The Beyond Blog

22 Jan 2026
Beyond Identity Opens Early Access for the AI Security Suite
Gain visibility and control over autonomous AI agents with Beyond Identity's AI Security Suite. Enforce identity, device context, and data governance with cryptographic proof. Early access is now open!
.avif)
09 Jan 2025
January 9, 2025
Beyond Identity Launches New Channel Program to Accelerate Partner Business Growth
The launch of our channel program signifies our commitment to a partner-first strategy
.avif)
06 Jan 2025
January 6, 2025
Beyond Identity Expands CrowdStrike Integration to Enforce Real-Time Access Decisions with Comprehensive Risk Attributes
The Beyond Identity integrations leverage CrowdStrike’s world-class threat detection and response capabilities to enhance preventive measures.

31 Dec 2024
December 31, 2024
BeyondTrust incident does not impact Beyond Identity
Recent potential incident involving BeyondTrust: unrelated and does not impact Beyond Identity and our customers.

20 Dec 2024
December 20, 2024
AuthQuake: A New Brute Force Attack on Microsoft MFA
AuthQuake is a newly discovered vulnerability that exploits weaknesses in Microsoft's MFA implementation. Learn more about what it is and how to defend against it

02 Dec 2024
December 2, 2024
How to Defend Against Rockstar 2FA Bypass Attacks Targeting Microsoft and Google
Rockstar 2FA is a phishing-as-a-service kit targeting Micorosft and Google services. Learn about their exploit techniques and how to defend against them effectively.

16 Oct 2024
October 16, 2024
Beyond Identity Secure SSO: Delivering 99.99% Uptime
.avif)
23 Sep 2024
September 23, 2024
Top 10 Takeaways from BeyondCon 2024
Top 10 takeaways from our inaugural Beyond Identity conference
18 Sep 2024
September 18, 2024
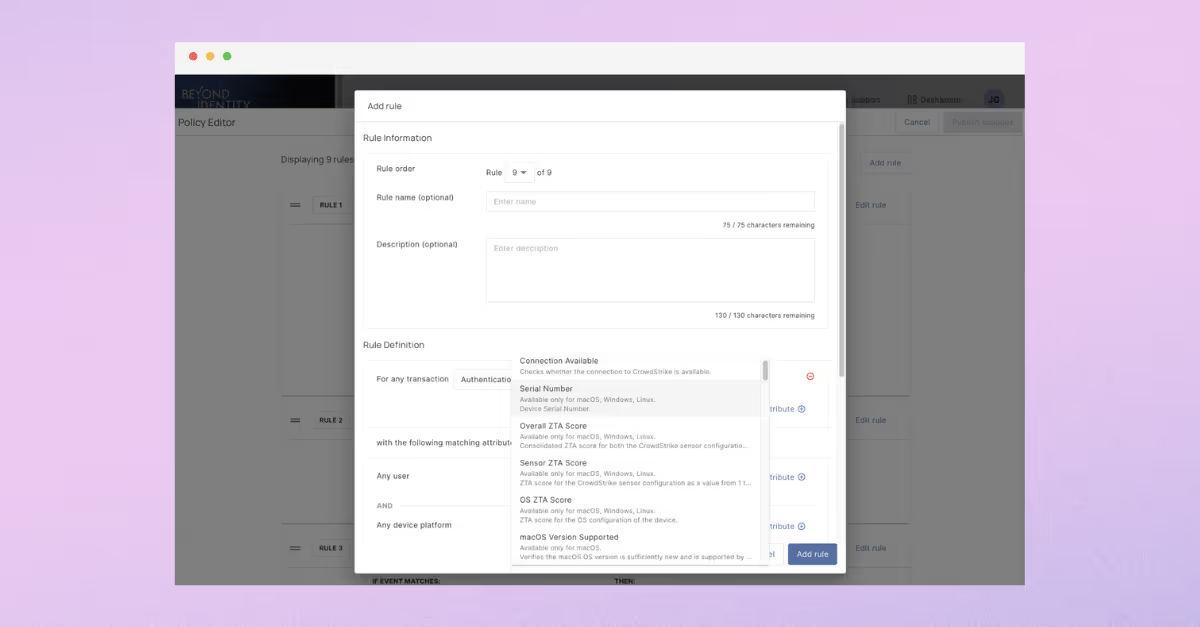
Continuous Risk-Based Access Control with Beyond Identity’s CrowdStrike Integration
Beyond Identity sets the standard in access security with the deepest CrowdStrike integration, allowing over 45 CrowdStrike attributes to be used in policy and administrators to quarantine risky devices via CrowdStrike
06 Aug 2024
August 6, 2024
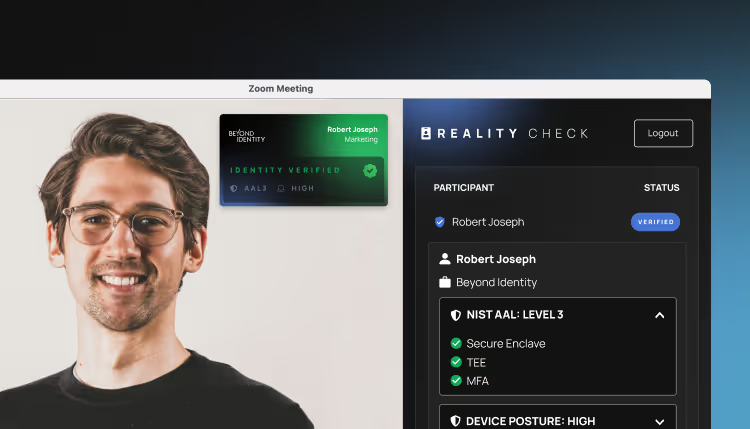
Introducing RealityCheck
RealityCheck uses deterministic signals to prevent deepfake and AI impersonation attacks on high-risk conference calls.

