The Beyond Blog

22 Jan 2026
Beyond Identity Opens Early Access for the AI Security Suite
Gain visibility and control over autonomous AI agents with Beyond Identity's AI Security Suite. Enforce identity, device context, and data governance with cryptographic proof. Early access is now open!

05 Feb 2024
February 5, 2024
Cloudflare Breach: Looking Into Cloudflare’s Thanksgiving 2023 Security Incident
Cloudflare’s disclosure of a security incident over Thanksgiving 2023 has sparked vital discussions in the cybersecurity community.

12 Jan 2024
January 12, 2024
Single-Device MFA: Eliminating Risks and Enabling Frictionless Security
To overcome security issues with traditional MFA, organizations are increasingly turning to single-device phishing-resistant MFA.

09 Jan 2024
January 9, 2024
Password Managers Hacked: A Comprehensive Overview
Recent breaches in popular password managers have raised serious concerns, despite their intended role as secure vaults.
11 Dec 2023
December 11, 2023
Mitigating Risks in the Wake of Okta Breaches: A Two-Pronged Approach
You can protect your Okta environment in the short-term while taking the time you need to plan and de-risk a migration down the line.

22 Nov 2023
November 22, 2023
Okta Breach Timeline: Breaking Down the Hacks
Okta's story the last two years highlights the urgent need for stronger defenses against vulnerabilities. Review the Okta breach timeline for insights.
14 Nov 2023
November 14, 2023
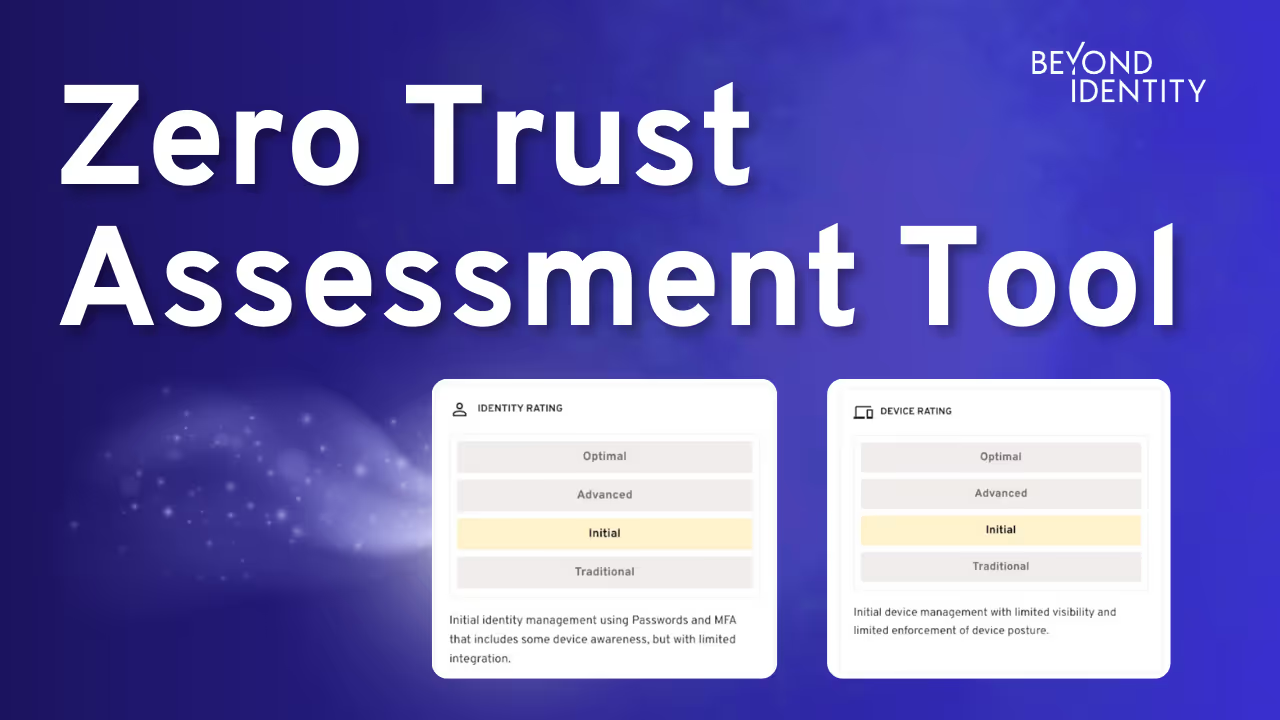
Beyond Identity's Zero Trust Assessment Tool: Unlock Your Security Potential
The new tool assesses your organization's current security environment by focusing on two critical aspects: identity verification and device compliance.

03 Nov 2023
November 3, 2023
Announcing: Okta Defense Kit
Free, privacy-preserving tools to rapidly determine whether your Okta instance is compromised and optimize overall Okta configuration security so you never have to wonder if you’ve been Okta Pwned.

26 Oct 2023
October 26, 2023
Beyond Identity Was Not Impacted by the Recent Okta Security Incident
We conclusively determined that our environment was not compromised and no Beyond Identity customers were impacted.

24 Oct 2023
October 24, 2023
A Clear Path Forward with Okta’s HAR File Challenges
Okta recommends sanitizing HAR files but stops short of providing a precise method for doing so. But worry not, Beyond Identity has risen to the occasion.

