Why Companies Need Both Zero Trust Authentication and Identity and Access Management
IT and security leaders face an uphill battle when it comes to battling cybercrime. Every day, criminals get more sophisticated and the costs of data breaches go up. That’s why Zero Trust Authentication and Identity and Access Management are so important. Used together, they are one of the best ways to reduce a company’s cybersecurity risk and overall impact of a cyber threat.
Zero Trust Authentication prevents bad actors from gaining access to critical company resources by denying access until the user and their device are verified. Since half of all external breaches are attributed to credential theft, this authentication approach significantly reduces the likelihood of unauthorized access. Zero Trust Authentication also means continuous checking user devices to ensure that cybercriminals cannot use infected or unsecured devices as a point of entry.
For Zero Trust Authentication to work, organizations need to create and manage digital user identities. Identity and Access Management (IAM) is the framework and set of policies that enable this user management. An IAM system houses and binds user identities and device information together. When a user logs in, the authenticator checks that user and device against the data stored in the IAM solution. It is the single source of truth in a zero trust architecture.
How to achieve Zero Trust Authentication
Many companies still rely on passwords coupled with weak and basic MFA for authentication. However, this traditional authentication method doesn’t assess behavior and risk profile when granting access. In short, it is no match for savvy cybercriminals.
Implementing Zero Trust Authentication should be one of the first initiatives on a zero trust journey. It’s easy to deploy and provides the most robust security available for a zero trust architecture.
Zero Trust Authentication has seven essential requirements. Your architecture must be:
- Passwordless.
- Phishing-resistant.
- Able to validate user devices.
- Capable of assessing device security posture.
- Able to analyze many types of risk signals.
- Equipped with continuous risk assessments.
- Integrated with your existing security infrastructure.
To meet all seven requirements, companies need to deploy these fundamental mechanisms:
Multi-Factor Authentication (MFA): MFA requires users to verify their identity with two or more factors. Asymmetric cryptography and biometric data are the gold standard of MFA because they are phishing-resistant.
Risk-Based Authentication (RBA): RBA adds extra security questions and checks for access to critical systems.
Device Trust: A series of checks for firewalls, antivirus software, biometrics, and more are performed at login to determine if a device is trustworthy.
Continuous Authentication: Regular checks for location changes, device posture, and other behaviors are performed behind the scenes during each user session.
Leveraging Identity and Access Management (IAM)
The IAM solution manages all user identities and sets access permissions. Every mechanism that enables Zero Trust Authentication relies on this data to approve access, making IAM solutions foundational to successful Zero Trust Authentication.
Without an IAM solution, user data and access management policies are scattered across various platforms. These silos make it harder to identify the source of the compromise and revoke access when there is a breach, giving bad actors all the time they need to wreak havoc in critical systems.
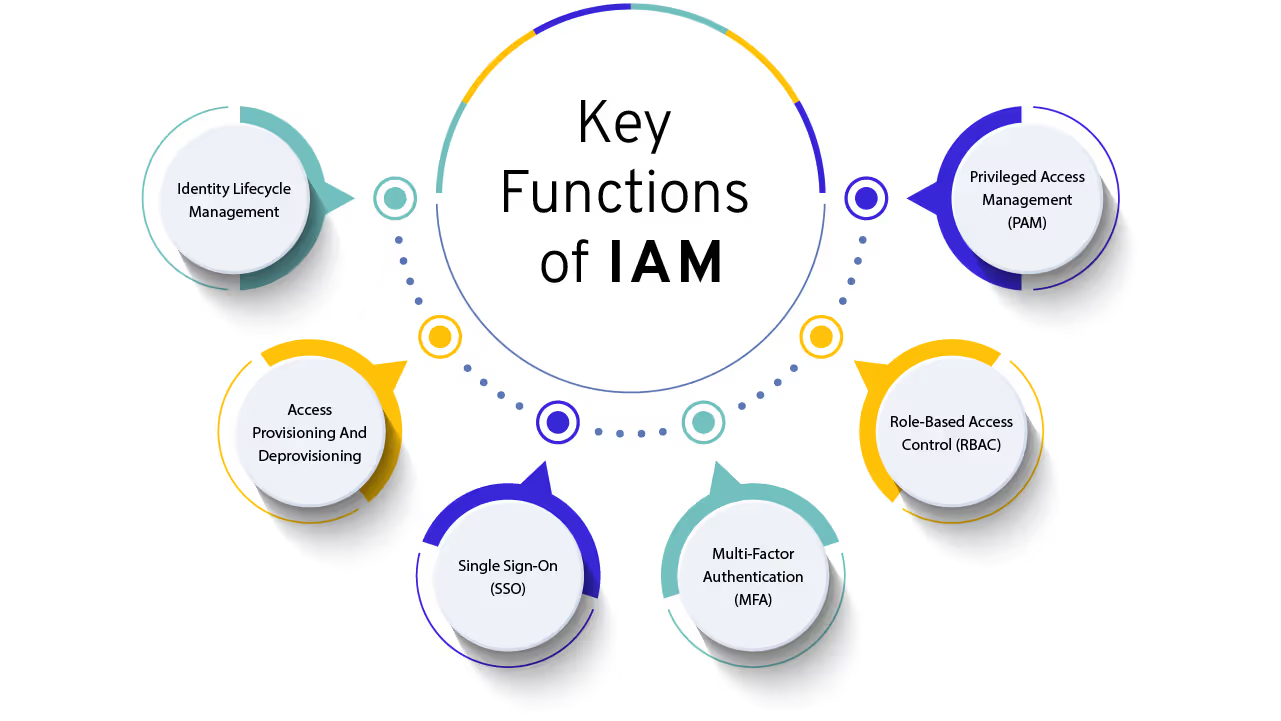
Key functions of IAM
Both solutions in action
Zero Trust Authentication cannot happen without IAM, but IAM solutions can function without Zero Trust Authentication. However, companies with only an IAM solution remain vulnerable to cybercriminals. With both solutions, companies shrink their attack surface and reduce organizational risk.
Zero Trust Authentication with IAM strengthens security by:
- Removing vulnerable passwords from the login process
- Relying only on phishing-resistant authentication factors
- Validating user devices
- Running device security checks
- Looking at risk signals for user and device
- Performing continuous risk assessments
Integrating into your security infrastructure
Zero Trust Authentication and IAM solutions can easily integrate into your existing security setup. Connecting other security tools to their authentication data speeds up your detection and response capabilities and allows you to adapt to evolving threats.
Centralizing user and authentication data also provides more holistic information for audit and compliance reports. Companies dedicated to compliance with cybersecurity and privacy regulations build trust with employees and customers alike.
User experience and adoption
For Zero Trust Authentication with IAM to be effective, every user must adopt the new login procedures. Users are much more likely to move to new authentication methods when they feel seamless and do not slow them down.
Eliminating passwords not only reduces login frustrations for employees but also decreases the time IT spends on password reset requests.. Passwords are also the single largest source of ransomware and other cyber attacks.
Beyond Identity’s Zero Trust Authentication offers a unique approach to phishing-resistant, passwordless authentication that is simple for both users and IT teams. User and device checks run in the background, unseen by the user, and take just seconds. Removing friction while increasing security.
Read the full report to learn more about the benefits of Zero Trust Authentication with IAM.
IT and security leaders face an uphill battle when it comes to battling cybercrime. Every day, criminals get more sophisticated and the costs of data breaches go up. That’s why Zero Trust Authentication and Identity and Access Management are so important. Used together, they are one of the best ways to reduce a company’s cybersecurity risk and overall impact of a cyber threat.
Zero Trust Authentication prevents bad actors from gaining access to critical company resources by denying access until the user and their device are verified. Since half of all external breaches are attributed to credential theft, this authentication approach significantly reduces the likelihood of unauthorized access. Zero Trust Authentication also means continuous checking user devices to ensure that cybercriminals cannot use infected or unsecured devices as a point of entry.
For Zero Trust Authentication to work, organizations need to create and manage digital user identities. Identity and Access Management (IAM) is the framework and set of policies that enable this user management. An IAM system houses and binds user identities and device information together. When a user logs in, the authenticator checks that user and device against the data stored in the IAM solution. It is the single source of truth in a zero trust architecture.
How to achieve Zero Trust Authentication
Many companies still rely on passwords coupled with weak and basic MFA for authentication. However, this traditional authentication method doesn’t assess behavior and risk profile when granting access. In short, it is no match for savvy cybercriminals.
Implementing Zero Trust Authentication should be one of the first initiatives on a zero trust journey. It’s easy to deploy and provides the most robust security available for a zero trust architecture.
Zero Trust Authentication has seven essential requirements. Your architecture must be:
- Passwordless.
- Phishing-resistant.
- Able to validate user devices.
- Capable of assessing device security posture.
- Able to analyze many types of risk signals.
- Equipped with continuous risk assessments.
- Integrated with your existing security infrastructure.
To meet all seven requirements, companies need to deploy these fundamental mechanisms:
Multi-Factor Authentication (MFA): MFA requires users to verify their identity with two or more factors. Asymmetric cryptography and biometric data are the gold standard of MFA because they are phishing-resistant.
Risk-Based Authentication (RBA): RBA adds extra security questions and checks for access to critical systems.
Device Trust: A series of checks for firewalls, antivirus software, biometrics, and more are performed at login to determine if a device is trustworthy.
Continuous Authentication: Regular checks for location changes, device posture, and other behaviors are performed behind the scenes during each user session.
Leveraging Identity and Access Management (IAM)
The IAM solution manages all user identities and sets access permissions. Every mechanism that enables Zero Trust Authentication relies on this data to approve access, making IAM solutions foundational to successful Zero Trust Authentication.
Without an IAM solution, user data and access management policies are scattered across various platforms. These silos make it harder to identify the source of the compromise and revoke access when there is a breach, giving bad actors all the time they need to wreak havoc in critical systems.
Key functions of IAM

Both solutions in action
Zero Trust Authentication cannot happen without IAM, but IAM solutions can function without Zero Trust Authentication. However, companies with only an IAM solution remain vulnerable to cybercriminals. With both solutions, companies shrink their attack surface and reduce organizational risk.
Zero Trust Authentication with IAM strengthens security by:
- Removing vulnerable passwords from the login process
- Relying only on phishing-resistant authentication factors
- Validating user devices
- Running device security checks
- Looking at risk signals for user and device
- Performing continuous risk assessments
Integrating into your security infrastructure
Zero Trust Authentication and IAM solutions can easily integrate into your existing security setup. Connecting other security tools to their authentication data speeds up your detection and response capabilities and allows you to adapt to evolving threats.
Centralizing user and authentication data also provides more holistic information for audit and compliance reports. Companies dedicated to compliance with cybersecurity and privacy regulations build trust with employees and customers alike.
User experience and adoption
For Zero Trust Authentication with IAM to be effective, every user must adopt the new login procedures. Users are much more likely to move to new authentication methods when they feel seamless and do not slow them down.
Eliminating passwords not only reduces login frustrations for employees but also decreases the time IT spends on password reset requests.. Passwords are also the single largest source of ransomware and other cyber attacks.
Beyond Identity’s Zero Trust Authentication offers a unique approach to phishing-resistant, passwordless authentication that is simple for both users and IT teams. User and device checks run in the background, unseen by the user, and take just seconds. Removing friction while increasing security.
Read the full report to learn more about the benefits of Zero Trust Authentication with IAM.
IT and security leaders face an uphill battle when it comes to battling cybercrime. Every day, criminals get more sophisticated and the costs of data breaches go up. That’s why Zero Trust Authentication and Identity and Access Management are so important. Used together, they are one of the best ways to reduce a company’s cybersecurity risk and overall impact of a cyber threat.
Zero Trust Authentication prevents bad actors from gaining access to critical company resources by denying access until the user and their device are verified. Since half of all external breaches are attributed to credential theft, this authentication approach significantly reduces the likelihood of unauthorized access. Zero Trust Authentication also means continuous checking user devices to ensure that cybercriminals cannot use infected or unsecured devices as a point of entry.
For Zero Trust Authentication to work, organizations need to create and manage digital user identities. Identity and Access Management (IAM) is the framework and set of policies that enable this user management. An IAM system houses and binds user identities and device information together. When a user logs in, the authenticator checks that user and device against the data stored in the IAM solution. It is the single source of truth in a zero trust architecture.
How to achieve Zero Trust Authentication
Many companies still rely on passwords coupled with weak and basic MFA for authentication. However, this traditional authentication method doesn’t assess behavior and risk profile when granting access. In short, it is no match for savvy cybercriminals.
Implementing Zero Trust Authentication should be one of the first initiatives on a zero trust journey. It’s easy to deploy and provides the most robust security available for a zero trust architecture.
Zero Trust Authentication has seven essential requirements. Your architecture must be:
- Passwordless.
- Phishing-resistant.
- Able to validate user devices.
- Capable of assessing device security posture.
- Able to analyze many types of risk signals.
- Equipped with continuous risk assessments.
- Integrated with your existing security infrastructure.
To meet all seven requirements, companies need to deploy these fundamental mechanisms:
Multi-Factor Authentication (MFA): MFA requires users to verify their identity with two or more factors. Asymmetric cryptography and biometric data are the gold standard of MFA because they are phishing-resistant.
Risk-Based Authentication (RBA): RBA adds extra security questions and checks for access to critical systems.
Device Trust: A series of checks for firewalls, antivirus software, biometrics, and more are performed at login to determine if a device is trustworthy.
Continuous Authentication: Regular checks for location changes, device posture, and other behaviors are performed behind the scenes during each user session.
Leveraging Identity and Access Management (IAM)
The IAM solution manages all user identities and sets access permissions. Every mechanism that enables Zero Trust Authentication relies on this data to approve access, making IAM solutions foundational to successful Zero Trust Authentication.
Without an IAM solution, user data and access management policies are scattered across various platforms. These silos make it harder to identify the source of the compromise and revoke access when there is a breach, giving bad actors all the time they need to wreak havoc in critical systems.
Key functions of IAM

Both solutions in action
Zero Trust Authentication cannot happen without IAM, but IAM solutions can function without Zero Trust Authentication. However, companies with only an IAM solution remain vulnerable to cybercriminals. With both solutions, companies shrink their attack surface and reduce organizational risk.
Zero Trust Authentication with IAM strengthens security by:
- Removing vulnerable passwords from the login process
- Relying only on phishing-resistant authentication factors
- Validating user devices
- Running device security checks
- Looking at risk signals for user and device
- Performing continuous risk assessments
Integrating into your security infrastructure
Zero Trust Authentication and IAM solutions can easily integrate into your existing security setup. Connecting other security tools to their authentication data speeds up your detection and response capabilities and allows you to adapt to evolving threats.
Centralizing user and authentication data also provides more holistic information for audit and compliance reports. Companies dedicated to compliance with cybersecurity and privacy regulations build trust with employees and customers alike.
User experience and adoption
For Zero Trust Authentication with IAM to be effective, every user must adopt the new login procedures. Users are much more likely to move to new authentication methods when they feel seamless and do not slow them down.
Eliminating passwords not only reduces login frustrations for employees but also decreases the time IT spends on password reset requests.. Passwords are also the single largest source of ransomware and other cyber attacks.
Beyond Identity’s Zero Trust Authentication offers a unique approach to phishing-resistant, passwordless authentication that is simple for both users and IT teams. User and device checks run in the background, unseen by the user, and take just seconds. Removing friction while increasing security.
Read the full report to learn more about the benefits of Zero Trust Authentication with IAM.







.png)






.avif)



.avif)






.avif)

