Which Authentication Method is Most Secure?
What is authentication? In the most basic terms it is verifying that you are who you say you are. Although this sounds simple, it is a problem that has been difficult to solve in the digital world. The measure of what makes an authentication solution effective is based on two components: security and usability.
Authentication Security and Usability
Security is the most obvious, and often the most discussed. This boils down to how effective the authentication method is at preventing identity theft or unauthorized access. However a narrow focus on security can ignore the practicality of using an authentication method. Although a unique device implanted under a person’s skin would be a highly secure authentication method, it is not practical.
In the real world, usability is as important as security. The costs of security failures can be read about in headlines about high-profile breaches, but the cost of usability failures are suffered more quietly. These costs manifest in the workplace in the forms of productivity loss and help desk expenses. When employees have a cumbersome process for logging in to the applications they need to work, they will either spend less time working and more time attempting to login while also burdening the help desk with the increased need for assistance or they will find a way around the login process sacrificing the security that was put in place.
The Authentication Methods
Passwords
The most common, and one of the most insecure, authentication method is the password. A string of characters used to verify the identity of a user, known to both the user and the service provider.
Security
From a security standpoint these are notoriously weak for two reasons. First, because it is a shared secret, meaning that it is stored somewhere (the application’s database) as well as being known by the user (often written down). This has been corrected for, somewhat, by hashing requirements for password storage. This still places the onus on the user to have a password (many users have over 100) stored in their memory and not recording it anywhere from where it can be stolen. For obvious reasons passwords do not do a great job of meeting the definition of authentication, proving that you are you, since anyone with your password can pretend to be you.
Usability
It is not even as if the password is trading weak security for increased user convenience. Constant resets and increasingly stringent requirements make passwords a consistent source of productivity loss and help desk calls.
Knowledge-Based Questions
A personal question about the user, often used in addition to passwords.
Security
There’s still a password and this is merely adding a second shared secret. Answers to the security questions, such as street names and your mother’s maiden name can be easily discovered on the internet and are a lower barrier to entry than the initial password.
Usability
On their own these are not terribly inconvenient since they do not likely require help desk calls or reduce productivity. However, since they often accompany a password, they add another step for the user without providing them additional security.
Mobile push notifications
A notification sent to a user’s mobile device, asking them to select “yes or no” as to whether or not they are trying to access a specific resource.
Security
Mobile push notifications are more secure than passwords or knowledge-based questions because they require the physical possession of a device, however, this method is still rife with security issues. Mobile push notifications are vulnerable to security issues on the mobile devices itself, such as SIM card hijacking, malware, or spyware on the device. Other security issues include notification flooding attacks that cause the user to select “yes” so routinely that they don’t pay attention to if it is in fact themself who is requesting access.
Usability
This is relatively easy once set up, as it only requires a device that the user already has, their mobile device. However, there is some inconvenience stemming from the need to always be in possession of a mobile device when logging in on other devices, such as their desktop computer or laptop.
Mobile SMS notifications
Sends a verification text message requiring the user to reply “yes or no”.
Security
These are very easy to spoof or compromise via a man in the middle attack. As the text is sent over the standard cell network these messages are not encrypted and can be intercepted.
Usability
Similar to mobile push notifications, these are pretty easy for users to navigate without a help desk but cause some inconvenience due to the need for the user’s mobile device to be on hand at all times.
Time-Based One Time Password (OTP)
A password or PIN valid for only a single session. This method requires a computer-generated code that typically changes every 30-60 seconds, depending on the configuration. The code is delivered via mobile app, hardware token, or sent to a user over SMS.
Security
One-Time Passwords are generally used in combination with passwords and are vulnerable to man-in-the-middle attacks and are a shared secret, creating two attack vectors.
Usability
They are reasonably burdensome for users given the need for external hardware and the small amount of time to copy the one time passcode from an external device to login.
Out-of-Band Voice/Call Back Authentication
The platform being accessed calls the requester's phone number to verify identity.
Security
This is not very secure as phone calls can be redirected or intercepted. Suffering from the same issues as SMS authentication, a phone number is not a secure verifier of identity.
Usability
This requires multiple devices and answering a phone call causing significant friction for the individual attempting to login.
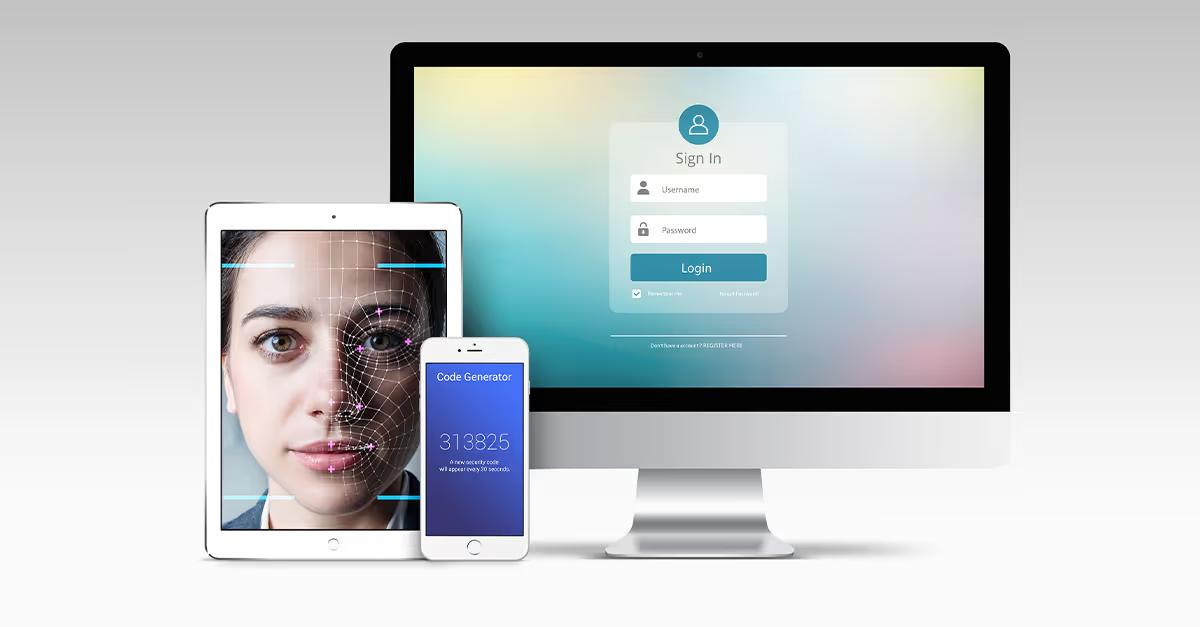
Biometrics
A physical or behavioral human characteristic such as facial recognition, fingerprinting, retina scans, etc.
Security
Biometrics are sensitive and it’s near impossible to spoof someone’s biometric. However, if a biometric is stolen, it cannot be changed. Therefore, biometrics can be a very secure authentication method, as long as the biometric data is stored securely. If a biometric is stored improperly, such as on the cloud, it can become a shared secret and subject to leaks.
Usability
This is an easy to use method for individuals, because a biometric is “something they are”. As long as false positives are minimized, this is a very simple form of authentication.
Public-Key Cryptography (PKC)
A cryptographic system relying on pairs of keys including a a private key stored securely on the device and a public key which is widely available.
Security
This type of technology has been used to secure digital transactions for 30 years. Similar to biometrics, this can be a very secure method of authentication as long as the private key is stored in a safe place.
Usability
With an application like Beyond Identity that manages asymmetric keys key, this can be very easy to use. For a user logging in it feels as though they only enter their username and that is it. There is no need for a second device, a hardware token or the memorization of a code.
What about legacy multi-factor authentication (MFA) solutions?
As we assessed available authentication methods we purposely looked at them each individually on their own merits. Although legacy MFA solutions combine multiple authentication methods with one another (usually one of which being a password), their security is not increased by this type of stacking and if anything it is usually to the detriment of their usability. Two doors with weak locks are not any more secure than one door with a weak lock, it is merely inconvenient.
What is Beyond Identity?
Beyond Identity combines two of the strongest authenticators: biometrics and asymmetric keys. It eliminates the password and provides an extremely secure authentication since the user’s identity is only stored locally on the device and it cannot be moved. There’s also a drastic reduction in user friction over other authentication methods, including legacy multi-factor authentication, because the end user doesn’t have to create, remember, or change passwords.
See for yourself: Get a Demo of Beyond Identity
What is authentication? In the most basic terms it is verifying that you are who you say you are. Although this sounds simple, it is a problem that has been difficult to solve in the digital world. The measure of what makes an authentication solution effective is based on two components: security and usability.
Authentication Security and Usability
Security is the most obvious, and often the most discussed. This boils down to how effective the authentication method is at preventing identity theft or unauthorized access. However a narrow focus on security can ignore the practicality of using an authentication method. Although a unique device implanted under a person’s skin would be a highly secure authentication method, it is not practical.
In the real world, usability is as important as security. The costs of security failures can be read about in headlines about high-profile breaches, but the cost of usability failures are suffered more quietly. These costs manifest in the workplace in the forms of productivity loss and help desk expenses. When employees have a cumbersome process for logging in to the applications they need to work, they will either spend less time working and more time attempting to login while also burdening the help desk with the increased need for assistance or they will find a way around the login process sacrificing the security that was put in place.
The Authentication Methods
Passwords
The most common, and one of the most insecure, authentication method is the password. A string of characters used to verify the identity of a user, known to both the user and the service provider.
Security
From a security standpoint these are notoriously weak for two reasons. First, because it is a shared secret, meaning that it is stored somewhere (the application’s database) as well as being known by the user (often written down). This has been corrected for, somewhat, by hashing requirements for password storage. This still places the onus on the user to have a password (many users have over 100) stored in their memory and not recording it anywhere from where it can be stolen. For obvious reasons passwords do not do a great job of meeting the definition of authentication, proving that you are you, since anyone with your password can pretend to be you.
Usability
It is not even as if the password is trading weak security for increased user convenience. Constant resets and increasingly stringent requirements make passwords a consistent source of productivity loss and help desk calls.
Knowledge-Based Questions
A personal question about the user, often used in addition to passwords.
Security
There’s still a password and this is merely adding a second shared secret. Answers to the security questions, such as street names and your mother’s maiden name can be easily discovered on the internet and are a lower barrier to entry than the initial password.
Usability
On their own these are not terribly inconvenient since they do not likely require help desk calls or reduce productivity. However, since they often accompany a password, they add another step for the user without providing them additional security.
Mobile push notifications
A notification sent to a user’s mobile device, asking them to select “yes or no” as to whether or not they are trying to access a specific resource.
Security
Mobile push notifications are more secure than passwords or knowledge-based questions because they require the physical possession of a device, however, this method is still rife with security issues. Mobile push notifications are vulnerable to security issues on the mobile devices itself, such as SIM card hijacking, malware, or spyware on the device. Other security issues include notification flooding attacks that cause the user to select “yes” so routinely that they don’t pay attention to if it is in fact themself who is requesting access.
Usability
This is relatively easy once set up, as it only requires a device that the user already has, their mobile device. However, there is some inconvenience stemming from the need to always be in possession of a mobile device when logging in on other devices, such as their desktop computer or laptop.
Mobile SMS notifications
Sends a verification text message requiring the user to reply “yes or no”.
Security
These are very easy to spoof or compromise via a man in the middle attack. As the text is sent over the standard cell network these messages are not encrypted and can be intercepted.
Usability
Similar to mobile push notifications, these are pretty easy for users to navigate without a help desk but cause some inconvenience due to the need for the user’s mobile device to be on hand at all times.
Time-Based One Time Password (OTP)
A password or PIN valid for only a single session. This method requires a computer-generated code that typically changes every 30-60 seconds, depending on the configuration. The code is delivered via mobile app, hardware token, or sent to a user over SMS.
Security
One-Time Passwords are generally used in combination with passwords and are vulnerable to man-in-the-middle attacks and are a shared secret, creating two attack vectors.
Usability
They are reasonably burdensome for users given the need for external hardware and the small amount of time to copy the one time passcode from an external device to login.
Out-of-Band Voice/Call Back Authentication
The platform being accessed calls the requester's phone number to verify identity.
Security
This is not very secure as phone calls can be redirected or intercepted. Suffering from the same issues as SMS authentication, a phone number is not a secure verifier of identity.
Usability
This requires multiple devices and answering a phone call causing significant friction for the individual attempting to login.
Biometrics
A physical or behavioral human characteristic such as facial recognition, fingerprinting, retina scans, etc.
Security
Biometrics are sensitive and it’s near impossible to spoof someone’s biometric. However, if a biometric is stolen, it cannot be changed. Therefore, biometrics can be a very secure authentication method, as long as the biometric data is stored securely. If a biometric is stored improperly, such as on the cloud, it can become a shared secret and subject to leaks.
Usability
This is an easy to use method for individuals, because a biometric is “something they are”. As long as false positives are minimized, this is a very simple form of authentication.
Public-Key Cryptography (PKC)
A cryptographic system relying on pairs of keys including a a private key stored securely on the device and a public key which is widely available.
Security
This type of technology has been used to secure digital transactions for 30 years. Similar to biometrics, this can be a very secure method of authentication as long as the private key is stored in a safe place.
Usability
With an application like Beyond Identity that manages asymmetric keys key, this can be very easy to use. For a user logging in it feels as though they only enter their username and that is it. There is no need for a second device, a hardware token or the memorization of a code.
What about legacy multi-factor authentication (MFA) solutions?
As we assessed available authentication methods we purposely looked at them each individually on their own merits. Although legacy MFA solutions combine multiple authentication methods with one another (usually one of which being a password), their security is not increased by this type of stacking and if anything it is usually to the detriment of their usability. Two doors with weak locks are not any more secure than one door with a weak lock, it is merely inconvenient.
What is Beyond Identity?
Beyond Identity combines two of the strongest authenticators: biometrics and asymmetric keys. It eliminates the password and provides an extremely secure authentication since the user’s identity is only stored locally on the device and it cannot be moved. There’s also a drastic reduction in user friction over other authentication methods, including legacy multi-factor authentication, because the end user doesn’t have to create, remember, or change passwords.
See for yourself: Get a Demo of Beyond Identity
What is authentication? In the most basic terms it is verifying that you are who you say you are. Although this sounds simple, it is a problem that has been difficult to solve in the digital world. The measure of what makes an authentication solution effective is based on two components: security and usability.
Authentication Security and Usability
Security is the most obvious, and often the most discussed. This boils down to how effective the authentication method is at preventing identity theft or unauthorized access. However a narrow focus on security can ignore the practicality of using an authentication method. Although a unique device implanted under a person’s skin would be a highly secure authentication method, it is not practical.
In the real world, usability is as important as security. The costs of security failures can be read about in headlines about high-profile breaches, but the cost of usability failures are suffered more quietly. These costs manifest in the workplace in the forms of productivity loss and help desk expenses. When employees have a cumbersome process for logging in to the applications they need to work, they will either spend less time working and more time attempting to login while also burdening the help desk with the increased need for assistance or they will find a way around the login process sacrificing the security that was put in place.
The Authentication Methods
Passwords
The most common, and one of the most insecure, authentication method is the password. A string of characters used to verify the identity of a user, known to both the user and the service provider.
Security
From a security standpoint these are notoriously weak for two reasons. First, because it is a shared secret, meaning that it is stored somewhere (the application’s database) as well as being known by the user (often written down). This has been corrected for, somewhat, by hashing requirements for password storage. This still places the onus on the user to have a password (many users have over 100) stored in their memory and not recording it anywhere from where it can be stolen. For obvious reasons passwords do not do a great job of meeting the definition of authentication, proving that you are you, since anyone with your password can pretend to be you.
Usability
It is not even as if the password is trading weak security for increased user convenience. Constant resets and increasingly stringent requirements make passwords a consistent source of productivity loss and help desk calls.
Knowledge-Based Questions
A personal question about the user, often used in addition to passwords.
Security
There’s still a password and this is merely adding a second shared secret. Answers to the security questions, such as street names and your mother’s maiden name can be easily discovered on the internet and are a lower barrier to entry than the initial password.
Usability
On their own these are not terribly inconvenient since they do not likely require help desk calls or reduce productivity. However, since they often accompany a password, they add another step for the user without providing them additional security.
Mobile push notifications
A notification sent to a user’s mobile device, asking them to select “yes or no” as to whether or not they are trying to access a specific resource.
Security
Mobile push notifications are more secure than passwords or knowledge-based questions because they require the physical possession of a device, however, this method is still rife with security issues. Mobile push notifications are vulnerable to security issues on the mobile devices itself, such as SIM card hijacking, malware, or spyware on the device. Other security issues include notification flooding attacks that cause the user to select “yes” so routinely that they don’t pay attention to if it is in fact themself who is requesting access.
Usability
This is relatively easy once set up, as it only requires a device that the user already has, their mobile device. However, there is some inconvenience stemming from the need to always be in possession of a mobile device when logging in on other devices, such as their desktop computer or laptop.
Mobile SMS notifications
Sends a verification text message requiring the user to reply “yes or no”.
Security
These are very easy to spoof or compromise via a man in the middle attack. As the text is sent over the standard cell network these messages are not encrypted and can be intercepted.
Usability
Similar to mobile push notifications, these are pretty easy for users to navigate without a help desk but cause some inconvenience due to the need for the user’s mobile device to be on hand at all times.
Time-Based One Time Password (OTP)
A password or PIN valid for only a single session. This method requires a computer-generated code that typically changes every 30-60 seconds, depending on the configuration. The code is delivered via mobile app, hardware token, or sent to a user over SMS.
Security
One-Time Passwords are generally used in combination with passwords and are vulnerable to man-in-the-middle attacks and are a shared secret, creating two attack vectors.
Usability
They are reasonably burdensome for users given the need for external hardware and the small amount of time to copy the one time passcode from an external device to login.
Out-of-Band Voice/Call Back Authentication
The platform being accessed calls the requester's phone number to verify identity.
Security
This is not very secure as phone calls can be redirected or intercepted. Suffering from the same issues as SMS authentication, a phone number is not a secure verifier of identity.
Usability
This requires multiple devices and answering a phone call causing significant friction for the individual attempting to login.
Biometrics
A physical or behavioral human characteristic such as facial recognition, fingerprinting, retina scans, etc.
Security
Biometrics are sensitive and it’s near impossible to spoof someone’s biometric. However, if a biometric is stolen, it cannot be changed. Therefore, biometrics can be a very secure authentication method, as long as the biometric data is stored securely. If a biometric is stored improperly, such as on the cloud, it can become a shared secret and subject to leaks.
Usability
This is an easy to use method for individuals, because a biometric is “something they are”. As long as false positives are minimized, this is a very simple form of authentication.
Public-Key Cryptography (PKC)
A cryptographic system relying on pairs of keys including a a private key stored securely on the device and a public key which is widely available.
Security
This type of technology has been used to secure digital transactions for 30 years. Similar to biometrics, this can be a very secure method of authentication as long as the private key is stored in a safe place.
Usability
With an application like Beyond Identity that manages asymmetric keys key, this can be very easy to use. For a user logging in it feels as though they only enter their username and that is it. There is no need for a second device, a hardware token or the memorization of a code.
What about legacy multi-factor authentication (MFA) solutions?
As we assessed available authentication methods we purposely looked at them each individually on their own merits. Although legacy MFA solutions combine multiple authentication methods with one another (usually one of which being a password), their security is not increased by this type of stacking and if anything it is usually to the detriment of their usability. Two doors with weak locks are not any more secure than one door with a weak lock, it is merely inconvenient.
What is Beyond Identity?
Beyond Identity combines two of the strongest authenticators: biometrics and asymmetric keys. It eliminates the password and provides an extremely secure authentication since the user’s identity is only stored locally on the device and it cannot be moved. There’s also a drastic reduction in user friction over other authentication methods, including legacy multi-factor authentication, because the end user doesn’t have to create, remember, or change passwords.
See for yourself: Get a Demo of Beyond Identity












.avif)
.avif)



.avif)






.avif)

