Former Employees Admit to Using Continued Account Access to Harm Previous Employers
Key takeaways
- 83% of respondents continued accessing accounts from their previous employer after leaving the company.
- 56% of respondents said they had used their continued digital access to harm their former employer.
- 24% of respondents admitted to intentionally keeping a password after leaving the company.
- 74% of employers have been negatively impacted by an employee breaching their digital security.
Leaving one’s job is becoming more and more common these days, whether voluntarily as part of The Great Resignation, forcibly as part of pandemic-related layoffs, or somewhere in between. Consequently, employers are increasingly confronted with the issue of how to maintain cybersecurity amid mass staff departures. Are employees remembering to remove their personal information from company tech, and are employers ensuring the security of sensitive company information?
The offboarding process clearly requires a different approach in today’s unprecedented climate. We wanted to know exactly how companies are handling the issue, so we spoke to more than 1,000 employers and employees from three different countries—Ireland, the United Kingdom, and the United States—to find out. Former employees shared exactly how they’re using (and misusing) their continued access, while current leaders shared their strategies for staying safe. To glean insight into the current state of affairs—and how offboarding processes should evolve going forward—keep reading.

Overall, being formally offboarded was the norm according to 70% of our respondents. When answers were broken down by country, however, the majority of Irish respondents had not experienced a formal offboarding. In comparison, 81% of respondents from the United States had. Nevertheless, there is a great deal of variety in what the process actually entails, as we discovered in the next section of our study.
The formality of leaving a job
Leaving a job isn’t typically as simple as just walking away. Here, we gave employees a chance to share who was involved in their offboarding process, as well as the specific steps taken.

The offboarding process was not a solo affair. Most commonly, exiting employment involved the supervisor or boss (33%) or an HR representative (31%). But for more than one in 10 respondents, this key process was left up to a fellow co-worker. And in spite of the risks a departing employee poses to company cybersecurity, only 9% of respondents remembered an IT specialist being involved in their exit experience.
Moving beyond the people involved and into the mechanics of the process, we found that at best, only half of employers were taking even the most basic precautions for their company’s cybersecurity. For instance, only 50% of respondents were asked to return company devices, only 41% returned digital key tokens, and only 35% deleted or reset their accounts. Employees did little to protect their own security, either—just 40% reported wiping their personal information from company devices before returning them, while only 38% set up email forwarding.
Access after exit
Next, our study delved into the specific digital items and assets previous employees still had access to after leaving (whether forcibly or voluntarily). In total, 83% of respondents said they still had access to the digital assets of their previous employer. Former employees also shared the information they actively chose to take with them.
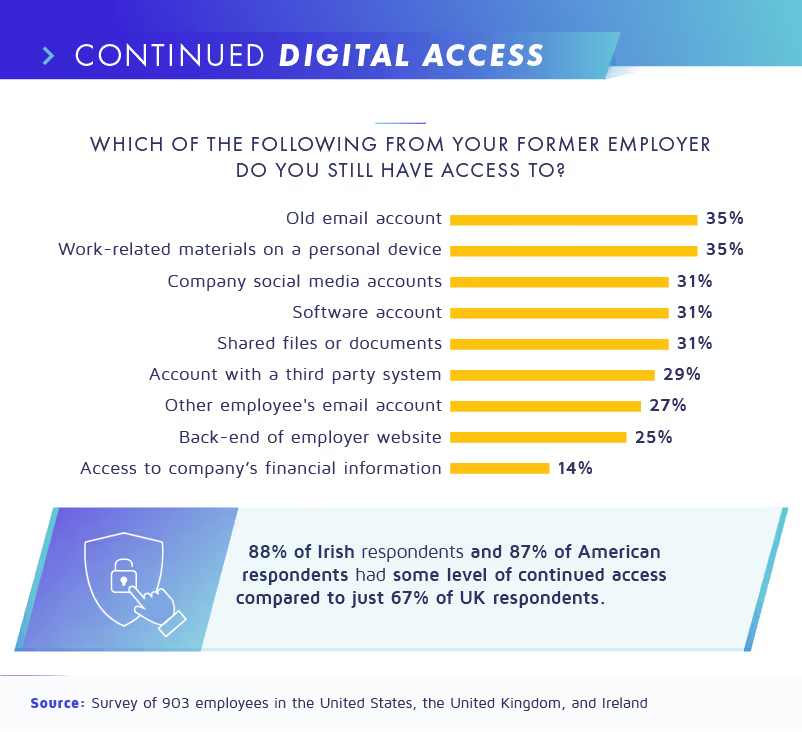
More than a third of former employees still had access to their company email account and work-related materials on a personal device. Furthermore, respondents often reported deliberately taking contact information for co-workers (31%), specific co-worker conversations they had saved (30%), and even potentially valuable company ideas (27%) with them.
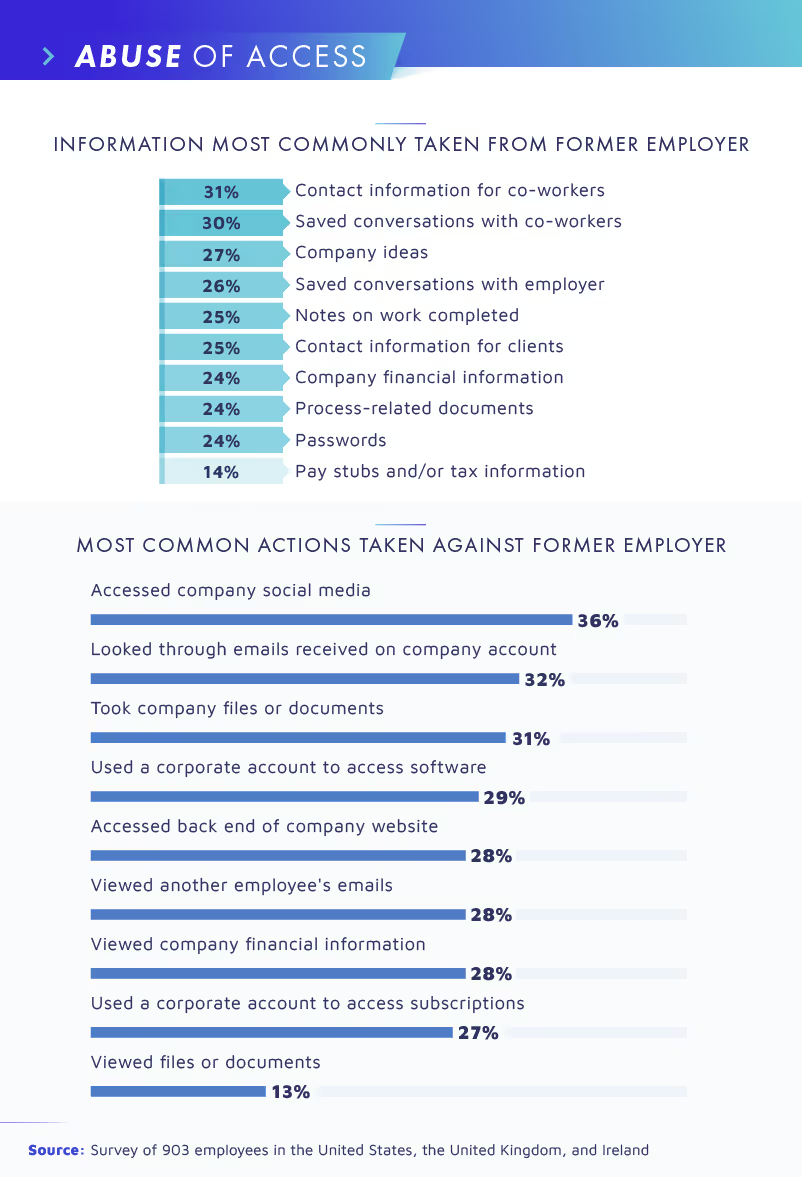
While some of these behaviors may seem harmless—perhaps an employee just wanted to stay in contact with a work friend—these are all examples of insider threats. The constant possibility of human error means that every time an employee logs onto the company network, they put their company’s digital security at risk. However, our results find that many previous employees were purposefully compromising their employers digital security.
Twenty-eight percent accessed the back end of their previous company’s website, while the same amount admitted to logging into someone’s email other than their own. When we asked if they told their former employer about any of this access, only 59% said yes.
Fallout of cyber exit risks
With so many employees taking so much with them when they go, cybersecurity risks have become full-blown threats. The next section of our study includes the number of employees who’d intentionally harmed previous employers using their residual digital access.
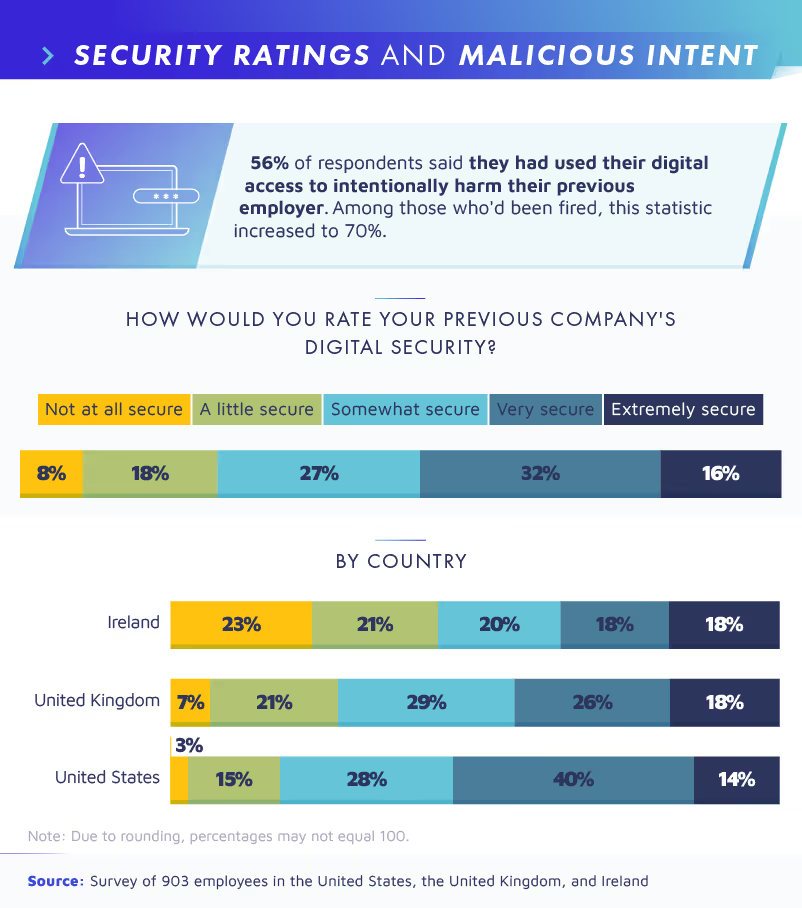
The recent mass exodus of employees spells bad news for businesses everywhere. More than half of respondents were willing to admit that they had used their remaining digital access to maliciously impact their previous employer. Bear in mind that this statistic refers to all employees—even those that left willingly. When an employee had been fired, the proportion of those who had intentionally caused harm jumped to 70%.
Irish businesses may want to take special note here, since employees from this country were the most likely to report that their previous company had zero corporate security (23%). That said, no country studied was immune to risk. While U.S. employees reported the highest level of security among former companies, only 14% described theirs as “extremely secure.”
First lines of company defense
With so much admitted malicious intent, we wanted to turn our study over to the business leaders and managers left to deal with the fallout. We asked a little over 200 business leaders in the U.S. about the specific offboarding processes their companies have implemented to protect themselves.

There appeared to be some discrepancy between employee and employer responses. While only 40% of employees reported wiping company devices upon leaving, 53% of managers and leaders insisted they did so, which nevertheless highlights a key concern: Only just over half of employers are even attempting to completely wipe a device after an employee’s departure.
Still fewer employers took back digital keys or tokens (52%), while just 51% took back company devices. Perhaps one of the most bonafide and easily doable protection methods, changing passwords, was employed by exactly half of the leaders we spoke to. While this specific behavior may fall outside the job description of owners and managers, getting an IT professional or HR representative to tackle this task is highly advisable.
Offboarding horror stories
With previous employees frequently admitting to attempting a post-departure cyberattack, we decided to ask business leaders for their perspective. What malicious actions had they experienced, and how much faith did they have in their companies’ cybersecurity?

Malicious post-departure security attacks appeared to be effective, as nearly three-quarters of business leaders reported having been harmed by a previous employee in this way. Thirty-nine percent specified that this included the employee accessing the company’s financial information, followed by 37% who mentioned them gaining unwanted access to work emails. More than a third said a disgruntled former employee had hacked into the back end of the company website, taken company files, and/or accessed company software. Even fellow employees weren’t safe, as a third said attackers had accessed a co-worker’s email.
Keeping your company and employees safe
The results of this study were ultimately quite shocking, with many respondents freely admitting to using their former company’s cybersecurity weaknesses to cause intentional harm. Leaders appear acutely aware of the issue and yet unsure of exactly how to improve security or practice effective offboarding procedures. It’s safe to say that relatively little is safe at headquarters in this era of mass employee departures.
The best way to maintain security during these tumultuous times is to leave it to the professionals. At Beyond Identity, we can help you secure your workforce and protect your company’s security from former employees with phishing-resistant MFA. Instead of easily stolen passwords, we use passwordless authentication that provides seamless and unobtrusive security. Our passwordless multi-factor authentication is strong and invisible with no need for a second device. Additionally, we can bind the identity of a user to their device, so a former employee would no longer be able to gain access to company resources. Learn more about keeping your company safe at www.beyondidentity.com.
Methodology and limitations
This study surveyed a total of 1,121 respondents. 903 respondents were standard employees, and 218 were business leaders. The 903 standard employees were residents of three different countries: 500 from the United States, 200 from the United Kingdom, and 203 from Ireland. All 218 business leaders resided in the United States.
The data presented in this study rely on self-report. Limitations of self-reported data include, but are not limited to, exaggeration, selective memory, and telescoping. This study was purely exploratory, and further study should be done into the relationship between offboarding processes and company security.
Fair use statement
It’s said there is safety in numbers, so feel free to spread this information to as many people as you can. Just be sure your purposes are noncommercial and that you link back to this page.
Key takeaways
- 83% of respondents continued accessing accounts from their previous employer after leaving the company.
- 56% of respondents said they had used their continued digital access to harm their former employer.
- 24% of respondents admitted to intentionally keeping a password after leaving the company.
- 74% of employers have been negatively impacted by an employee breaching their digital security.
Leaving one’s job is becoming more and more common these days, whether voluntarily as part of The Great Resignation, forcibly as part of pandemic-related layoffs, or somewhere in between. Consequently, employers are increasingly confronted with the issue of how to maintain cybersecurity amid mass staff departures. Are employees remembering to remove their personal information from company tech, and are employers ensuring the security of sensitive company information?
The offboarding process clearly requires a different approach in today’s unprecedented climate. We wanted to know exactly how companies are handling the issue, so we spoke to more than 1,000 employers and employees from three different countries—Ireland, the United Kingdom, and the United States—to find out. Former employees shared exactly how they’re using (and misusing) their continued access, while current leaders shared their strategies for staying safe. To glean insight into the current state of affairs—and how offboarding processes should evolve going forward—keep reading.

Overall, being formally offboarded was the norm according to 70% of our respondents. When answers were broken down by country, however, the majority of Irish respondents had not experienced a formal offboarding. In comparison, 81% of respondents from the United States had. Nevertheless, there is a great deal of variety in what the process actually entails, as we discovered in the next section of our study.
The formality of leaving a job
Leaving a job isn’t typically as simple as just walking away. Here, we gave employees a chance to share who was involved in their offboarding process, as well as the specific steps taken.

The offboarding process was not a solo affair. Most commonly, exiting employment involved the supervisor or boss (33%) or an HR representative (31%). But for more than one in 10 respondents, this key process was left up to a fellow co-worker. And in spite of the risks a departing employee poses to company cybersecurity, only 9% of respondents remembered an IT specialist being involved in their exit experience.
Moving beyond the people involved and into the mechanics of the process, we found that at best, only half of employers were taking even the most basic precautions for their company’s cybersecurity. For instance, only 50% of respondents were asked to return company devices, only 41% returned digital key tokens, and only 35% deleted or reset their accounts. Employees did little to protect their own security, either—just 40% reported wiping their personal information from company devices before returning them, while only 38% set up email forwarding.
Access after exit
Next, our study delved into the specific digital items and assets previous employees still had access to after leaving (whether forcibly or voluntarily). In total, 83% of respondents said they still had access to the digital assets of their previous employer. Former employees also shared the information they actively chose to take with them.

More than a third of former employees still had access to their company email account and work-related materials on a personal device. Furthermore, respondents often reported deliberately taking contact information for co-workers (31%), specific co-worker conversations they had saved (30%), and even potentially valuable company ideas (27%) with them.

While some of these behaviors may seem harmless—perhaps an employee just wanted to stay in contact with a work friend—these are all examples of insider threats. The constant possibility of human error means that every time an employee logs onto the company network, they put their company’s digital security at risk. However, our results find that many previous employees were purposefully compromising their employers digital security.
Twenty-eight percent accessed the back end of their previous company’s website, while the same amount admitted to logging into someone’s email other than their own. When we asked if they told their former employer about any of this access, only 59% said yes.
Fallout of cyber exit risks
With so many employees taking so much with them when they go, cybersecurity risks have become full-blown threats. The next section of our study includes the number of employees who’d intentionally harmed previous employers using their residual digital access.

The recent mass exodus of employees spells bad news for businesses everywhere. More than half of respondents were willing to admit that they had used their remaining digital access to maliciously impact their previous employer. Bear in mind that this statistic refers to all employees—even those that left willingly. When an employee had been fired, the proportion of those who had intentionally caused harm jumped to 70%.
Irish businesses may want to take special note here, since employees from this country were the most likely to report that their previous company had zero corporate security (23%). That said, no country studied was immune to risk. While U.S. employees reported the highest level of security among former companies, only 14% described theirs as “extremely secure.”
First lines of company defense
With so much admitted malicious intent, we wanted to turn our study over to the business leaders and managers left to deal with the fallout. We asked a little over 200 business leaders in the U.S. about the specific offboarding processes their companies have implemented to protect themselves.

There appeared to be some discrepancy between employee and employer responses. While only 40% of employees reported wiping company devices upon leaving, 53% of managers and leaders insisted they did so, which nevertheless highlights a key concern: Only just over half of employers are even attempting to completely wipe a device after an employee’s departure.
Still fewer employers took back digital keys or tokens (52%), while just 51% took back company devices. Perhaps one of the most bonafide and easily doable protection methods, changing passwords, was employed by exactly half of the leaders we spoke to. While this specific behavior may fall outside the job description of owners and managers, getting an IT professional or HR representative to tackle this task is highly advisable.
Offboarding horror stories
With previous employees frequently admitting to attempting a post-departure cyberattack, we decided to ask business leaders for their perspective. What malicious actions had they experienced, and how much faith did they have in their companies’ cybersecurity?

Malicious post-departure security attacks appeared to be effective, as nearly three-quarters of business leaders reported having been harmed by a previous employee in this way. Thirty-nine percent specified that this included the employee accessing the company’s financial information, followed by 37% who mentioned them gaining unwanted access to work emails. More than a third said a disgruntled former employee had hacked into the back end of the company website, taken company files, and/or accessed company software. Even fellow employees weren’t safe, as a third said attackers had accessed a co-worker’s email.
Keeping your company and employees safe
The results of this study were ultimately quite shocking, with many respondents freely admitting to using their former company’s cybersecurity weaknesses to cause intentional harm. Leaders appear acutely aware of the issue and yet unsure of exactly how to improve security or practice effective offboarding procedures. It’s safe to say that relatively little is safe at headquarters in this era of mass employee departures.
The best way to maintain security during these tumultuous times is to leave it to the professionals. At Beyond Identity, we can help you secure your workforce and protect your company’s security from former employees with phishing-resistant MFA. Instead of easily stolen passwords, we use passwordless authentication that provides seamless and unobtrusive security. Our passwordless multi-factor authentication is strong and invisible with no need for a second device. Additionally, we can bind the identity of a user to their device, so a former employee would no longer be able to gain access to company resources. Learn more about keeping your company safe at www.beyondidentity.com.
Methodology and limitations
This study surveyed a total of 1,121 respondents. 903 respondents were standard employees, and 218 were business leaders. The 903 standard employees were residents of three different countries: 500 from the United States, 200 from the United Kingdom, and 203 from Ireland. All 218 business leaders resided in the United States.
The data presented in this study rely on self-report. Limitations of self-reported data include, but are not limited to, exaggeration, selective memory, and telescoping. This study was purely exploratory, and further study should be done into the relationship between offboarding processes and company security.
Fair use statement
It’s said there is safety in numbers, so feel free to spread this information to as many people as you can. Just be sure your purposes are noncommercial and that you link back to this page.
Key takeaways
- 83% of respondents continued accessing accounts from their previous employer after leaving the company.
- 56% of respondents said they had used their continued digital access to harm their former employer.
- 24% of respondents admitted to intentionally keeping a password after leaving the company.
- 74% of employers have been negatively impacted by an employee breaching their digital security.
Leaving one’s job is becoming more and more common these days, whether voluntarily as part of The Great Resignation, forcibly as part of pandemic-related layoffs, or somewhere in between. Consequently, employers are increasingly confronted with the issue of how to maintain cybersecurity amid mass staff departures. Are employees remembering to remove their personal information from company tech, and are employers ensuring the security of sensitive company information?
The offboarding process clearly requires a different approach in today’s unprecedented climate. We wanted to know exactly how companies are handling the issue, so we spoke to more than 1,000 employers and employees from three different countries—Ireland, the United Kingdom, and the United States—to find out. Former employees shared exactly how they’re using (and misusing) their continued access, while current leaders shared their strategies for staying safe. To glean insight into the current state of affairs—and how offboarding processes should evolve going forward—keep reading.

Overall, being formally offboarded was the norm according to 70% of our respondents. When answers were broken down by country, however, the majority of Irish respondents had not experienced a formal offboarding. In comparison, 81% of respondents from the United States had. Nevertheless, there is a great deal of variety in what the process actually entails, as we discovered in the next section of our study.
The formality of leaving a job
Leaving a job isn’t typically as simple as just walking away. Here, we gave employees a chance to share who was involved in their offboarding process, as well as the specific steps taken.

The offboarding process was not a solo affair. Most commonly, exiting employment involved the supervisor or boss (33%) or an HR representative (31%). But for more than one in 10 respondents, this key process was left up to a fellow co-worker. And in spite of the risks a departing employee poses to company cybersecurity, only 9% of respondents remembered an IT specialist being involved in their exit experience.
Moving beyond the people involved and into the mechanics of the process, we found that at best, only half of employers were taking even the most basic precautions for their company’s cybersecurity. For instance, only 50% of respondents were asked to return company devices, only 41% returned digital key tokens, and only 35% deleted or reset their accounts. Employees did little to protect their own security, either—just 40% reported wiping their personal information from company devices before returning them, while only 38% set up email forwarding.
Access after exit
Next, our study delved into the specific digital items and assets previous employees still had access to after leaving (whether forcibly or voluntarily). In total, 83% of respondents said they still had access to the digital assets of their previous employer. Former employees also shared the information they actively chose to take with them.

More than a third of former employees still had access to their company email account and work-related materials on a personal device. Furthermore, respondents often reported deliberately taking contact information for co-workers (31%), specific co-worker conversations they had saved (30%), and even potentially valuable company ideas (27%) with them.

While some of these behaviors may seem harmless—perhaps an employee just wanted to stay in contact with a work friend—these are all examples of insider threats. The constant possibility of human error means that every time an employee logs onto the company network, they put their company’s digital security at risk. However, our results find that many previous employees were purposefully compromising their employers digital security.
Twenty-eight percent accessed the back end of their previous company’s website, while the same amount admitted to logging into someone’s email other than their own. When we asked if they told their former employer about any of this access, only 59% said yes.
Fallout of cyber exit risks
With so many employees taking so much with them when they go, cybersecurity risks have become full-blown threats. The next section of our study includes the number of employees who’d intentionally harmed previous employers using their residual digital access.

The recent mass exodus of employees spells bad news for businesses everywhere. More than half of respondents were willing to admit that they had used their remaining digital access to maliciously impact their previous employer. Bear in mind that this statistic refers to all employees—even those that left willingly. When an employee had been fired, the proportion of those who had intentionally caused harm jumped to 70%.
Irish businesses may want to take special note here, since employees from this country were the most likely to report that their previous company had zero corporate security (23%). That said, no country studied was immune to risk. While U.S. employees reported the highest level of security among former companies, only 14% described theirs as “extremely secure.”
First lines of company defense
With so much admitted malicious intent, we wanted to turn our study over to the business leaders and managers left to deal with the fallout. We asked a little over 200 business leaders in the U.S. about the specific offboarding processes their companies have implemented to protect themselves.

There appeared to be some discrepancy between employee and employer responses. While only 40% of employees reported wiping company devices upon leaving, 53% of managers and leaders insisted they did so, which nevertheless highlights a key concern: Only just over half of employers are even attempting to completely wipe a device after an employee’s departure.
Still fewer employers took back digital keys or tokens (52%), while just 51% took back company devices. Perhaps one of the most bonafide and easily doable protection methods, changing passwords, was employed by exactly half of the leaders we spoke to. While this specific behavior may fall outside the job description of owners and managers, getting an IT professional or HR representative to tackle this task is highly advisable.
Offboarding horror stories
With previous employees frequently admitting to attempting a post-departure cyberattack, we decided to ask business leaders for their perspective. What malicious actions had they experienced, and how much faith did they have in their companies’ cybersecurity?

Malicious post-departure security attacks appeared to be effective, as nearly three-quarters of business leaders reported having been harmed by a previous employee in this way. Thirty-nine percent specified that this included the employee accessing the company’s financial information, followed by 37% who mentioned them gaining unwanted access to work emails. More than a third said a disgruntled former employee had hacked into the back end of the company website, taken company files, and/or accessed company software. Even fellow employees weren’t safe, as a third said attackers had accessed a co-worker’s email.
Keeping your company and employees safe
The results of this study were ultimately quite shocking, with many respondents freely admitting to using their former company’s cybersecurity weaknesses to cause intentional harm. Leaders appear acutely aware of the issue and yet unsure of exactly how to improve security or practice effective offboarding procedures. It’s safe to say that relatively little is safe at headquarters in this era of mass employee departures.
The best way to maintain security during these tumultuous times is to leave it to the professionals. At Beyond Identity, we can help you secure your workforce and protect your company’s security from former employees with phishing-resistant MFA. Instead of easily stolen passwords, we use passwordless authentication that provides seamless and unobtrusive security. Our passwordless multi-factor authentication is strong and invisible with no need for a second device. Additionally, we can bind the identity of a user to their device, so a former employee would no longer be able to gain access to company resources. Learn more about keeping your company safe at www.beyondidentity.com.
Methodology and limitations
This study surveyed a total of 1,121 respondents. 903 respondents were standard employees, and 218 were business leaders. The 903 standard employees were residents of three different countries: 500 from the United States, 200 from the United Kingdom, and 203 from Ireland. All 218 business leaders resided in the United States.
The data presented in this study rely on self-report. Limitations of self-reported data include, but are not limited to, exaggeration, selective memory, and telescoping. This study was purely exploratory, and further study should be done into the relationship between offboarding processes and company security.
Fair use statement
It’s said there is safety in numbers, so feel free to spread this information to as many people as you can. Just be sure your purposes are noncommercial and that you link back to this page.







.png)






.avif)



.avif)






.avif)

