Hacking Microsoft in Real Time: Username and Password
Transcript
Today, we are going to see a case study of what a phishing attack looks like using an open source transparent phishing proxy.
Our demo begins with our threat actor, Clara, preparing a phishing email. She uses a template she has found successful in the past, and customizes it for her victim. This template attempts to manipulate the victim into opening the link based on the premise of someone impersonating the victim on LinkedIn.
She knows the victim uses Microsoft Office 365, so she prepares a phishing link that looks like an Office Share link. Since she knows the victim will be less likely to be suspicious of interacting with it. She starts her phishing proxy, which in this case is Evilginx, and retrieves a malicious link. She embeds the link in her email, addresses it to her target, and after one final look at the content, she sends it off.
Now, Clara will wait until the victim opens the email. Our victim, Stanley, is busy doing some payroll changes when he receives the malicious email from Clara. Stanley opens the email and briefly reads the content. The content sounds urgent, so he opens the embedded link.
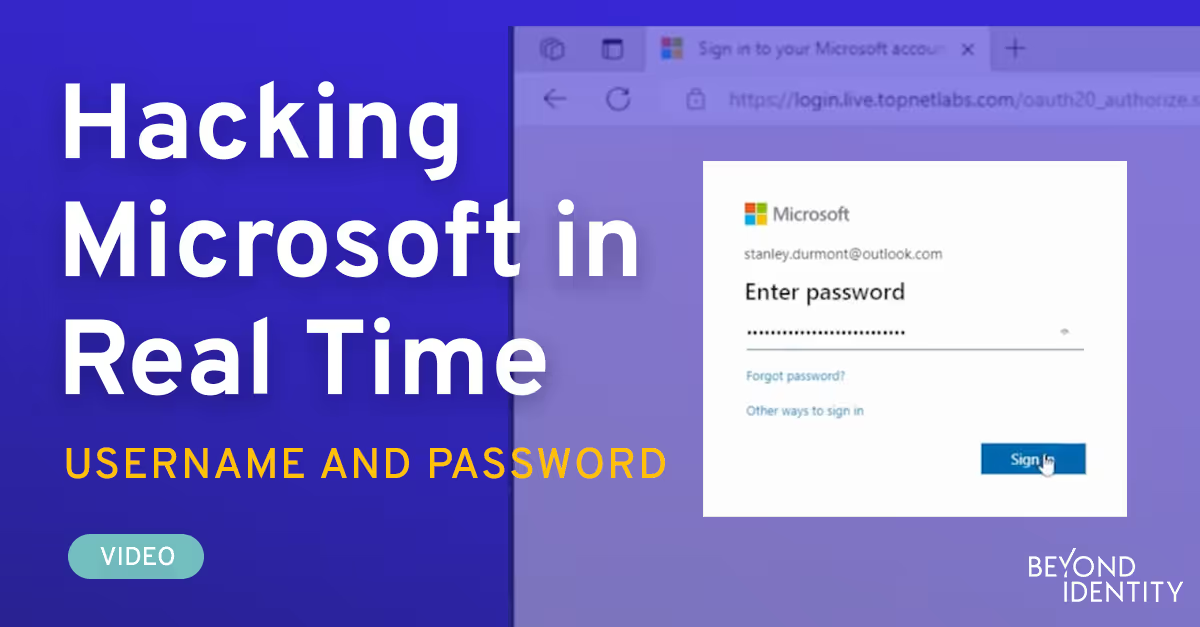
To Stanley, this page looks exactly like the Microsoft login page he is accustomed to. Being a security minded individual, Stanley saves his username and password on a sticky note on his desktop. He enters them into the portal and logs in. However, he finds no screenshots. As soon as Stanley opened the link, Clara began to see traffic in her phishing proxy. Clara waits for a while until she sees that Stanley submitted the form and completed the login process.
Once Clara sees that all authorization tokens have been intercepted interacts with the proxy in order to dump the session. The session not only captured Stanley's username and password, but it also copied the cookie that the server granted to Stanley's web browser. Clara takes this cookie and with the help of a Chrome extension, she executes a session takeover, gaining access to Stanley's account.
Now that Clara has a foothold in Stanley's account, She can act as Stanley, access his documents, and escalate her attack.
Transcript
Today, we are going to see a case study of what a phishing attack looks like using an open source transparent phishing proxy.
Our demo begins with our threat actor, Clara, preparing a phishing email. She uses a template she has found successful in the past, and customizes it for her victim. This template attempts to manipulate the victim into opening the link based on the premise of someone impersonating the victim on LinkedIn.
She knows the victim uses Microsoft Office 365, so she prepares a phishing link that looks like an Office Share link. Since she knows the victim will be less likely to be suspicious of interacting with it. She starts her phishing proxy, which in this case is Evilginx, and retrieves a malicious link. She embeds the link in her email, addresses it to her target, and after one final look at the content, she sends it off.
Now, Clara will wait until the victim opens the email. Our victim, Stanley, is busy doing some payroll changes when he receives the malicious email from Clara. Stanley opens the email and briefly reads the content. The content sounds urgent, so he opens the embedded link.
To Stanley, this page looks exactly like the Microsoft login page he is accustomed to. Being a security minded individual, Stanley saves his username and password on a sticky note on his desktop. He enters them into the portal and logs in. However, he finds no screenshots. As soon as Stanley opened the link, Clara began to see traffic in her phishing proxy. Clara waits for a while until she sees that Stanley submitted the form and completed the login process.
Once Clara sees that all authorization tokens have been intercepted interacts with the proxy in order to dump the session. The session not only captured Stanley's username and password, but it also copied the cookie that the server granted to Stanley's web browser. Clara takes this cookie and with the help of a Chrome extension, she executes a session takeover, gaining access to Stanley's account.
Now that Clara has a foothold in Stanley's account, She can act as Stanley, access his documents, and escalate her attack.
Transcript
Today, we are going to see a case study of what a phishing attack looks like using an open source transparent phishing proxy.
Our demo begins with our threat actor, Clara, preparing a phishing email. She uses a template she has found successful in the past, and customizes it for her victim. This template attempts to manipulate the victim into opening the link based on the premise of someone impersonating the victim on LinkedIn.
She knows the victim uses Microsoft Office 365, so she prepares a phishing link that looks like an Office Share link. Since she knows the victim will be less likely to be suspicious of interacting with it. She starts her phishing proxy, which in this case is Evilginx, and retrieves a malicious link. She embeds the link in her email, addresses it to her target, and after one final look at the content, she sends it off.
Now, Clara will wait until the victim opens the email. Our victim, Stanley, is busy doing some payroll changes when he receives the malicious email from Clara. Stanley opens the email and briefly reads the content. The content sounds urgent, so he opens the embedded link.
To Stanley, this page looks exactly like the Microsoft login page he is accustomed to. Being a security minded individual, Stanley saves his username and password on a sticky note on his desktop. He enters them into the portal and logs in. However, he finds no screenshots. As soon as Stanley opened the link, Clara began to see traffic in her phishing proxy. Clara waits for a while until she sees that Stanley submitted the form and completed the login process.
Once Clara sees that all authorization tokens have been intercepted interacts with the proxy in order to dump the session. The session not only captured Stanley's username and password, but it also copied the cookie that the server granted to Stanley's web browser. Clara takes this cookie and with the help of a Chrome extension, she executes a session takeover, gaining access to Stanley's account.
Now that Clara has a foothold in Stanley's account, She can act as Stanley, access his documents, and escalate her attack.






.png)






.avif)



.avif)






.avif)

