The Beyond Blog

22 Jan 2026
Beyond Identity Opens Early Access for the AI Security Suite
Gain visibility and control over autonomous AI agents with Beyond Identity's AI Security Suite. Enforce identity, device context, and data governance with cryptographic proof. Early access is now open!

18 Jul 2022
July 18, 2022
Pros & Cons of Social Logins
Social login allows users to authenticate in a website or app without needing to create another password for this new account, or having to remember this password next time they return.

15 Jul 2022
July 15, 2022
Authentication Metrics to Track and Why They Matter
Metrics matter because what you can measure, you can improve. Metrics provide visibility into what is and is not working for a business, enabling the company to improve processes or make strategic investments to maximize efficiency and revenue.

30 Jun 2022
June 30, 2022
Passwordless E-Commerce: Make the Checkout Experience Enjoyable
How can you make it easy for online shoppers to spend their hard-earned money? By providing a passwordless e-commerce experience.

28 Jun 2022
June 28, 2022
Data Breaches are More Costly for These 10 Industries
Beyond Identity collected data from the IBM Security’s Cost of a Data Breach Report 2021 to identify 10 industries where data breaches are the most costly.

27 Jun 2022
June 27, 2022
Secure Your Repo Access & Code Commits with GitLab and Beyond Identity
Beyond Identity and GitLab are addressing the weakness created by implicit trust placed in the software supply chains.

16 Jun 2022
June 16, 2022
Top Trends and Topics Coming Out of the RSA and Gartner Conferences
Here are some of the most popular topics that came out of RSA and Gartner conferences, where the top cybersecurity professionals gathered.

07 Jun 2022
June 7, 2022
Putting the “Continuous” in Continuous Authentication
We made our Continuous Risk-Based Authentication capability generally available, making “continuous authentication” actually continuous.
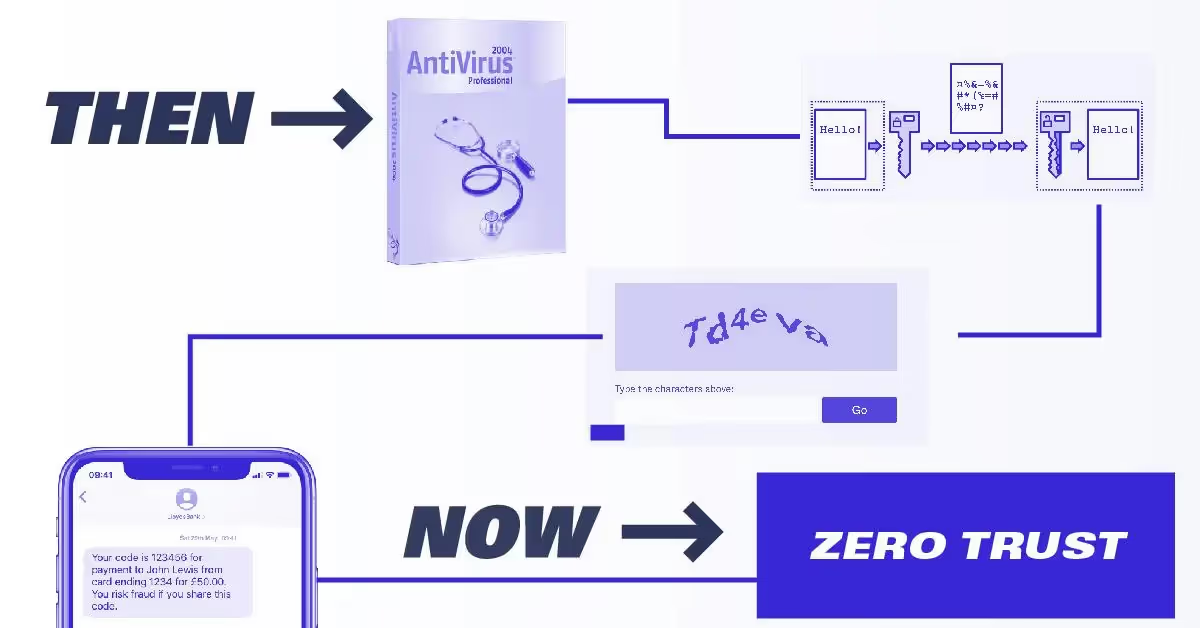
31 May 2022
May 31, 2022
History of Online Security, from CAPTCHA to Multi-Factor Authentication
Beyond Identity covers the history of cybersecurity, from the first antivirus program to the rise of two-factor authentication.

25 May 2022
May 25, 2022
What to Know From the 2022 Verizon Data Breach Investigations Report (DBIR)
The 2022 Verizon DBIR is full of insights and data about the current state of cybersecurity. Here are the top five takeaways you need to know.

