Password-Based MFA Vulnerabilities
Password-based multi-factor authentication (MFA) is the standard for securing sensitive data, and it dramatically reduces your risk of attack. But it cannot totally eliminate security risks because the password is still there, and the factors used by this type of traditional MFA are easily phishable.
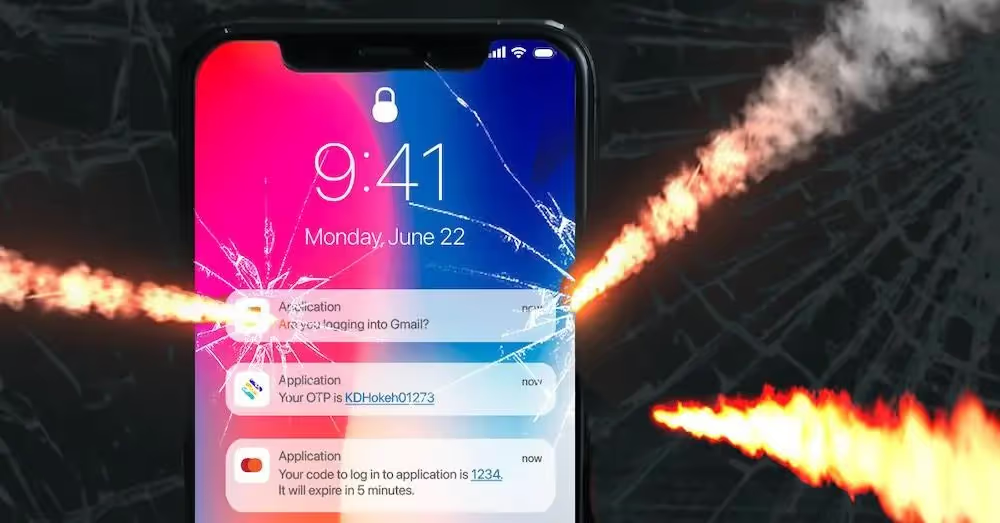
Hackers can easily intercept one-time passwords sent by email, text, or push notification and gain full access to your entire network if security measures aren’t in place. Users hate MFA that relies on second devices and slows down the authentication process and will try to avoid it at all costs. The time has come to look beyond password-based MFA and towards a passwordless future.
Let’s discuss the most common password-based MFA vulnerabilities and steps you can take right now to protect your organization from an ever-increasing number of cyberattacks.
Password-based MFA isn’t secure
IT departments have known for decades that the password is a risky method to protect sensitive assets. When first-gen MFA first started seeing widespread adoption in the early 2000s, most IT managers felt they finally had found a way to deal with the inherent insecurity of passwords.
Those good feelings were short-lived. Cybercriminals adapted and sought out new ways to hack MFA. It wasn’t difficult, either. Techniques that had been around for years, like phishing, proved helpful in bypassing or intercepting insecure second factors.
These days, ‘phish kits’ that specifically target MFA are readily available in hacking forums. SaaS-like hacking tools are becoming commonplace, making it easy to launch a successful attack without much (if any) coding experience.
Compromised, insecure factors are often the way in
Insecure factors have been the leading source of attacks for years. In fact, compromised credentials are the source of three out of every five attacks, according to Verizon’s 2021 Data Breach Investigations Report. Maybe it was foolish to believe attackers wouldn’t find ways to hack password-based MFA.
After all, MFA itself is based on inherently insecure factors. It’s not just the password that’s the issue:
- Push notifications are often used without an unphishable factor (such as biometrics). If the passcode is in that notification, that’s even worse.
- SMS text messages are often used to deliver passcodes. But with SIM swapping and interception, attackers can easily retrieve text messages.
- Magic links arrive by e-mail and like SMS, can be easily intercepted.
- One-time passwords (OTPs) annoy users and are a pain to use. Adoption is often low as users look for workarounds, defeating the whole purpose of added security.
An emerging vector: MFA prompt bombing
Notification fatigue is real, and hackers are taking advantage of this to crack password-based MFA. The recent Lapsus$ and Solarwinds hacks both used a technique called “MFA prompt bombing” to trick users into letting them in.
The idea is simple: the attacker obtains the password to an account with MFA. They then use the OTP feature to send multiple authentication requests to the legitimate user. If the timing is correct, the user might accept one of these to silence notifications. Once that’s done, the attacker can register their device with full access to the compromised account.
Prompt bombing works best with phone calls or texts, but any phishable factors could be used in such an attack. Users expect MFA to behave like this, because login issues with MFA aren’t rare.
Password-based MFA frustrates users
Password-based MFA is both insecure and an awful user experience, resulting in people finding workarounds having to use it–and thus negating any security it might provide. Entering a password is already tedious, and with first-gen MFA users must wait for a second factor to log in. The friction this creates in the user experience is substantial, and adoption is low as a result.
Users refuse to use MFA for various reasons. Some don’t want to sign up for a Google or Microsoft account for their authenticator apps due to privacy concerns. Others might not always have a second device on hand so they opt out of MFA.
There are even more issues when MFA fails. Users might never get the passcode or may receive multiple texts or receive them minutes, if not hours later. This is why techniques like MFA prompt bombing are successful: users already expect things not to work right, so a random authentication request might not look as suspicious as it should.
Why are we still trusting our critical data to passwords?
With all of the password-based MFA vulnerabilities, there is an immediate need for organizations to move beyond the password. But even with the clear need for passwordless authentication, most organizations still use passwords (often without MFA).
Today’s threat landscape makes that a dangerous choice. IBM found that compromised credentials cost organizations an average $4.4 million per attack. That includes the cost of remediation and increasingly higher ransoms to regain control of data.
Organizations were right to turn to password-based MFA, as it at least shut the door most of the way to cyber criminals. But the password is still as insecure as ever, and attackers have found a way around MFA.
Passwords are decades-old relics. In 2022, technology is available (and has been for a while) to eliminate the password. Why are we still relying on insecure ways to protect our sensitive data?
Unphishable and Frictionless MFA is the answer
There is a way to improve both MFA and do away with the password. Passwordless MFA combines authentication and MFA into a single application. Passwordless MFA that is truly phishing-resistant uses one (or more) of three ways to authenticate the users:
- Cryptographic keys
- Local biometrics
- Device-level security checks
Cryptographic keys are tied to the user and device. This allows organizations to know who accesses the network. Local biometrics add certainty of identity that the user with the correct credential is indeed who they say they are. Adding device-level security checks enables organizations to enforce security policies across devices.
Beyond Identity believes MFA should be unphishable, passwordless, and invisible. Invisible MFA creates a seamless login experience that is as simple as a click. With Secure Work, authentication is frictionless, yet far more secure than any password-based MFA solution currently on the market.
Secure Work uses immutable cryptographic credentials tied to both user and device. The platform supports top SSO solutions like Okta, Ping, Forgerock, OneLogin, Microsoft ADFS, and more with just a few lines of additional code.
Best-in-class monitoring and risk-based authentication protect your organization continuously, dramatically reducing the number and potential scope of an insider attack. You also gain the capability to make sure your users aren’t putting you at risk of attack through device-level security checks to ensure all updates are installed, and the device itself hasn’t been modified. Our continuous authentication capability allows you to continuously check user behavior and device security posture every ten minutes to further secure your critical data and resources.
All of this happens without any friction during the login process. Additional authentication factors are added only when necessary, so after a short registration process, MFA becomes invisible, and authentication is less of a hassle. Continuous authentication allows you to continuously check user behavior and device security posture every ten minutes to further secure your critical data and resources.
Ready to ditch passwords once and for all and learn more about phishing-resistant MFA? Let us show you how Beyond Identity’s invisible MFA will revolutionize how both you and your users think about modern secure authentication. Get your free demo today.
Password-based multi-factor authentication (MFA) is the standard for securing sensitive data, and it dramatically reduces your risk of attack. But it cannot totally eliminate security risks because the password is still there, and the factors used by this type of traditional MFA are easily phishable.
Hackers can easily intercept one-time passwords sent by email, text, or push notification and gain full access to your entire network if security measures aren’t in place. Users hate MFA that relies on second devices and slows down the authentication process and will try to avoid it at all costs. The time has come to look beyond password-based MFA and towards a passwordless future.
Let’s discuss the most common password-based MFA vulnerabilities and steps you can take right now to protect your organization from an ever-increasing number of cyberattacks.
Password-based MFA isn’t secure
IT departments have known for decades that the password is a risky method to protect sensitive assets. When first-gen MFA first started seeing widespread adoption in the early 2000s, most IT managers felt they finally had found a way to deal with the inherent insecurity of passwords.
Those good feelings were short-lived. Cybercriminals adapted and sought out new ways to hack MFA. It wasn’t difficult, either. Techniques that had been around for years, like phishing, proved helpful in bypassing or intercepting insecure second factors.
These days, ‘phish kits’ that specifically target MFA are readily available in hacking forums. SaaS-like hacking tools are becoming commonplace, making it easy to launch a successful attack without much (if any) coding experience.
Compromised, insecure factors are often the way in
Insecure factors have been the leading source of attacks for years. In fact, compromised credentials are the source of three out of every five attacks, according to Verizon’s 2021 Data Breach Investigations Report. Maybe it was foolish to believe attackers wouldn’t find ways to hack password-based MFA.
After all, MFA itself is based on inherently insecure factors. It’s not just the password that’s the issue:
- Push notifications are often used without an unphishable factor (such as biometrics). If the passcode is in that notification, that’s even worse.
- SMS text messages are often used to deliver passcodes. But with SIM swapping and interception, attackers can easily retrieve text messages.
- Magic links arrive by e-mail and like SMS, can be easily intercepted.
- One-time passwords (OTPs) annoy users and are a pain to use. Adoption is often low as users look for workarounds, defeating the whole purpose of added security.
An emerging vector: MFA prompt bombing
Notification fatigue is real, and hackers are taking advantage of this to crack password-based MFA. The recent Lapsus$ and Solarwinds hacks both used a technique called “MFA prompt bombing” to trick users into letting them in.
The idea is simple: the attacker obtains the password to an account with MFA. They then use the OTP feature to send multiple authentication requests to the legitimate user. If the timing is correct, the user might accept one of these to silence notifications. Once that’s done, the attacker can register their device with full access to the compromised account.
Prompt bombing works best with phone calls or texts, but any phishable factors could be used in such an attack. Users expect MFA to behave like this, because login issues with MFA aren’t rare.
Password-based MFA frustrates users
Password-based MFA is both insecure and an awful user experience, resulting in people finding workarounds having to use it–and thus negating any security it might provide. Entering a password is already tedious, and with first-gen MFA users must wait for a second factor to log in. The friction this creates in the user experience is substantial, and adoption is low as a result.
Users refuse to use MFA for various reasons. Some don’t want to sign up for a Google or Microsoft account for their authenticator apps due to privacy concerns. Others might not always have a second device on hand so they opt out of MFA.
There are even more issues when MFA fails. Users might never get the passcode or may receive multiple texts or receive them minutes, if not hours later. This is why techniques like MFA prompt bombing are successful: users already expect things not to work right, so a random authentication request might not look as suspicious as it should.
Why are we still trusting our critical data to passwords?
With all of the password-based MFA vulnerabilities, there is an immediate need for organizations to move beyond the password. But even with the clear need for passwordless authentication, most organizations still use passwords (often without MFA).
Today’s threat landscape makes that a dangerous choice. IBM found that compromised credentials cost organizations an average $4.4 million per attack. That includes the cost of remediation and increasingly higher ransoms to regain control of data.
Organizations were right to turn to password-based MFA, as it at least shut the door most of the way to cyber criminals. But the password is still as insecure as ever, and attackers have found a way around MFA.
Passwords are decades-old relics. In 2022, technology is available (and has been for a while) to eliminate the password. Why are we still relying on insecure ways to protect our sensitive data?
Unphishable and Frictionless MFA is the answer
There is a way to improve both MFA and do away with the password. Passwordless MFA combines authentication and MFA into a single application. Passwordless MFA that is truly phishing-resistant uses one (or more) of three ways to authenticate the users:
- Cryptographic keys
- Local biometrics
- Device-level security checks
Cryptographic keys are tied to the user and device. This allows organizations to know who accesses the network. Local biometrics add certainty of identity that the user with the correct credential is indeed who they say they are. Adding device-level security checks enables organizations to enforce security policies across devices.
Beyond Identity believes MFA should be unphishable, passwordless, and invisible. Invisible MFA creates a seamless login experience that is as simple as a click. With Secure Work, authentication is frictionless, yet far more secure than any password-based MFA solution currently on the market.
Secure Work uses immutable cryptographic credentials tied to both user and device. The platform supports top SSO solutions like Okta, Ping, Forgerock, OneLogin, Microsoft ADFS, and more with just a few lines of additional code.
Best-in-class monitoring and risk-based authentication protect your organization continuously, dramatically reducing the number and potential scope of an insider attack. You also gain the capability to make sure your users aren’t putting you at risk of attack through device-level security checks to ensure all updates are installed, and the device itself hasn’t been modified. Our continuous authentication capability allows you to continuously check user behavior and device security posture every ten minutes to further secure your critical data and resources.
All of this happens without any friction during the login process. Additional authentication factors are added only when necessary, so after a short registration process, MFA becomes invisible, and authentication is less of a hassle. Continuous authentication allows you to continuously check user behavior and device security posture every ten minutes to further secure your critical data and resources.
Ready to ditch passwords once and for all and learn more about phishing-resistant MFA? Let us show you how Beyond Identity’s invisible MFA will revolutionize how both you and your users think about modern secure authentication. Get your free demo today.
Password-based multi-factor authentication (MFA) is the standard for securing sensitive data, and it dramatically reduces your risk of attack. But it cannot totally eliminate security risks because the password is still there, and the factors used by this type of traditional MFA are easily phishable.
Hackers can easily intercept one-time passwords sent by email, text, or push notification and gain full access to your entire network if security measures aren’t in place. Users hate MFA that relies on second devices and slows down the authentication process and will try to avoid it at all costs. The time has come to look beyond password-based MFA and towards a passwordless future.
Let’s discuss the most common password-based MFA vulnerabilities and steps you can take right now to protect your organization from an ever-increasing number of cyberattacks.
Password-based MFA isn’t secure
IT departments have known for decades that the password is a risky method to protect sensitive assets. When first-gen MFA first started seeing widespread adoption in the early 2000s, most IT managers felt they finally had found a way to deal with the inherent insecurity of passwords.
Those good feelings were short-lived. Cybercriminals adapted and sought out new ways to hack MFA. It wasn’t difficult, either. Techniques that had been around for years, like phishing, proved helpful in bypassing or intercepting insecure second factors.
These days, ‘phish kits’ that specifically target MFA are readily available in hacking forums. SaaS-like hacking tools are becoming commonplace, making it easy to launch a successful attack without much (if any) coding experience.
Compromised, insecure factors are often the way in
Insecure factors have been the leading source of attacks for years. In fact, compromised credentials are the source of three out of every five attacks, according to Verizon’s 2021 Data Breach Investigations Report. Maybe it was foolish to believe attackers wouldn’t find ways to hack password-based MFA.
After all, MFA itself is based on inherently insecure factors. It’s not just the password that’s the issue:
- Push notifications are often used without an unphishable factor (such as biometrics). If the passcode is in that notification, that’s even worse.
- SMS text messages are often used to deliver passcodes. But with SIM swapping and interception, attackers can easily retrieve text messages.
- Magic links arrive by e-mail and like SMS, can be easily intercepted.
- One-time passwords (OTPs) annoy users and are a pain to use. Adoption is often low as users look for workarounds, defeating the whole purpose of added security.
An emerging vector: MFA prompt bombing
Notification fatigue is real, and hackers are taking advantage of this to crack password-based MFA. The recent Lapsus$ and Solarwinds hacks both used a technique called “MFA prompt bombing” to trick users into letting them in.
The idea is simple: the attacker obtains the password to an account with MFA. They then use the OTP feature to send multiple authentication requests to the legitimate user. If the timing is correct, the user might accept one of these to silence notifications. Once that’s done, the attacker can register their device with full access to the compromised account.
Prompt bombing works best with phone calls or texts, but any phishable factors could be used in such an attack. Users expect MFA to behave like this, because login issues with MFA aren’t rare.
Password-based MFA frustrates users
Password-based MFA is both insecure and an awful user experience, resulting in people finding workarounds having to use it–and thus negating any security it might provide. Entering a password is already tedious, and with first-gen MFA users must wait for a second factor to log in. The friction this creates in the user experience is substantial, and adoption is low as a result.
Users refuse to use MFA for various reasons. Some don’t want to sign up for a Google or Microsoft account for their authenticator apps due to privacy concerns. Others might not always have a second device on hand so they opt out of MFA.
There are even more issues when MFA fails. Users might never get the passcode or may receive multiple texts or receive them minutes, if not hours later. This is why techniques like MFA prompt bombing are successful: users already expect things not to work right, so a random authentication request might not look as suspicious as it should.
Why are we still trusting our critical data to passwords?
With all of the password-based MFA vulnerabilities, there is an immediate need for organizations to move beyond the password. But even with the clear need for passwordless authentication, most organizations still use passwords (often without MFA).
Today’s threat landscape makes that a dangerous choice. IBM found that compromised credentials cost organizations an average $4.4 million per attack. That includes the cost of remediation and increasingly higher ransoms to regain control of data.
Organizations were right to turn to password-based MFA, as it at least shut the door most of the way to cyber criminals. But the password is still as insecure as ever, and attackers have found a way around MFA.
Passwords are decades-old relics. In 2022, technology is available (and has been for a while) to eliminate the password. Why are we still relying on insecure ways to protect our sensitive data?
Unphishable and Frictionless MFA is the answer
There is a way to improve both MFA and do away with the password. Passwordless MFA combines authentication and MFA into a single application. Passwordless MFA that is truly phishing-resistant uses one (or more) of three ways to authenticate the users:
- Cryptographic keys
- Local biometrics
- Device-level security checks
Cryptographic keys are tied to the user and device. This allows organizations to know who accesses the network. Local biometrics add certainty of identity that the user with the correct credential is indeed who they say they are. Adding device-level security checks enables organizations to enforce security policies across devices.
Beyond Identity believes MFA should be unphishable, passwordless, and invisible. Invisible MFA creates a seamless login experience that is as simple as a click. With Secure Work, authentication is frictionless, yet far more secure than any password-based MFA solution currently on the market.
Secure Work uses immutable cryptographic credentials tied to both user and device. The platform supports top SSO solutions like Okta, Ping, Forgerock, OneLogin, Microsoft ADFS, and more with just a few lines of additional code.
Best-in-class monitoring and risk-based authentication protect your organization continuously, dramatically reducing the number and potential scope of an insider attack. You also gain the capability to make sure your users aren’t putting you at risk of attack through device-level security checks to ensure all updates are installed, and the device itself hasn’t been modified. Our continuous authentication capability allows you to continuously check user behavior and device security posture every ten minutes to further secure your critical data and resources.
All of this happens without any friction during the login process. Additional authentication factors are added only when necessary, so after a short registration process, MFA becomes invisible, and authentication is less of a hassle. Continuous authentication allows you to continuously check user behavior and device security posture every ten minutes to further secure your critical data and resources.
Ready to ditch passwords once and for all and learn more about phishing-resistant MFA? Let us show you how Beyond Identity’s invisible MFA will revolutionize how both you and your users think about modern secure authentication. Get your free demo today.






.png)






.avif)



.avif)






.avif)

