Announcing Beyond Identity + Splunk’s Partnership and Integration: Get Full Authentication Event Data For Risk-Modeling and Security Insights
Beyond Identity is announcing a new integration with Splunk to deliver granular authentication event data at the device level in real-time to power investigations and identify problematic and risky behaviors that introduce risk. Remote work, distance learning, and BYOD policies have complicated securing identities and access management. Beyond Identity’s integration with Splunk solves this issue seamlessly and causes no additional friction for your organization’s users. The integration pushes aggregated detail concerning the authentication event-including both identity and the security of the device, for delivery into Splunk for further analysis. In this blog post, we’ll review our new integration with Splunk, its benefits, and how you can integrate today.
Authentication data for faster threat detection
At Beyond Identity, we believe that customers own their authentication data and should be able to leverage it for valuable insight into the risks threatening their businesses, organizations, and institutions. We built this integration with Splunk to deliver on that belief and as a part of our commitment to securing every authentication event. The data and insights gathered and delivered to Splunk will inform security and threat intelligence teams of problematic behaviors or operational issues based on past attacks and in near-real-time, without the need for disparate data streams, reducing noise for analysts.
Beyond Identity enables more thorough investigation and faster response - leveraging immutable and granular authentication records based on strong cryptographically device-bound identities. We chose to integrate and partner with Splunk because they lead the market for analysis and monitoring in the IT and security markets. Their robust Security Information and Event Management (SIEM) tools offer complete visibility into activity across your network and power real-time threat response. Now, with Beyond Identity, Splunk users can further enhance Splunk’s market-leading technology with aggregated device-level authentication and device security data to:
- Investigate incidents and determine their potential severity and impact on a business or other operations.
- To report on these activities.
- To build models that can identify problematic behaviors before they impact business or operations or other operations.
Feed real-time risk signals from Beyond Identity into Splunk
The Beyond Identity + Splunk integration will help secure access by enforcing acceptable device security on every device attempting to access cloud resources for security analysts and system administrators. Together we improve investigations and reduce noise while also providing granular details of every authentication event backed by cryptographic standards. As a result, security teams can ensure only secured devices and authorized users access company data to block lateral movement and feed real-time risk signals into Splunk to help improve threat investigations.
Benefits:
A Granular Understanding of Threats
Beyond Identity pushes near real-time authentication data, including device security metadata, into customer’s SIEM to inform models and investigations.
Tighter Access Controls
Beyond Identity restricts access to organizational resources to only secured, authorized devices and users.
An End to Password-based Risk
Beyond Identity eliminates passwords and replaces them with cryptographically proved identities bound to primary devices like managed laptops.
Support Zero Trust Authentication
Beyond Identity uses continuous authentication and real-time device security posture data to prevent unauthorized and unsecured access and defend against lateral movement.
The Beyond Identity + Splunk integration delivers data that establishes identity provenance and a basis for device trust directly for analysis and modeling.
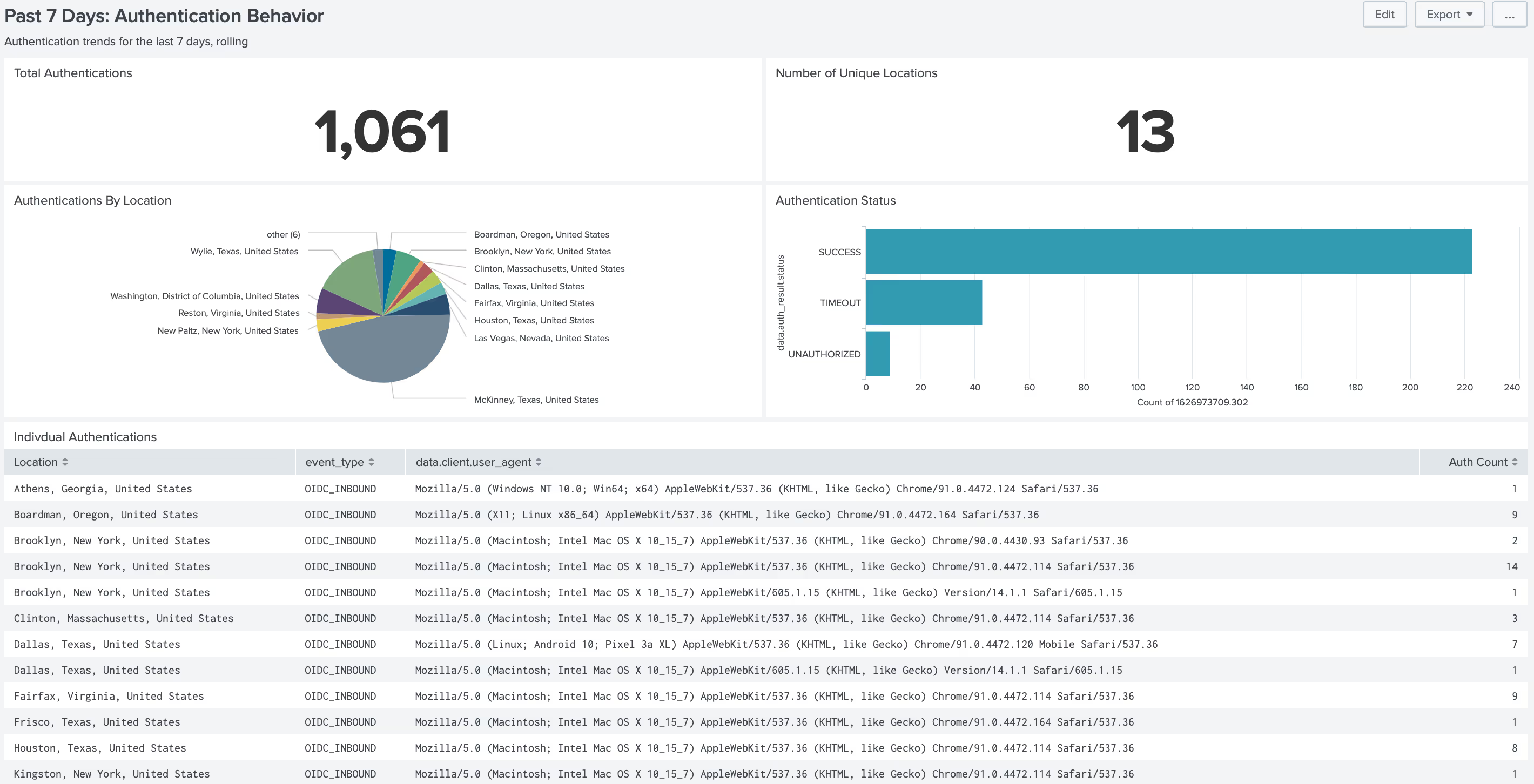
With Beyond Identity + Splunk’s Integration, You Can:
Provide Strong Passwordless MFA
Beyond Identity eliminates passwords as an authentication method and cryptographically binds user identity to the device via the secure TPM hardware on the accessing device. This stops password-based attacks across the applications you monitor with Splunk before allowing access to critical cloud resources.
Capture Granular Risk Signals and Immutable Logs
Beyond Identity captures granular device security posture data at the exact time of login, such as operating system version, security software state, and device type. Authentication event data is captured and aggregated in the Beyond Identity Administrative Console for every login attempt.
Identify Risky Users in Near Real-Time
Beyond Identity stops unauthorized users and rejects devices from authentication if they do not meet an organization’s security requirements. Unauthorized devices that are not bound to a valid identity are stopped from authenticating. All authentication data is fed into Splunk and normalized to inform threat defense.
Map Robust Authentication Event Data to SIEM
Beyond Identity injects data from every authentication attempt into Splunk’s Common Information Model to extract insights about the security posture of device-bound users, their authentication attempts, and the rejection of those who failed to satisfy device security requirements.
Get The Integration Today From The Splunk Marketplace
Implementing the Beyond Identity + Splunk integration is easy and fast. To get started, Splunk users just have to contact the Beyond Identity support team at support@beyondidentity.com to collect configuration details, including the needed API URL and API key.
In addition, user management requires no dedicated person-hours for password resets, complex configurations for authentication, or device registration. Instead, users no longer use passwords for access, authentication experiences are uniform across devices and applications, and device management is self-serve.
Ready to get more information on the risks threatening your systems?
Request a demo and see it in action
Beyond Identity is announcing a new integration with Splunk to deliver granular authentication event data at the device level in real-time to power investigations and identify problematic and risky behaviors that introduce risk. Remote work, distance learning, and BYOD policies have complicated securing identities and access management. Beyond Identity’s integration with Splunk solves this issue seamlessly and causes no additional friction for your organization’s users. The integration pushes aggregated detail concerning the authentication event-including both identity and the security of the device, for delivery into Splunk for further analysis. In this blog post, we’ll review our new integration with Splunk, its benefits, and how you can integrate today.
Authentication data for faster threat detection
At Beyond Identity, we believe that customers own their authentication data and should be able to leverage it for valuable insight into the risks threatening their businesses, organizations, and institutions. We built this integration with Splunk to deliver on that belief and as a part of our commitment to securing every authentication event. The data and insights gathered and delivered to Splunk will inform security and threat intelligence teams of problematic behaviors or operational issues based on past attacks and in near-real-time, without the need for disparate data streams, reducing noise for analysts.
Beyond Identity enables more thorough investigation and faster response - leveraging immutable and granular authentication records based on strong cryptographically device-bound identities. We chose to integrate and partner with Splunk because they lead the market for analysis and monitoring in the IT and security markets. Their robust Security Information and Event Management (SIEM) tools offer complete visibility into activity across your network and power real-time threat response. Now, with Beyond Identity, Splunk users can further enhance Splunk’s market-leading technology with aggregated device-level authentication and device security data to:
- Investigate incidents and determine their potential severity and impact on a business or other operations.
- To report on these activities.
- To build models that can identify problematic behaviors before they impact business or operations or other operations.
Feed real-time risk signals from Beyond Identity into Splunk
The Beyond Identity + Splunk integration will help secure access by enforcing acceptable device security on every device attempting to access cloud resources for security analysts and system administrators. Together we improve investigations and reduce noise while also providing granular details of every authentication event backed by cryptographic standards. As a result, security teams can ensure only secured devices and authorized users access company data to block lateral movement and feed real-time risk signals into Splunk to help improve threat investigations.
Benefits:
A Granular Understanding of Threats
Beyond Identity pushes near real-time authentication data, including device security metadata, into customer’s SIEM to inform models and investigations.
Tighter Access Controls
Beyond Identity restricts access to organizational resources to only secured, authorized devices and users.
An End to Password-based Risk
Beyond Identity eliminates passwords and replaces them with cryptographically proved identities bound to primary devices like managed laptops.
Support Zero Trust Authentication
Beyond Identity uses continuous authentication and real-time device security posture data to prevent unauthorized and unsecured access and defend against lateral movement.
The Beyond Identity + Splunk integration delivers data that establishes identity provenance and a basis for device trust directly for analysis and modeling.

With Beyond Identity + Splunk’s Integration, You Can:
Provide Strong Passwordless MFA
Beyond Identity eliminates passwords as an authentication method and cryptographically binds user identity to the device via the secure TPM hardware on the accessing device. This stops password-based attacks across the applications you monitor with Splunk before allowing access to critical cloud resources.
Capture Granular Risk Signals and Immutable Logs
Beyond Identity captures granular device security posture data at the exact time of login, such as operating system version, security software state, and device type. Authentication event data is captured and aggregated in the Beyond Identity Administrative Console for every login attempt.
Identify Risky Users in Near Real-Time
Beyond Identity stops unauthorized users and rejects devices from authentication if they do not meet an organization’s security requirements. Unauthorized devices that are not bound to a valid identity are stopped from authenticating. All authentication data is fed into Splunk and normalized to inform threat defense.
Map Robust Authentication Event Data to SIEM
Beyond Identity injects data from every authentication attempt into Splunk’s Common Information Model to extract insights about the security posture of device-bound users, their authentication attempts, and the rejection of those who failed to satisfy device security requirements.
Get The Integration Today From The Splunk Marketplace

Implementing the Beyond Identity + Splunk integration is easy and fast. To get started, Splunk users just have to contact the Beyond Identity support team at support@beyondidentity.com to collect configuration details, including the needed API URL and API key.
In addition, user management requires no dedicated person-hours for password resets, complex configurations for authentication, or device registration. Instead, users no longer use passwords for access, authentication experiences are uniform across devices and applications, and device management is self-serve.
Ready to get more information on the risks threatening your systems?
Request a demo and see it in action
Beyond Identity is announcing a new integration with Splunk to deliver granular authentication event data at the device level in real-time to power investigations and identify problematic and risky behaviors that introduce risk. Remote work, distance learning, and BYOD policies have complicated securing identities and access management. Beyond Identity’s integration with Splunk solves this issue seamlessly and causes no additional friction for your organization’s users. The integration pushes aggregated detail concerning the authentication event-including both identity and the security of the device, for delivery into Splunk for further analysis. In this blog post, we’ll review our new integration with Splunk, its benefits, and how you can integrate today.
Authentication data for faster threat detection
At Beyond Identity, we believe that customers own their authentication data and should be able to leverage it for valuable insight into the risks threatening their businesses, organizations, and institutions. We built this integration with Splunk to deliver on that belief and as a part of our commitment to securing every authentication event. The data and insights gathered and delivered to Splunk will inform security and threat intelligence teams of problematic behaviors or operational issues based on past attacks and in near-real-time, without the need for disparate data streams, reducing noise for analysts.
Beyond Identity enables more thorough investigation and faster response - leveraging immutable and granular authentication records based on strong cryptographically device-bound identities. We chose to integrate and partner with Splunk because they lead the market for analysis and monitoring in the IT and security markets. Their robust Security Information and Event Management (SIEM) tools offer complete visibility into activity across your network and power real-time threat response. Now, with Beyond Identity, Splunk users can further enhance Splunk’s market-leading technology with aggregated device-level authentication and device security data to:
- Investigate incidents and determine their potential severity and impact on a business or other operations.
- To report on these activities.
- To build models that can identify problematic behaviors before they impact business or operations or other operations.
Feed real-time risk signals from Beyond Identity into Splunk
The Beyond Identity + Splunk integration will help secure access by enforcing acceptable device security on every device attempting to access cloud resources for security analysts and system administrators. Together we improve investigations and reduce noise while also providing granular details of every authentication event backed by cryptographic standards. As a result, security teams can ensure only secured devices and authorized users access company data to block lateral movement and feed real-time risk signals into Splunk to help improve threat investigations.
Benefits:
A Granular Understanding of Threats
Beyond Identity pushes near real-time authentication data, including device security metadata, into customer’s SIEM to inform models and investigations.
Tighter Access Controls
Beyond Identity restricts access to organizational resources to only secured, authorized devices and users.
An End to Password-based Risk
Beyond Identity eliminates passwords and replaces them with cryptographically proved identities bound to primary devices like managed laptops.
Support Zero Trust Authentication
Beyond Identity uses continuous authentication and real-time device security posture data to prevent unauthorized and unsecured access and defend against lateral movement.
The Beyond Identity + Splunk integration delivers data that establishes identity provenance and a basis for device trust directly for analysis and modeling.

With Beyond Identity + Splunk’s Integration, You Can:
Provide Strong Passwordless MFA
Beyond Identity eliminates passwords as an authentication method and cryptographically binds user identity to the device via the secure TPM hardware on the accessing device. This stops password-based attacks across the applications you monitor with Splunk before allowing access to critical cloud resources.
Capture Granular Risk Signals and Immutable Logs
Beyond Identity captures granular device security posture data at the exact time of login, such as operating system version, security software state, and device type. Authentication event data is captured and aggregated in the Beyond Identity Administrative Console for every login attempt.
Identify Risky Users in Near Real-Time
Beyond Identity stops unauthorized users and rejects devices from authentication if they do not meet an organization’s security requirements. Unauthorized devices that are not bound to a valid identity are stopped from authenticating. All authentication data is fed into Splunk and normalized to inform threat defense.
Map Robust Authentication Event Data to SIEM
Beyond Identity injects data from every authentication attempt into Splunk’s Common Information Model to extract insights about the security posture of device-bound users, their authentication attempts, and the rejection of those who failed to satisfy device security requirements.
Get The Integration Today From The Splunk Marketplace

Implementing the Beyond Identity + Splunk integration is easy and fast. To get started, Splunk users just have to contact the Beyond Identity support team at support@beyondidentity.com to collect configuration details, including the needed API URL and API key.
In addition, user management requires no dedicated person-hours for password resets, complex configurations for authentication, or device registration. Instead, users no longer use passwords for access, authentication experiences are uniform across devices and applications, and device management is self-serve.
Ready to get more information on the risks threatening your systems?







.png)






.avif)



.avif)






.avif)

