A Look Inside Beyond Identity and Okta’s Passwordless Single Sign-On Integration
Go Passwordless Today
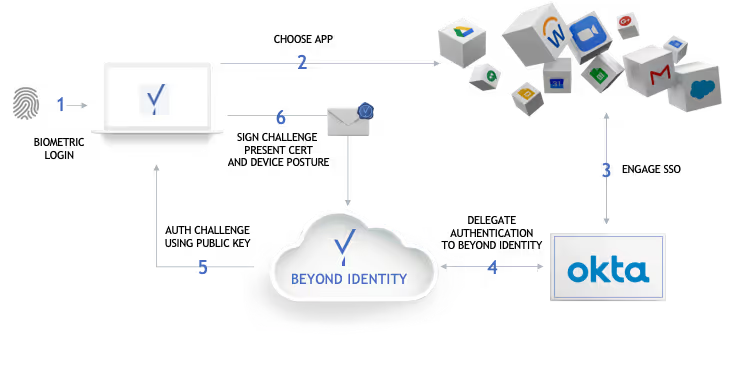
Beyond Identity’s integration helps companies solve the password problem in multiple places, including logging into desktops, the Okta SSO portal, and SSO-enabled applications. To register or login, users no longer need to create, remember, or change passwords. Beyond Identity eliminates passwords and replaces them with a secure authentication method.
To enroll in passwordless authentication, employees simply download the Beyond Identity App onto their device(s) and register their identity on the device. And that’s it! Employees can then securely login to apps with just a username (no password). Whichever app they’re requesting access to, delegates authentication to Okta, which then automatically validates the identity using Beyond Identity’s authenticator app installed on the device. Users can add multiple devices without help desk or IT support–reducing lockouts and help desk costs.
Improve Policies With Risk-based, Dynamic Authorization Decisions
As an added layer of security, administrators can create custom access policies in Beyond Identity’s Admin Portal. Organizations can implement adaptive-risk based authorization and control for which individuals and devices are allowed to access an application based on that device’s security posture at the time of login.
The Beyond Identity App provides 12+ security posture data elements from company-issued or personal (BYOD) devices without requiring 3rd party tools like a mobile device management (MDM) or endpoint detection and response (EDR).
Device security posture includes:
- OS Version
- Password protection status
- Biometric enablement status
- Secure enclave status
- Hard drive encryption status
- Firewall enablement status
- Gatekeeper enablement status
- And more!
Your team can build granular access controls and enforce risk-based authorization decisions based on the risk-level of users, devices, and apps. The ability to collect device security posture data is available in Beyond Identity’s App and does not require 3rd party tools or complicated integrations.
Security teams get real-time visibility into who’s coming across your perimeter and which device they are using and the security posture of the device at the time of each login transaction. The log data is stored in our data lake and as an immutable audit record–tying identities to devices to resources accessed and providing invaluable data for SOC and Audit/Compliance teams. The comprehensive audit data can also be integrated into GRC, SIEM, and other key security and risk management technologies.
Try it Today
It’s a seamless integration. It only takes a few configuration changes in your Okta environment and there’s no code-required. Simply add Beyond Identity as a delegated identity provider in your Okta environment and add an authentication routing rule. All of these features are built-in to the Beyond Identity cloud platform and do not require 3rd party tools or complicated integrations.
Choose Beyond Identity’s cloud-native solution for passwordless desktop, passwordless single sign-on, and device security posture for risk-based access decisions.
It’s time to fundamentally improve the way users login!
Go Passwordless Today
Beyond Identity’s integration helps companies solve the password problem in multiple places, including logging into desktops, the Okta SSO portal, and SSO-enabled applications. To register or login, users no longer need to create, remember, or change passwords. Beyond Identity eliminates passwords and replaces them with a secure authentication method.
To enroll in passwordless authentication, employees simply download the Beyond Identity App onto their device(s) and register their identity on the device. And that’s it! Employees can then securely login to apps with just a username (no password). Whichever app they’re requesting access to, delegates authentication to Okta, which then automatically validates the identity using Beyond Identity’s authenticator app installed on the device. Users can add multiple devices without help desk or IT support–reducing lockouts and help desk costs.
Improve Policies With Risk-based, Dynamic Authorization Decisions
As an added layer of security, administrators can create custom access policies in Beyond Identity’s Admin Portal. Organizations can implement adaptive-risk based authorization and control for which individuals and devices are allowed to access an application based on that device’s security posture at the time of login.
The Beyond Identity App provides 12+ security posture data elements from company-issued or personal (BYOD) devices without requiring 3rd party tools like a mobile device management (MDM) or endpoint detection and response (EDR).
Device security posture includes:
- OS Version
- Password protection status
- Biometric enablement status
- Secure enclave status
- Hard drive encryption status
- Firewall enablement status
- Gatekeeper enablement status
- And more!

Your team can build granular access controls and enforce risk-based authorization decisions based on the risk-level of users, devices, and apps. The ability to collect device security posture data is available in Beyond Identity’s App and does not require 3rd party tools or complicated integrations.
Security teams get real-time visibility into who’s coming across your perimeter and which device they are using and the security posture of the device at the time of each login transaction. The log data is stored in our data lake and as an immutable audit record–tying identities to devices to resources accessed and providing invaluable data for SOC and Audit/Compliance teams. The comprehensive audit data can also be integrated into GRC, SIEM, and other key security and risk management technologies.
Try it Today
It’s a seamless integration. It only takes a few configuration changes in your Okta environment and there’s no code-required. Simply add Beyond Identity as a delegated identity provider in your Okta environment and add an authentication routing rule. All of these features are built-in to the Beyond Identity cloud platform and do not require 3rd party tools or complicated integrations.
Choose Beyond Identity’s cloud-native solution for passwordless desktop, passwordless single sign-on, and device security posture for risk-based access decisions.
It’s time to fundamentally improve the way users login!
Go Passwordless Today
Beyond Identity’s integration helps companies solve the password problem in multiple places, including logging into desktops, the Okta SSO portal, and SSO-enabled applications. To register or login, users no longer need to create, remember, or change passwords. Beyond Identity eliminates passwords and replaces them with a secure authentication method.
To enroll in passwordless authentication, employees simply download the Beyond Identity App onto their device(s) and register their identity on the device. And that’s it! Employees can then securely login to apps with just a username (no password). Whichever app they’re requesting access to, delegates authentication to Okta, which then automatically validates the identity using Beyond Identity’s authenticator app installed on the device. Users can add multiple devices without help desk or IT support–reducing lockouts and help desk costs.
Improve Policies With Risk-based, Dynamic Authorization Decisions
As an added layer of security, administrators can create custom access policies in Beyond Identity’s Admin Portal. Organizations can implement adaptive-risk based authorization and control for which individuals and devices are allowed to access an application based on that device’s security posture at the time of login.
The Beyond Identity App provides 12+ security posture data elements from company-issued or personal (BYOD) devices without requiring 3rd party tools like a mobile device management (MDM) or endpoint detection and response (EDR).
Device security posture includes:
- OS Version
- Password protection status
- Biometric enablement status
- Secure enclave status
- Hard drive encryption status
- Firewall enablement status
- Gatekeeper enablement status
- And more!

Your team can build granular access controls and enforce risk-based authorization decisions based on the risk-level of users, devices, and apps. The ability to collect device security posture data is available in Beyond Identity’s App and does not require 3rd party tools or complicated integrations.
Security teams get real-time visibility into who’s coming across your perimeter and which device they are using and the security posture of the device at the time of each login transaction. The log data is stored in our data lake and as an immutable audit record–tying identities to devices to resources accessed and providing invaluable data for SOC and Audit/Compliance teams. The comprehensive audit data can also be integrated into GRC, SIEM, and other key security and risk management technologies.
Try it Today
It’s a seamless integration. It only takes a few configuration changes in your Okta environment and there’s no code-required. Simply add Beyond Identity as a delegated identity provider in your Okta environment and add an authentication routing rule. All of these features are built-in to the Beyond Identity cloud platform and do not require 3rd party tools or complicated integrations.
Choose Beyond Identity’s cloud-native solution for passwordless desktop, passwordless single sign-on, and device security posture for risk-based access decisions.
It’s time to fundamentally improve the way users login!







.png)






.avif)



.avif)






.avif)

