Beyond Identity's Zero Trust Assessment Tool: Unlock Your Security Potential
In today’s rapidly evolving digital threat landscape, rise of remote work and mobile devices, and the need for reducing attack surfaces, organizations face an ever-increasing need to bolster their cybersecurity defenses.
One of the frameworks for mitigating these threats, zero trust, has gained prominence as it encourages continuous scrutiny of the user and device, irrespective of their network location or device ownership. This approach has been supported by the National Institute of Standards and Technology (NIST) through their zero trust architecture publication, and the Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model.
The challenge with adopting zero trust
There are many challenges associated with adopting zero trust, with one of them assessing your organization's current security posture and determining where you stand. Ask yourself:
- Authentication security: Are your current authentication methods robust and secure enough to withstand modern threats?
- Device management: Are your device management practices equipped with the necessary security measures to protect against unauthorized access and data breaches?
Another challenge is grasping the concept of an optimal zero trust implementation. When you have answered where you stand and where you want to go, you can begin to map out your journey towards zero trust implementation.
Initiating your zero trust journey
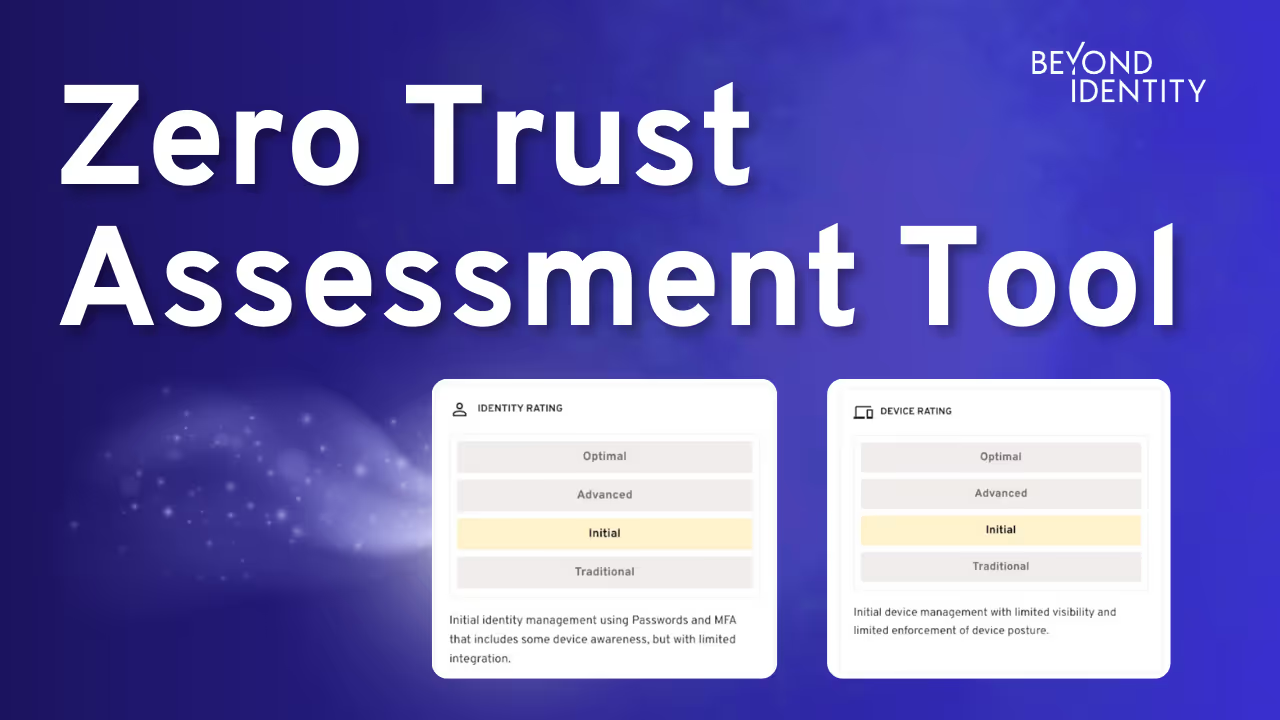
Beyond Identity's Identity and Device Zero Trust Assessment Tool serves as your guide through your zero trust journey. This tool assesses your organization's current security environment by focusing on two critical aspects: identity verification and device compliance.
Referencing the CISA Zero Trust Maturity Model, we provide an analysis of your current environment.
We go in depth on your authentication factors and device management practices, comparing them to the standards of an “Optimal” level of zero trust. Then, we illustrate the steps needed to get there.
See an overview of the tool and how it works:
Getting started
Begin your journey toward understanding, enhancing, and securing your environment today with our FREE assessment tool. Explore it at zerotrustassess.com.
Your cybersecurity transformation starts here.
In today’s rapidly evolving digital threat landscape, rise of remote work and mobile devices, and the need for reducing attack surfaces, organizations face an ever-increasing need to bolster their cybersecurity defenses.
One of the frameworks for mitigating these threats, zero trust, has gained prominence as it encourages continuous scrutiny of the user and device, irrespective of their network location or device ownership. This approach has been supported by the National Institute of Standards and Technology (NIST) through their zero trust architecture publication, and the Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model.
The challenge with adopting zero trust
There are many challenges associated with adopting zero trust, with one of them assessing your organization's current security posture and determining where you stand. Ask yourself:
- Authentication security: Are your current authentication methods robust and secure enough to withstand modern threats?
- Device management: Are your device management practices equipped with the necessary security measures to protect against unauthorized access and data breaches?
Another challenge is grasping the concept of an optimal zero trust implementation. When you have answered where you stand and where you want to go, you can begin to map out your journey towards zero trust implementation.
Initiating your zero trust journey
Beyond Identity's Identity and Device Zero Trust Assessment Tool serves as your guide through your zero trust journey. This tool assesses your organization's current security environment by focusing on two critical aspects: identity verification and device compliance.
Referencing the CISA Zero Trust Maturity Model, we provide an analysis of your current environment.
We go in depth on your authentication factors and device management practices, comparing them to the standards of an “Optimal” level of zero trust. Then, we illustrate the steps needed to get there.
See an overview of the tool and how it works:
Getting started
Begin your journey toward understanding, enhancing, and securing your environment today with our FREE assessment tool. Explore it at zerotrustassess.com.
Your cybersecurity transformation starts here.
In today’s rapidly evolving digital threat landscape, rise of remote work and mobile devices, and the need for reducing attack surfaces, organizations face an ever-increasing need to bolster their cybersecurity defenses.
One of the frameworks for mitigating these threats, zero trust, has gained prominence as it encourages continuous scrutiny of the user and device, irrespective of their network location or device ownership. This approach has been supported by the National Institute of Standards and Technology (NIST) through their zero trust architecture publication, and the Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model.
The challenge with adopting zero trust
There are many challenges associated with adopting zero trust, with one of them assessing your organization's current security posture and determining where you stand. Ask yourself:
- Authentication security: Are your current authentication methods robust and secure enough to withstand modern threats?
- Device management: Are your device management practices equipped with the necessary security measures to protect against unauthorized access and data breaches?
Another challenge is grasping the concept of an optimal zero trust implementation. When you have answered where you stand and where you want to go, you can begin to map out your journey towards zero trust implementation.
Initiating your zero trust journey
Beyond Identity's Identity and Device Zero Trust Assessment Tool serves as your guide through your zero trust journey. This tool assesses your organization's current security environment by focusing on two critical aspects: identity verification and device compliance.
Referencing the CISA Zero Trust Maturity Model, we provide an analysis of your current environment.
We go in depth on your authentication factors and device management practices, comparing them to the standards of an “Optimal” level of zero trust. Then, we illustrate the steps needed to get there.
See an overview of the tool and how it works:
Getting started
Begin your journey toward understanding, enhancing, and securing your environment today with our FREE assessment tool. Explore it at zerotrustassess.com.
Your cybersecurity transformation starts here.






.png)






.avif)



.avif)






.avif)

