The Beyond Blog
.png)
15 Sep 2025
Universal Identity Defense for Legacy and On-Prem Applications with Beyond Identity and CrowdStrike
Extend phishing-resistant MFA to Kerberos, NTLM, LDAP, SMB with Beyond Identity + CrowdStrike.

27 Jun 2022
June 27, 2022
Secure Your Repo Access & Code Commits with GitLab and Beyond Identity
Beyond Identity and GitLab are addressing the weakness created by implicit trust placed in the software supply chains.

16 Jun 2022
June 16, 2022
Top Trends and Topics Coming Out of the RSA and Gartner Conferences
Here are some of the most popular topics that came out of RSA and Gartner conferences, where the top cybersecurity professionals gathered.

07 Jun 2022
June 7, 2022
Putting the “Continuous” in Continuous Authentication
We made our Continuous Risk-Based Authentication capability generally available, making “continuous authentication” actually continuous.
31 May 2022
May 31, 2022
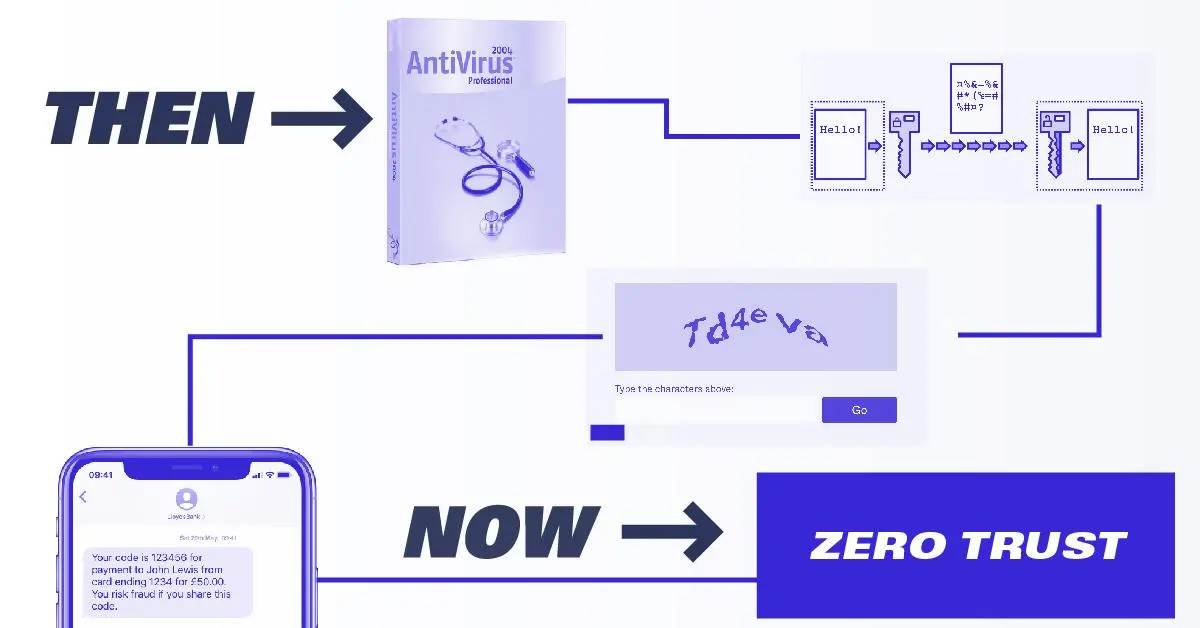
History of Online Security, from CAPTCHA to Multi-Factor Authentication
Beyond Identity covers the history of cybersecurity, from the first antivirus program to the rise of two-factor authentication.

25 May 2022
May 25, 2022
What to Know From the 2022 Verizon Data Breach Investigations Report (DBIR)
The 2022 Verizon DBIR is full of insights and data about the current state of cybersecurity. Here are the top five takeaways you need to know.

17 May 2022
May 17, 2022
Why the GitHub 2023 2FA Mandate isn't Enough
This 2FA initiative from GitHub is designed to improve the overall security of the software supply chain, but it doesn’t go far enough.

11 May 2022
May 11, 2022
NIST and Passwordless Solutions: Meeting Compliance Needs
The truth is that passwordless authentication is NIST 800-63 compliant and a much better solution than simply improving your password policies.
04 May 2022
May 4, 2022
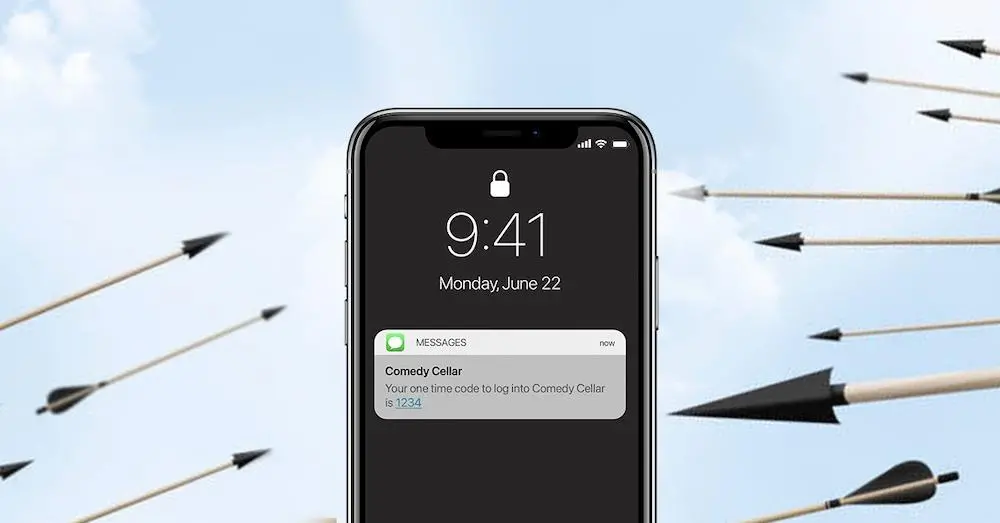
Why Your MFA Is Insecure
Using multiple insecure authentication mechanisms provides little security and many MFA solutions today still leave companies vulnerable to attack.

29 Apr 2022
April 29, 2022
Countries With the Most—and Least—Digital Freedom
Beyond Identity compiled data from Freedom House’s 2021 Freedom on the Net report to rank the countries with the most and least digital freedom.

