Eliminate phishing risks
Single-device, passwordless, phishing-resistant MFA to secure every authentication.
Eliminate breaches at the source
Remove your #1 threat vector: the credential.
Secure your entire fleet
Protect access from managed and unmanaged devices, like BYOD, mobile phones, and contractors.
Compliant by default
Meet the toughest mandates from day one; NIST 800-63B, AAL3, and CISA Phishing-Resistant MFA mandates.
Increase user productivity
Remove the top cause of support tickets: passwords. Users stay productive and your team breathes easier.

Built to protect every user,
on every device
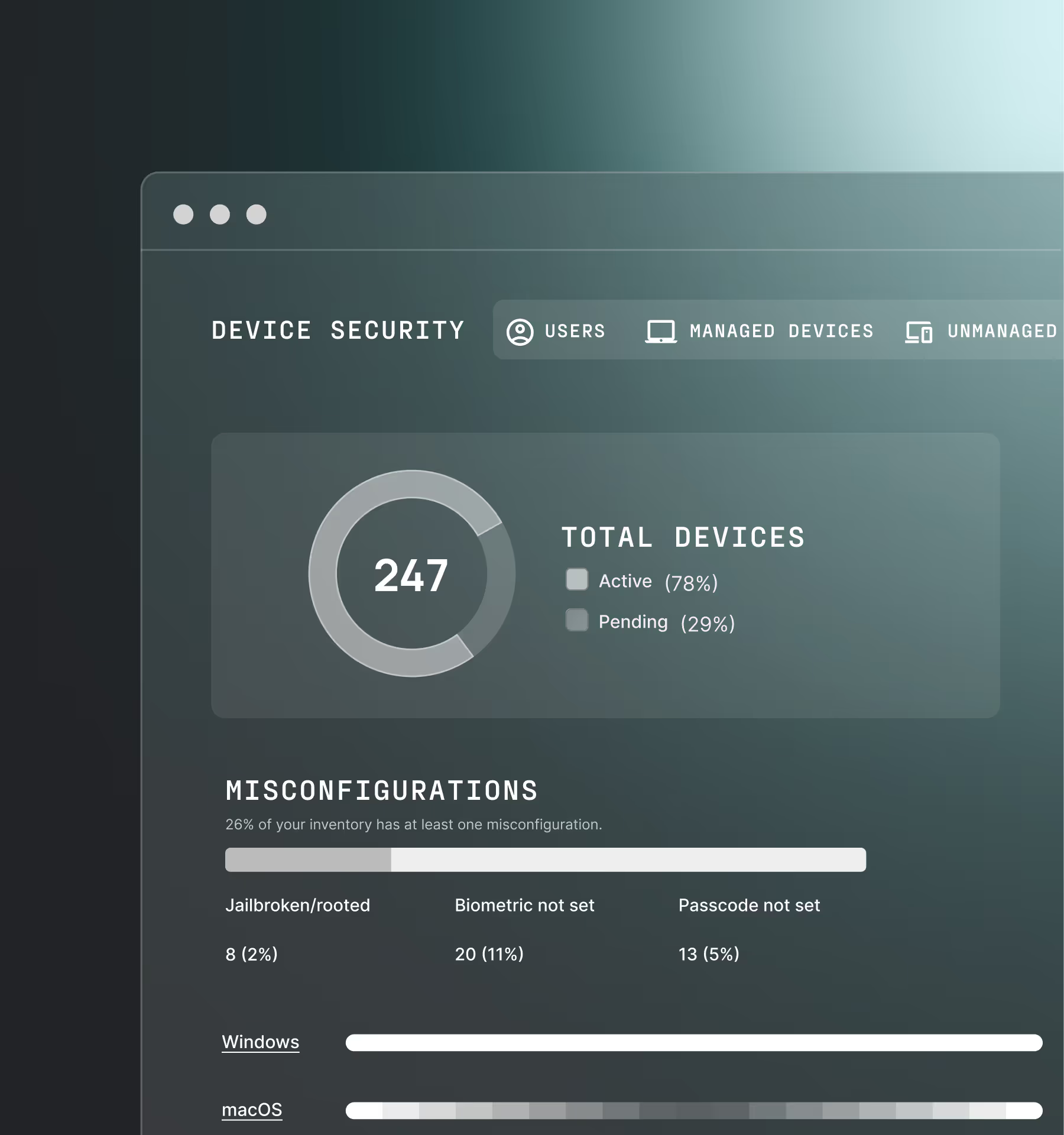
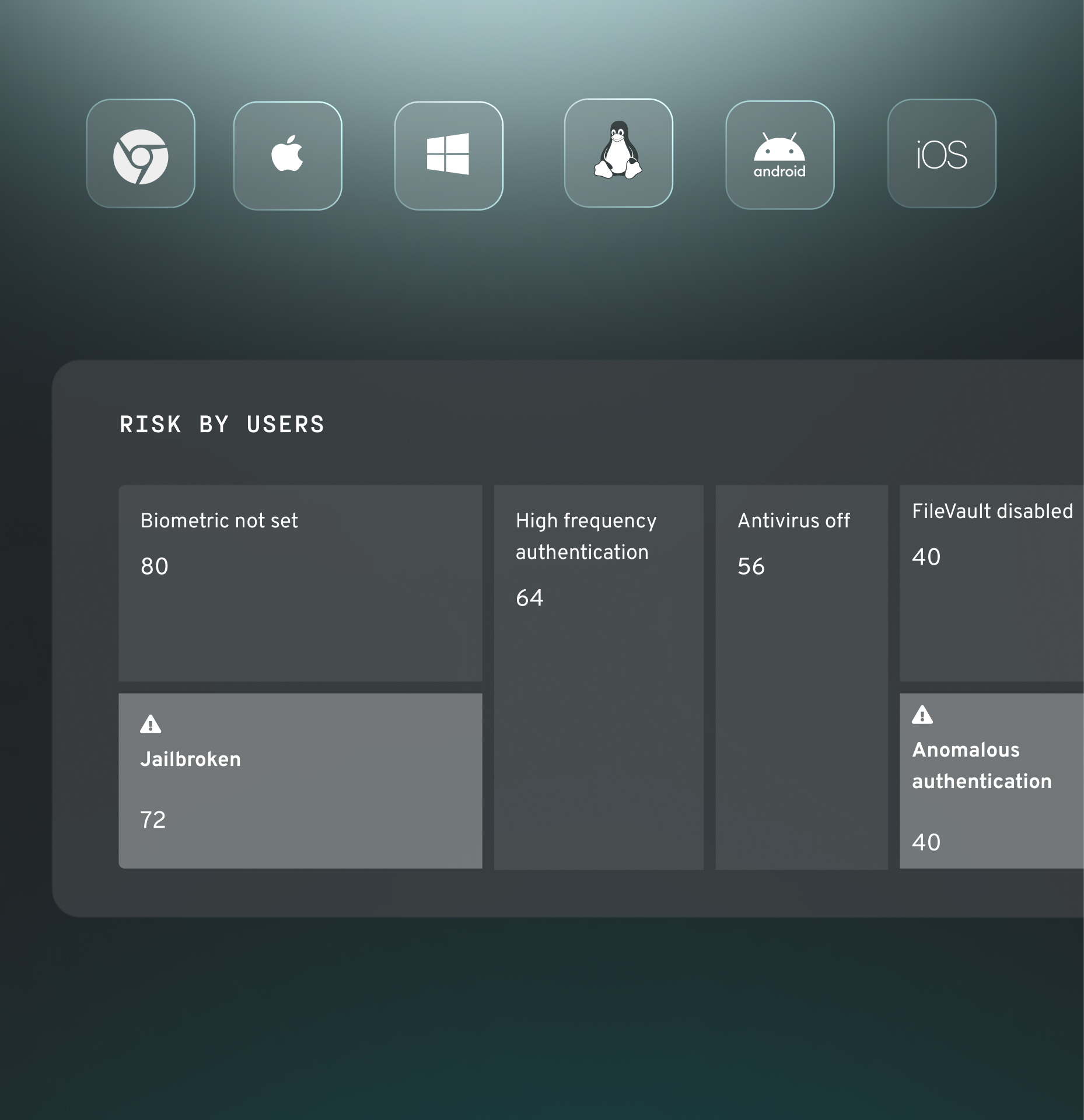
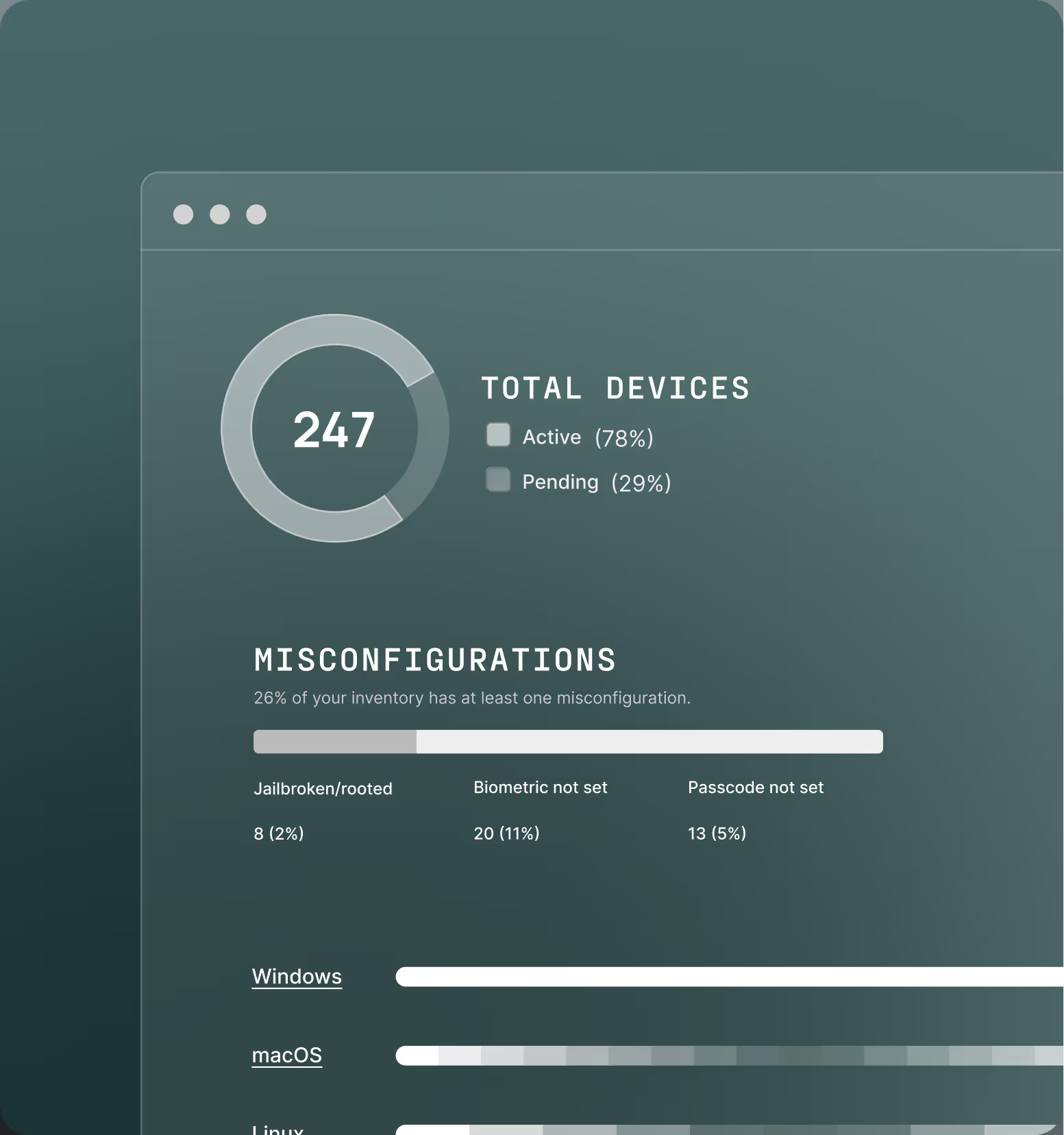
Legacy technology poses a direct threat to your organization by granting access to devices that are out of compliance or whose security posture has changed.
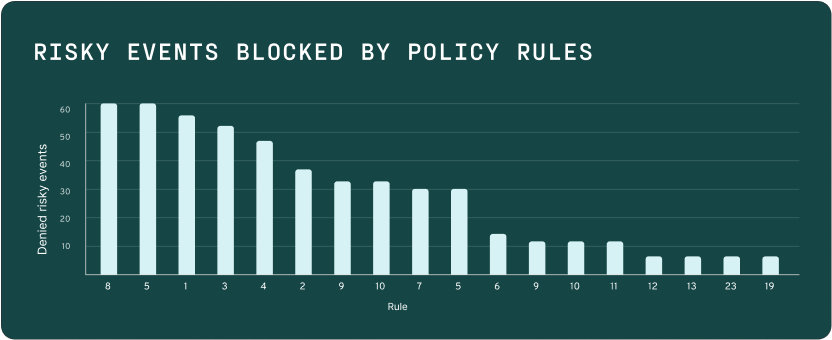
Continuous risk-based authentication
Single-device, passwordless login experiences that takes out the speedbumps in authentication across every device and OS (including Linux!)
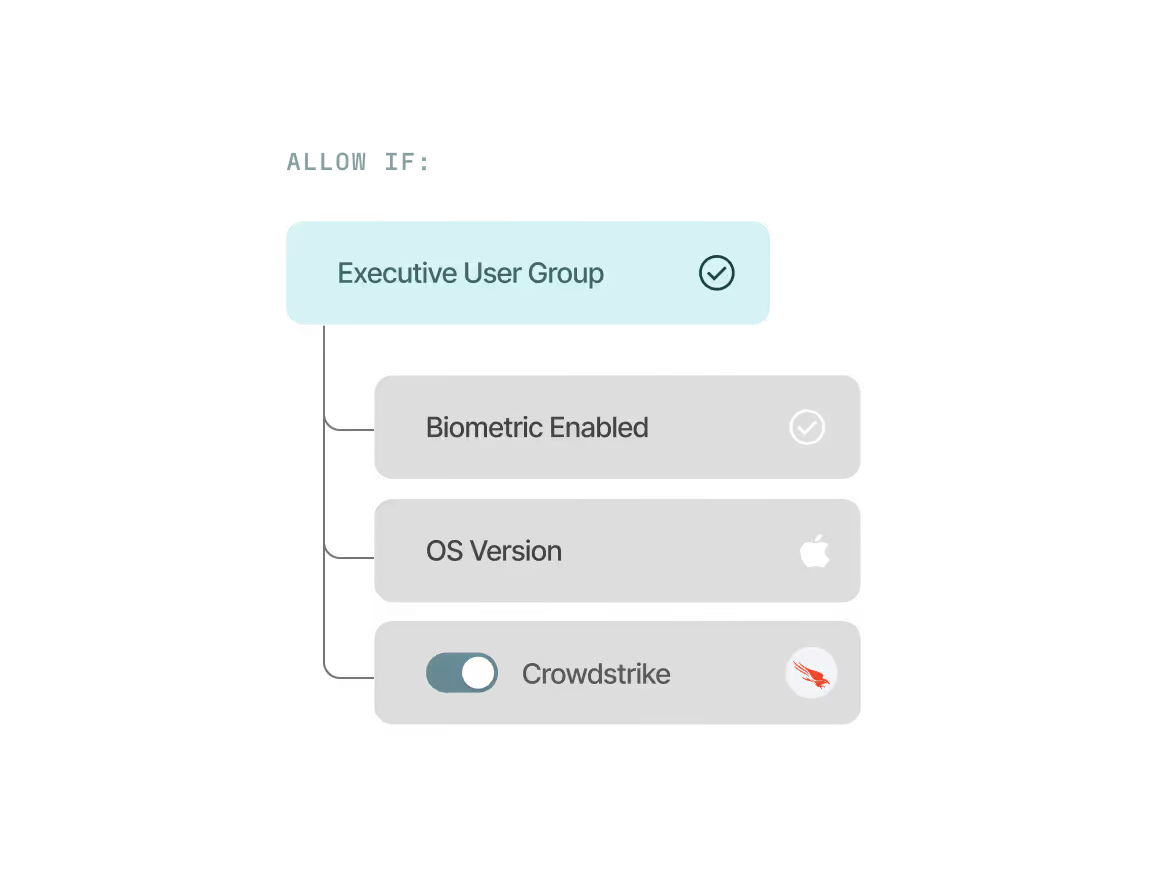
Enforce precise access controls
Easily configure customizable, adaptive risk-based policies tailored to your exact security and compliance requirements. Leverage signals natively collected by Beyond Identity and other security tools in your stack.

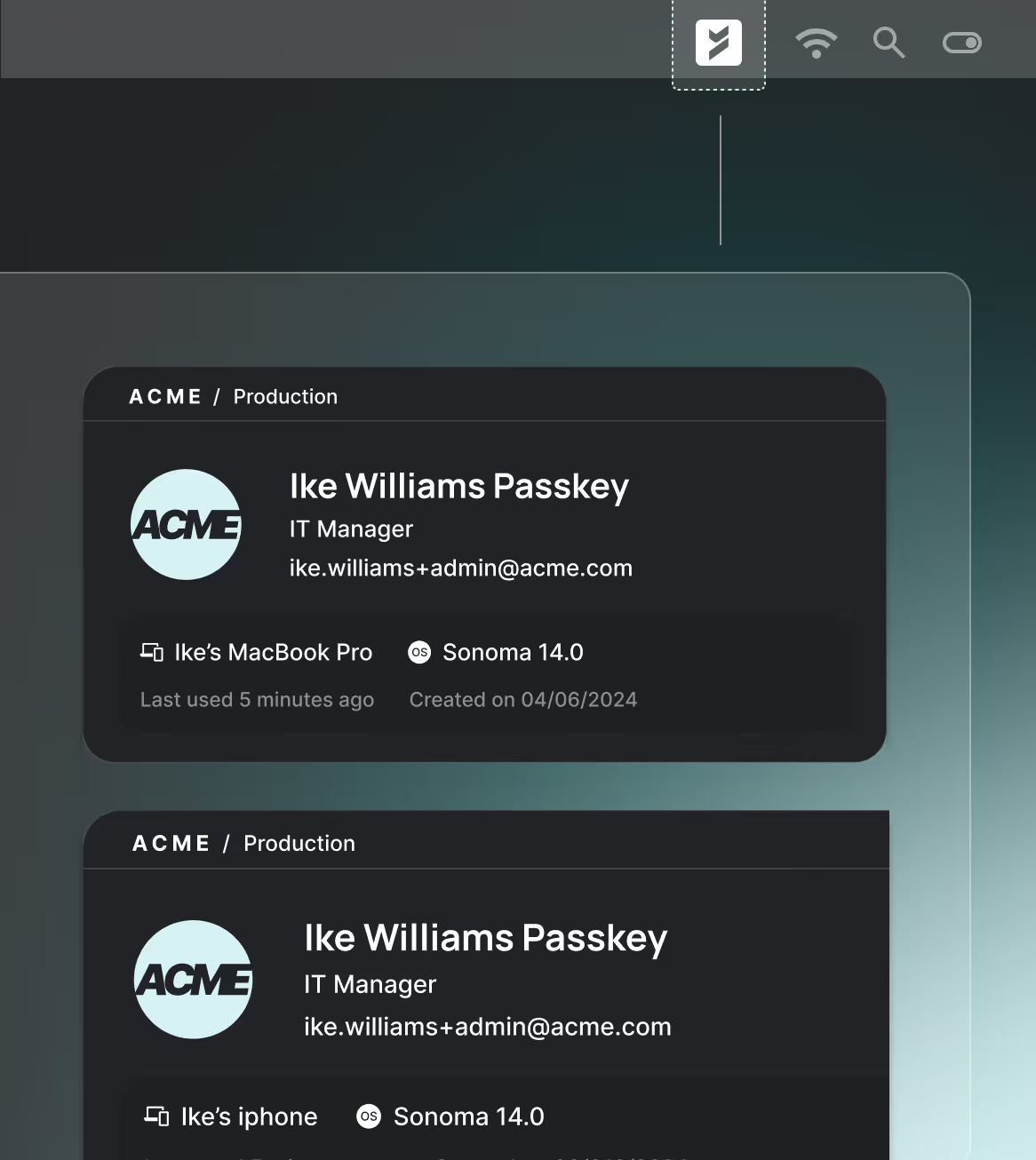
Device security compliance
Ensure access is only granted to a trusted device, managed or unmanaged, with the appropriate security posture as defined by your policy.
Why Beyond Identity?
Traditional MFA providers leaves organizations exposed to modern threats. Beyond Identity’s phishing-resistant MFA solution prevents those threats at the source.
Validating both users and devices continuously, as separate
but equally important requirements for risk-based authentication.
Single-point in time authorization of users only, oftentimes using phishable factors that can leave organizations open to risk.
Frictionless
Authenticates users through built-in biometrics or device unlock — no codes, links, or second devices required.
Frustrating
Adds friction with passwords, OTPs, push notifications, and secondary devices.
100% Phish-resistant
100% resistant — uses tamper-proof, device-bound cryptographic passkeys.
Vulnerable
Relies on phishable factors like SMS, OTP, or push approvals.
operation
100% Passwordless
Passwords are fully eliminated across devices and operating systems.
Relies on passwords
Passwords are required for setup or fallback authentication.
validation
User and device
Authenticates both user identity and device posture (e.g., OS version, encryption, firewall).
Users only
Focuses on user identity only; device trust is ignored.
Always-on
Monitors user and device compliance after login; revokes access if the user or device drifts out of policy.
Static
Performs static checks at login — no reevaluation post-authentication.
Continuous
Continuously enforces fine-grained policies across managed and unmanaged devices.
Static
Provides no visibility into device security posture.
integration
Fully integrated
Integrates natively with CrowdStrike, Intune, Jamf, Okta, SentinelOne, and others to enforce conditional access.
Limited
Limited or surface-level integrations, often lacking enforcement.
Enhanced
Exports cryptographically linked user-device logs to SIEMs (JSON/syslog) for forensic investigation.
Siloed
Siloed logging; minimal context for incident response.
policy enforcement
Easy
Built-in controls enforce Zero Trust and compliance frameworks (e.g., NIST 800-207) by design.
Complicated
Admins must manually configure controls; inconsistent and hard to scale.
Compliant
Designed from the ground up to enforce Zero Trust — no implicit trust, continuous validation of users and devices.
Immature
Still perimeter-based; lacks continuous trust evaluation.
Adversaries Exploit Japanese Brokerage Accounts in $700M Stock Manipulation Spree
What Is Push Bombing? And How Beyond Identity Makes It Impossible
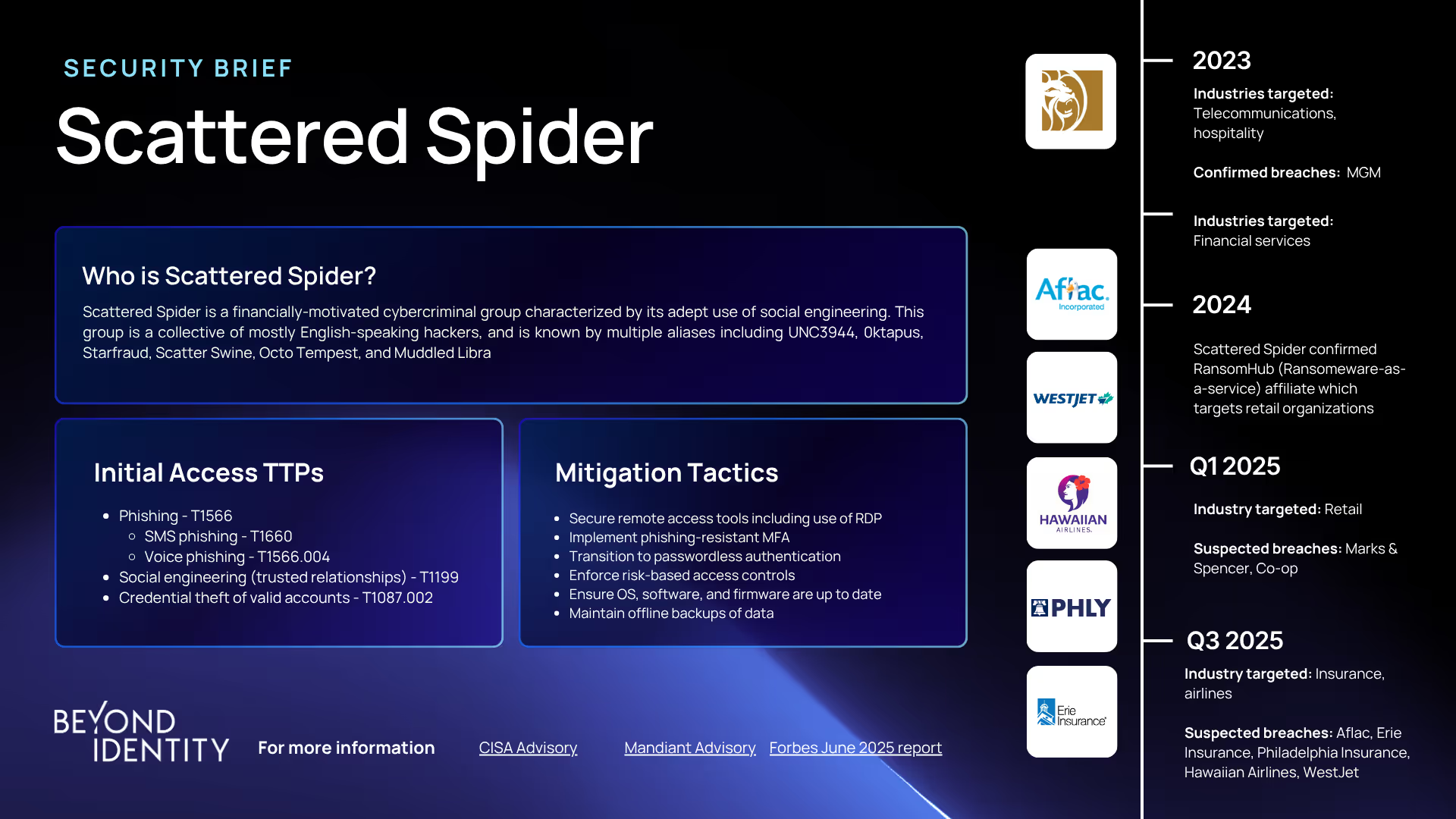
Scattered Spider: How to Effectively Defend Against This Aggressive Threat

%20(2).avif)

.avif)
