Risk Policies and Step-Up Authentication
In this video, we’ll walk through how to create risk policies in Beyond Identity. First, admins will log in to the Beyond Identity Console.
Note: there isn't a password to log in. Admins use their Beyond Identity Authenticator and credentials on their device, which means only your admin's registered devices can access the admin console.
Now, click on the policy tab. So admins can determine if a user and a device meets their security requirements and whether they should be allowed to access company resources or not. There are policies for authentication and the types of policies that are allowed to add the Beyond Identity Authenticator.
For policies, rules execute in consecutive order, from top to bottom, and admins can drag and reorder rules. There's a variety of granular risk signals that admins can use to build policies. Admins can choose to approve, ask for additional verification or step up, or deny authentication.
Common risk policies
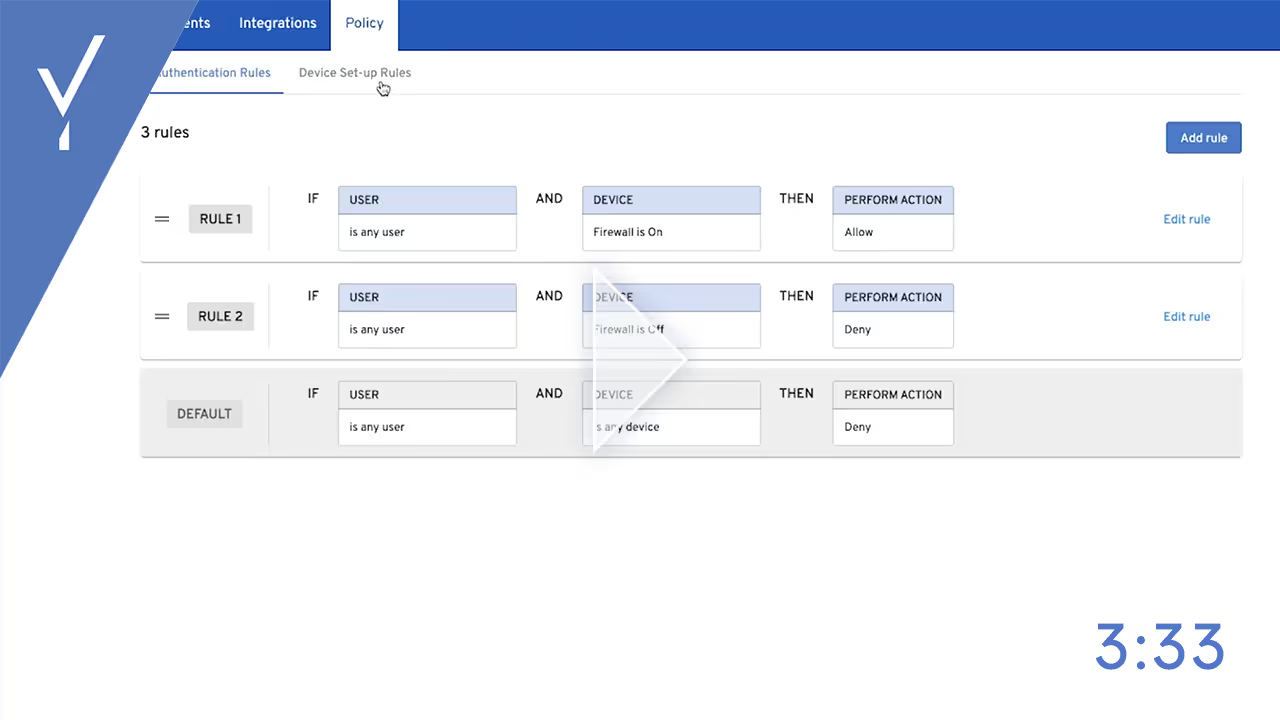
We're going to walk through some common risk policies that customers create. The first policy we’re going to walk through is to check a user’s computer to make sure they have their firewall on before allowing them to authenticate.
The policy is set so that if firewall is on, it will allow the user in. If the firewall is off, it will deny the user. So let's turn off firewall. And so the user is not authorized.
So let's turn the firewall on and try again. Now we're in.
Another common occurrence is for admins to enable step-up authentication in high-risk situations as defined by the company. For example, if a user is logging in from an unmanaged device, admins can ask the user for a step up verification such as an OS biometric verification to get access.
Now let's see this step up in action. The user requests access, they’re asked for a step-up biometric, and now they’re in.
The last policy we’re going to walk through is if companies don’t want to allow users to add the Authenticator to their mobile device, they can restrict which operating systems are allowed to add an authenticator. They can create a rule that says if this is an iOS device, then users are not allowed to set up their credentials on that device.
So let’s see that in action. Here, an iPhone is opened and they’re trying to set up their credentials, and they’re unable to. The rule executed successfully.
This was a quick overview of a few types of risk access policies you can configure in Beyond Identity.
In this video, we’ll walk through how to create risk policies in Beyond Identity. First, admins will log in to the Beyond Identity Console.
Note: there isn't a password to log in. Admins use their Beyond Identity Authenticator and credentials on their device, which means only your admin's registered devices can access the admin console.
Now, click on the policy tab. So admins can determine if a user and a device meets their security requirements and whether they should be allowed to access company resources or not. There are policies for authentication and the types of policies that are allowed to add the Beyond Identity Authenticator.
For policies, rules execute in consecutive order, from top to bottom, and admins can drag and reorder rules. There's a variety of granular risk signals that admins can use to build policies. Admins can choose to approve, ask for additional verification or step up, or deny authentication.
Common risk policies
We're going to walk through some common risk policies that customers create. The first policy we’re going to walk through is to check a user’s computer to make sure they have their firewall on before allowing them to authenticate.
The policy is set so that if firewall is on, it will allow the user in. If the firewall is off, it will deny the user. So let's turn off firewall. And so the user is not authorized.
So let's turn the firewall on and try again. Now we're in.
Another common occurrence is for admins to enable step-up authentication in high-risk situations as defined by the company. For example, if a user is logging in from an unmanaged device, admins can ask the user for a step up verification such as an OS biometric verification to get access.
Now let's see this step up in action. The user requests access, they’re asked for a step-up biometric, and now they’re in.
The last policy we’re going to walk through is if companies don’t want to allow users to add the Authenticator to their mobile device, they can restrict which operating systems are allowed to add an authenticator. They can create a rule that says if this is an iOS device, then users are not allowed to set up their credentials on that device.
So let’s see that in action. Here, an iPhone is opened and they’re trying to set up their credentials, and they’re unable to. The rule executed successfully.
This was a quick overview of a few types of risk access policies you can configure in Beyond Identity.
In this video, we’ll walk through how to create risk policies in Beyond Identity. First, admins will log in to the Beyond Identity Console.
Note: there isn't a password to log in. Admins use their Beyond Identity Authenticator and credentials on their device, which means only your admin's registered devices can access the admin console.
Now, click on the policy tab. So admins can determine if a user and a device meets their security requirements and whether they should be allowed to access company resources or not. There are policies for authentication and the types of policies that are allowed to add the Beyond Identity Authenticator.
For policies, rules execute in consecutive order, from top to bottom, and admins can drag and reorder rules. There's a variety of granular risk signals that admins can use to build policies. Admins can choose to approve, ask for additional verification or step up, or deny authentication.
Common risk policies
We're going to walk through some common risk policies that customers create. The first policy we’re going to walk through is to check a user’s computer to make sure they have their firewall on before allowing them to authenticate.
The policy is set so that if firewall is on, it will allow the user in. If the firewall is off, it will deny the user. So let's turn off firewall. And so the user is not authorized.
So let's turn the firewall on and try again. Now we're in.
Another common occurrence is for admins to enable step-up authentication in high-risk situations as defined by the company. For example, if a user is logging in from an unmanaged device, admins can ask the user for a step up verification such as an OS biometric verification to get access.
Now let's see this step up in action. The user requests access, they’re asked for a step-up biometric, and now they’re in.
The last policy we’re going to walk through is if companies don’t want to allow users to add the Authenticator to their mobile device, they can restrict which operating systems are allowed to add an authenticator. They can create a rule that says if this is an iOS device, then users are not allowed to set up their credentials on that device.
So let’s see that in action. Here, an iPhone is opened and they’re trying to set up their credentials, and they’re unable to. The rule executed successfully.
This was a quick overview of a few types of risk access policies you can configure in Beyond Identity.






.png)






.avif)



.avif)






.avif)

