Gartner Designates Passwordless Authentication a Priority for 2022
As remote work continues to dominate as we head into 2022, finding the best security solution for organizations remains a top priority, especially as employees connect to critical resources using their own personal devices. So it’s no surprise that in Gartner’s report on emerging technologies and trends for 2022 that they consider “ubiquitous and transparent security” one of the core trends and themes going into this new year.
Gartner’s impact radar shows which technologies in these core areas will be a focus in the future and which are an initiative that organizations should take on now:
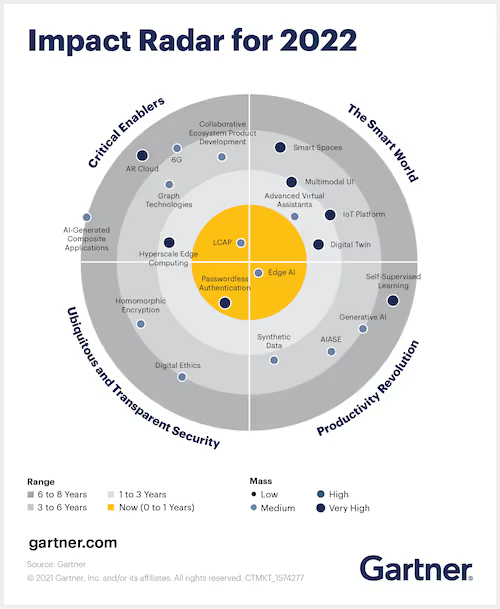
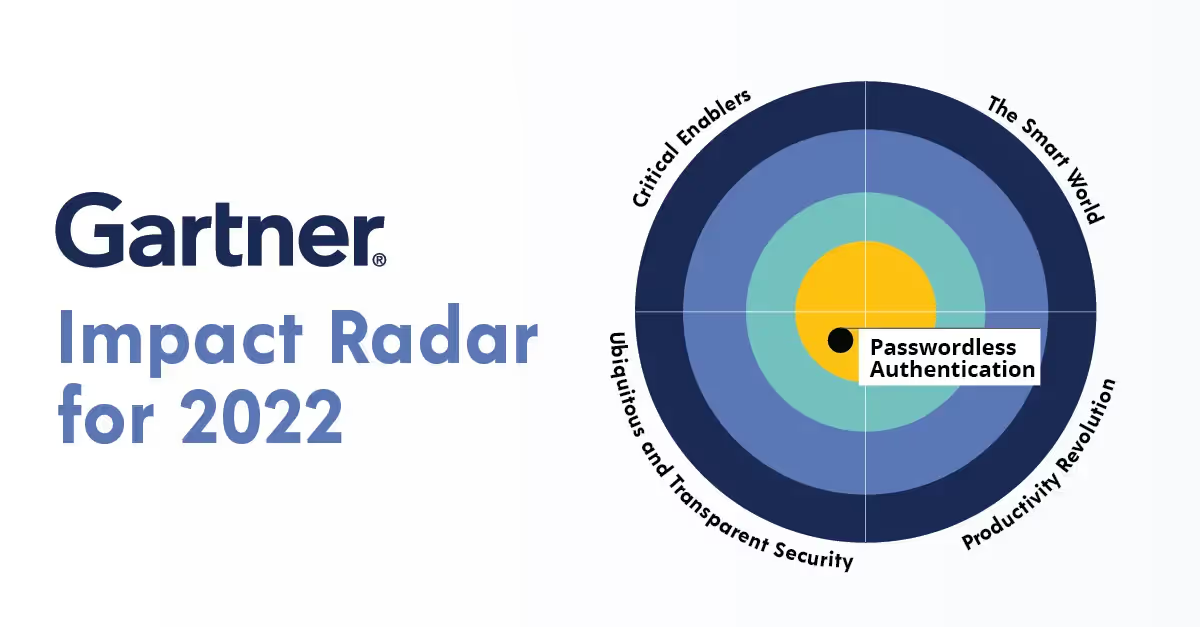
Gartner deems passwordless authentication as critical
Gartner has designated passwordless authentication as a key technology that organizations should adopt as soon as possible. Passwords have long been the bane of security team’s existence. They cause 89% of web application breaches through credential stuffing and brute force attacks, and stolen passwords allow threats like ransomware and phishing to gain traction. Passwordless authentication solves these issues because by eliminating passwords you remove all of the risks associated with them.
It’s important to note that not all solutions that tout themselves as “passwordless” truly remove passwords from the equation. Magic links, one-time passcodes, and mobile push notifications still have passwords as a back-up option, meaning a hacker can steal them and use them to authenticate. If a password is still in any way a part of the authentication process it can be stolen and used by malicious actors to wreak havoc.
How Beyond Identity uses passwordless authentication
Beyond Identity’s passwordless authentication not only truly removes passwords, but also provides risk-based authentication so you can be sure the person logging in is who they say they are, while also ensuring the security posture of the device. Our passwordless MFA provides strong, invisible authentication and verifies users with customizable risk policies. You can see how Beyond Identity works or request a demo to see it in action.
Are you interested in passwordless authentication? Here are some resources:
- Guide: Passwordless Authentication: What It Is and How It Works
- White paper: Why Passwords Stink
- Blog: Traditional Two-Factor Authentication vs. Beyond Identity’s Passwordless Authentication
- Blog: Can Passwordless Authentication Replace My MFA?
- Report: Overcoming the Hassle of Passwords and MFA with Passwordless Authentication
- Video: Why Strong Passwordless Authentication is a Foundational Element of Your IAM and Security Portfolio
As remote work continues to dominate as we head into 2022, finding the best security solution for organizations remains a top priority, especially as employees connect to critical resources using their own personal devices. So it’s no surprise that in Gartner’s report on emerging technologies and trends for 2022 that they consider “ubiquitous and transparent security” one of the core trends and themes going into this new year.
Gartner’s impact radar shows which technologies in these core areas will be a focus in the future and which are an initiative that organizations should take on now:

Gartner deems passwordless authentication as critical
Gartner has designated passwordless authentication as a key technology that organizations should adopt as soon as possible. Passwords have long been the bane of security team’s existence. They cause 89% of web application breaches through credential stuffing and brute force attacks, and stolen passwords allow threats like ransomware and phishing to gain traction. Passwordless authentication solves these issues because by eliminating passwords you remove all of the risks associated with them.
It’s important to note that not all solutions that tout themselves as “passwordless” truly remove passwords from the equation. Magic links, one-time passcodes, and mobile push notifications still have passwords as a back-up option, meaning a hacker can steal them and use them to authenticate. If a password is still in any way a part of the authentication process it can be stolen and used by malicious actors to wreak havoc.
How Beyond Identity uses passwordless authentication
Beyond Identity’s passwordless authentication not only truly removes passwords, but also provides risk-based authentication so you can be sure the person logging in is who they say they are, while also ensuring the security posture of the device. Our passwordless MFA provides strong, invisible authentication and verifies users with customizable risk policies. You can see how Beyond Identity works or request a demo to see it in action.
Are you interested in passwordless authentication? Here are some resources:
- Guide: Passwordless Authentication: What It Is and How It Works
- White paper: Why Passwords Stink
- Blog: Traditional Two-Factor Authentication vs. Beyond Identity’s Passwordless Authentication
- Blog: Can Passwordless Authentication Replace My MFA?
- Report: Overcoming the Hassle of Passwords and MFA with Passwordless Authentication
- Video: Why Strong Passwordless Authentication is a Foundational Element of Your IAM and Security Portfolio
As remote work continues to dominate as we head into 2022, finding the best security solution for organizations remains a top priority, especially as employees connect to critical resources using their own personal devices. So it’s no surprise that in Gartner’s report on emerging technologies and trends for 2022 that they consider “ubiquitous and transparent security” one of the core trends and themes going into this new year.
Gartner’s impact radar shows which technologies in these core areas will be a focus in the future and which are an initiative that organizations should take on now:

Gartner deems passwordless authentication as critical
Gartner has designated passwordless authentication as a key technology that organizations should adopt as soon as possible. Passwords have long been the bane of security team’s existence. They cause 89% of web application breaches through credential stuffing and brute force attacks, and stolen passwords allow threats like ransomware and phishing to gain traction. Passwordless authentication solves these issues because by eliminating passwords you remove all of the risks associated with them.
It’s important to note that not all solutions that tout themselves as “passwordless” truly remove passwords from the equation. Magic links, one-time passcodes, and mobile push notifications still have passwords as a back-up option, meaning a hacker can steal them and use them to authenticate. If a password is still in any way a part of the authentication process it can be stolen and used by malicious actors to wreak havoc.
How Beyond Identity uses passwordless authentication
Beyond Identity’s passwordless authentication not only truly removes passwords, but also provides risk-based authentication so you can be sure the person logging in is who they say they are, while also ensuring the security posture of the device. Our passwordless MFA provides strong, invisible authentication and verifies users with customizable risk policies. You can see how Beyond Identity works or request a demo to see it in action.
Are you interested in passwordless authentication? Here are some resources:
- Guide: Passwordless Authentication: What It Is and How It Works
- White paper: Why Passwords Stink
- Blog: Traditional Two-Factor Authentication vs. Beyond Identity’s Passwordless Authentication
- Blog: Can Passwordless Authentication Replace My MFA?
- Report: Overcoming the Hassle of Passwords and MFA with Passwordless Authentication
- Video: Why Strong Passwordless Authentication is a Foundational Element of Your IAM and Security Portfolio












.avif)
.avif)



.avif)






.avif)

