What's FIDO?
If the name FIDO conjures up a generic-looking dog who lives in a generic-looking house in suburbia, think again. FIDO stands for Fast IDentity Online and is an open industry association that oversees the development and publication of strong passwordless authentication standards using public-private key cryptography.
The organization’s most recent publication is the FIDO2 specifications. FIDO2 is comprised of W3C’s Web Authentication (WebAuthn) and FIDO Alliance’s Client to Authenticator Protocol (CTAP).
Taken together, FIDO2 enables users to leverage devices they already have to authenticate to online services without the friction of passwords and with much higher security than passwords and SMS OTPs (one-time passcodes).
How does FIDO work?
FIDO authentication uses public-private key cryptography. When a user registers with an application, the user's device creates a new key pair (also called a passkey). The user's device stores the private key and the corresponding public key is sent to the online service.
When the user wants to log in, the device presents the private key created during registration to sign the authentication challenge which provides the possession factor. The private key can be used only if the user is able to unlock their device with a local biometric, PIN, or external device (e.g. Yubikey or biometric reader) which provides an inherence factor.
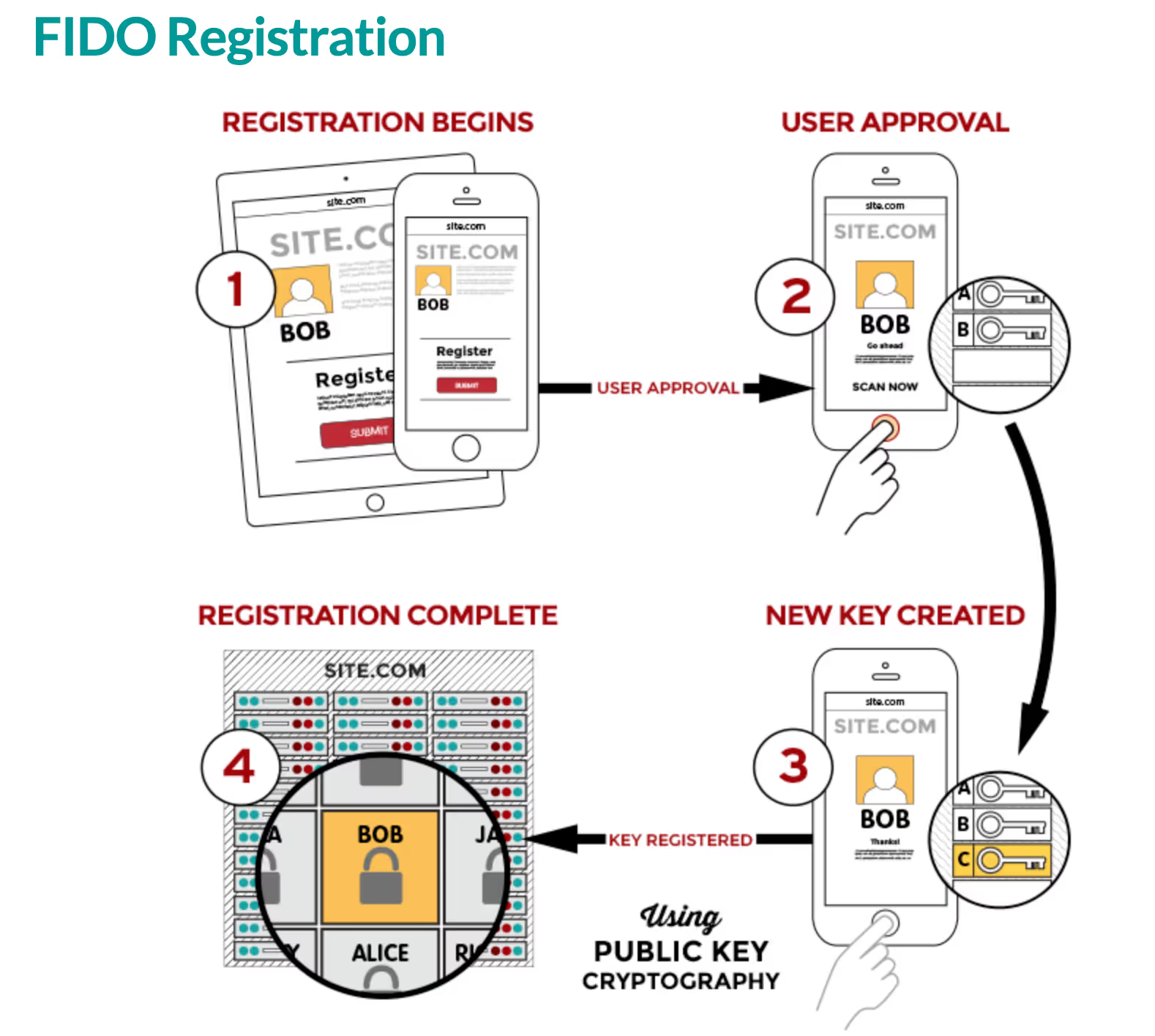
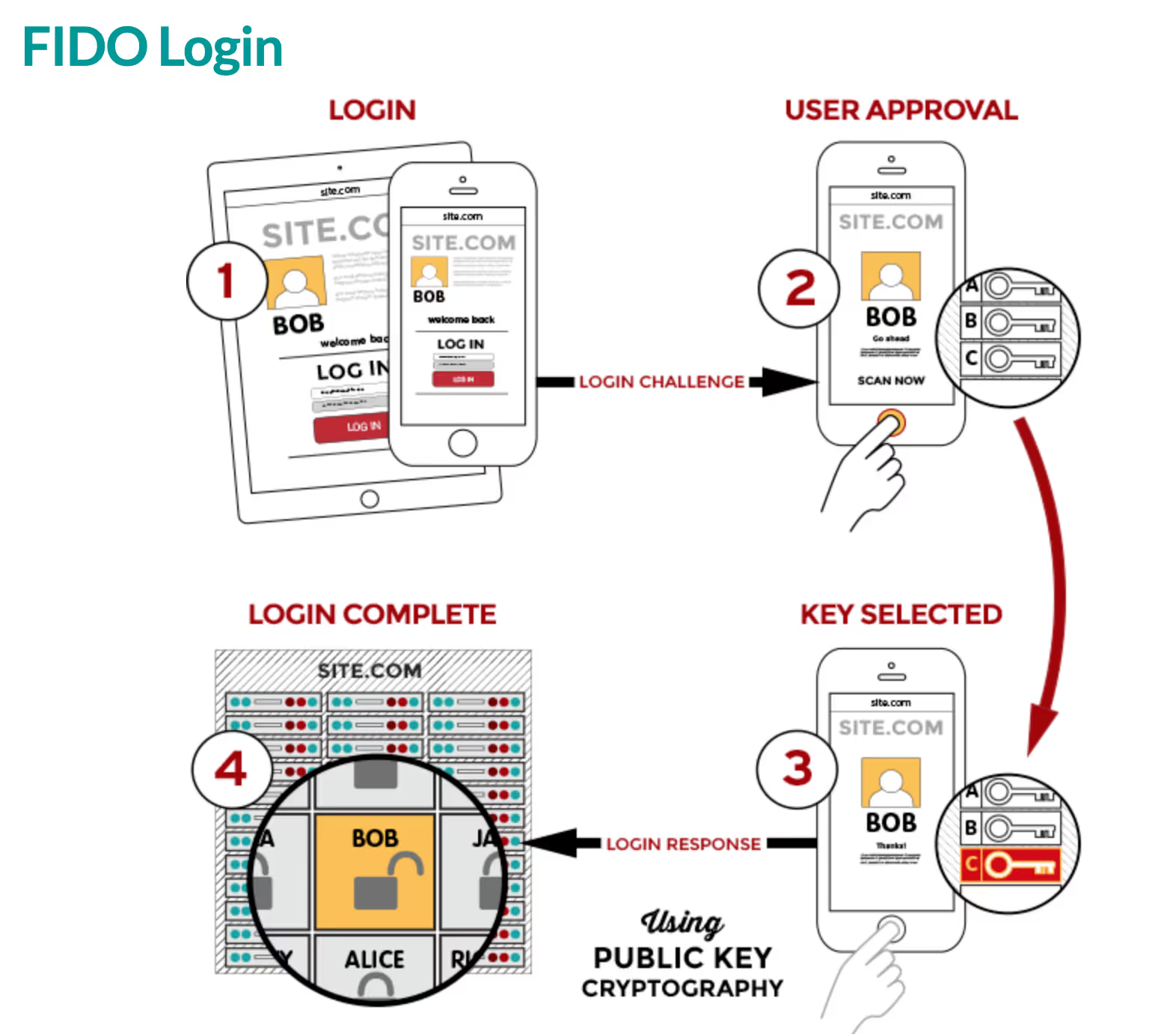
Key concepts in FIDO
Authenticator: Authenticators are hardware that a user owns which is able to perform user verification as well as generation and use of the cryptographic material required for authentication. There are two types of authenticators:
- Roaming authenticator: a separate device from the user's first device. Roaming authenticators are also called cross-platform authenticators because they can be used on multiple devices. They leverage mechanisms such as direct USB connection, Bluetooth, or near-field communication (NFC). For example, I can use my Yubikey as a roaming authenticator by plugging it into my laptop's USB port.
- Platform authenticator: authenticator that is built-in to the user's device. This is commonly available on all modern OS platforms including MacOS, Windows, iOS, and Android. Platform authenticators only work on the same device that the user is logging in from. An example of a platform authenticator in action is if I use Apple Touch ID to authenticate into my passkey-enabled account.
Relying party: servers that broker requests for access into resources. It sends a challenge and credential identifier to the browser.
WebAuthn: browser JS API defining interface for creating and using FIDO credentials. It is one component of the FIDO2 protocol.
CTAP: stands for Client to Authenticator Protocols which defines how to communicate with authenticators over Bluetooth, NFC, and USB. CTAP includes both CTAP1 and CTAP2. CTAP is the other component of the FIDO2 protocol.
Why FIDO?
You might be asking yourself, why should I take on the work of implementing FIDO now? There are multiple compelling reasons:
- Users don’t need to create, maintain, and reset passwords at all leading to higher conversions.
- Credentials are not stored on the server, meaning your users cannot get spoofed or otherwise compromised by a hacker finding a way into your system.
- All token handling as well as your customer’s private key are contained within the Authenticator itself, even when there’s some transaction text that needs to be shown and accepted by them. Malware cannot emulate the pressing of a button, the scan of a face, or a swipe of a fingerprint.
- It’s a Challenge/Response-based exchange that employs SSH and is done with public key cryptography and short-lived codes so it’s highly secure.
Implementing FIDO authentication can be difficult for developers. Beyond Identity offers the easiest way to implement FIDO2 Universal Passkeys in both your web and native applications to enable passwordless experiences no matter what browser, device, or application your users are on.
If the name FIDO conjures up a generic-looking dog who lives in a generic-looking house in suburbia, think again. FIDO stands for Fast IDentity Online and is an open industry association that oversees the development and publication of strong passwordless authentication standards using public-private key cryptography.
The organization’s most recent publication is the FIDO2 specifications. FIDO2 is comprised of W3C’s Web Authentication (WebAuthn) and FIDO Alliance’s Client to Authenticator Protocol (CTAP).
Taken together, FIDO2 enables users to leverage devices they already have to authenticate to online services without the friction of passwords and with much higher security than passwords and SMS OTPs (one-time passcodes).
How does FIDO work?
FIDO authentication uses public-private key cryptography. When a user registers with an application, the user's device creates a new key pair (also called a passkey). The user's device stores the private key and the corresponding public key is sent to the online service.
When the user wants to log in, the device presents the private key created during registration to sign the authentication challenge which provides the possession factor. The private key can be used only if the user is able to unlock their device with a local biometric, PIN, or external device (e.g. Yubikey or biometric reader) which provides an inherence factor.


Key concepts in FIDO
Authenticator: Authenticators are hardware that a user owns which is able to perform user verification as well as generation and use of the cryptographic material required for authentication. There are two types of authenticators:
- Roaming authenticator: a separate device from the user's first device. Roaming authenticators are also called cross-platform authenticators because they can be used on multiple devices. They leverage mechanisms such as direct USB connection, Bluetooth, or near-field communication (NFC). For example, I can use my Yubikey as a roaming authenticator by plugging it into my laptop's USB port.
- Platform authenticator: authenticator that is built-in to the user's device. This is commonly available on all modern OS platforms including MacOS, Windows, iOS, and Android. Platform authenticators only work on the same device that the user is logging in from. An example of a platform authenticator in action is if I use Apple Touch ID to authenticate into my passkey-enabled account.
Relying party: servers that broker requests for access into resources. It sends a challenge and credential identifier to the browser.
WebAuthn: browser JS API defining interface for creating and using FIDO credentials. It is one component of the FIDO2 protocol.
CTAP: stands for Client to Authenticator Protocols which defines how to communicate with authenticators over Bluetooth, NFC, and USB. CTAP includes both CTAP1 and CTAP2. CTAP is the other component of the FIDO2 protocol.
Why FIDO?
You might be asking yourself, why should I take on the work of implementing FIDO now? There are multiple compelling reasons:
- Users don’t need to create, maintain, and reset passwords at all leading to higher conversions.
- Credentials are not stored on the server, meaning your users cannot get spoofed or otherwise compromised by a hacker finding a way into your system.
- All token handling as well as your customer’s private key are contained within the Authenticator itself, even when there’s some transaction text that needs to be shown and accepted by them. Malware cannot emulate the pressing of a button, the scan of a face, or a swipe of a fingerprint.
- It’s a Challenge/Response-based exchange that employs SSH and is done with public key cryptography and short-lived codes so it’s highly secure.
Implementing FIDO authentication can be difficult for developers. Beyond Identity offers the easiest way to implement FIDO2 Universal Passkeys in both your web and native applications to enable passwordless experiences no matter what browser, device, or application your users are on.
If the name FIDO conjures up a generic-looking dog who lives in a generic-looking house in suburbia, think again. FIDO stands for Fast IDentity Online and is an open industry association that oversees the development and publication of strong passwordless authentication standards using public-private key cryptography.
The organization’s most recent publication is the FIDO2 specifications. FIDO2 is comprised of W3C’s Web Authentication (WebAuthn) and FIDO Alliance’s Client to Authenticator Protocol (CTAP).
Taken together, FIDO2 enables users to leverage devices they already have to authenticate to online services without the friction of passwords and with much higher security than passwords and SMS OTPs (one-time passcodes).
How does FIDO work?
FIDO authentication uses public-private key cryptography. When a user registers with an application, the user's device creates a new key pair (also called a passkey). The user's device stores the private key and the corresponding public key is sent to the online service.
When the user wants to log in, the device presents the private key created during registration to sign the authentication challenge which provides the possession factor. The private key can be used only if the user is able to unlock their device with a local biometric, PIN, or external device (e.g. Yubikey or biometric reader) which provides an inherence factor.


Key concepts in FIDO
Authenticator: Authenticators are hardware that a user owns which is able to perform user verification as well as generation and use of the cryptographic material required for authentication. There are two types of authenticators:
- Roaming authenticator: a separate device from the user's first device. Roaming authenticators are also called cross-platform authenticators because they can be used on multiple devices. They leverage mechanisms such as direct USB connection, Bluetooth, or near-field communication (NFC). For example, I can use my Yubikey as a roaming authenticator by plugging it into my laptop's USB port.
- Platform authenticator: authenticator that is built-in to the user's device. This is commonly available on all modern OS platforms including MacOS, Windows, iOS, and Android. Platform authenticators only work on the same device that the user is logging in from. An example of a platform authenticator in action is if I use Apple Touch ID to authenticate into my passkey-enabled account.
Relying party: servers that broker requests for access into resources. It sends a challenge and credential identifier to the browser.
WebAuthn: browser JS API defining interface for creating and using FIDO credentials. It is one component of the FIDO2 protocol.
CTAP: stands for Client to Authenticator Protocols which defines how to communicate with authenticators over Bluetooth, NFC, and USB. CTAP includes both CTAP1 and CTAP2. CTAP is the other component of the FIDO2 protocol.
Why FIDO?
You might be asking yourself, why should I take on the work of implementing FIDO now? There are multiple compelling reasons:
- Users don’t need to create, maintain, and reset passwords at all leading to higher conversions.
- Credentials are not stored on the server, meaning your users cannot get spoofed or otherwise compromised by a hacker finding a way into your system.
- All token handling as well as your customer’s private key are contained within the Authenticator itself, even when there’s some transaction text that needs to be shown and accepted by them. Malware cannot emulate the pressing of a button, the scan of a face, or a swipe of a fingerprint.
- It’s a Challenge/Response-based exchange that employs SSH and is done with public key cryptography and short-lived codes so it’s highly secure.
Implementing FIDO authentication can be difficult for developers. Beyond Identity offers the easiest way to implement FIDO2 Universal Passkeys in both your web and native applications to enable passwordless experiences no matter what browser, device, or application your users are on.







.png)






.avif)



.avif)






.avif)

