Companies’ Cybersecurity Concerns With Gig Economy
Key takeaways
- 87% of contractors still have access to previous clients’ accounts which contain sensitive data.
- Only 62% of contractors say companies informed them of security protocols to follow during the onboarding process.
- 73% of managers say their company has forgotten to change an internal password once a gig worker left the company.
Gig Economy Puts Companies’ Cybersecurity at Risk
In today’s highly connected world, an increasing number of businesses and workers are opting for the gig model. More and more companies prefer hiring short-term workers and contractors instead of full-time employees—as a result, the gig economy is growing. In 2021, 59 million Americans freelanced, representing more than one-third of the entire U.S. workforce.
The gig economy provides numerous upsides for independent contractors. But gig workers can pose serious cybersecurity risks for the company by remotely accessing sensitive corporate data on their own devices. Learning the risks is crucial to building solid security protocols and taking proactive measures.
We recently studied how businesses are navigating cybersecurity challenges like these. To find out what security protocols they follow before, during, and after freelance gigs, we surveyed 1,196 managers and contractors about the current state of cybersecurity risks in the gig economy. Warning: The following cybersecurity data may be disturbing to some business owners.
Sensitive data is only a click away
Our research shows that contractors hired for a short gig may have lifetime access to companies’ most sensitive data and accounts. We also found that workers who require remote access to corporate data to do their work don’t often follow their clients’ security regulations.
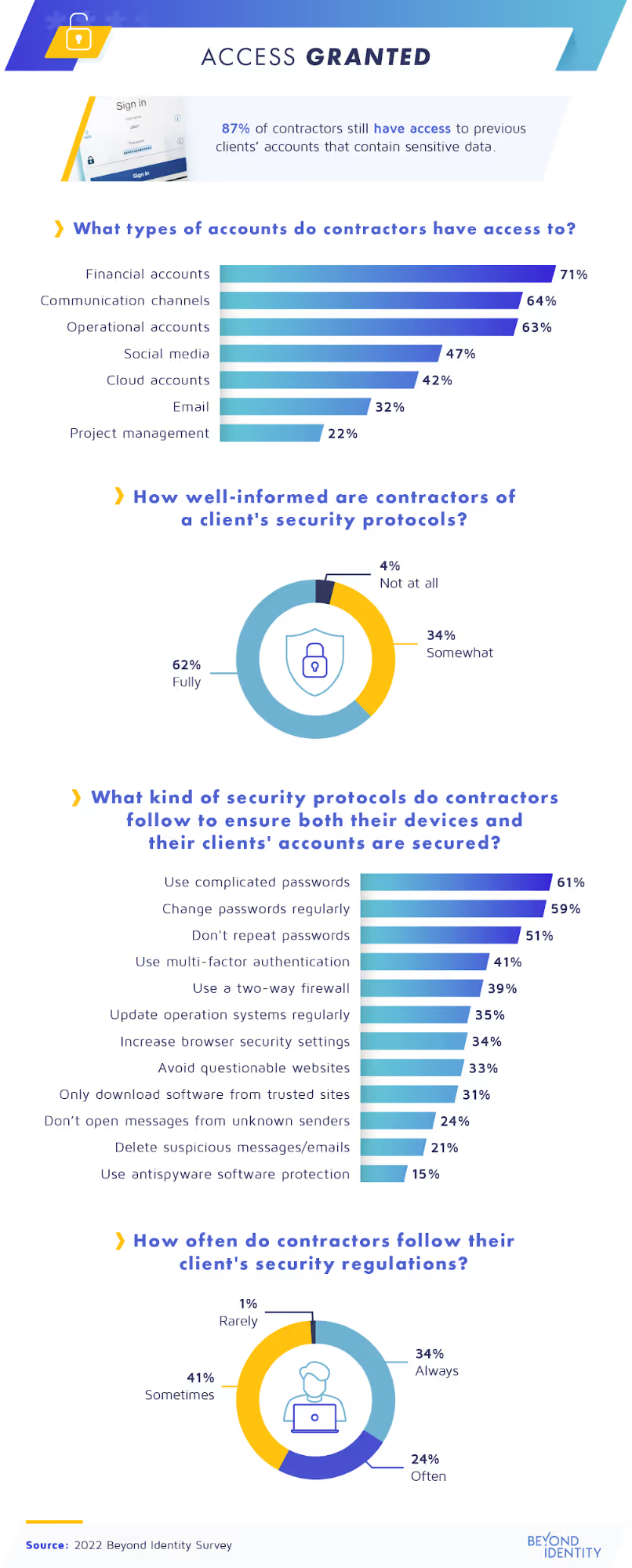
When companies sign a short-term contract with a contractor, they agree to temporarily share their accounts, which often contain sensitive data. For many, the trick is remembering to disconnect them when the job ends. But we found that 87% of contractors still have access to previous clients’ accounts.
What they can still access varies, but often, it includes financial, communication, and operational accounts. This access may allow some of the most serious personal and corporate data breaches, social media hacks, and even phishing activities.
In addition, contractors must follow security protocols to protect their devices and their clients’ accounts while working with a company. Our survey results showed 62% of companies requested that contractors follow security protocols during the onboarding process. To comply, most gig workers we surveyed said they use complicated passwords, which they change regularly. Using multi-factor authentication and a two-way firewall were also among the top security measures contractors take as a precaution against cyberattacks; however, less than 50% of respondents said they use these protections.
Are these actions enough to stop cybercriminals and ensure a secure workflow? Possibly, if all contractors follow their clients’ security regulations all the time. However, only slightly more than one-third of contractors said they ‘‘always’’ do this. About one-quarter said they follow the regulations “often,” while 41% said they only do it ‘‘sometimes.”
Following protocol?
Failure to follow security protocols can have severe consequences for both companies and contractors. There are an estimated 2,200 cyberattacks daily, meaning more than 800,000 people get hacked each year. One of the top causes is human error, with approximately 88% of all data hacks happening due to an employee’s (or contractor’s) mistake.
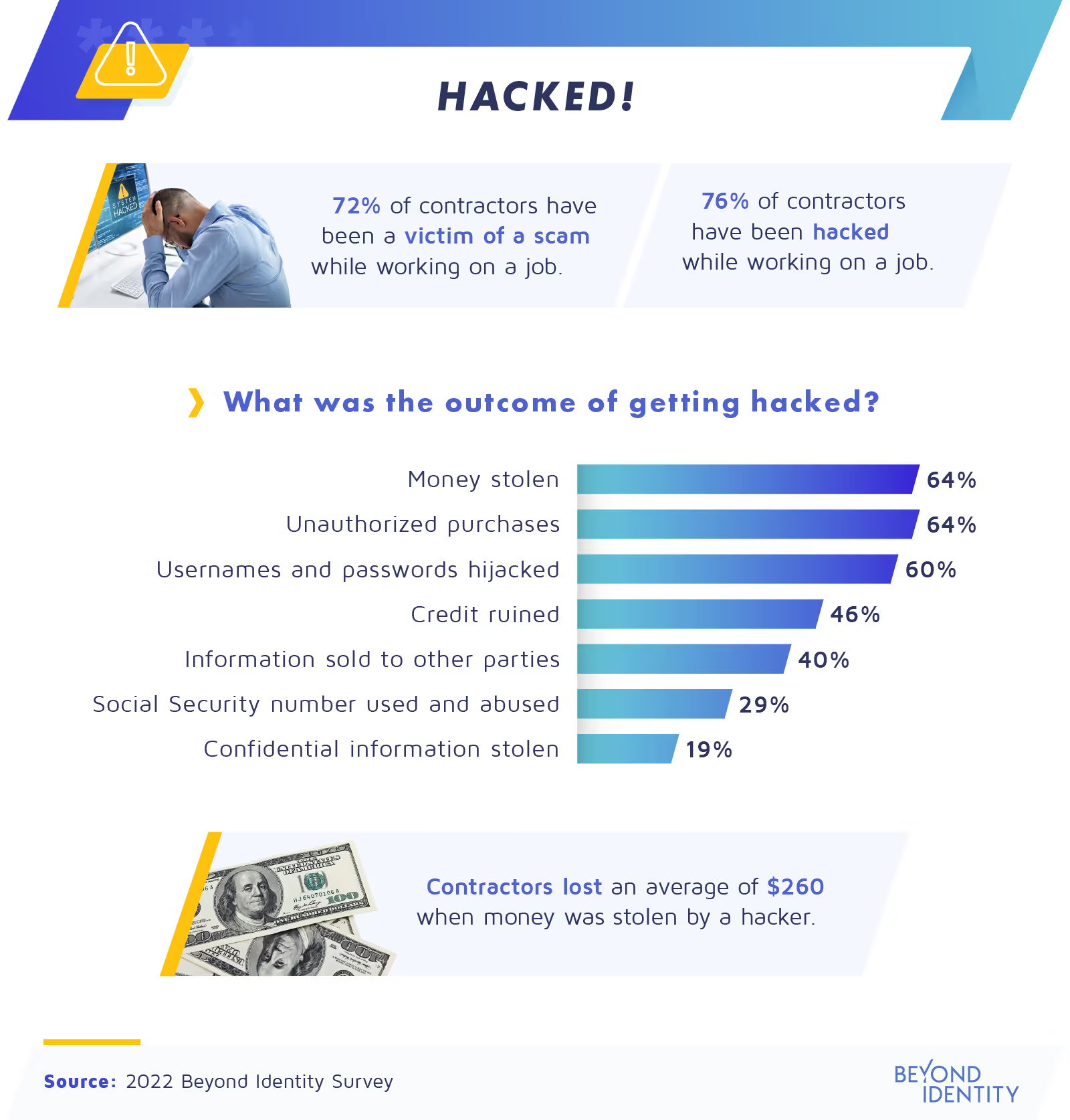
Unfortunately, we found that 76% of contractors have been hacked while working on a gig for a company. As a result, 64% of gig workers have had an average of $260 stolen from them, often in the form of unauthorized purchases due to account breaches.
Theft of confidential and personal information is one of the most disturbing consequences of getting hacked. According to our research, 60% of contractors’ usernames and passwords have been hijacked, giving an entry point to sensitive data and confidential information. Many other contractors (40%) had their information sold to other parties, while 29% of short-term workers said their Social Security numbers were used and abused by hackers.
The importance of training
As we mentioned above, hacking incidents are often caused by employees’ mistakes, so those who work directly with gig workers play a key role in a company’s cybersecurity. Next, we’ll learn more about companies’ training procedures and how they might impact their safety.
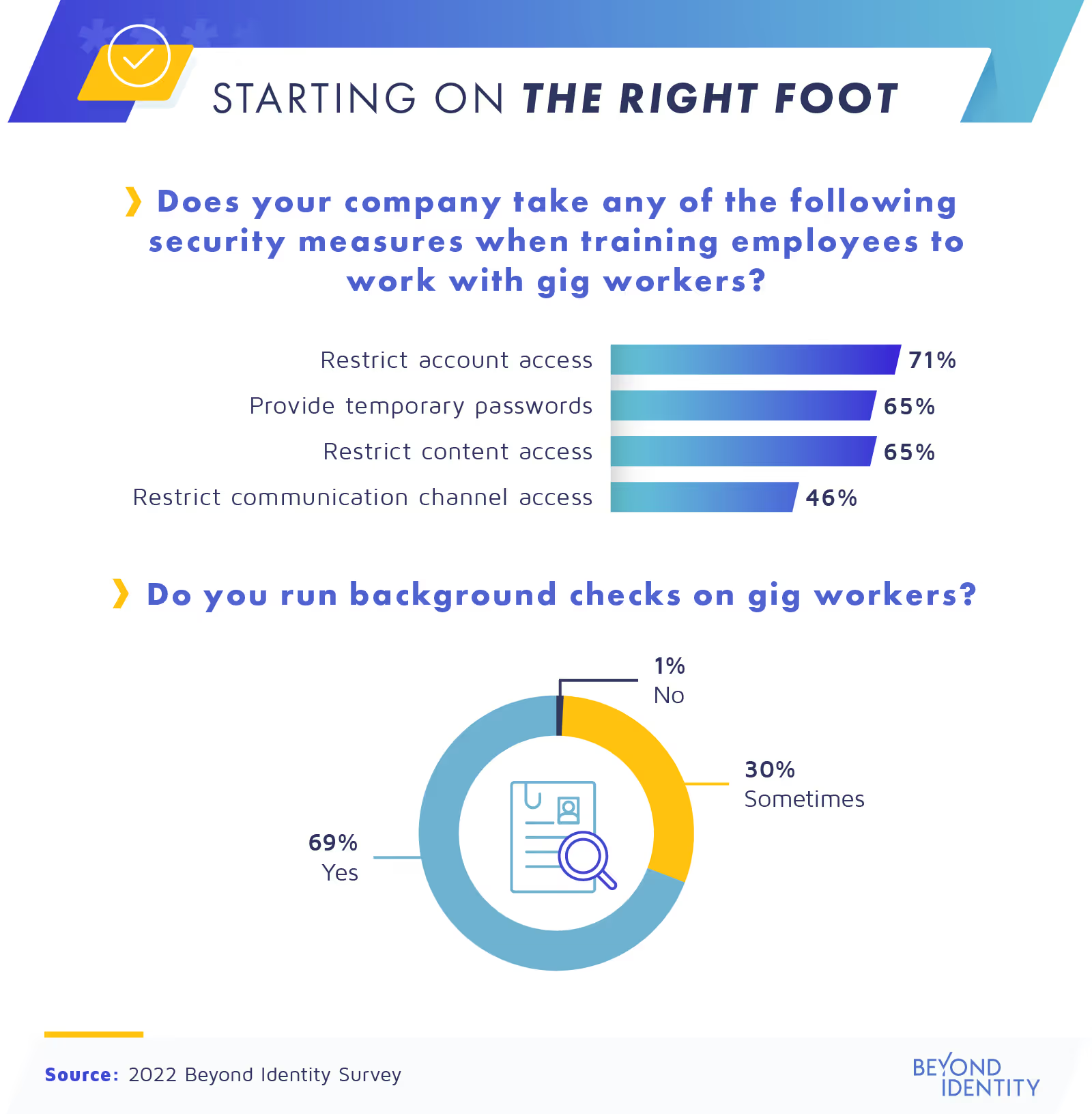
Cybercriminals’ techniques are constantly evolving in today’s fast-paced digital society. Prevention works best with effective protocols in place, which both employees and contractors need to be trained to follow. For many companies, this includes training employees to work with contractors safely.
This might include restricting contractors’ access to company accounts—a method reportedly used by 71% of business managers. Others (65%) have provided gig workers with temporary passwords. The same percentage also restricted their access to certain content.
It also helps to make sure you’re onboarding the right contractors in the first place, which is why 69% of companies have run background checks on their gig workers. That leaves 31% of businesses that didn’t, running the risk of hiring someone who might have cybercriminal activity on their record.
Work interruptions
Most companies focus on cybersecurity protocols before and during the gig work. However, the ones taken after the gig is over are just as vital for cybersecurity, if not more so.
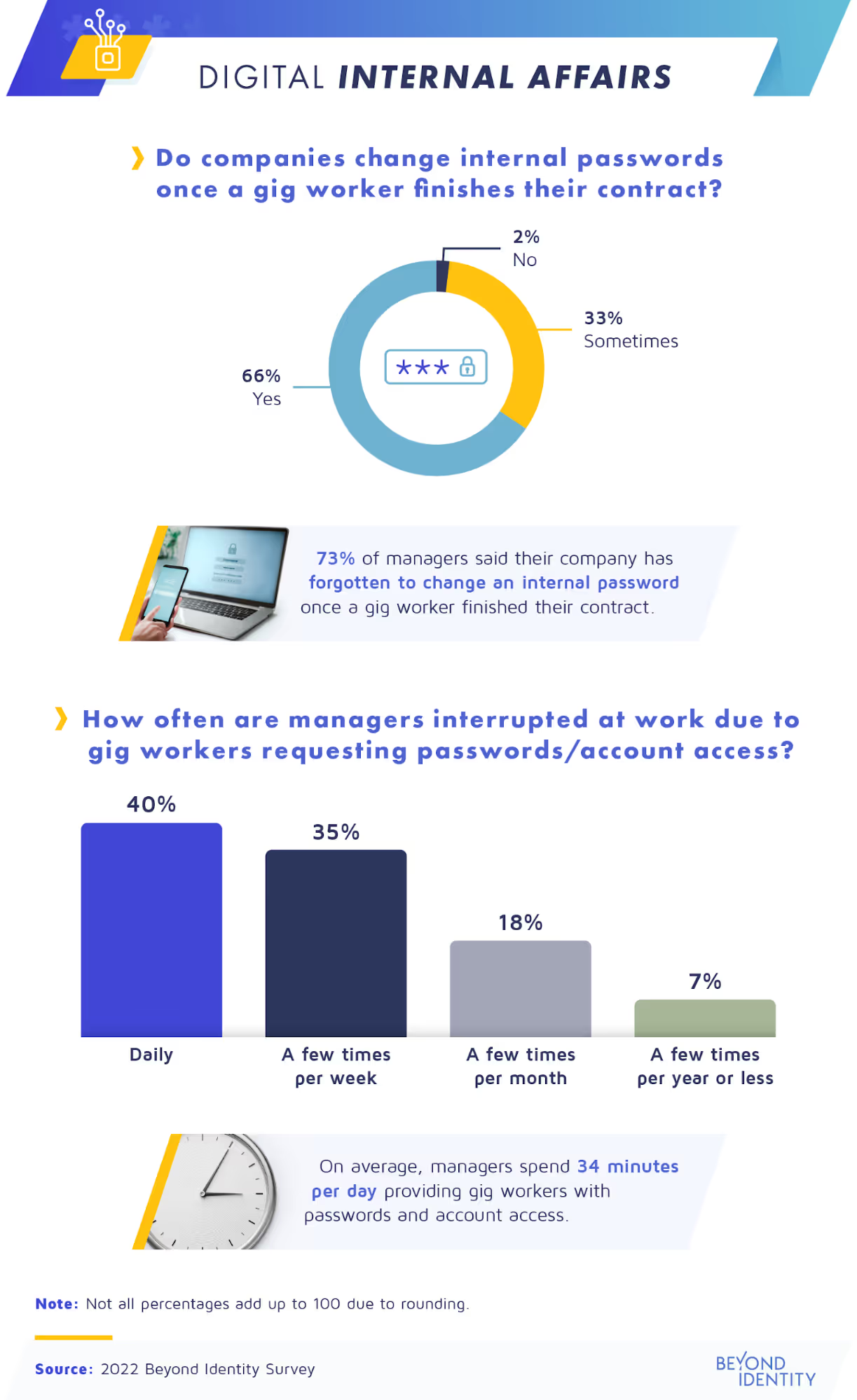
Many business managers’ valuable time is mostly dedicated to their own tasks and those of their full-time employees. That’s why companies often need contractors to be self-starters and make decisions alone without taking up too much of a manager’s time. But while giving important passwords and account access to gig workers can save time, it’s not a safe solution.
According to our survey, 40% of managers are interrupted daily at work due to gig workers requesting passwords or account access, and 35% are interrupted a few times per week. On average, managers spend 34 minutes daily on these tasks. So, it’s easy to see how one might occasionally forget to change these passwords and permissions later.
However, these oversights can lead to leaked data. As a recent example, the Target-owned platform, Shipt was compromised by hackers who obtained gig workers’ emails and passwords. Despite the risk, while 66% said their company’s policy is to change a password after a gig worker finishes a job, this has often fallen through the cracks. We found that 73% of managers have forgotten to do this at the end of a gig.
Keeping companies secure
Fueled by the COVID-19 pandemic, remote work and the gig economy have undoubtedly brought dynamic growth to companies. While hiring gig workers has advantages for companies, it can also create cybersecurity threats.
While providing temporary passwords and restricting access may seem like a solution, forgetting to change these logins and permissions later puts businesses at risk. And without the proper protocols, gig workers are also open to cyberattacks while on the job.
In a digital world where hackers attack constantly, can your company’s cybersecurity training keep up? How will the future of gig work shape these practices? It might be time to level them up to ensure companies’ data remains safe.
Methodology
Beyond Identity surveyed 1,196 managers and contractors about cyber security and the gig economy. Among them, 58% were contractors, and 42% were managers who had hired a contractor on behalf of their company.
About Beyond Identity
Beyond Identity provides passwordless solutions to help secure digital business. Our cloud-native solutions also increase customers’ business velocity, and reduce their operating costs.
Fair use statement
This study is available to share only for noncommercial purposes as long as you link back to this original page.
Key takeaways
- 87% of contractors still have access to previous clients’ accounts which contain sensitive data.
- Only 62% of contractors say companies informed them of security protocols to follow during the onboarding process.
- 73% of managers say their company has forgotten to change an internal password once a gig worker left the company.
Gig Economy Puts Companies’ Cybersecurity at Risk
In today’s highly connected world, an increasing number of businesses and workers are opting for the gig model. More and more companies prefer hiring short-term workers and contractors instead of full-time employees—as a result, the gig economy is growing. In 2021, 59 million Americans freelanced, representing more than one-third of the entire U.S. workforce.
The gig economy provides numerous upsides for independent contractors. But gig workers can pose serious cybersecurity risks for the company by remotely accessing sensitive corporate data on their own devices. Learning the risks is crucial to building solid security protocols and taking proactive measures.
We recently studied how businesses are navigating cybersecurity challenges like these. To find out what security protocols they follow before, during, and after freelance gigs, we surveyed 1,196 managers and contractors about the current state of cybersecurity risks in the gig economy. Warning: The following cybersecurity data may be disturbing to some business owners.
Sensitive data is only a click away
Our research shows that contractors hired for a short gig may have lifetime access to companies’ most sensitive data and accounts. We also found that workers who require remote access to corporate data to do their work don’t often follow their clients’ security regulations.

When companies sign a short-term contract with a contractor, they agree to temporarily share their accounts, which often contain sensitive data. For many, the trick is remembering to disconnect them when the job ends. But we found that 87% of contractors still have access to previous clients’ accounts.
What they can still access varies, but often, it includes financial, communication, and operational accounts. This access may allow some of the most serious personal and corporate data breaches, social media hacks, and even phishing activities.
In addition, contractors must follow security protocols to protect their devices and their clients’ accounts while working with a company. Our survey results showed 62% of companies requested that contractors follow security protocols during the onboarding process. To comply, most gig workers we surveyed said they use complicated passwords, which they change regularly. Using multi-factor authentication and a two-way firewall were also among the top security measures contractors take as a precaution against cyberattacks; however, less than 50% of respondents said they use these protections.
Are these actions enough to stop cybercriminals and ensure a secure workflow? Possibly, if all contractors follow their clients’ security regulations all the time. However, only slightly more than one-third of contractors said they ‘‘always’’ do this. About one-quarter said they follow the regulations “often,” while 41% said they only do it ‘‘sometimes.”
Following protocol?
Failure to follow security protocols can have severe consequences for both companies and contractors. There are an estimated 2,200 cyberattacks daily, meaning more than 800,000 people get hacked each year. One of the top causes is human error, with approximately 88% of all data hacks happening due to an employee’s (or contractor’s) mistake.

Unfortunately, we found that 76% of contractors have been hacked while working on a gig for a company. As a result, 64% of gig workers have had an average of $260 stolen from them, often in the form of unauthorized purchases due to account breaches.
Theft of confidential and personal information is one of the most disturbing consequences of getting hacked. According to our research, 60% of contractors’ usernames and passwords have been hijacked, giving an entry point to sensitive data and confidential information. Many other contractors (40%) had their information sold to other parties, while 29% of short-term workers said their Social Security numbers were used and abused by hackers.
The importance of training
As we mentioned above, hacking incidents are often caused by employees’ mistakes, so those who work directly with gig workers play a key role in a company’s cybersecurity. Next, we’ll learn more about companies’ training procedures and how they might impact their safety.

Cybercriminals’ techniques are constantly evolving in today’s fast-paced digital society. Prevention works best with effective protocols in place, which both employees and contractors need to be trained to follow. For many companies, this includes training employees to work with contractors safely.
This might include restricting contractors’ access to company accounts—a method reportedly used by 71% of business managers. Others (65%) have provided gig workers with temporary passwords. The same percentage also restricted their access to certain content.
It also helps to make sure you’re onboarding the right contractors in the first place, which is why 69% of companies have run background checks on their gig workers. That leaves 31% of businesses that didn’t, running the risk of hiring someone who might have cybercriminal activity on their record.
Work interruptions
Most companies focus on cybersecurity protocols before and during the gig work. However, the ones taken after the gig is over are just as vital for cybersecurity, if not more so.

Many business managers’ valuable time is mostly dedicated to their own tasks and those of their full-time employees. That’s why companies often need contractors to be self-starters and make decisions alone without taking up too much of a manager’s time. But while giving important passwords and account access to gig workers can save time, it’s not a safe solution.
According to our survey, 40% of managers are interrupted daily at work due to gig workers requesting passwords or account access, and 35% are interrupted a few times per week. On average, managers spend 34 minutes daily on these tasks. So, it’s easy to see how one might occasionally forget to change these passwords and permissions later.
However, these oversights can lead to leaked data. As a recent example, the Target-owned platform, Shipt was compromised by hackers who obtained gig workers’ emails and passwords. Despite the risk, while 66% said their company’s policy is to change a password after a gig worker finishes a job, this has often fallen through the cracks. We found that 73% of managers have forgotten to do this at the end of a gig.
Keeping companies secure
Fueled by the COVID-19 pandemic, remote work and the gig economy have undoubtedly brought dynamic growth to companies. While hiring gig workers has advantages for companies, it can also create cybersecurity threats.
While providing temporary passwords and restricting access may seem like a solution, forgetting to change these logins and permissions later puts businesses at risk. And without the proper protocols, gig workers are also open to cyberattacks while on the job.
In a digital world where hackers attack constantly, can your company’s cybersecurity training keep up? How will the future of gig work shape these practices? It might be time to level them up to ensure companies’ data remains safe.
Methodology
Beyond Identity surveyed 1,196 managers and contractors about cyber security and the gig economy. Among them, 58% were contractors, and 42% were managers who had hired a contractor on behalf of their company.
About Beyond Identity
Beyond Identity provides passwordless solutions to help secure digital business. Our cloud-native solutions also increase customers’ business velocity, and reduce their operating costs.
Fair use statement
This study is available to share only for noncommercial purposes as long as you link back to this original page.
Key takeaways
- 87% of contractors still have access to previous clients’ accounts which contain sensitive data.
- Only 62% of contractors say companies informed them of security protocols to follow during the onboarding process.
- 73% of managers say their company has forgotten to change an internal password once a gig worker left the company.
Gig Economy Puts Companies’ Cybersecurity at Risk
In today’s highly connected world, an increasing number of businesses and workers are opting for the gig model. More and more companies prefer hiring short-term workers and contractors instead of full-time employees—as a result, the gig economy is growing. In 2021, 59 million Americans freelanced, representing more than one-third of the entire U.S. workforce.
The gig economy provides numerous upsides for independent contractors. But gig workers can pose serious cybersecurity risks for the company by remotely accessing sensitive corporate data on their own devices. Learning the risks is crucial to building solid security protocols and taking proactive measures.
We recently studied how businesses are navigating cybersecurity challenges like these. To find out what security protocols they follow before, during, and after freelance gigs, we surveyed 1,196 managers and contractors about the current state of cybersecurity risks in the gig economy. Warning: The following cybersecurity data may be disturbing to some business owners.
Sensitive data is only a click away
Our research shows that contractors hired for a short gig may have lifetime access to companies’ most sensitive data and accounts. We also found that workers who require remote access to corporate data to do their work don’t often follow their clients’ security regulations.

When companies sign a short-term contract with a contractor, they agree to temporarily share their accounts, which often contain sensitive data. For many, the trick is remembering to disconnect them when the job ends. But we found that 87% of contractors still have access to previous clients’ accounts.
What they can still access varies, but often, it includes financial, communication, and operational accounts. This access may allow some of the most serious personal and corporate data breaches, social media hacks, and even phishing activities.
In addition, contractors must follow security protocols to protect their devices and their clients’ accounts while working with a company. Our survey results showed 62% of companies requested that contractors follow security protocols during the onboarding process. To comply, most gig workers we surveyed said they use complicated passwords, which they change regularly. Using multi-factor authentication and a two-way firewall were also among the top security measures contractors take as a precaution against cyberattacks; however, less than 50% of respondents said they use these protections.
Are these actions enough to stop cybercriminals and ensure a secure workflow? Possibly, if all contractors follow their clients’ security regulations all the time. However, only slightly more than one-third of contractors said they ‘‘always’’ do this. About one-quarter said they follow the regulations “often,” while 41% said they only do it ‘‘sometimes.”
Following protocol?
Failure to follow security protocols can have severe consequences for both companies and contractors. There are an estimated 2,200 cyberattacks daily, meaning more than 800,000 people get hacked each year. One of the top causes is human error, with approximately 88% of all data hacks happening due to an employee’s (or contractor’s) mistake.

Unfortunately, we found that 76% of contractors have been hacked while working on a gig for a company. As a result, 64% of gig workers have had an average of $260 stolen from them, often in the form of unauthorized purchases due to account breaches.
Theft of confidential and personal information is one of the most disturbing consequences of getting hacked. According to our research, 60% of contractors’ usernames and passwords have been hijacked, giving an entry point to sensitive data and confidential information. Many other contractors (40%) had their information sold to other parties, while 29% of short-term workers said their Social Security numbers were used and abused by hackers.
The importance of training
As we mentioned above, hacking incidents are often caused by employees’ mistakes, so those who work directly with gig workers play a key role in a company’s cybersecurity. Next, we’ll learn more about companies’ training procedures and how they might impact their safety.

Cybercriminals’ techniques are constantly evolving in today’s fast-paced digital society. Prevention works best with effective protocols in place, which both employees and contractors need to be trained to follow. For many companies, this includes training employees to work with contractors safely.
This might include restricting contractors’ access to company accounts—a method reportedly used by 71% of business managers. Others (65%) have provided gig workers with temporary passwords. The same percentage also restricted their access to certain content.
It also helps to make sure you’re onboarding the right contractors in the first place, which is why 69% of companies have run background checks on their gig workers. That leaves 31% of businesses that didn’t, running the risk of hiring someone who might have cybercriminal activity on their record.
Work interruptions
Most companies focus on cybersecurity protocols before and during the gig work. However, the ones taken after the gig is over are just as vital for cybersecurity, if not more so.

Many business managers’ valuable time is mostly dedicated to their own tasks and those of their full-time employees. That’s why companies often need contractors to be self-starters and make decisions alone without taking up too much of a manager’s time. But while giving important passwords and account access to gig workers can save time, it’s not a safe solution.
According to our survey, 40% of managers are interrupted daily at work due to gig workers requesting passwords or account access, and 35% are interrupted a few times per week. On average, managers spend 34 minutes daily on these tasks. So, it’s easy to see how one might occasionally forget to change these passwords and permissions later.
However, these oversights can lead to leaked data. As a recent example, the Target-owned platform, Shipt was compromised by hackers who obtained gig workers’ emails and passwords. Despite the risk, while 66% said their company’s policy is to change a password after a gig worker finishes a job, this has often fallen through the cracks. We found that 73% of managers have forgotten to do this at the end of a gig.
Keeping companies secure
Fueled by the COVID-19 pandemic, remote work and the gig economy have undoubtedly brought dynamic growth to companies. While hiring gig workers has advantages for companies, it can also create cybersecurity threats.
While providing temporary passwords and restricting access may seem like a solution, forgetting to change these logins and permissions later puts businesses at risk. And without the proper protocols, gig workers are also open to cyberattacks while on the job.
In a digital world where hackers attack constantly, can your company’s cybersecurity training keep up? How will the future of gig work shape these practices? It might be time to level them up to ensure companies’ data remains safe.
Methodology
Beyond Identity surveyed 1,196 managers and contractors about cyber security and the gig economy. Among them, 58% were contractors, and 42% were managers who had hired a contractor on behalf of their company.
About Beyond Identity
Beyond Identity provides passwordless solutions to help secure digital business. Our cloud-native solutions also increase customers’ business velocity, and reduce their operating costs.
Fair use statement
This study is available to share only for noncommercial purposes as long as you link back to this original page.







.png)






.avif)



.avif)






.avif)

