Cybersecurity Risks of Improper Offboarding After Layoffs
No company wants to make layoffs, but unfortunately, it happens. Economic headwinds can make it tough to do business, and redundancies may be inevitable. Other times, employees may simply move to new roles. But did you know that improperly offboarding an employee can be a potential security risk?
To find out more about offboarding practices and problems, we surveyed employers and employees who have experienced layoffs in the past six months. Read on to see how improper offboarding of laid-off employees can increase a business’s cybersecurity risk and how you can avoid it.
Key takeaways
- Nearly one-third of employers have suffered a website hack due to ineffective offboarding.
- Over 25% of employers had their companies’ reputations damaged due to ineffective offboarding.
- 91% of employees still have access to company files since offboarding earlier this year.
Employee offboarding checklist
Offboarding employees can mean different things depending on company policy. Let’s dive into the data to find out what it usually looks like for businesses.
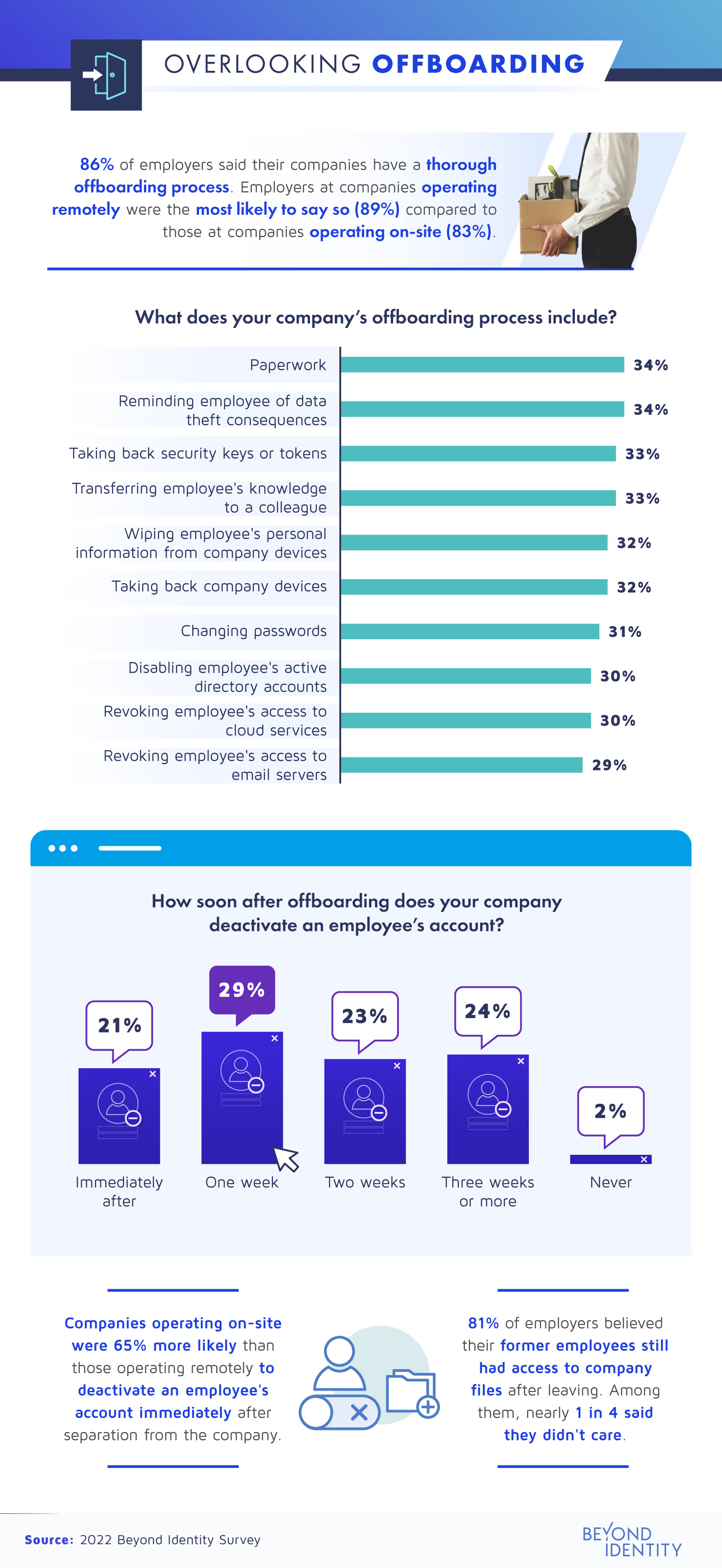
Although cloud and email services are channels where employees share sensitive data, some companies neglected to revoke laid-off employees’ access to them during offboarding. For example, nearly one-third (29%) said they don’t immediately cancel employees’ access to the company’s Google Workspace account after they leave the organization.
These oversights leave room for cybersecurity breaches, especially now that cyberattacks are increasingly seen as dangerous to businesses.
Employee offboarding gone wrong
Improper offboarding comes with consequences. Let’s take a look at the costs it can incur.
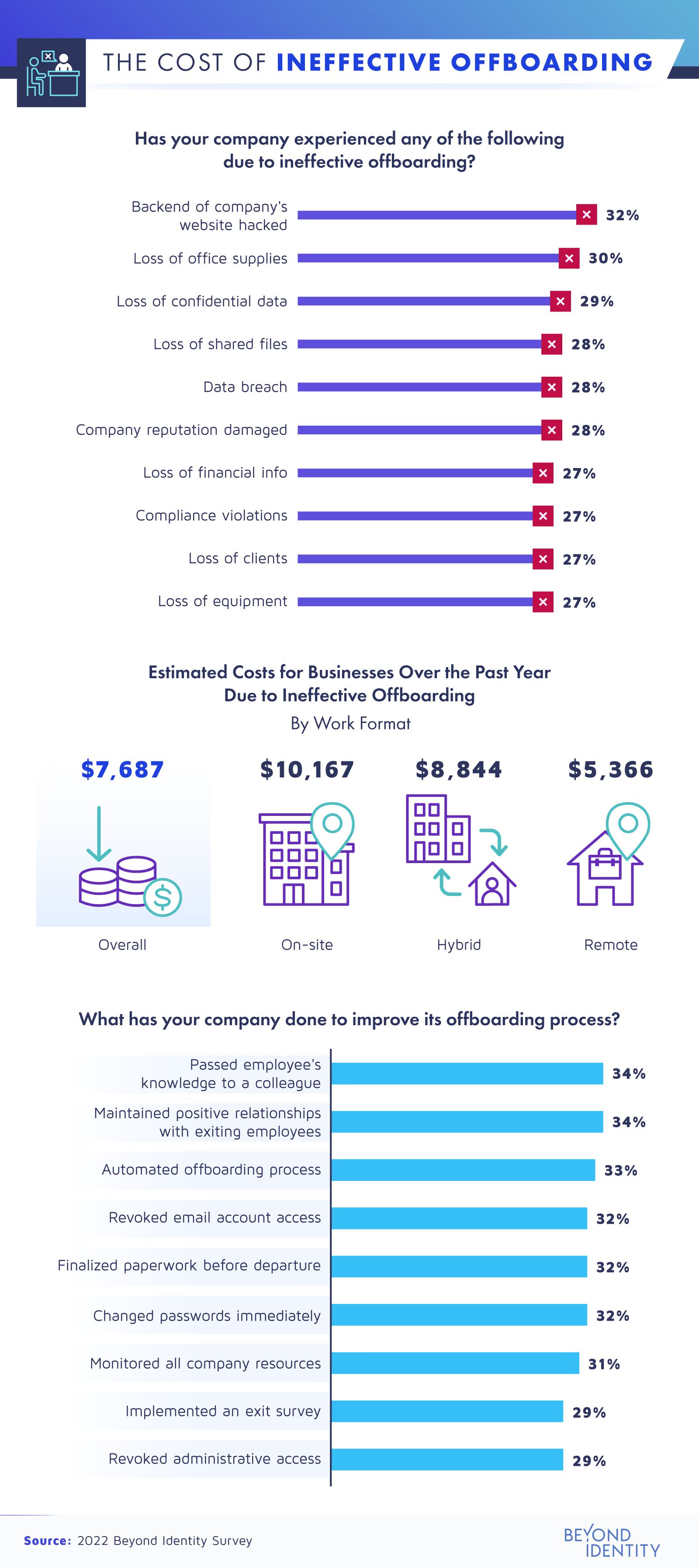
Ineffective offboarding after a layoff most commonly resulted in businesses having the backend of their websites hacked (32%), office supplies stolen (30%), and data or files lost (29%) or breached (28%). Over half of the results had to do with cybersecurity.
With a data breach in the U.S. costing $9.44 million on average, the need to effectively offboard employees is critical. To see what poor offboarding cost our respondents, we asked employers to share how much they’ve spent to fix things in the past year. The average expenditure was about $7,700. Companies with on-site or hybrid operations reported above-average losses, $10,167 and $8,844, respectively.
Fortunately, our survey also shows that businesses can do more to decrease these risks. For instance, 29% of respondents have begun revoking administrative access as part of their offboarding process. Although this security improvement has been implemented by the fewest companies we surveyed, revoking access to and deactivating these accounts could save them thousands of dollars.
Cutting ties the wrong way
Sometimes, employees and employers don’t see eye-to-eye, which can affect how they handle the offboarding process during layoffs. Next, we asked employees how they reacted to their offboarding experiences.
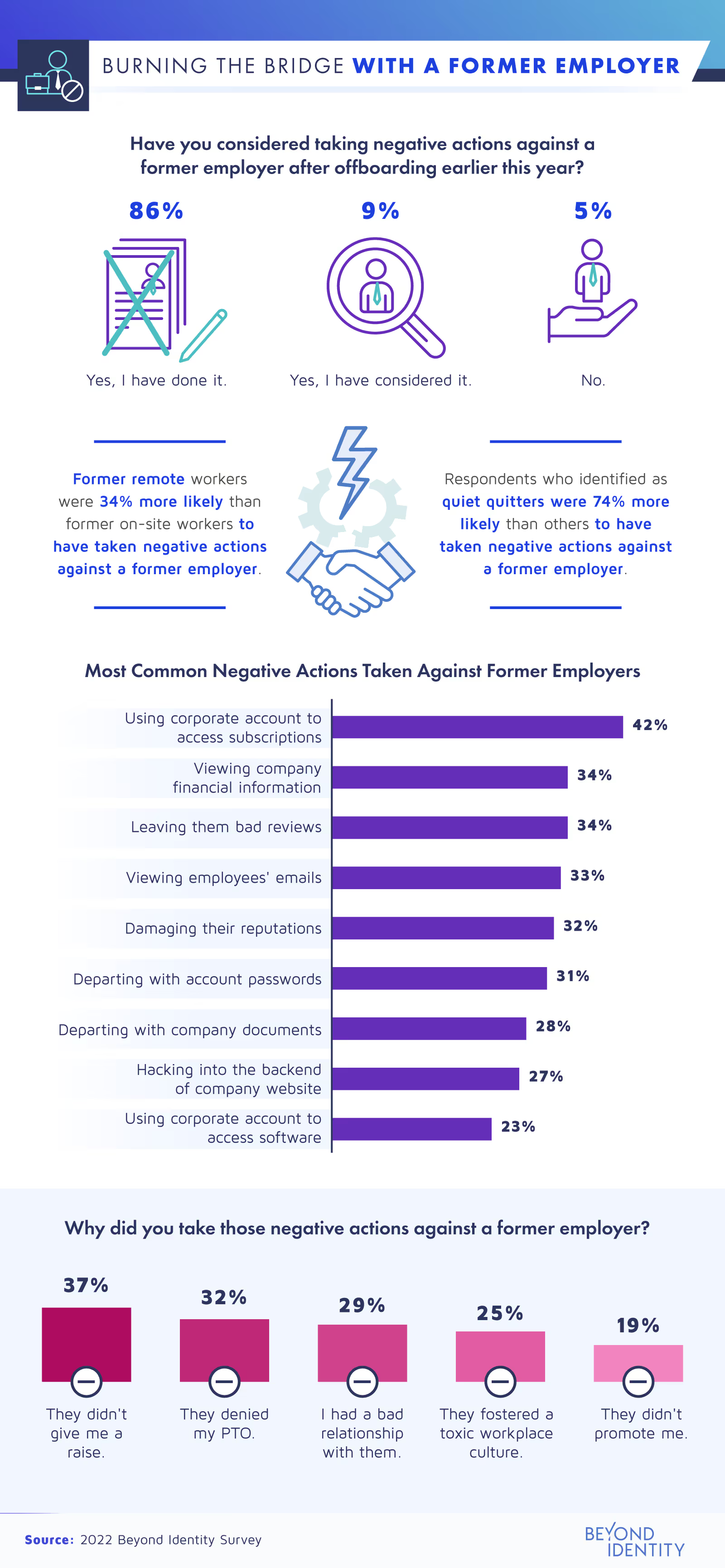
Of all the negative actions taken against former employers, companies could have avoided more than half if the laid-off employee no longer had access to their work accounts. The most common retaliation was using a work account to access subscription services (42%). But many also viewed other employees’ emails (33%) and, shockingly, hacked their former employers’ websites (27%).
These behaviors may relate to the Great Resignation—the current phenomenon of employees leaving their companies for better pay and treatment. Specifically, we found that these reactions were usually due to an employee grievance against their former employer, such as not receiving a raise (37%) or being denied paid time off (32%). Interestingly, male employees (90%) were also more likely than female employees (75%) to try to harm their former company.
Age may also have something to do with retaliation after a layoff, with younger generations perhaps being more sensitive to these employer wrongdoings. We found that the most negative actions were taken by Gen Zers (92%) and millennials (88%), compared to just 67% of Gen Xers. Regardless of their employees’ ages, managers would do well to do frequent checks on current employee satisfaction in addition to increasing their security procedures during offboarding.
Bad practices after offboarding
Businesses make some common mistakes when offboarding laid-off employees, and avoiding them could decrease cybersecurity risks. Here are some areas that companies may want to focus on and improve.
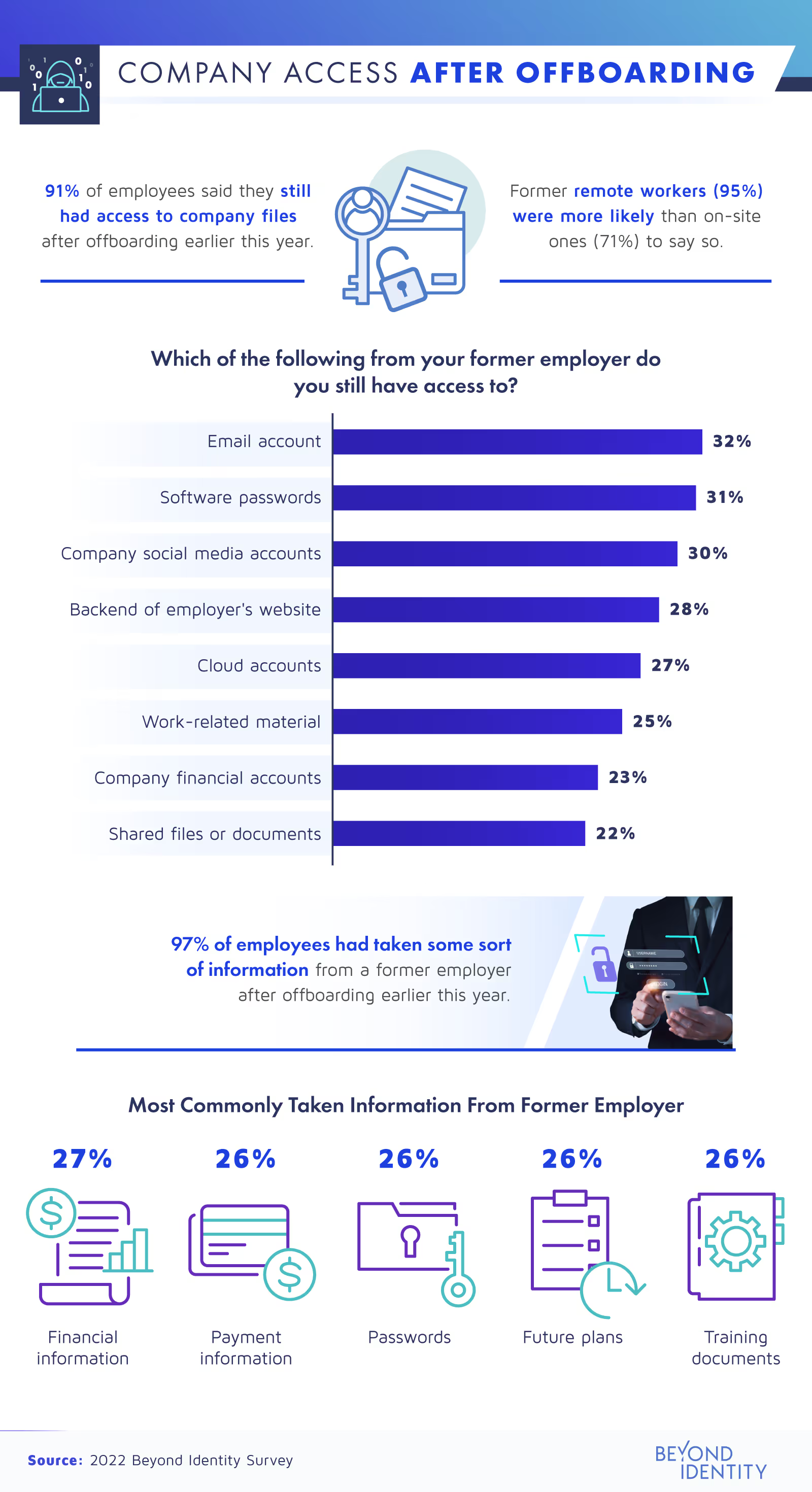
The most common offboarding oversights involved neglecting to revoke access to work-related IT accounts and services. According to recently laid-off employees, many still had access to their former company’s email (32%), software (31%), and social media accounts (30%) after being let go.
Even more alarming, nearly one-quarter (23%) said they can still access company financial information, which could lead to expensive data leaks. The data taken most often by laid-of employees involved money: 27% have taken financial information, and 26% have taken payment data.
These offboarding issues not only put businesses at risk but also the customers and business partners who have entrusted them with their data. Considering that more than one-third of businesses (34%) experience some form of insider-related cybersecurity incident every year, improving offboarding procedures could make a big difference.
Making offboarding easy
With the lack of attention given to offboarding when employees are laid off, it’s no surprise that many companies have suffered a website hack after a worker left the company. Even though some employers are revoking access to former employees’ accounts once they depart, many aren’t doing it fast enough.
Employees may find themselves at odds with an employer for a myriad of personal grievances (especially if they’ve been let go) but that shouldn’t result in data breaches, hacking, or the loss of financial information. Ensuring employees’ work accounts are deactivated (and swiftly) will help keep company data, systems, and information secure.
Methodology
For this campaign, we surveyed 1,009 employers and 207 employees. Among employees, 71% were men, and 29% were women. The generational breakdown was as follows: 24% Gen Z, 57% millennials, 16% Gen X, and 3% baby boomers. Among employers, 62% were men, and 38% were women. The generational breakdown was as follows: 21% Gen Z, 34% millennials, 31% Gen X, and 13% baby boomers.
About Beyond Identity
The FIDO2 certified leader in phishing-resistant and passwordless MFA, Beyond Identity allows organizations to eliminate friction during the authentication process and removes all phishable factors while ensuring only authorized users using secure devices can gain access.
Fair use statement
Readers can share these findings for any noncommercial purpose. We only ask that you provide a link back to this page in doing so.
No company wants to make layoffs, but unfortunately, it happens. Economic headwinds can make it tough to do business, and redundancies may be inevitable. Other times, employees may simply move to new roles. But did you know that improperly offboarding an employee can be a potential security risk?
To find out more about offboarding practices and problems, we surveyed employers and employees who have experienced layoffs in the past six months. Read on to see how improper offboarding of laid-off employees can increase a business’s cybersecurity risk and how you can avoid it.
Key takeaways
- Nearly one-third of employers have suffered a website hack due to ineffective offboarding.
- Over 25% of employers had their companies’ reputations damaged due to ineffective offboarding.
- 91% of employees still have access to company files since offboarding earlier this year.
Employee offboarding checklist
Offboarding employees can mean different things depending on company policy. Let’s dive into the data to find out what it usually looks like for businesses.

Although cloud and email services are channels where employees share sensitive data, some companies neglected to revoke laid-off employees’ access to them during offboarding. For example, nearly one-third (29%) said they don’t immediately cancel employees’ access to the company’s Google Workspace account after they leave the organization.
These oversights leave room for cybersecurity breaches, especially now that cyberattacks are increasingly seen as dangerous to businesses.
Employee offboarding gone wrong
Improper offboarding comes with consequences. Let’s take a look at the costs it can incur.

Ineffective offboarding after a layoff most commonly resulted in businesses having the backend of their websites hacked (32%), office supplies stolen (30%), and data or files lost (29%) or breached (28%). Over half of the results had to do with cybersecurity.
With a data breach in the U.S. costing $9.44 million on average, the need to effectively offboard employees is critical. To see what poor offboarding cost our respondents, we asked employers to share how much they’ve spent to fix things in the past year. The average expenditure was about $7,700. Companies with on-site or hybrid operations reported above-average losses, $10,167 and $8,844, respectively.
Fortunately, our survey also shows that businesses can do more to decrease these risks. For instance, 29% of respondents have begun revoking administrative access as part of their offboarding process. Although this security improvement has been implemented by the fewest companies we surveyed, revoking access to and deactivating these accounts could save them thousands of dollars.
Cutting ties the wrong way
Sometimes, employees and employers don’t see eye-to-eye, which can affect how they handle the offboarding process during layoffs. Next, we asked employees how they reacted to their offboarding experiences.

Of all the negative actions taken against former employers, companies could have avoided more than half if the laid-off employee no longer had access to their work accounts. The most common retaliation was using a work account to access subscription services (42%). But many also viewed other employees’ emails (33%) and, shockingly, hacked their former employers’ websites (27%).
These behaviors may relate to the Great Resignation—the current phenomenon of employees leaving their companies for better pay and treatment. Specifically, we found that these reactions were usually due to an employee grievance against their former employer, such as not receiving a raise (37%) or being denied paid time off (32%). Interestingly, male employees (90%) were also more likely than female employees (75%) to try to harm their former company.
Age may also have something to do with retaliation after a layoff, with younger generations perhaps being more sensitive to these employer wrongdoings. We found that the most negative actions were taken by Gen Zers (92%) and millennials (88%), compared to just 67% of Gen Xers. Regardless of their employees’ ages, managers would do well to do frequent checks on current employee satisfaction in addition to increasing their security procedures during offboarding.
Bad practices after offboarding
Businesses make some common mistakes when offboarding laid-off employees, and avoiding them could decrease cybersecurity risks. Here are some areas that companies may want to focus on and improve.

The most common offboarding oversights involved neglecting to revoke access to work-related IT accounts and services. According to recently laid-off employees, many still had access to their former company’s email (32%), software (31%), and social media accounts (30%) after being let go.
Even more alarming, nearly one-quarter (23%) said they can still access company financial information, which could lead to expensive data leaks. The data taken most often by laid-of employees involved money: 27% have taken financial information, and 26% have taken payment data.
These offboarding issues not only put businesses at risk but also the customers and business partners who have entrusted them with their data. Considering that more than one-third of businesses (34%) experience some form of insider-related cybersecurity incident every year, improving offboarding procedures could make a big difference.
Making offboarding easy
With the lack of attention given to offboarding when employees are laid off, it’s no surprise that many companies have suffered a website hack after a worker left the company. Even though some employers are revoking access to former employees’ accounts once they depart, many aren’t doing it fast enough.
Employees may find themselves at odds with an employer for a myriad of personal grievances (especially if they’ve been let go) but that shouldn’t result in data breaches, hacking, or the loss of financial information. Ensuring employees’ work accounts are deactivated (and swiftly) will help keep company data, systems, and information secure.
Methodology
For this campaign, we surveyed 1,009 employers and 207 employees. Among employees, 71% were men, and 29% were women. The generational breakdown was as follows: 24% Gen Z, 57% millennials, 16% Gen X, and 3% baby boomers. Among employers, 62% were men, and 38% were women. The generational breakdown was as follows: 21% Gen Z, 34% millennials, 31% Gen X, and 13% baby boomers.
About Beyond Identity
The FIDO2 certified leader in phishing-resistant and passwordless MFA, Beyond Identity allows organizations to eliminate friction during the authentication process and removes all phishable factors while ensuring only authorized users using secure devices can gain access.
Fair use statement
Readers can share these findings for any noncommercial purpose. We only ask that you provide a link back to this page in doing so.
No company wants to make layoffs, but unfortunately, it happens. Economic headwinds can make it tough to do business, and redundancies may be inevitable. Other times, employees may simply move to new roles. But did you know that improperly offboarding an employee can be a potential security risk?
To find out more about offboarding practices and problems, we surveyed employers and employees who have experienced layoffs in the past six months. Read on to see how improper offboarding of laid-off employees can increase a business’s cybersecurity risk and how you can avoid it.
Key takeaways
- Nearly one-third of employers have suffered a website hack due to ineffective offboarding.
- Over 25% of employers had their companies’ reputations damaged due to ineffective offboarding.
- 91% of employees still have access to company files since offboarding earlier this year.
Employee offboarding checklist
Offboarding employees can mean different things depending on company policy. Let’s dive into the data to find out what it usually looks like for businesses.

Although cloud and email services are channels where employees share sensitive data, some companies neglected to revoke laid-off employees’ access to them during offboarding. For example, nearly one-third (29%) said they don’t immediately cancel employees’ access to the company’s Google Workspace account after they leave the organization.
These oversights leave room for cybersecurity breaches, especially now that cyberattacks are increasingly seen as dangerous to businesses.
Employee offboarding gone wrong
Improper offboarding comes with consequences. Let’s take a look at the costs it can incur.

Ineffective offboarding after a layoff most commonly resulted in businesses having the backend of their websites hacked (32%), office supplies stolen (30%), and data or files lost (29%) or breached (28%). Over half of the results had to do with cybersecurity.
With a data breach in the U.S. costing $9.44 million on average, the need to effectively offboard employees is critical. To see what poor offboarding cost our respondents, we asked employers to share how much they’ve spent to fix things in the past year. The average expenditure was about $7,700. Companies with on-site or hybrid operations reported above-average losses, $10,167 and $8,844, respectively.
Fortunately, our survey also shows that businesses can do more to decrease these risks. For instance, 29% of respondents have begun revoking administrative access as part of their offboarding process. Although this security improvement has been implemented by the fewest companies we surveyed, revoking access to and deactivating these accounts could save them thousands of dollars.
Cutting ties the wrong way
Sometimes, employees and employers don’t see eye-to-eye, which can affect how they handle the offboarding process during layoffs. Next, we asked employees how they reacted to their offboarding experiences.

Of all the negative actions taken against former employers, companies could have avoided more than half if the laid-off employee no longer had access to their work accounts. The most common retaliation was using a work account to access subscription services (42%). But many also viewed other employees’ emails (33%) and, shockingly, hacked their former employers’ websites (27%).
These behaviors may relate to the Great Resignation—the current phenomenon of employees leaving their companies for better pay and treatment. Specifically, we found that these reactions were usually due to an employee grievance against their former employer, such as not receiving a raise (37%) or being denied paid time off (32%). Interestingly, male employees (90%) were also more likely than female employees (75%) to try to harm their former company.
Age may also have something to do with retaliation after a layoff, with younger generations perhaps being more sensitive to these employer wrongdoings. We found that the most negative actions were taken by Gen Zers (92%) and millennials (88%), compared to just 67% of Gen Xers. Regardless of their employees’ ages, managers would do well to do frequent checks on current employee satisfaction in addition to increasing their security procedures during offboarding.
Bad practices after offboarding
Businesses make some common mistakes when offboarding laid-off employees, and avoiding them could decrease cybersecurity risks. Here are some areas that companies may want to focus on and improve.

The most common offboarding oversights involved neglecting to revoke access to work-related IT accounts and services. According to recently laid-off employees, many still had access to their former company’s email (32%), software (31%), and social media accounts (30%) after being let go.
Even more alarming, nearly one-quarter (23%) said they can still access company financial information, which could lead to expensive data leaks. The data taken most often by laid-of employees involved money: 27% have taken financial information, and 26% have taken payment data.
These offboarding issues not only put businesses at risk but also the customers and business partners who have entrusted them with their data. Considering that more than one-third of businesses (34%) experience some form of insider-related cybersecurity incident every year, improving offboarding procedures could make a big difference.
Making offboarding easy
With the lack of attention given to offboarding when employees are laid off, it’s no surprise that many companies have suffered a website hack after a worker left the company. Even though some employers are revoking access to former employees’ accounts once they depart, many aren’t doing it fast enough.
Employees may find themselves at odds with an employer for a myriad of personal grievances (especially if they’ve been let go) but that shouldn’t result in data breaches, hacking, or the loss of financial information. Ensuring employees’ work accounts are deactivated (and swiftly) will help keep company data, systems, and information secure.
Methodology
For this campaign, we surveyed 1,009 employers and 207 employees. Among employees, 71% were men, and 29% were women. The generational breakdown was as follows: 24% Gen Z, 57% millennials, 16% Gen X, and 3% baby boomers. Among employers, 62% were men, and 38% were women. The generational breakdown was as follows: 21% Gen Z, 34% millennials, 31% Gen X, and 13% baby boomers.
About Beyond Identity
The FIDO2 certified leader in phishing-resistant and passwordless MFA, Beyond Identity allows organizations to eliminate friction during the authentication process and removes all phishable factors while ensuring only authorized users using secure devices can gain access.
Fair use statement
Readers can share these findings for any noncommercial purpose. We only ask that you provide a link back to this page in doing so.







.png)






.avif)



.avif)






.avif)

