdStrike, Tenable, McAfee, Kaspersky, or Jamf? Beyond Identity checks that employee devices are reporting into the cloud and getting configurations.
For example, you can see:
- Is the correct version of CrowdStrike running on your employees’ machines?
- Is the machine talking to the CrowdStrike cloud?
- When was the last time the machine checked into the CrowdStrike server

Enforcing Risk-Based Authentication Starts With Secure Devices
The device checks from Beyond Identity let you ask detailed questions in your security policies, giving you peace of mind that your security setup is totally functional.
Check out how it works in the video below.












.avif)
.avif)



.avif)






.avif)

