Is Two-Factor Authentication (2FA) Worth It?
One of the most common pieces of advice you will receive from InfoSec teams and security experts is to turn on two-factor authentication, also known as 2FA. 2FA is part of a broader authentication method called multi-factor authentication, or MFA, in which a second factor is used to authenticate a login attempt. These factors fall into three categories, either something you know, something you have, or something you are.
2FA and MFA add an additional layer of security to your systems and applications—at least in theory. However, there are many ways in which 2FA can be breached, hacked, or manipulated, resulting in huge problems for your organization.
While 2FA is frequently promoted, there are still many concerns regarding this authentication method and the level of security it actually provides. Many organizations consider adding MFA to their security protocol due to its reputation, but while frequently recommended, is 2FA truly worth the effort to get employees to enable and adopt this authentication system? The answer is simple: no. There are better, more secure authentication methods available at your disposal that we will be discussing today.
Security Risks
2FA is sometimes praised as being an excellent method of preventing threat actors from scraping vulnerabilities and exposing data breaches from your most critical applications and systems, but this is not the case. 2FA, and MFA in general, is actually a highly risky authentication method, with many opportunities for failure and vulnerability exposure.
One method of breaching 2FA could be through text message. If you receive a text from an unknown number to visit a fake or counterfeit website and click it by mistake or out of confusion, a hacker could easily trick you into verifying the text message or authentication app code you received. With that information, a malicious cybercriminal could steal your PII (Personal Identifiable Information) and compromise your systems or accounts. While a text message does indeed utilize a second factor, it is not a secure one, it is not a reliable way to secure your systems and applications.
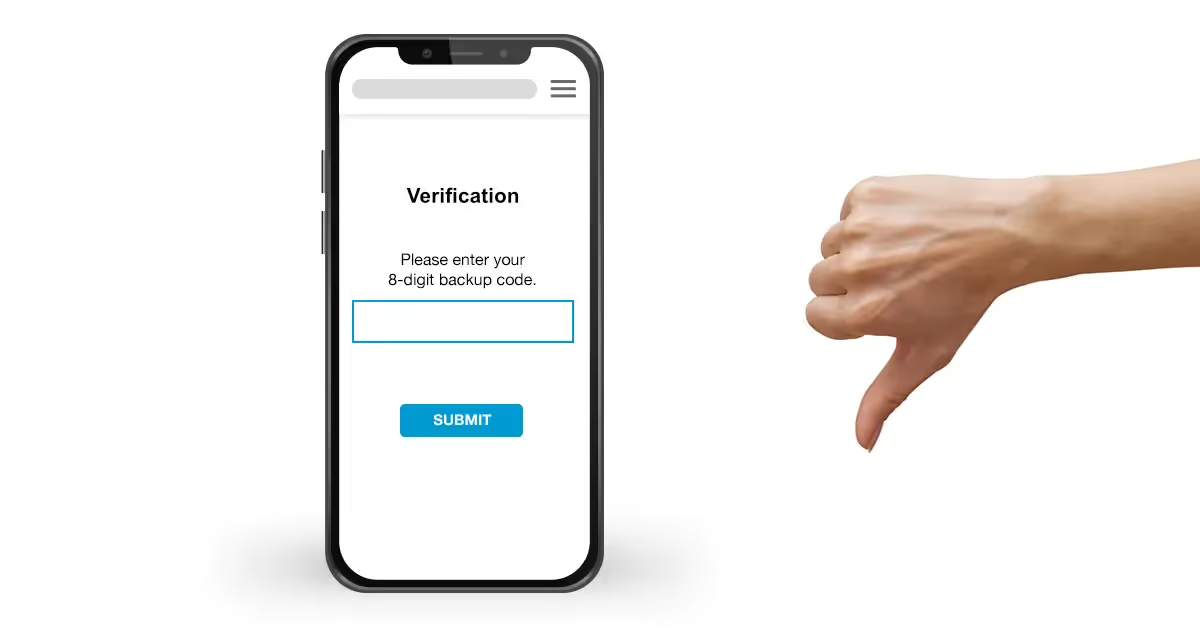
Another method of 2FA is through the use of backup codes. Often when first signing up for a new application or website, backup codes are assigned to a user in case they ever forget their password or security question responses. If these backup codes fall into the wrong hands, they could be used to breach the account in question, resulting in massive losses for the organization.
Even with 2FA, users are still not safe from attacks such as phishing scams, like receiving an email from a fake site and account requesting a password reset, social engineering, such as manipulation or psychological attack on individuals to retrieve sensitive information, or even the theft of physical items, such as hardware security keys. For example, Twitter CEO Jack Dorsey recently fell prey to a SIM swap attack that involves deceiving a mobile carrier into switching service to a new phone. All a SIM swap requires is a call to the phone company and a bit of social engineering, and your number can easily fall in the wrong hands. They never have to even be in the same continent as you to essentially steal your phone.
User Experience
One of the most inconvenient aspects to 2FA and MFA in general is the poor experience for your employees. MFA is not only an inconvenient process for the employer, but also results in a whole host of complications for the user. 2FA requires the use of a second, often personal device, which frequently causes aggravation for the user. A second device is also not always available in emergency situations, such as a media crisis or website outage, and can cause delays during critical business events.
Another aspect is the interruption of user workflow. Whether it’s opening an authentication app, relaying a text message, or retrieving a hardware security key, 2FA causes unnecessary work delays that impede progress. Small, frequent interruptions result in a taskforce that is not being utilized effectively, and as a result, quality and consistency may suffer.
If your organization utilizes 2FA hardware security keys, you are especially in trouble. These physical authentic devices can easily be lost or stolen, leaving your organization primed for an unsuspected attack. Regardless of how secure you may think these keys are, the fact is that while a physical item is less likely to be hacked virtually, it still faces the same physical risks in the real world. Traditional MFA leads to a poor user experience as a result of these security and convenience gaps.
Limited Access Control
One of the biggest challenges when using 2FA is the limited access control it offers its users. Without continuous risk-based authentication, there is no way to verify that the individual using the application is who they claim to be, which can make way for hackers to lean into data breaches and vulnerabilities within your systems.
Many organizations have also made changes to their existing policies, allowing employees to use their own devices in this changing work from home culture. As a result, 2FA offers significantly less protection, and results in security vulnerabilities that can easily be exploited.
What Should You Use Instead?
2FA is not worth the investment. Between a poor user experience, limited or non-existence access control, and the high risk factors, we know that 2FA is an outdated, insecure method of authentication. Luckily, Beyond Identity is here to help you keep all your applications and resources safe and secure.
Beyond Identity eliminates passwords completely so hackers have no credentials to steal in the first place. Beyond Identity is able to verify identities using biometrics, and able to assess security risk by analyzing the security posture of the device that is being used to login. Needless to say this is not only far more secure than 2FA but also far more convenient.
See for yourself: request a demo of Beyond Identity
One of the most common pieces of advice you will receive from InfoSec teams and security experts is to turn on two-factor authentication, also known as 2FA. 2FA is part of a broader authentication method called multi-factor authentication, or MFA, in which a second factor is used to authenticate a login attempt. These factors fall into three categories, either something you know, something you have, or something you are.
2FA and MFA add an additional layer of security to your systems and applications—at least in theory. However, there are many ways in which 2FA can be breached, hacked, or manipulated, resulting in huge problems for your organization.
While 2FA is frequently promoted, there are still many concerns regarding this authentication method and the level of security it actually provides. Many organizations consider adding MFA to their security protocol due to its reputation, but while frequently recommended, is 2FA truly worth the effort to get employees to enable and adopt this authentication system? The answer is simple: no. There are better, more secure authentication methods available at your disposal that we will be discussing today.
Security Risks
2FA is sometimes praised as being an excellent method of preventing threat actors from scraping vulnerabilities and exposing data breaches from your most critical applications and systems, but this is not the case. 2FA, and MFA in general, is actually a highly risky authentication method, with many opportunities for failure and vulnerability exposure.
One method of breaching 2FA could be through text message. If you receive a text from an unknown number to visit a fake or counterfeit website and click it by mistake or out of confusion, a hacker could easily trick you into verifying the text message or authentication app code you received. With that information, a malicious cybercriminal could steal your PII (Personal Identifiable Information) and compromise your systems or accounts. While a text message does indeed utilize a second factor, it is not a secure one, it is not a reliable way to secure your systems and applications.
Another method of 2FA is through the use of backup codes. Often when first signing up for a new application or website, backup codes are assigned to a user in case they ever forget their password or security question responses. If these backup codes fall into the wrong hands, they could be used to breach the account in question, resulting in massive losses for the organization.
Even with 2FA, users are still not safe from attacks such as phishing scams, like receiving an email from a fake site and account requesting a password reset, social engineering, such as manipulation or psychological attack on individuals to retrieve sensitive information, or even the theft of physical items, such as hardware security keys. For example, Twitter CEO Jack Dorsey recently fell prey to a SIM swap attack that involves deceiving a mobile carrier into switching service to a new phone. All a SIM swap requires is a call to the phone company and a bit of social engineering, and your number can easily fall in the wrong hands. They never have to even be in the same continent as you to essentially steal your phone.
User Experience
One of the most inconvenient aspects to 2FA and MFA in general is the poor experience for your employees. MFA is not only an inconvenient process for the employer, but also results in a whole host of complications for the user. 2FA requires the use of a second, often personal device, which frequently causes aggravation for the user. A second device is also not always available in emergency situations, such as a media crisis or website outage, and can cause delays during critical business events.
Another aspect is the interruption of user workflow. Whether it’s opening an authentication app, relaying a text message, or retrieving a hardware security key, 2FA causes unnecessary work delays that impede progress. Small, frequent interruptions result in a taskforce that is not being utilized effectively, and as a result, quality and consistency may suffer.
If your organization utilizes 2FA hardware security keys, you are especially in trouble. These physical authentic devices can easily be lost or stolen, leaving your organization primed for an unsuspected attack. Regardless of how secure you may think these keys are, the fact is that while a physical item is less likely to be hacked virtually, it still faces the same physical risks in the real world. Traditional MFA leads to a poor user experience as a result of these security and convenience gaps.
Limited Access Control
One of the biggest challenges when using 2FA is the limited access control it offers its users. Without continuous risk-based authentication, there is no way to verify that the individual using the application is who they claim to be, which can make way for hackers to lean into data breaches and vulnerabilities within your systems.
Many organizations have also made changes to their existing policies, allowing employees to use their own devices in this changing work from home culture. As a result, 2FA offers significantly less protection, and results in security vulnerabilities that can easily be exploited.
What Should You Use Instead?
2FA is not worth the investment. Between a poor user experience, limited or non-existence access control, and the high risk factors, we know that 2FA is an outdated, insecure method of authentication. Luckily, Beyond Identity is here to help you keep all your applications and resources safe and secure.
Beyond Identity eliminates passwords completely so hackers have no credentials to steal in the first place. Beyond Identity is able to verify identities using biometrics, and able to assess security risk by analyzing the security posture of the device that is being used to login. Needless to say this is not only far more secure than 2FA but also far more convenient.
See for yourself: request a demo of Beyond Identity
One of the most common pieces of advice you will receive from InfoSec teams and security experts is to turn on two-factor authentication, also known as 2FA. 2FA is part of a broader authentication method called multi-factor authentication, or MFA, in which a second factor is used to authenticate a login attempt. These factors fall into three categories, either something you know, something you have, or something you are.
2FA and MFA add an additional layer of security to your systems and applications—at least in theory. However, there are many ways in which 2FA can be breached, hacked, or manipulated, resulting in huge problems for your organization.
While 2FA is frequently promoted, there are still many concerns regarding this authentication method and the level of security it actually provides. Many organizations consider adding MFA to their security protocol due to its reputation, but while frequently recommended, is 2FA truly worth the effort to get employees to enable and adopt this authentication system? The answer is simple: no. There are better, more secure authentication methods available at your disposal that we will be discussing today.
Security Risks
2FA is sometimes praised as being an excellent method of preventing threat actors from scraping vulnerabilities and exposing data breaches from your most critical applications and systems, but this is not the case. 2FA, and MFA in general, is actually a highly risky authentication method, with many opportunities for failure and vulnerability exposure.
One method of breaching 2FA could be through text message. If you receive a text from an unknown number to visit a fake or counterfeit website and click it by mistake or out of confusion, a hacker could easily trick you into verifying the text message or authentication app code you received. With that information, a malicious cybercriminal could steal your PII (Personal Identifiable Information) and compromise your systems or accounts. While a text message does indeed utilize a second factor, it is not a secure one, it is not a reliable way to secure your systems and applications.
Another method of 2FA is through the use of backup codes. Often when first signing up for a new application or website, backup codes are assigned to a user in case they ever forget their password or security question responses. If these backup codes fall into the wrong hands, they could be used to breach the account in question, resulting in massive losses for the organization.
Even with 2FA, users are still not safe from attacks such as phishing scams, like receiving an email from a fake site and account requesting a password reset, social engineering, such as manipulation or psychological attack on individuals to retrieve sensitive information, or even the theft of physical items, such as hardware security keys. For example, Twitter CEO Jack Dorsey recently fell prey to a SIM swap attack that involves deceiving a mobile carrier into switching service to a new phone. All a SIM swap requires is a call to the phone company and a bit of social engineering, and your number can easily fall in the wrong hands. They never have to even be in the same continent as you to essentially steal your phone.
User Experience
One of the most inconvenient aspects to 2FA and MFA in general is the poor experience for your employees. MFA is not only an inconvenient process for the employer, but also results in a whole host of complications for the user. 2FA requires the use of a second, often personal device, which frequently causes aggravation for the user. A second device is also not always available in emergency situations, such as a media crisis or website outage, and can cause delays during critical business events.
Another aspect is the interruption of user workflow. Whether it’s opening an authentication app, relaying a text message, or retrieving a hardware security key, 2FA causes unnecessary work delays that impede progress. Small, frequent interruptions result in a taskforce that is not being utilized effectively, and as a result, quality and consistency may suffer.
If your organization utilizes 2FA hardware security keys, you are especially in trouble. These physical authentic devices can easily be lost or stolen, leaving your organization primed for an unsuspected attack. Regardless of how secure you may think these keys are, the fact is that while a physical item is less likely to be hacked virtually, it still faces the same physical risks in the real world. Traditional MFA leads to a poor user experience as a result of these security and convenience gaps.
Limited Access Control
One of the biggest challenges when using 2FA is the limited access control it offers its users. Without continuous risk-based authentication, there is no way to verify that the individual using the application is who they claim to be, which can make way for hackers to lean into data breaches and vulnerabilities within your systems.
Many organizations have also made changes to their existing policies, allowing employees to use their own devices in this changing work from home culture. As a result, 2FA offers significantly less protection, and results in security vulnerabilities that can easily be exploited.
What Should You Use Instead?
2FA is not worth the investment. Between a poor user experience, limited or non-existence access control, and the high risk factors, we know that 2FA is an outdated, insecure method of authentication. Luckily, Beyond Identity is here to help you keep all your applications and resources safe and secure.
Beyond Identity eliminates passwords completely so hackers have no credentials to steal in the first place. Beyond Identity is able to verify identities using biometrics, and able to assess security risk by analyzing the security posture of the device that is being used to login. Needless to say this is not only far more secure than 2FA but also far more convenient.












.avif)
.avif)



.avif)






.avif)

