Resource Library
Explore our collection of resources covering the latest in cybersecurity, industry trends, and expert insights
_v2.avif)
03 Feb 2025
February 3, 2025
Beyond Identity's CrowdStrike Integration: Going from Detection & Response to Prevention
In this webinar, our product experts break down how this bi-directional integration proactively stops threats by turning risk signals into immediate access decisions.

03 Jan 2025
January 3, 2025
Attackers Love Your SSO: Here’s How to Fight Back
Traditional SSOs often prioritize ease of use over robust security, leaving organizations vulnerable to credential-based attacks. In this webinar, we’ll show you how to transform your SSO into a critical security solution.

30 Dec 2024
December 30, 2024
AuthQuake: The Brute Force Attack Exploiting Microsoft MFA
We break down how the AuthQuake exploit works, why Microsoft’s response falls short, and the steps your organization can take to secure against similar attacks.

23 Dec 2024
December 23, 2024
Reclaim the Moments that Matter with Secure Access
The holidays are a time to connect with loved ones, not to battle security incidents. But attackers don’t take a break—and neither should your defenses.

16 Dec 2024
December 16, 2024
Beyond Talk: Simple to Administer
CEO Jasson Casey and Sr. Product Architect Louis Marascio break down how Beyond Identity simplifies the admin experience.

22 Nov 2024
November 22, 2024
Secure Access: How Beyond Identity Enables Security Guarantees
Our key guarantees: eliminating identity-based attacks and ensuring only secure devices, managed or unmanaged, gain and maintain access.
.avif)
13 Nov 2024
November 13, 2024
Beyond Talk: Easy to Use
In this video, we break down our Easy to Use pillar, emphasizing why intuitive design and seamless experiences are critical for effective cybersecurity.
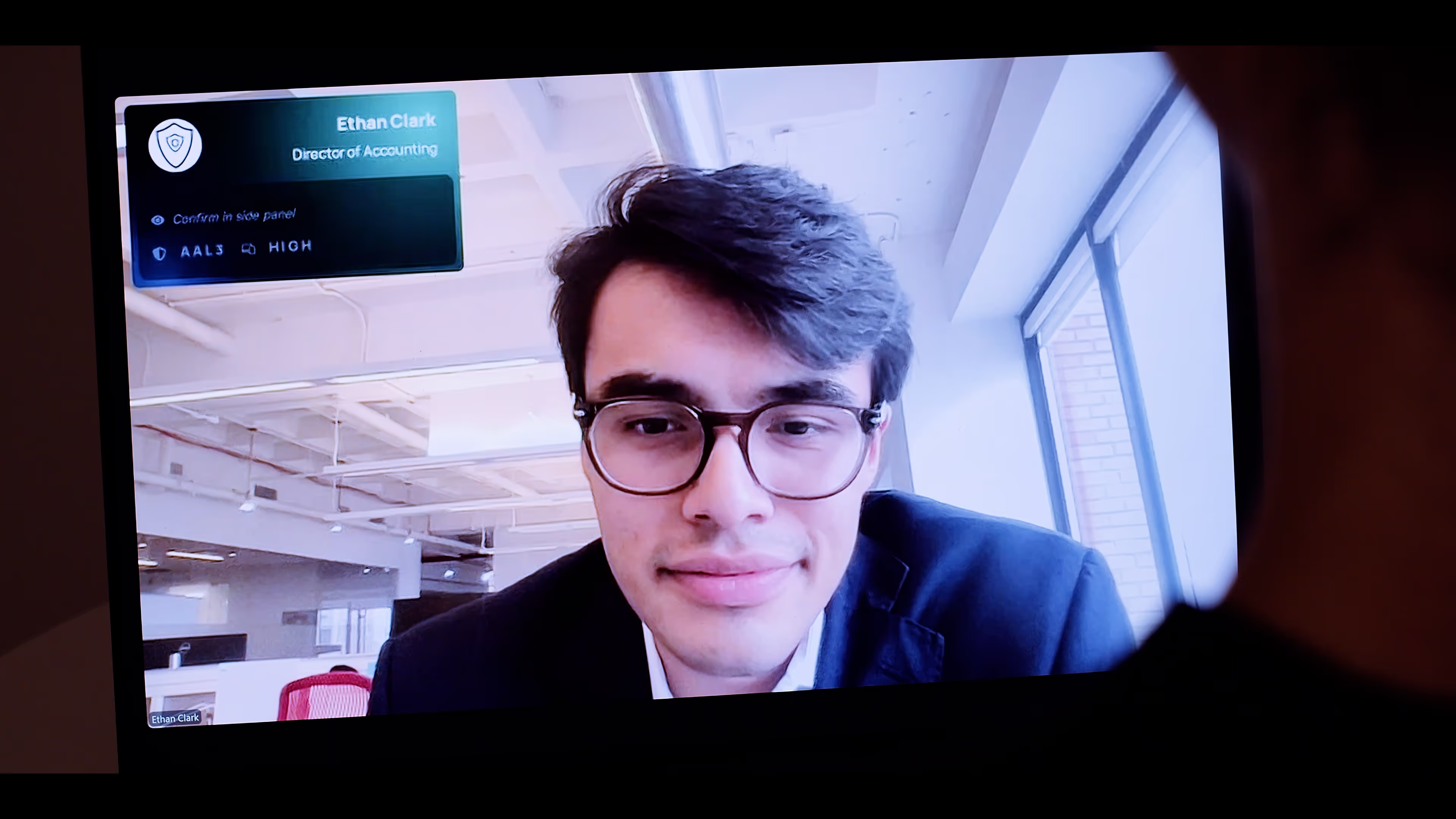
24 Oct 2024
October 24, 2024
Guarantee AI deception prevention with RealityCheck
Beyond Identity's RealityCheck solution is designed to protect your organization from deepfake attacks and identity fraud.

