The Beyond Blog
.png)
15 Sep 2025
Universal Identity Defense for Legacy and On-Prem Applications with Beyond Identity and CrowdStrike
Extend phishing-resistant MFA to Kerberos, NTLM, LDAP, SMB with Beyond Identity + CrowdStrike.
22 May 2024
May 22, 2024
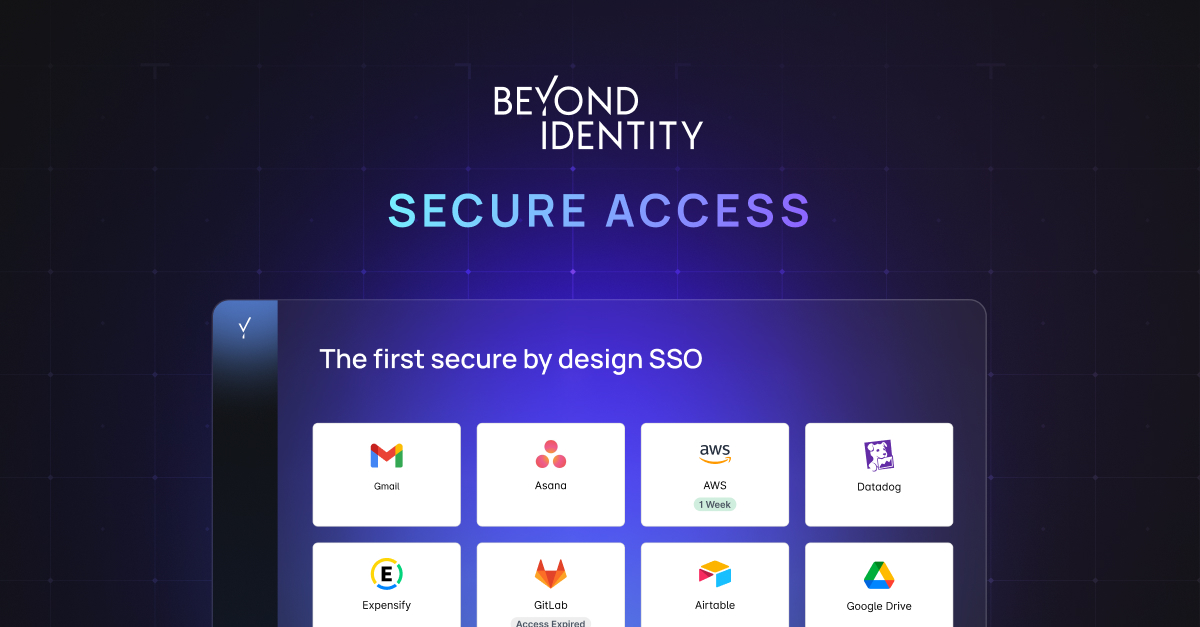
No More Compromise: The First and Only Secure-by-Design Access Platform is Here
Legacy SSOs, such as Okta and Microsoft Entra ID, were built for productivity, but failed to secure organizations . Introducing Secure Access, the first unified identity access management platform designed to secure the most vulnerable part of your environment against current and future threats, while being simple to administer and easy to use.

16 May 2024
May 16, 2024
Combating Deepfakes and Generative AI: A Zero Trust Approach to Authenticity Assurance
Generative AI poses significant threats to organizations as they combat deepfake impersonations and increasing phishing attempts. What does a zero trust approach look like for defending against generative AI?

16 May 2024
May 16, 2024
Beyond Identity Signs CISA Secure by Design Pledge
Beyond Identity signs the CISA Secure by Design pledge. Learn more about the pledge and our unwavering commitment to Secure by Design.

30 Apr 2024
April 30, 2024
8 ‘Don’t Miss’ Sessions at RSAC 2024
Learn which sessions we think are a "must see" at RSA Conference 2024
%2520(2).png)
24 Apr 2024
April 24, 2024
Guaranteed Security: From Probabilities to Absolutes
Learn why adopting a new, deterministic approach to cybersecurity is crucial in a new webinar

22 Apr 2024
April 22, 2024
Bridging the Gap: Honoring Veterans in Cybersecurity with VetSec at RSAC
Tom Marsland, Chairman of VetSec, discusses why an upcoming event honoring veterans at RSAC 2024 is so critical for the security industry
.jpeg)
17 Apr 2024
April 17, 2024
Managing Your Attack Surface with Beyond Identity
Securing your organization's attack surface is essential to protect you from financial losses, reputational damage, operational disruptions, and theft of sensitive information
11 Apr 2024
April 11, 2024
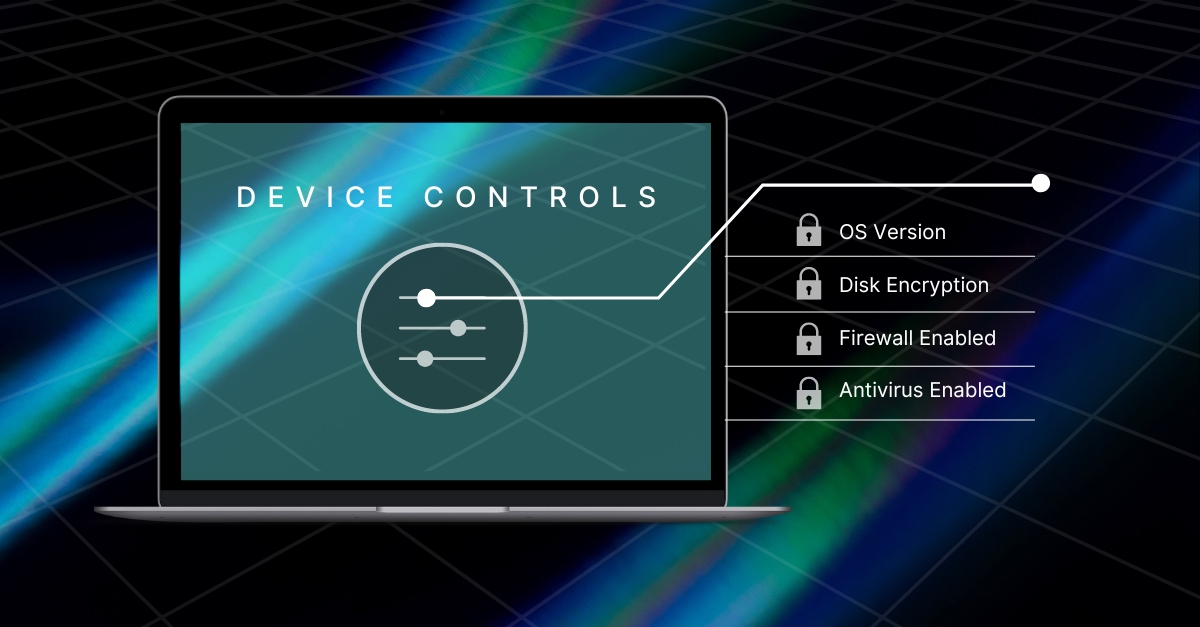
Closing the Gaps in Endpoint Security: Beyond Traditional Solutions
Learn more about advanced endpoint security strategies, modern MFA, zero-trust principles, and unified management for risk management
09 Apr 2024
April 9, 2024

