Resource Library
Explore our collection of resources covering the latest in cybersecurity, industry trends, and expert insights

19 Feb 2026
February 19, 2026
Design Unfiltered: AI Tooling Adoption with Allan Ziolkowski
A practical AI workflow for designers: rebuild your app as a lightweight sandbox, use your design system as guardrails, and prototype in real code faster.
17 Feb 2026
February 17, 2026
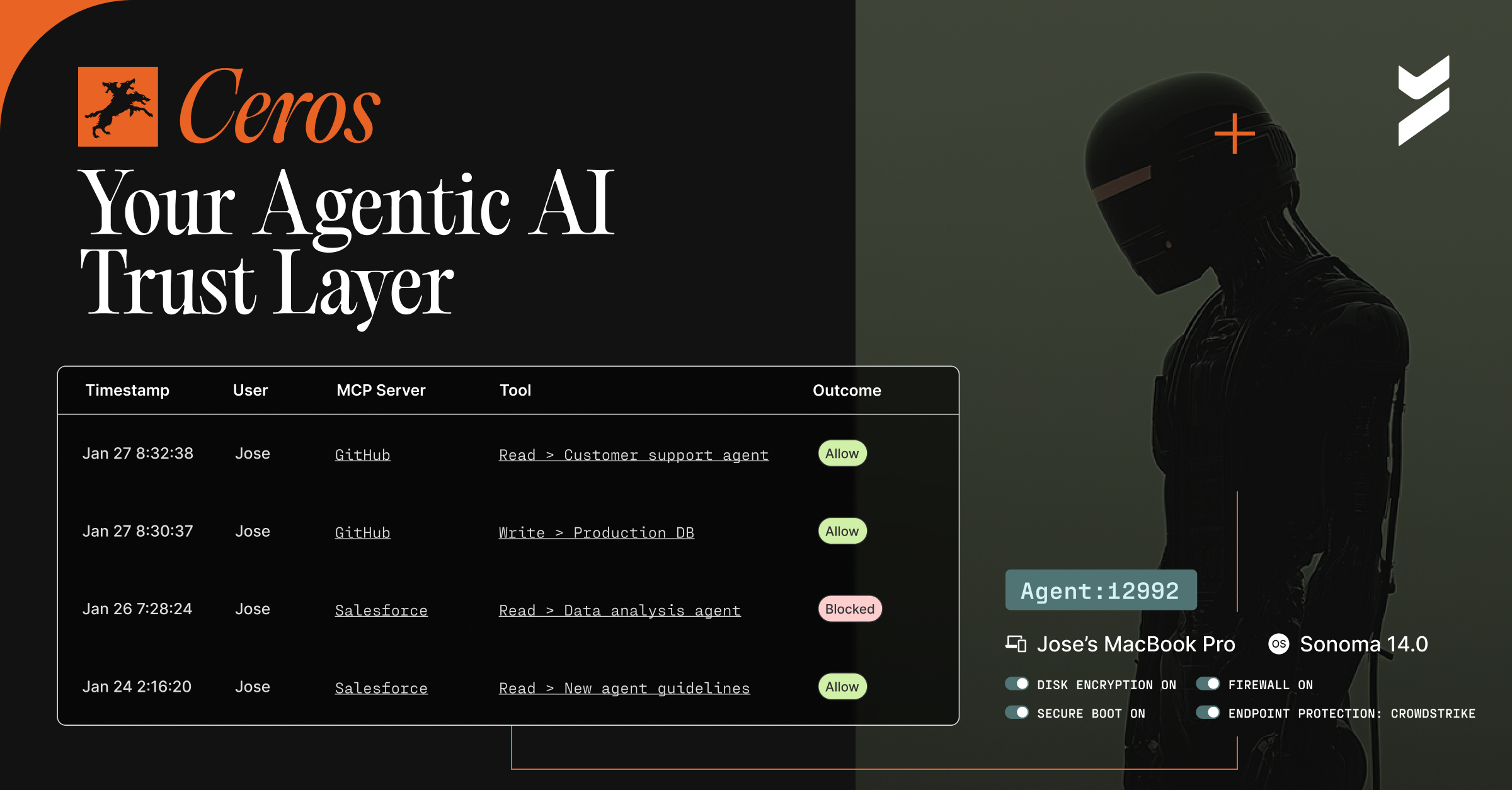
Introducing Ceros: The Agentic AI Trust Layer, Now Open for Public Preview
Secure your AI agents with Ceros, the trust layer that prevents credential theft, enforces policy in real time, and delivers full session visibility. Open for public preview now.
02 Feb 2026
February 2, 2026
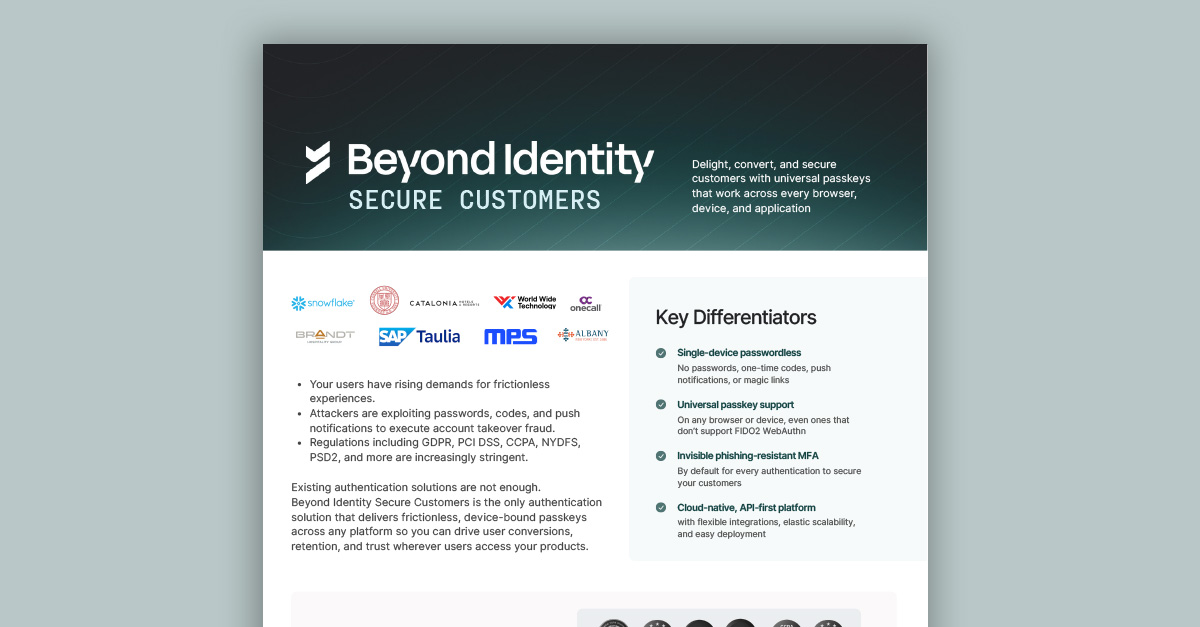
Secure Customers
Delight, convert, and secure customers with universal passkeys that work across every browser, device, and application.

27 Jan 2026
January 27, 2026
What 50 CISOs Told Us: The Top AI Risks They’re Budgeting for in 2026
What 50 CISOs say about AI risk in 2026: data leakage, Shadow AI, access to source code, budget priorities, and where security leaders are investing.

22 Jan 2026
January 22, 2026
Securing Agentic AI: From MCPs, Tool Use, to Shadow API Key Sprawl
Developers ship faster with AI, but insecure MCP servers create blind spots. Learn how to secure agentic AI in desktop IDEs.
22 Dec 2025
December 22, 2025
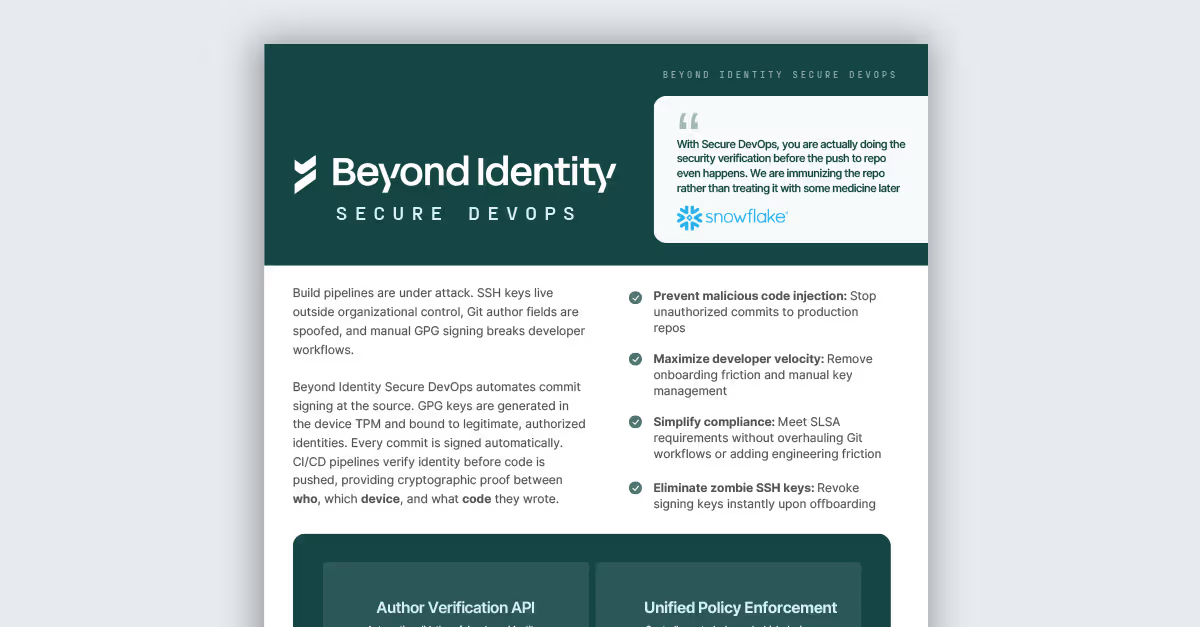
Secure DevOps Datasheet
Verify that every piece of source code is committed from a corporate identity and authorized device to stop software supply chain attacks before they start.
.avif)
09 Dec 2025
December 9, 2025
The New Blind Spot in AI-Native Orgs: Untrusted Devices + Agentic Access
AI-native orgs are moving fast, but untrusted devices and shadow AI create silent access paths. Learn how deterministic, device-bound identity closes the AI security blind spot.

08 Dec 2025
December 8, 2025
The Hacker News Webinar: Winning the AI Arms Race
See why AI-generated phishing has become indistinguishable from real email and how organizations are shutting it down with deterministic, device-verified access.

