About The Bridge to Zero Trust Virtual Event
On March 15, 2023, The Bridge to Zero Trust Virtual Event gathered top industry leaders and cybersecurity specialists for a discussion about the future of cybersecurity, the role of zero trust architectures in that future, and how authentication plays a critical role.
The live event may be over, but you can still watch every session.
This is your opportunity to hear from industry experts and leaders who share practical insights and tips on how to implement the foundation for zero trust security.
Who will I hear from?
You’ll hear from leaders and security specialists from BeyondTrust, CrowdStrike, CDW, FIDO, Ping, Palo Alto, World Wide Technology, and more, including:
- Megan Shamas, FIDO Alliance
- Chase Cunningham, Dr. Zero Trust
- Aubrey Turner, Ping Identity
- Doug Good, Palo Alto Networks
- Chris Kachigian, CrowdStrike
- Kevin Dana, WWT
- Marcos Christodonte II, CDW
- David Manks, BeyondTrust
What will I learn?
Sessions included:
- Using Zero Trust Principles to Unleash Proactive Security
- Authentication Meets Zero Trust
- FIDO Alliance: The Road Ahead for Authentication
- Leadership Panel: Authentication Meets the Zero Trust Ecosystem
- From Concept to Practice: Architecting and Accelerating Your Zero Trust Objectives
- Security Within Reach: Practical Steps to Get on the Road to Zero Trust
- One Mission: Zero Trust Authentication that Fortifies IT and Inspires Users
- Optiv Zero Trust Assessment Best Practices
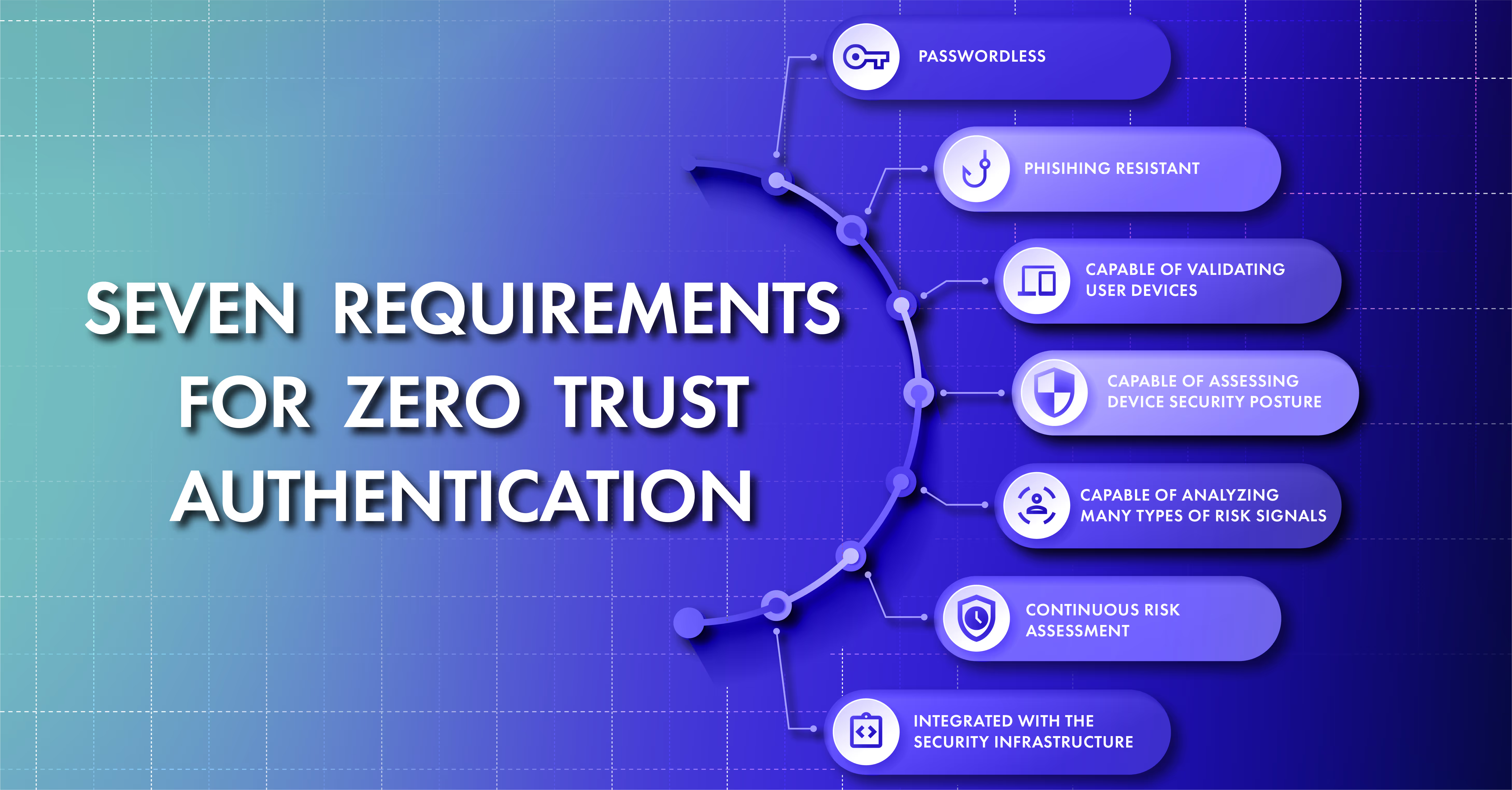
Our central topic for the event is the importance of authentication in the zero trust ecosystem and the seven requirements for Zero Trust Authentication.
You can watch a replay of the event today.
Want to read more about Zero Trust Authentication?
Check out these resources:
- The Rise of Zero Trust Authentication - white paper that discusses how phishing-resistant, passwordless authentication advances zero trust security
- Zero Trust Authentication: Securing User and Device Access for a Distributed, Multi-Cloud World - ebook written by Jon Friedman of AimPoint Group that describes:
- The role of authentication in zero trust security
- The fatal shortcomings in existing authentication
- Technologies that can provide passwordless, phishing-resistant MFA
- Low-friction authentication that simplifies deployment and ensures user acceptance
- How Zero Trust Authentication integrates with security tools and strengthens your overall security program
- How you can deploy Zero Trust Authentication fast and generate quick wins
On March 15, 2023, The Bridge to Zero Trust Virtual Event gathered top industry leaders and cybersecurity specialists for a discussion about the future of cybersecurity, the role of zero trust architectures in that future, and how authentication plays a critical role.
The live event may be over, but you can still watch every session.
This is your opportunity to hear from industry experts and leaders who share practical insights and tips on how to implement the foundation for zero trust security.
Who will I hear from?
You’ll hear from leaders and security specialists from BeyondTrust, CrowdStrike, CDW, FIDO, Ping, Palo Alto, World Wide Technology, and more, including:
- Megan Shamas, FIDO Alliance
- Chase Cunningham, Dr. Zero Trust
- Aubrey Turner, Ping Identity
- Doug Good, Palo Alto Networks
- Chris Kachigian, CrowdStrike
- Kevin Dana, WWT
- Marcos Christodonte II, CDW
- David Manks, BeyondTrust
What will I learn?
Sessions included:
- Using Zero Trust Principles to Unleash Proactive Security
- Authentication Meets Zero Trust
- FIDO Alliance: The Road Ahead for Authentication
- Leadership Panel: Authentication Meets the Zero Trust Ecosystem
- From Concept to Practice: Architecting and Accelerating Your Zero Trust Objectives
- Security Within Reach: Practical Steps to Get on the Road to Zero Trust
- One Mission: Zero Trust Authentication that Fortifies IT and Inspires Users
- Optiv Zero Trust Assessment Best Practices
Our central topic for the event is the importance of authentication in the zero trust ecosystem and the seven requirements for Zero Trust Authentication.

You can watch a replay of the event today.
Want to read more about Zero Trust Authentication?
Check out these resources:
- The Rise of Zero Trust Authentication - white paper that discusses how phishing-resistant, passwordless authentication advances zero trust security
- Zero Trust Authentication: Securing User and Device Access for a Distributed, Multi-Cloud World - ebook written by Jon Friedman of AimPoint Group that describes:
- The role of authentication in zero trust security
- The fatal shortcomings in existing authentication
- Technologies that can provide passwordless, phishing-resistant MFA
- Low-friction authentication that simplifies deployment and ensures user acceptance
- How Zero Trust Authentication integrates with security tools and strengthens your overall security program
- How you can deploy Zero Trust Authentication fast and generate quick wins
On March 15, 2023, The Bridge to Zero Trust Virtual Event gathered top industry leaders and cybersecurity specialists for a discussion about the future of cybersecurity, the role of zero trust architectures in that future, and how authentication plays a critical role.
The live event may be over, but you can still watch every session.
This is your opportunity to hear from industry experts and leaders who share practical insights and tips on how to implement the foundation for zero trust security.
Who will I hear from?
You’ll hear from leaders and security specialists from BeyondTrust, CrowdStrike, CDW, FIDO, Ping, Palo Alto, World Wide Technology, and more, including:
- Megan Shamas, FIDO Alliance
- Chase Cunningham, Dr. Zero Trust
- Aubrey Turner, Ping Identity
- Doug Good, Palo Alto Networks
- Chris Kachigian, CrowdStrike
- Kevin Dana, WWT
- Marcos Christodonte II, CDW
- David Manks, BeyondTrust
What will I learn?
Sessions included:
- Using Zero Trust Principles to Unleash Proactive Security
- Authentication Meets Zero Trust
- FIDO Alliance: The Road Ahead for Authentication
- Leadership Panel: Authentication Meets the Zero Trust Ecosystem
- From Concept to Practice: Architecting and Accelerating Your Zero Trust Objectives
- Security Within Reach: Practical Steps to Get on the Road to Zero Trust
- One Mission: Zero Trust Authentication that Fortifies IT and Inspires Users
- Optiv Zero Trust Assessment Best Practices
Our central topic for the event is the importance of authentication in the zero trust ecosystem and the seven requirements for Zero Trust Authentication.

You can watch a replay of the event today.
Want to read more about Zero Trust Authentication?
Check out these resources:
- The Rise of Zero Trust Authentication - white paper that discusses how phishing-resistant, passwordless authentication advances zero trust security
- Zero Trust Authentication: Securing User and Device Access for a Distributed, Multi-Cloud World - ebook written by Jon Friedman of AimPoint Group that describes:
- The role of authentication in zero trust security
- The fatal shortcomings in existing authentication
- Technologies that can provide passwordless, phishing-resistant MFA
- Low-friction authentication that simplifies deployment and ensures user acceptance
- How Zero Trust Authentication integrates with security tools and strengthens your overall security program
- How you can deploy Zero Trust Authentication fast and generate quick wins













.avif)
.avif)



.avif)






.avif)

