How to Prevent Phishing: A New Approach
Urgent and stressful situations challenge us. Ideally, we maintain composure. All too often, we succumb to the pressure and behave in ways we later regret.
Think of phishing as this sort of psychological stress.
Protection against phishing has failed, leaving our passwords and psyches vulnerable. What if there were a more straightforward solution than deploying email gateways, enrolling employees in awareness training, and resetting passwords?
What if we simply eliminated the very thing that phishing attacks are after?
What Is Phishing?
Phishing is the most common and costly cyberthreat. It leverages the pretense of an urgent request from a trusted source to make people give up personal information, usually over email.
In 2020, the toll of phishing was staggering:
- Phishing and stolen credentials were the top two threat actions in breaches.
- More than half of cybersecurity professionals saw an increase in email phishing attacks since the coronavirus pandemic began.
- Phishing attacks affected 85 percent of all active organizations.
- Users opened 30 percent of phishing emails.
- Hackers designed 57 percent of all phishing attacks for credential theft.
- The average phishing attack cost $1.6 million.
With phishing attacks on the rise in 2021, the threat is evolving.
There's no way to stop 100 percent of phishing attacks. But there is a way to make a large chunk of phishing emails completely ineffective.
If credential theft made up 57 percent of all phishing attacks in 2020, wouldn’t eliminating passwords prevent roughly 57 percent of all phishing attacks?
Before we get into that, we need to understand why hackers are so desperate for credentials in the first place.
What Are Credential Harvesting Phishing Emails?
Stealing passwords is the easiest and most effective way for hackers to breach confidential information.
Passwords to popular workplace applications like Office 365 provide long-term access to sensitive information and other individuals within the organization. Hackers use this momentum to take over other accounts, inflict financial damage, and commit espionage.
That’s why they craft credential harvesting emails that provoke users to click a link. This compromised link directs them to a spoofed login page designed to steal passwords.
Three Examples of Phishing Emails
Even though there are endless flavors of phishing emails, they all have something in common. For them to work, the victim needs to take the bait for it to work.
The three examples of phishing emails below attempt to make the victim click on a link so they can solve a problem with an online account.
1. Password Reset Phishing Emails
Beware of cleverly disguised phishing emails suggesting it’s time to reset your password. Many of these reminders are credential harvesting attacks masquerading as a security best practice.
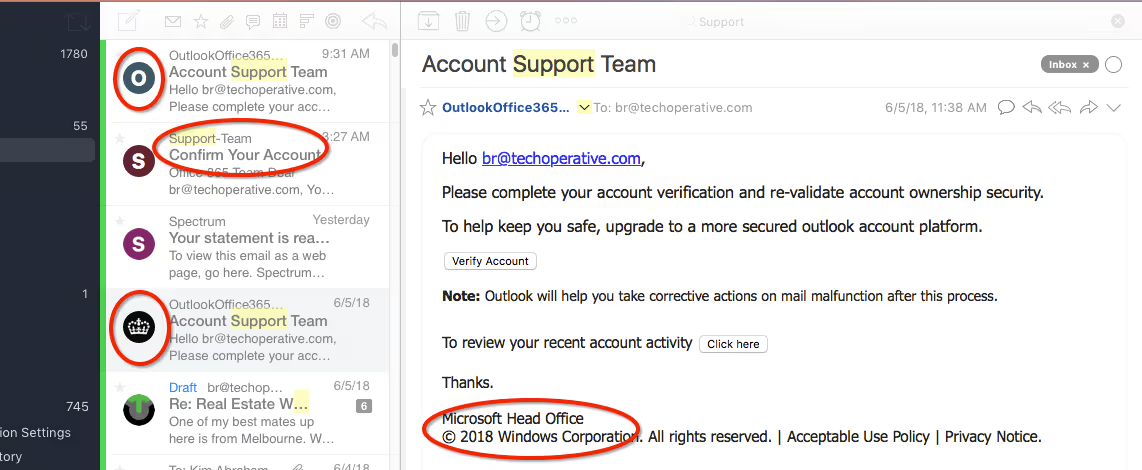
Your company might have a policy on password resets, requesting that you update them quarterly. Suppose you’re unaware of such a policy or haven’t heard your colleagues complain about password resets before. In that case, there’s a chance that the password reset request is a phishing email.
2. Package Delivery Phishing Emails
In the age of coronavirus, fewer things are more frustrating than a package delivery gone wrong.

Remember: Hackers prey on anxiety and frustration to pressure victims into risky behavior, like clicking on a tracking link that requires a “login” before you see the status of your shipment.
3. Banking Update Phishing Emails
You might get a message from Bank of America claiming that something’s wrong with your account. Perhaps there’s been an unauthorized transaction, or maybe your account’s been suspended.
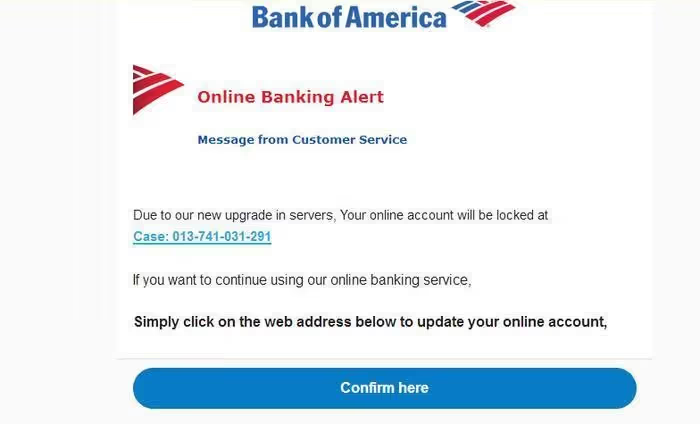
The email suggests that you need to log in to your account and reset your password to fix the problem. This ploy is just another attempt to harvest your credentials while you’re in a state of panic.
Why Old Ways of Phishing Prevention Don’t Work
What we’ve been doing to prevent phishing isn’t working – especially when it comes to credential harvesting emails. Most popular anti-phishing solutions offer temporary, surface-level solutions to the problem.
Let’s look at the top three phishing prevention methods and some key reasons they fail to protect personal information.
1. Password Resets Miss The Point
- Passwords are inherently weak. Most people reuse passwords. Even if you use a password manager, what good does that do if your master password is guessable? Ultimately, passwords are a “shared secret,” which means they’re sitting ducks in a data center that can be breached.
- It’s easy to crack passwords. Because passwords are shared secrets, they’re always vulnerable. Even worse, most passwords are easy to guess. Brute force attacks, password spraying, shoulder surfing, and credential stuffing prove that if there’s a password, there’s a way to get hacked.
- Password resets are useless in account takeover situations. When hackers gain control of your account, they can reset the password to lock you out.
2. User Awareness Training Can’t Keep Up
- Phishing emails prey on human behavior like fear and excitement. It’s easy to forget what you learned in a training video when confronted with an email containing alarming information.
- Phishing techniques evolve faster than training programs. Hackers are aware of anti-phishing trends and use that information to design attacks users won’t anticipate.
3. Anti-Phishing Software Will Always Miss Some Emails
- Secure email gateways miss a large chunk of phishing emails. Security software doesn’t stop the phishing problem at its core; it merely detects and prevents phishing emails designed to harvest credentials. No solution can catch 100% of phishing emails.
- False positives cause headaches for IT teams. If your secure email gateway has a 1% false positive rate, that can have serious consequences – especially if your organization has a high volume of email traffic. Those false positives can be as costly as a phishing email, slowing down projects and censoring timely information.
And so, the battle rages. Hackers continue to develop phishing emails indistinguishable from regular online communication.
It’s time for a paradigm shift. Rather than feebly attempt to block the attack, why not eliminate the target?
Go Passwordless: A New Way to Prevent Credential Harvesting Phishing Attacks
Attackers phishing for passwords won’t find them if there are no passwords to steal in the first place.
What would happen if a user without any passwords to hack got a phishing email asking them to reset their password? They wouldn’t even open it. What if they encountered a spoofed login page? They would have no password to enter.
That’s the power of eliminating passwords. It renders credential harvesting phishes obsolete.
By removing the password from the equation, it takes away the bounty from the hacker.
What Is Passwordless Authentication?
Passwordless authentication is a form of authentication that doesn’t use passwords. But to be a bit more specific:
- No one can use a password to authenticate
- Passwords can’t be used as an alternative authentication method, a backup, or as part of the authentication process “sometimes”
This means password managers that simply hide the password, or a single sign-on that allows you to use only one password are not truly passwordless. This is important because when there are truly no passwords, then a stolen password can’t be used by an attacker.
In conclusion...
Phishing prevention as we know it is a losing battle. Password resets, user awareness training, and security software burden the victim and not the hacker. These cost organizations valuable time and money in guesswork.
As long as passwords exist, they will be the number one security issue in the digital world. Credential harvesting phishing emails will keep flooding inboxes and draining resources.
Phishing is here to stay, and credentials will remain the primary target. We need to make credential harvesting attempts ineffective with passwordless authentication. Even though this doesn’t stop phishing attacks that attempt to deliver malware, it’s an important step forward to drastically reduce the volume of breaches.
Get a demo and stop credential harvesting phishing emails for good.
Urgent and stressful situations challenge us. Ideally, we maintain composure. All too often, we succumb to the pressure and behave in ways we later regret.
Think of phishing as this sort of psychological stress.
Protection against phishing has failed, leaving our passwords and psyches vulnerable. What if there were a more straightforward solution than deploying email gateways, enrolling employees in awareness training, and resetting passwords?
What if we simply eliminated the very thing that phishing attacks are after?
What Is Phishing?
Phishing is the most common and costly cyberthreat. It leverages the pretense of an urgent request from a trusted source to make people give up personal information, usually over email.
In 2020, the toll of phishing was staggering:
- Phishing and stolen credentials were the top two threat actions in breaches.
- More than half of cybersecurity professionals saw an increase in email phishing attacks since the coronavirus pandemic began.
- Phishing attacks affected 85 percent of all active organizations.
- Users opened 30 percent of phishing emails.
- Hackers designed 57 percent of all phishing attacks for credential theft.
- The average phishing attack cost $1.6 million.
With phishing attacks on the rise in 2021, the threat is evolving.
There's no way to stop 100 percent of phishing attacks. But there is a way to make a large chunk of phishing emails completely ineffective.
If credential theft made up 57 percent of all phishing attacks in 2020, wouldn’t eliminating passwords prevent roughly 57 percent of all phishing attacks?
Before we get into that, we need to understand why hackers are so desperate for credentials in the first place.
What Are Credential Harvesting Phishing Emails?
Stealing passwords is the easiest and most effective way for hackers to breach confidential information.
Passwords to popular workplace applications like Office 365 provide long-term access to sensitive information and other individuals within the organization. Hackers use this momentum to take over other accounts, inflict financial damage, and commit espionage.
That’s why they craft credential harvesting emails that provoke users to click a link. This compromised link directs them to a spoofed login page designed to steal passwords.
Three Examples of Phishing Emails
Even though there are endless flavors of phishing emails, they all have something in common. For them to work, the victim needs to take the bait for it to work.
The three examples of phishing emails below attempt to make the victim click on a link so they can solve a problem with an online account.
1. Password Reset Phishing Emails
Beware of cleverly disguised phishing emails suggesting it’s time to reset your password. Many of these reminders are credential harvesting attacks masquerading as a security best practice.

Your company might have a policy on password resets, requesting that you update them quarterly. Suppose you’re unaware of such a policy or haven’t heard your colleagues complain about password resets before. In that case, there’s a chance that the password reset request is a phishing email.
2. Package Delivery Phishing Emails
In the age of coronavirus, fewer things are more frustrating than a package delivery gone wrong.

Remember: Hackers prey on anxiety and frustration to pressure victims into risky behavior, like clicking on a tracking link that requires a “login” before you see the status of your shipment.
3. Banking Update Phishing Emails
You might get a message from Bank of America claiming that something’s wrong with your account. Perhaps there’s been an unauthorized transaction, or maybe your account’s been suspended.

The email suggests that you need to log in to your account and reset your password to fix the problem. This ploy is just another attempt to harvest your credentials while you’re in a state of panic.
Why Old Ways of Phishing Prevention Don’t Work
What we’ve been doing to prevent phishing isn’t working – especially when it comes to credential harvesting emails. Most popular anti-phishing solutions offer temporary, surface-level solutions to the problem.
Let’s look at the top three phishing prevention methods and some key reasons they fail to protect personal information.
1. Password Resets Miss The Point
- Passwords are inherently weak. Most people reuse passwords. Even if you use a password manager, what good does that do if your master password is guessable? Ultimately, passwords are a “shared secret,” which means they’re sitting ducks in a data center that can be breached.
- It’s easy to crack passwords. Because passwords are shared secrets, they’re always vulnerable. Even worse, most passwords are easy to guess. Brute force attacks, password spraying, shoulder surfing, and credential stuffing prove that if there’s a password, there’s a way to get hacked.
- Password resets are useless in account takeover situations. When hackers gain control of your account, they can reset the password to lock you out.
2. User Awareness Training Can’t Keep Up
- Phishing emails prey on human behavior like fear and excitement. It’s easy to forget what you learned in a training video when confronted with an email containing alarming information.
- Phishing techniques evolve faster than training programs. Hackers are aware of anti-phishing trends and use that information to design attacks users won’t anticipate.
3. Anti-Phishing Software Will Always Miss Some Emails
- Secure email gateways miss a large chunk of phishing emails. Security software doesn’t stop the phishing problem at its core; it merely detects and prevents phishing emails designed to harvest credentials. No solution can catch 100% of phishing emails.
- False positives cause headaches for IT teams. If your secure email gateway has a 1% false positive rate, that can have serious consequences – especially if your organization has a high volume of email traffic. Those false positives can be as costly as a phishing email, slowing down projects and censoring timely information.
And so, the battle rages. Hackers continue to develop phishing emails indistinguishable from regular online communication.
It’s time for a paradigm shift. Rather than feebly attempt to block the attack, why not eliminate the target?
Go Passwordless: A New Way to Prevent Credential Harvesting Phishing Attacks
Attackers phishing for passwords won’t find them if there are no passwords to steal in the first place.
What would happen if a user without any passwords to hack got a phishing email asking them to reset their password? They wouldn’t even open it. What if they encountered a spoofed login page? They would have no password to enter.
That’s the power of eliminating passwords. It renders credential harvesting phishes obsolete.
By removing the password from the equation, it takes away the bounty from the hacker.
What Is Passwordless Authentication?
Passwordless authentication is a form of authentication that doesn’t use passwords. But to be a bit more specific:
- No one can use a password to authenticate
- Passwords can’t be used as an alternative authentication method, a backup, or as part of the authentication process “sometimes”
This means password managers that simply hide the password, or a single sign-on that allows you to use only one password are not truly passwordless. This is important because when there are truly no passwords, then a stolen password can’t be used by an attacker.
In conclusion...
Phishing prevention as we know it is a losing battle. Password resets, user awareness training, and security software burden the victim and not the hacker. These cost organizations valuable time and money in guesswork.
As long as passwords exist, they will be the number one security issue in the digital world. Credential harvesting phishing emails will keep flooding inboxes and draining resources.
Phishing is here to stay, and credentials will remain the primary target. We need to make credential harvesting attempts ineffective with passwordless authentication. Even though this doesn’t stop phishing attacks that attempt to deliver malware, it’s an important step forward to drastically reduce the volume of breaches.
Get a demo and stop credential harvesting phishing emails for good.
Urgent and stressful situations challenge us. Ideally, we maintain composure. All too often, we succumb to the pressure and behave in ways we later regret.
Think of phishing as this sort of psychological stress.
Protection against phishing has failed, leaving our passwords and psyches vulnerable. What if there were a more straightforward solution than deploying email gateways, enrolling employees in awareness training, and resetting passwords?
What if we simply eliminated the very thing that phishing attacks are after?
What Is Phishing?
Phishing is the most common and costly cyberthreat. It leverages the pretense of an urgent request from a trusted source to make people give up personal information, usually over email.
In 2020, the toll of phishing was staggering:
- Phishing and stolen credentials were the top two threat actions in breaches.
- More than half of cybersecurity professionals saw an increase in email phishing attacks since the coronavirus pandemic began.
- Phishing attacks affected 85 percent of all active organizations.
- Users opened 30 percent of phishing emails.
- Hackers designed 57 percent of all phishing attacks for credential theft.
- The average phishing attack cost $1.6 million.
With phishing attacks on the rise in 2021, the threat is evolving.
There's no way to stop 100 percent of phishing attacks. But there is a way to make a large chunk of phishing emails completely ineffective.
If credential theft made up 57 percent of all phishing attacks in 2020, wouldn’t eliminating passwords prevent roughly 57 percent of all phishing attacks?
Before we get into that, we need to understand why hackers are so desperate for credentials in the first place.
What Are Credential Harvesting Phishing Emails?
Stealing passwords is the easiest and most effective way for hackers to breach confidential information.
Passwords to popular workplace applications like Office 365 provide long-term access to sensitive information and other individuals within the organization. Hackers use this momentum to take over other accounts, inflict financial damage, and commit espionage.
That’s why they craft credential harvesting emails that provoke users to click a link. This compromised link directs them to a spoofed login page designed to steal passwords.
Three Examples of Phishing Emails
Even though there are endless flavors of phishing emails, they all have something in common. For them to work, the victim needs to take the bait for it to work.
The three examples of phishing emails below attempt to make the victim click on a link so they can solve a problem with an online account.
1. Password Reset Phishing Emails
Beware of cleverly disguised phishing emails suggesting it’s time to reset your password. Many of these reminders are credential harvesting attacks masquerading as a security best practice.

Your company might have a policy on password resets, requesting that you update them quarterly. Suppose you’re unaware of such a policy or haven’t heard your colleagues complain about password resets before. In that case, there’s a chance that the password reset request is a phishing email.
2. Package Delivery Phishing Emails
In the age of coronavirus, fewer things are more frustrating than a package delivery gone wrong.

Remember: Hackers prey on anxiety and frustration to pressure victims into risky behavior, like clicking on a tracking link that requires a “login” before you see the status of your shipment.
3. Banking Update Phishing Emails
You might get a message from Bank of America claiming that something’s wrong with your account. Perhaps there’s been an unauthorized transaction, or maybe your account’s been suspended.

The email suggests that you need to log in to your account and reset your password to fix the problem. This ploy is just another attempt to harvest your credentials while you’re in a state of panic.
Why Old Ways of Phishing Prevention Don’t Work
What we’ve been doing to prevent phishing isn’t working – especially when it comes to credential harvesting emails. Most popular anti-phishing solutions offer temporary, surface-level solutions to the problem.
Let’s look at the top three phishing prevention methods and some key reasons they fail to protect personal information.
1. Password Resets Miss The Point
- Passwords are inherently weak. Most people reuse passwords. Even if you use a password manager, what good does that do if your master password is guessable? Ultimately, passwords are a “shared secret,” which means they’re sitting ducks in a data center that can be breached.
- It’s easy to crack passwords. Because passwords are shared secrets, they’re always vulnerable. Even worse, most passwords are easy to guess. Brute force attacks, password spraying, shoulder surfing, and credential stuffing prove that if there’s a password, there’s a way to get hacked.
- Password resets are useless in account takeover situations. When hackers gain control of your account, they can reset the password to lock you out.
2. User Awareness Training Can’t Keep Up
- Phishing emails prey on human behavior like fear and excitement. It’s easy to forget what you learned in a training video when confronted with an email containing alarming information.
- Phishing techniques evolve faster than training programs. Hackers are aware of anti-phishing trends and use that information to design attacks users won’t anticipate.
3. Anti-Phishing Software Will Always Miss Some Emails
- Secure email gateways miss a large chunk of phishing emails. Security software doesn’t stop the phishing problem at its core; it merely detects and prevents phishing emails designed to harvest credentials. No solution can catch 100% of phishing emails.
- False positives cause headaches for IT teams. If your secure email gateway has a 1% false positive rate, that can have serious consequences – especially if your organization has a high volume of email traffic. Those false positives can be as costly as a phishing email, slowing down projects and censoring timely information.
And so, the battle rages. Hackers continue to develop phishing emails indistinguishable from regular online communication.
It’s time for a paradigm shift. Rather than feebly attempt to block the attack, why not eliminate the target?
Go Passwordless: A New Way to Prevent Credential Harvesting Phishing Attacks
Attackers phishing for passwords won’t find them if there are no passwords to steal in the first place.
What would happen if a user without any passwords to hack got a phishing email asking them to reset their password? They wouldn’t even open it. What if they encountered a spoofed login page? They would have no password to enter.
That’s the power of eliminating passwords. It renders credential harvesting phishes obsolete.
By removing the password from the equation, it takes away the bounty from the hacker.
What Is Passwordless Authentication?
Passwordless authentication is a form of authentication that doesn’t use passwords. But to be a bit more specific:
- No one can use a password to authenticate
- Passwords can’t be used as an alternative authentication method, a backup, or as part of the authentication process “sometimes”
This means password managers that simply hide the password, or a single sign-on that allows you to use only one password are not truly passwordless. This is important because when there are truly no passwords, then a stolen password can’t be used by an attacker.
In conclusion...
Phishing prevention as we know it is a losing battle. Password resets, user awareness training, and security software burden the victim and not the hacker. These cost organizations valuable time and money in guesswork.
As long as passwords exist, they will be the number one security issue in the digital world. Credential harvesting phishing emails will keep flooding inboxes and draining resources.
Phishing is here to stay, and credentials will remain the primary target. We need to make credential harvesting attempts ineffective with passwordless authentication. Even though this doesn’t stop phishing attacks that attempt to deliver malware, it’s an important step forward to drastically reduce the volume of breaches.
Get a demo and stop credential harvesting phishing emails for good.






.png)






.avif)



.avif)






.avif)

