Closing the Gaps in Endpoint Security: Beyond Traditional Solutions
Technologists love a good acronym, and there are plenty to be found when it comes to securing enterprise endpoints. A new Beyond Identity white paper explores some of them—namely, endpoint detection and response(EDR), unified endpoint management (UEM), and managed detection and response (MDR).
Endpoints are growing exponentially in the enterprise, especially given the rise in remote work since the pandemic, and they are ripe for attacks. Gartner refers to endpoints as “your organization’s largest attack surface.”
Hackers use a number of techniques to infiltrate endpoints, including phishing, stealing credentials, software and hardware-based supplychain attacks, and ransomware attacks.
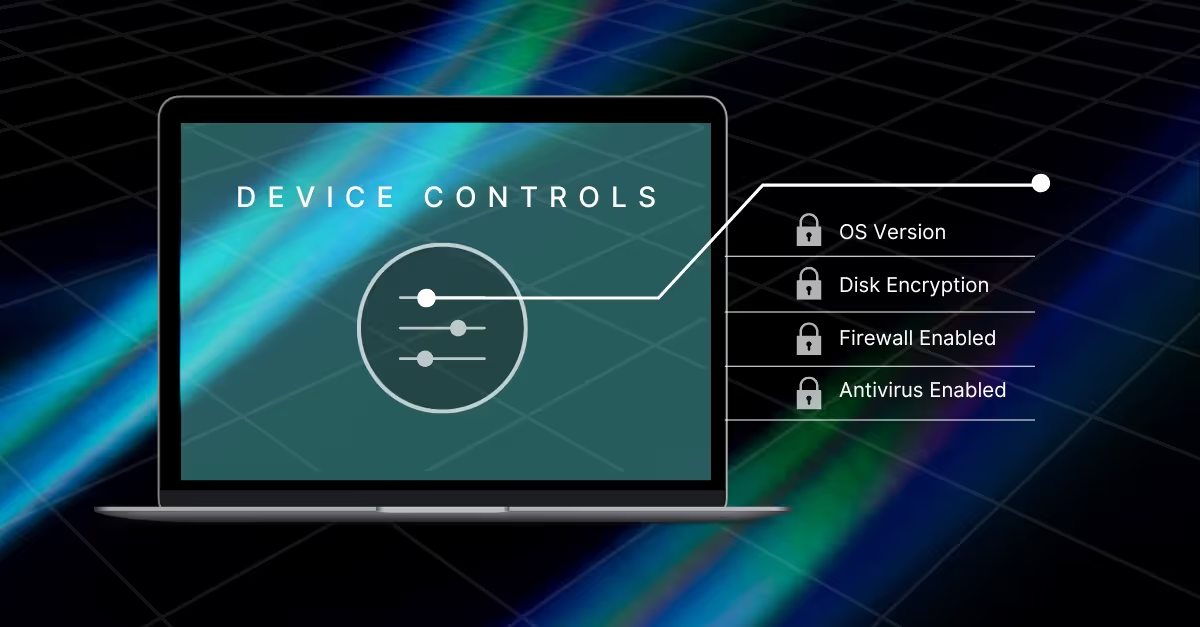
While protecting endpoints has never been more important,many solutions leave gaps, which may be giving organizations a false sense of security. Our white paper examines why antivirus software is no longer enough,and what some of the common gaps are, including device misconfigurations, unmanaged devices, and unique vulnerabilities that infiltrate specific devices due to user behavior.
We also discuss how organizations can improve their endpoint security. It starts with creating a framework that defines the risk acceptance criteria, critical risks, and residual risks, and identifies a starting point to measure the progress, according to Gartner.
The white paper also details the capabilities to look for in an endpoint protection solution. Key among them are continuous assessment of device security posture, ensuring real-time compliance with organizational security policies, and continuous monitoring of endpoints.
One of the big challenges organizations face is tool sprawl and security teams operating in silos with disparate endpoint solutions. This leads to unnecessary spending, increased risk, and more friction, which translates to a less-than-ideal digital employee experience.
Consolidating teams into a centralized endpoint team structure—and consolidating endpoint management platforms--will help improve operations and lead to a more mature endpoint management model, according to Gartner.
Another issue is that security teams are often working off endpoint management strategies that rely upon traditional multifactor authentication (MFA)that does not eliminate the use of passwords, which can be the most insecure part of the login process. Up to 80 percent of successful data breaches are duet o compromised passwords, according to Verizon’s annual Data Breach IndexReport. Eliminating passwords in the authentication process with phishing-resistant MFA increases security and improves the user experience.
Today, organizations need to improve efficiencies by implementing modern MFA. The benefits are continuous monitoring and phishing-resistant MFA that do not require passwords or assume an MDM tool is configured correctly.
Modern MFA allows for rapid response and adjustment in realtime as new information emerges. Besides continuous monitoring, it also incorporatesthreat hunting, and the flexibility to implement changes to security protocols in real time, especially on oft-moving and exposed assets like endpoints.
Further, adopting a zero-trust methodology is essential foreffective device control management. This approach ensures that no deviceis assumed secure based on past checks or compliances. This is critical forpreventing access to the corporate network from devices that could open doors to attackers.
For more on improving device controls, download our whitepaper today.
About the author: Esther Shein is a longtime freelance tech and business writer and editor whose work has appeared in several publications, including CIO.com, TechRepublic, VentureBeat, ZDNet, TechTarget, The Boston Globe and Inc. She has also written thought leadership whitepapers, ebooks, case studies and marketing materials.
Technologists love a good acronym, and there are plenty to be found when it comes to securing enterprise endpoints. A new Beyond Identity white paper explores some of them—namely, endpoint detection and response(EDR), unified endpoint management (UEM), and managed detection and response (MDR).
Endpoints are growing exponentially in the enterprise, especially given the rise in remote work since the pandemic, and they are ripe for attacks. Gartner refers to endpoints as “your organization’s largest attack surface.”
Hackers use a number of techniques to infiltrate endpoints, including phishing, stealing credentials, software and hardware-based supplychain attacks, and ransomware attacks.
While protecting endpoints has never been more important,many solutions leave gaps, which may be giving organizations a false sense of security. Our white paper examines why antivirus software is no longer enough,and what some of the common gaps are, including device misconfigurations, unmanaged devices, and unique vulnerabilities that infiltrate specific devices due to user behavior.
We also discuss how organizations can improve their endpoint security. It starts with creating a framework that defines the risk acceptance criteria, critical risks, and residual risks, and identifies a starting point to measure the progress, according to Gartner.
The white paper also details the capabilities to look for in an endpoint protection solution. Key among them are continuous assessment of device security posture, ensuring real-time compliance with organizational security policies, and continuous monitoring of endpoints.
One of the big challenges organizations face is tool sprawl and security teams operating in silos with disparate endpoint solutions. This leads to unnecessary spending, increased risk, and more friction, which translates to a less-than-ideal digital employee experience.
Consolidating teams into a centralized endpoint team structure—and consolidating endpoint management platforms--will help improve operations and lead to a more mature endpoint management model, according to Gartner.
Another issue is that security teams are often working off endpoint management strategies that rely upon traditional multifactor authentication (MFA)that does not eliminate the use of passwords, which can be the most insecure part of the login process. Up to 80 percent of successful data breaches are duet o compromised passwords, according to Verizon’s annual Data Breach IndexReport. Eliminating passwords in the authentication process with phishing-resistant MFA increases security and improves the user experience.
Today, organizations need to improve efficiencies by implementing modern MFA. The benefits are continuous monitoring and phishing-resistant MFA that do not require passwords or assume an MDM tool is configured correctly.
Modern MFA allows for rapid response and adjustment in realtime as new information emerges. Besides continuous monitoring, it also incorporatesthreat hunting, and the flexibility to implement changes to security protocols in real time, especially on oft-moving and exposed assets like endpoints.
Further, adopting a zero-trust methodology is essential foreffective device control management. This approach ensures that no deviceis assumed secure based on past checks or compliances. This is critical forpreventing access to the corporate network from devices that could open doors to attackers.
For more on improving device controls, download our whitepaper today.
About the author: Esther Shein is a longtime freelance tech and business writer and editor whose work has appeared in several publications, including CIO.com, TechRepublic, VentureBeat, ZDNet, TechTarget, The Boston Globe and Inc. She has also written thought leadership whitepapers, ebooks, case studies and marketing materials.
Technologists love a good acronym, and there are plenty to be found when it comes to securing enterprise endpoints. A new Beyond Identity white paper explores some of them—namely, endpoint detection and response(EDR), unified endpoint management (UEM), and managed detection and response (MDR).
Endpoints are growing exponentially in the enterprise, especially given the rise in remote work since the pandemic, and they are ripe for attacks. Gartner refers to endpoints as “your organization’s largest attack surface.”
Hackers use a number of techniques to infiltrate endpoints, including phishing, stealing credentials, software and hardware-based supplychain attacks, and ransomware attacks.
While protecting endpoints has never been more important,many solutions leave gaps, which may be giving organizations a false sense of security. Our white paper examines why antivirus software is no longer enough,and what some of the common gaps are, including device misconfigurations, unmanaged devices, and unique vulnerabilities that infiltrate specific devices due to user behavior.
We also discuss how organizations can improve their endpoint security. It starts with creating a framework that defines the risk acceptance criteria, critical risks, and residual risks, and identifies a starting point to measure the progress, according to Gartner.
The white paper also details the capabilities to look for in an endpoint protection solution. Key among them are continuous assessment of device security posture, ensuring real-time compliance with organizational security policies, and continuous monitoring of endpoints.
One of the big challenges organizations face is tool sprawl and security teams operating in silos with disparate endpoint solutions. This leads to unnecessary spending, increased risk, and more friction, which translates to a less-than-ideal digital employee experience.
Consolidating teams into a centralized endpoint team structure—and consolidating endpoint management platforms--will help improve operations and lead to a more mature endpoint management model, according to Gartner.
Another issue is that security teams are often working off endpoint management strategies that rely upon traditional multifactor authentication (MFA)that does not eliminate the use of passwords, which can be the most insecure part of the login process. Up to 80 percent of successful data breaches are duet o compromised passwords, according to Verizon’s annual Data Breach IndexReport. Eliminating passwords in the authentication process with phishing-resistant MFA increases security and improves the user experience.
Today, organizations need to improve efficiencies by implementing modern MFA. The benefits are continuous monitoring and phishing-resistant MFA that do not require passwords or assume an MDM tool is configured correctly.
Modern MFA allows for rapid response and adjustment in realtime as new information emerges. Besides continuous monitoring, it also incorporatesthreat hunting, and the flexibility to implement changes to security protocols in real time, especially on oft-moving and exposed assets like endpoints.
Further, adopting a zero-trust methodology is essential foreffective device control management. This approach ensures that no deviceis assumed secure based on past checks or compliances. This is critical forpreventing access to the corporate network from devices that could open doors to attackers.
For more on improving device controls, download our whitepaper today.
About the author: Esther Shein is a longtime freelance tech and business writer and editor whose work has appeared in several publications, including CIO.com, TechRepublic, VentureBeat, ZDNet, TechTarget, The Boston Globe and Inc. She has also written thought leadership whitepapers, ebooks, case studies and marketing materials.






.png)






.avif)



.avif)






.avif)

