New: Secure Credential Extension Now Available in Secure Access
Attackers constantly look for new ways to exploit credentials, especially during high risk moments such as credential extension and recovery.
As part of our commitment to zero trust and secure by design principles, Beyond Identity has improved the passkey extension flow to proactively address emerging threats while keeping the user experience seamless.
Whether your users are onboarding a new laptop or adding a secondary mobile device, this update ensures every step is verified, every device is compliant, and every credential is protected.
What’s new in the enhanced credential extension flow?
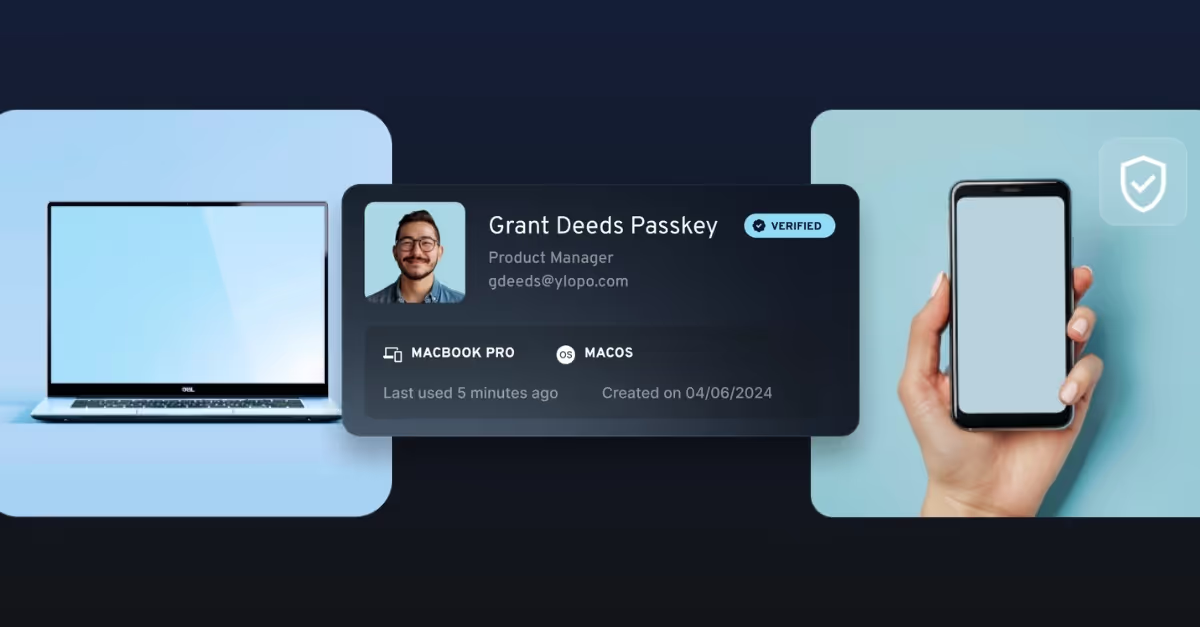
The key update: credential extension now begins on the untrusted device.
Instead of initiating from a trusted device and pushing passkeys out, Beyond Identity Secure Access reverses the process:
- The new device initiates enrollment and generates a one-time QR or 9-digit code: This ensures that the new device is physically present and under the user’s control.
- The user enters that code into an existing trusted device: The trusted device will only respond to explicit requests from a device that a user has authorized instead of pushing passkeys out.
- Both devices are evaluated for security compliance: If one doesn’t meet your policy, the passkey cannot be extended. This is an existing feature that continues to be enforced in the updated credential extension flow.
- The trust device validates the request, and upon successful policy evaluation, a new passkey is created
The user maintains their ability to extend their credentials without contacting IT. IT maintains secure credential operations by default. That’s what we call a win-win.
See it in action!
You can check out the user flow in this video or contact us to get a custom demo.
If you’re an existing Beyond Identity customer, please reach out to your customer support representative to test and deploy this feature for your environment. Or you can check out the documentation for Secure Access or Secure Work.
Attackers constantly look for new ways to exploit credentials, especially during high risk moments such as credential extension and recovery.
As part of our commitment to zero trust and secure by design principles, Beyond Identity has improved the passkey extension flow to proactively address emerging threats while keeping the user experience seamless.
Whether your users are onboarding a new laptop or adding a secondary mobile device, this update ensures every step is verified, every device is compliant, and every credential is protected.
What’s new in the enhanced credential extension flow?
The key update: credential extension now begins on the untrusted device.
Instead of initiating from a trusted device and pushing passkeys out, Beyond Identity Secure Access reverses the process:
- The new device initiates enrollment and generates a one-time QR or 9-digit code: This ensures that the new device is physically present and under the user’s control.
- The user enters that code into an existing trusted device: The trusted device will only respond to explicit requests from a device that a user has authorized instead of pushing passkeys out.
- Both devices are evaluated for security compliance: If one doesn’t meet your policy, the passkey cannot be extended. This is an existing feature that continues to be enforced in the updated credential extension flow.
- The trust device validates the request, and upon successful policy evaluation, a new passkey is created
The user maintains their ability to extend their credentials without contacting IT. IT maintains secure credential operations by default. That’s what we call a win-win.
See it in action!
You can check out the user flow in this video or contact us to get a custom demo.
If you’re an existing Beyond Identity customer, please reach out to your customer support representative to test and deploy this feature for your environment. Or you can check out the documentation for Secure Access or Secure Work.
Attackers constantly look for new ways to exploit credentials, especially during high risk moments such as credential extension and recovery.
As part of our commitment to zero trust and secure by design principles, Beyond Identity has improved the passkey extension flow to proactively address emerging threats while keeping the user experience seamless.
Whether your users are onboarding a new laptop or adding a secondary mobile device, this update ensures every step is verified, every device is compliant, and every credential is protected.
What’s new in the enhanced credential extension flow?
The key update: credential extension now begins on the untrusted device.
Instead of initiating from a trusted device and pushing passkeys out, Beyond Identity Secure Access reverses the process:
- The new device initiates enrollment and generates a one-time QR or 9-digit code: This ensures that the new device is physically present and under the user’s control.
- The user enters that code into an existing trusted device: The trusted device will only respond to explicit requests from a device that a user has authorized instead of pushing passkeys out.
- Both devices are evaluated for security compliance: If one doesn’t meet your policy, the passkey cannot be extended. This is an existing feature that continues to be enforced in the updated credential extension flow.
- The trust device validates the request, and upon successful policy evaluation, a new passkey is created
The user maintains their ability to extend their credentials without contacting IT. IT maintains secure credential operations by default. That’s what we call a win-win.
See it in action!
You can check out the user flow in this video or contact us to get a custom demo.
If you’re an existing Beyond Identity customer, please reach out to your customer support representative to test and deploy this feature for your environment. Or you can check out the documentation for Secure Access or Secure Work.












.avif)
.avif)



.avif)






.avif)

